AWS Site-to-Site VPN Configuration Notes
 Peter Walker
Peter Walker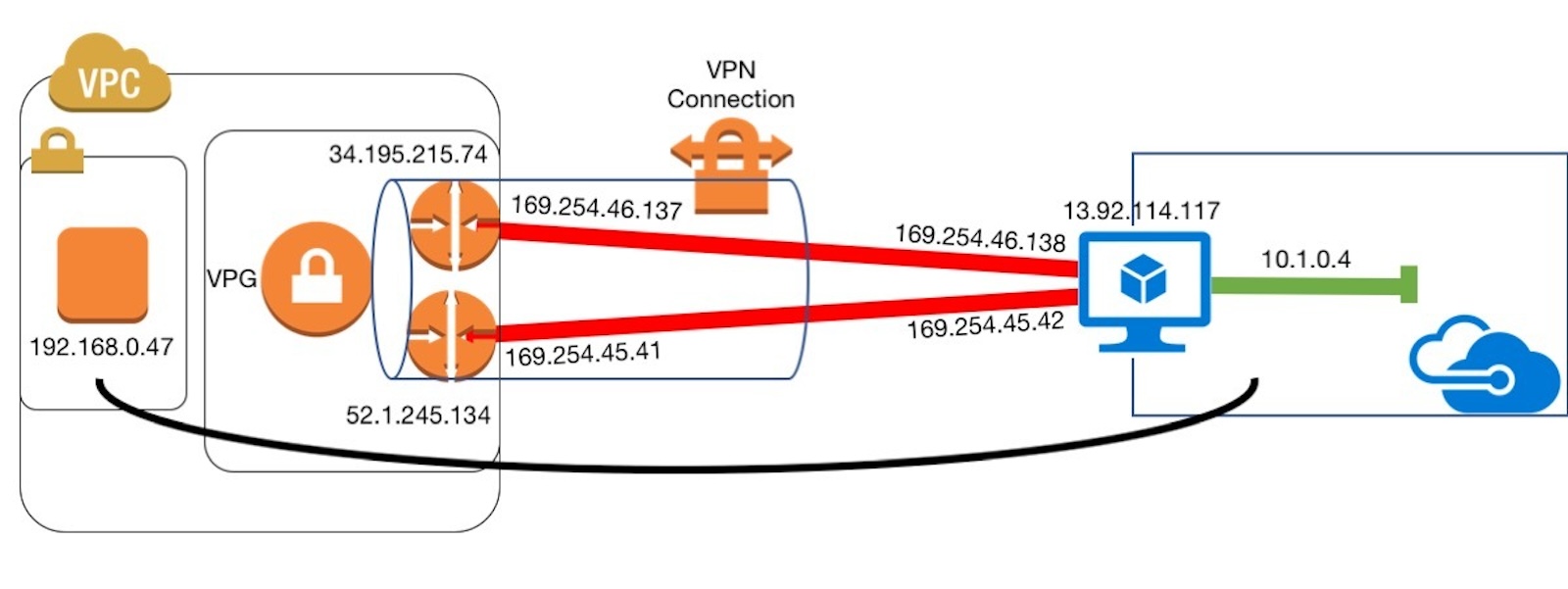
More details here: AWS Site-to-Site VPN Documentation
I recently had to configure a Site-to-Site VPN connection between an AWS VPC and an Azure VNet. The appliance on the other end was able to ultimately talk to an EC2 instance after messing around with the config. I did a lot of Googling and couldn't figure out what I did wrong, so I began to add static routes to troubleshoot connectivity and enable ICMP via Security Groups.
After some messing around with the configuration I realized the static routes were improperly configured on my end. I entered the subnets for the local VPC, but these should have been the subnets on the other end - Azure's VNet. I also realized I had to open a few ports to allow the ingress from Azure to AWS at the required ports.
TLDR; take a look at the Static Routes - these need to reference the subnets on the other end. Also don't forget about Security Groups to control ingress on your required ports.
Subscribe to my newsletter
Read articles from Peter Walker directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Peter Walker
Peter Walker
DevOps Engineer that wears multiple hats.