Get started with AWS Network Load Balancer
 Maxat Akbanov
Maxat Akbanov
Amazon Web Services (AWS) offers a variety of load balancing services, one of which is the Network Load Balancer (NLB). The NLB operates at the fourth layer of the OSI model (the transport layer) and is designed to handle millions of requests per second while maintaining ultra-low latencies.
Key Characteristics:
High Performance:
Handles volatile workloads and millions of requests per second.
Delivers low-latency performance.
Static or Elastic IP:
- Offers a static IP per Availability Zone (AZ) or a single elastic IP to support use-cases that require IP address persistency.
TLS Termination:
- Supports TLS termination, allowing it to handle SSL (Secure Sockets Layer) and/or TLS (Transport Layer Security) traffic.
Target Groups:
- Supports routing requests to AWS services like EC2 instances, ECS containers, EKS pods, Lambda functions, and IP addresses.
Health Checks:
- Monitors the health of registered targets and ensures that traffic is only routed to healthy targets.
Preservation of Source IP:
- Preserves the source IP address and source ports of the client, which can be essential for applications that require tracking of the IP address for security, audit, or compliance purposes.
Zonal Isolation:
- Enables zonal isolation, which keeps traffic and failures isolated to the availability zone in which they originate.
Support for UDP Traffic:
- Unlike some other load balancers, NLB allows for the routing and load balancing of UDP (User Datagram Protocol) traffic.
Use-Cases:
High-Performance Applications:
- Ideal for applications that need to handle high-throughput and volatile workloads with low latency.
TCP/UDP Protocols:
- Suited for applications or systems that use TCP or UDP protocols and need to manage requests in a high-performance manner.
TLS Offloading:
- Suitable for applications requiring optimized and secure handling of TLS encryption and decryption (TLS offloading).
Static IP or Elastic IP:
- Useful when an application requires a consistent IP address.
Microservices and Container-Based Applications:
- NLB enables efficient and performant routing to services and applications within containerized infrastructures like ECS and EKS.
How NLB Works:
Listener Configuration:
- A listener is configured with a protocol and a port for connections from clients to the load balancer, and a default rule for forwarding requests.
Target Registration:
- Register targets, such as EC2 instances or microservices, with the NLB, and it will automatically route traffic to them based on health and configured routing rules.
Health Checks:
- NLB conducts health checks to ensure targets are capable of handling traffic. If a target fails a health check, it is de-registered, and traffic is routed to healthy targets.
Handle Client Requests:
- When a client sends a request to the NLB, it selects a target from its registered list and forwards the request to it, based on the routing rules defined.
Continuous Monitoring:
- Continuously monitors the health of its targets and adjusts routing accordingly.
The AWS Network Load Balancer is an effective solution for managing network traffic with high-throughput, low-latency needs, while offering robust health checks, sticky sessions, and support for both TCP and UDP protocols. Its operation at the transport layer allows for the management and routing of packets in an optimized, efficient manner, making it suitable for applications and architectures that require high performance and reliability.
Workshop Exercise: Deploying a Basic Web Application with AWS Network Load Balancer (NLB)
Objective:
Deploy two EC2 instances running a basic web application, and distribute incoming HTTP requests to these instances using a Network Load Balancer.
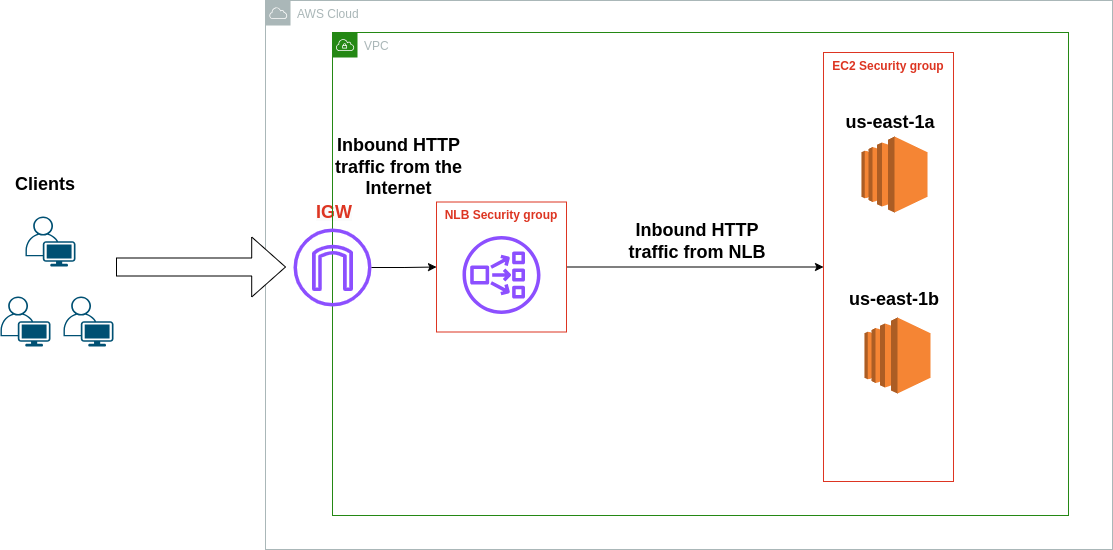
Step 1: Deploy EC2 Instances
- Launch two EC2 instances, ensuring they're in different Availability Zones (AZs).
To specify the Availability zone to launch EC2 instance use --placement AvailabilityZone=us-east-1a flag.

