What is Azure Key Vault and how to use it in your Azure Pipeline?
 Abhinandan Shrestha
Abhinandan Shrestha
To understand Azure Key vaults, think of a scenario like a backend connection to databases. The question is “Do we directly use connection strings in our code?”. Storing connection strings and other sensitive information directly in your code is generally not recommended. Instead, using environment variables or a configuration management system is a better approach. Similar to the backend scenario, Azure Key Vault allows you to implement this approach in a cloud-based environment. Azure Key Vault is a cloud-based service provided by Microsoft Azure that allows you to securely store and manage sensitive information such as secrets, keys, and certificates. It provides a central repository for managing and safeguarding cryptographic keys, secrets (like API keys or database connection strings), and digital certificates. Azure Key Vault is considered a better and more secure approach for managing secrets and sensitive configuration information in Azure-based applications including Synapse pipelines and Data Factory.
Q. How to use key vaults in your Azure Pipelines?
Step1: Copy the Managed Identity object ID of your synapse workspace or if you are using Data Factory, copy the Managed Identity object ID of Data Factory

Step 2: Go to Key vaults

Step 3: Go to Secrets > Generate/import
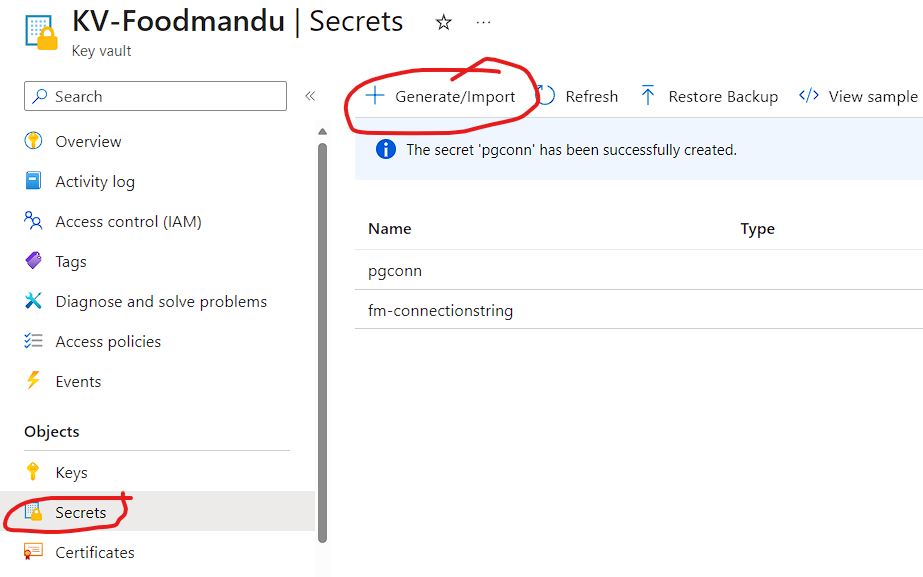
Step 4: Give your secrets a name and paste the connection string
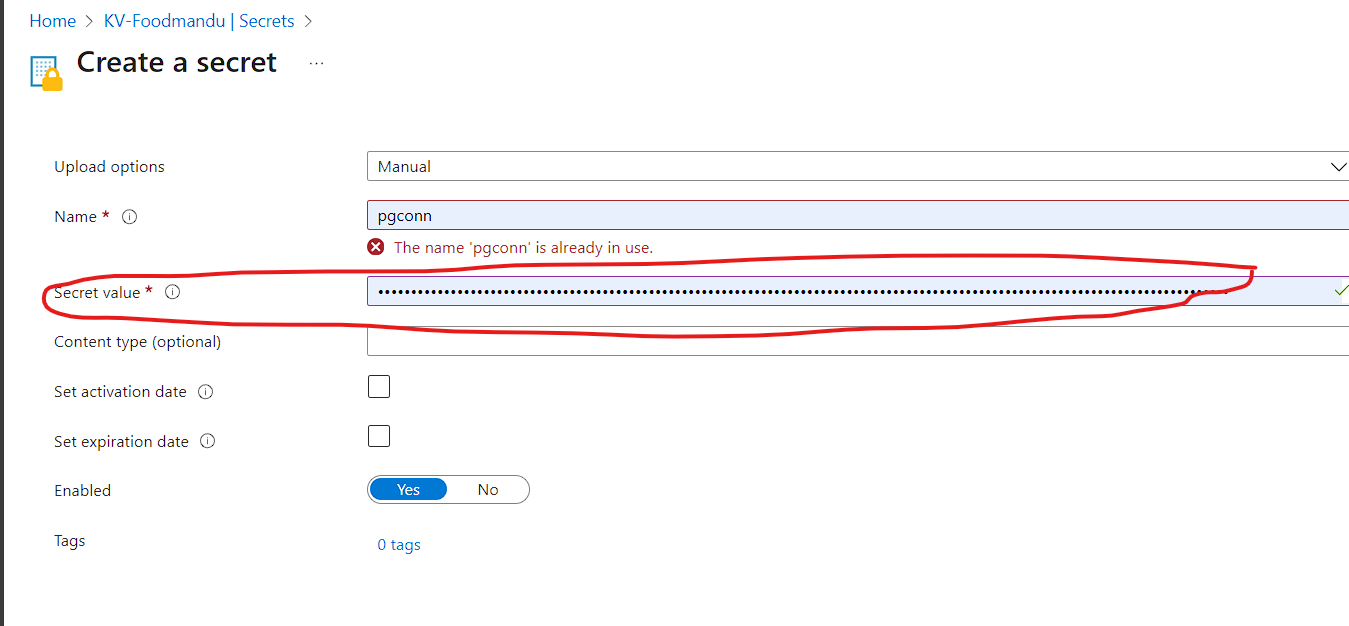
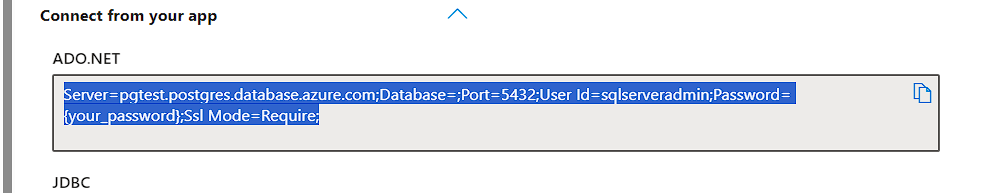
Server=pgtest.postgres.database.azure.com;Database={database_name};Port=5432;User Id=sqlserveradmin;Password={your_password};Ssl Mode=Require;
Step 5: Go to your key vault > Access Configuration > Go to access policies

