How SSH Works: A Comprehensive Overview
 Bhavesh Yadav
Bhavesh YadavTable of contents
In today's digital age, secure communication and data transfer are of utmost importance. Whether you're a developer, system administrator, or just a regular user, you've probably heard of SSH. SSH, or Secure Shell, is a network protocol that allows you to securely connect to a remote server or computer over an unsecured network. It provides a secure channel for data communication, remote command execution, and other network services. SSH is widely used in the IT industry for managing servers, transferring files, and accessing remote resources. It's a powerful tool that can help you streamline your workflow and improve your productivity.
In this blog, we'll explore the basics of SSH, how it works, and how you can use it to connect to remote servers securely. We'll also cover some best practices for using SSH and common issues you may encounter. So, whether you're a seasoned IT professional or just getting started, read on to learn more about SSH and how it can benefit you.
How SSH Works
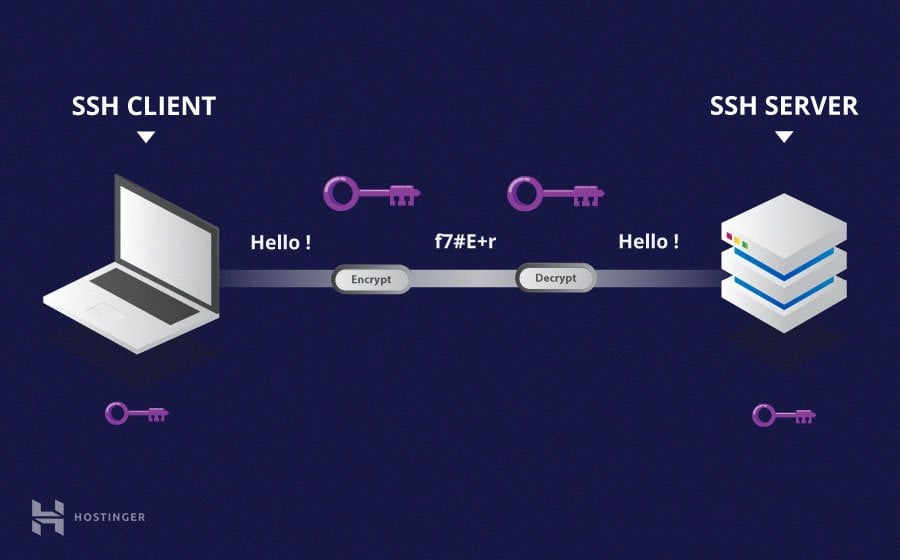
SSH works by establishing a secure, encrypted connection between two computers. When a user logs in to a remote system using SSH, the client and server exchange cryptographic keys to establish a secure connection. Once the connection is established, the user can execute commands on the remote system as if they were sitting in front of it.
SSH uses public-key cryptography to authenticate users and encrypt data. Public-key cryptography involves the use of two keys: a public key and a private key. The public key is shared with others, while the private key is kept secret. When a user logs in to a remote system using SSH, the client sends its public key to the server. The server then uses this key to encrypt a message that can only be decrypted using the client's private key. This ensures that only the client with the correct private key can log in to the remote system.
Setting Up SSH
To use SSH, you'll need to have an SSH client installed on your local machine and an SSH server running on the remote system you want to connect to. Most Linux and Unix systems come with an SSH server pre-installed, but you may need to install an SSH client on your local machine if it doesn't already have one.
To set up SSH, you'll need to generate a public-private key pair on your local machine. You can do this using the ssh-keygen command, which is included with most SSH clients. Once you've generated your key pair, you'll need to copy your public key to the remote system you want to connect to. You can do this using the ssh-copy-id command, which will copy your public key to the remote system's authorized_keys file.
Once you've set up SSH, you can log in to the remote system using the ssh command. For example, to log in to a remote system with the IP address 192.168.1.100, you would use the following command:
ssh username@192.168.1.100
Replace "username" with your username on the remote system.
Best Practices for Using SSH
To use SSH securely, there are a few best practices you should follow:
Use strong passwords: Even though SSH uses public-key cryptography for authentication, you should still use strong passwords to protect your private key. If someone gains access to your private key, they can log in to any system that has your public key.
Use a passphrase: When you generate your SSH key pair, you can add a passphrase to your private key. This passphrase is required to use your private key, so even if someone gains access to your private key, they won't be able to use it without the passphrase.
Disable password authentication: To further secure your SSH connection, you can disable password authentication and only allow public-key authentication. This ensures that only users with the correct private key can log in to the remote system.
Use a firewall: To prevent unauthorized access to your SSH server, you should use a firewall to restrict access to the SSH port (usually port 22). You can also use tools like fail2ban to automatically block IP addresses that attempt to log in to your server with incorrect credentials.
Conclusion
SSH is a powerful tool for remote system administration and file transfers. By following best practices for using SSH securely, you can ensure that your remote connections are protected from unauthorized access. If you're new to SSH, take some time to learn the basics and experiment with different configurations to find the setup that works best for you.
Subscribe to my newsletter
Read articles from Bhavesh Yadav directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Bhavesh Yadav
Bhavesh Yadav
Passionate full stack developer with expertise in both front-end and back-end technologies. Creating seamless digital experiences through innovative solutions.