SSH into each instance and install a web server (e.g., Apache). Create a unique HTML page for each (e.g., “Hello from Instance 1/2”).
Example commands for installing Apache and editing the default web page on an Amazon Linux 2 server:
# Once inside the EC2 instance, update the packages sudo yum update -y # Install Apache HTTP Server sudo yum install -y httpd # Start Apache HTTP Server sudo systemctl start httpd # Ensure Apache HTTP Server starts at boot sudo systemctl enable httpd # Create a custom index.html file echo "Hello from Instance 1" | sudo tee /var/www/html/index.html
Step 2: Configure Security Groups
Ensure EC2 security groups allow traffic on port 80 (HTTP) from source NLBSecurityGroup.


After creation of the NLB, create an NLB security group that allows incoming traffic on port 80. In NLBSecurityGroup allow HTTP traffic from anywhere on port 80 and add it to the load balancer.

Step 3: Set Up the Network Load Balancer
Navigate to EC2 → Load Balancers → Create Load Balancer.
Choose Network Load Balancer, provide a name, choose "internet-facing"

Select the VPC and enable the AZs where your EC2 instances are.

Step 4: Define Target Group and Add Instances
Create a new target group with a relevant name and select "instance" as the target type and TCP as the protocol.

Define a health check path (e.g., “/index.html”).

Add your EC2 instances to this target group.

Step 5: Configure Routing and Listener
Go back to your NLB configuration and set up the routing to point to the target group you just created.
Ensure that the listener for TCP traffic on port 80 is correctly configured.

Enable cross-zone load balancing

Step 6: Finalize and Test the NLB
Complete the NLB setup and note down the DNS name given by AWS.
Visit the DNS URL in a web browser, and you should see the message from one of your EC2 instances. Refresh several times to see if it balances between “Hello from Instance 1” and “Hello from Instance 2”.
Step 7: Simulate Failure
Stop the Apache service on one of your instances (e.g. instance 1):
sudo systemctl stop httpdRefresh your web page using the NLB DNS name. All requests should now be routed to the healthy instance.

Once you're satisfied with the test, restart Apache:
sudo systemctl start httpd
Step 8: Clean Up
Navigate to the NLB section and delete the NLB.
Delete or de-register the target group (if it's not deleted with the NLB).
Terminate the EC2 instances to prevent further charges.
Extra Tasks:
Auto Scaling: Explore AWS Auto Scaling Groups and associate your target group with the Auto Scaling Group, enabling automatic scaling of your application based on defined metrics.
Secure Traffic: In the NLB, change your listener from TCP/80 to TLS/443, and provide the necessary SSL certificates. If you use self-signed certificates for testing, remember they are not recommended for production.
CloudWatch Metrics: Navigate to CloudWatch and explore metrics under the “Load Balancer” namespace. Set up some basic alarms, e.g., an alarm for when the number of healthy hosts in your target group equals zero.
Logging: In the NLB settings, enable logging, specifying an S3 bucket for storage. Investigate logs to understand your traffic patterns.
References:
Subscribe to my newsletter
Read articles from Maxat Akbanov directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Maxat Akbanov
Maxat Akbanov
Hey, I'm a postgraduate in Cyber Security with practical experience in Software Engineering and DevOps Operations. The top player on TryHackMe platform, multilingual speaker (Kazakh, Russian, English, Spanish, and Turkish), curios person, bookworm, geek, sports lover, and just a good guy to speak with!