Step 6: Select Get, List, WRAP, UNWRAP permissions

Step 7: Enter the managed identity key from step 1
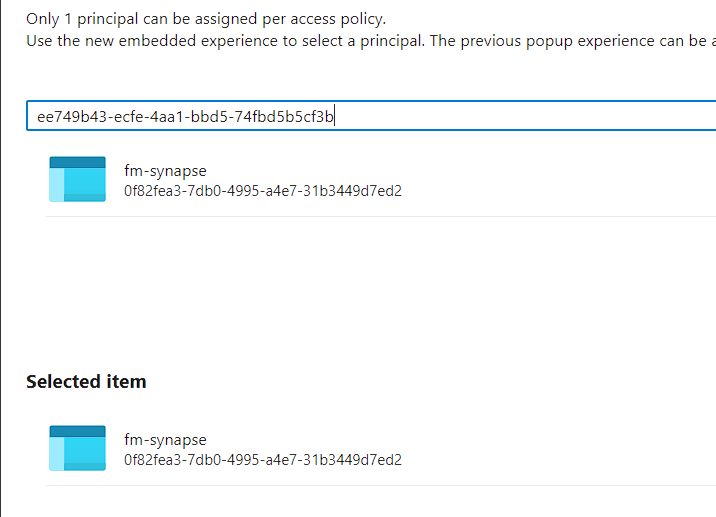
Step 8: Review and Create

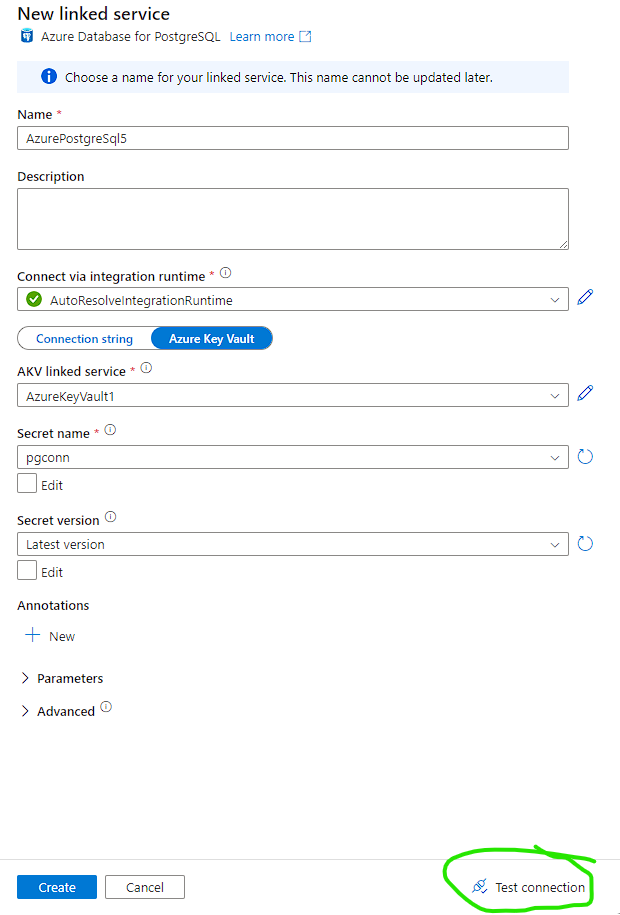
Step 9: Test Connection
Subscribe to my newsletter
Read articles from Abhinandan Shrestha directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by