Day - 39 AWS and IAM Basics☁
 sonal singh
sonal singh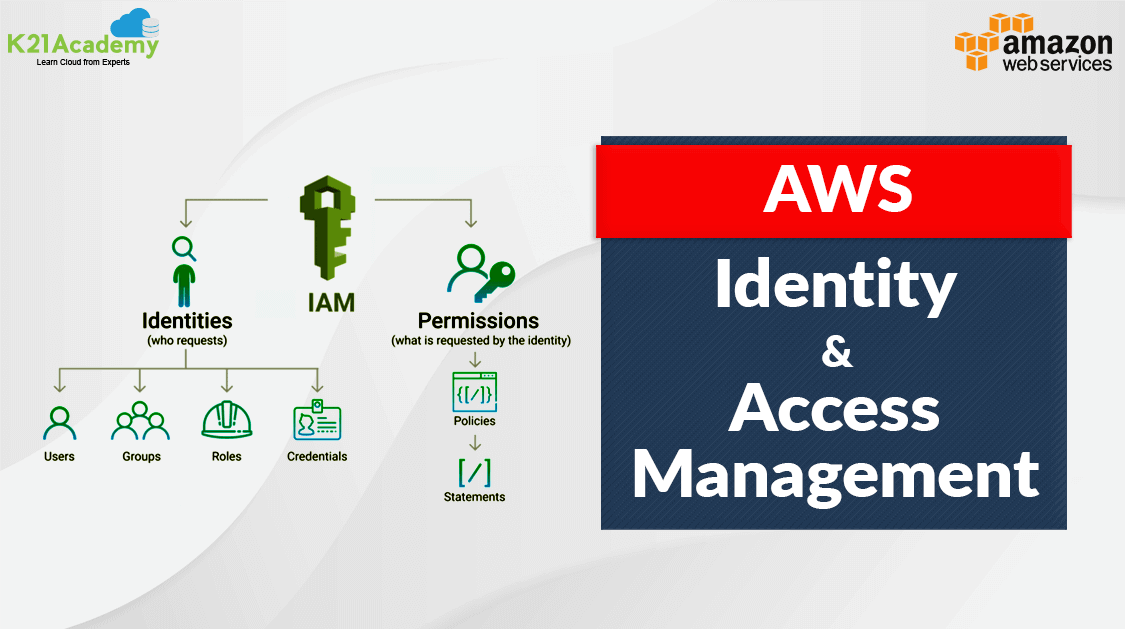
Introduction to IAM :
AWS Identity and Access Management (IAM) is a web service that helps you securely control access to AWS resources.
With IAM, you can centrally manage permissions that control which AWS resources users can access.
You use IAM to control who is authenticated (signed in) and authorized (has permissions) to use resources.
When you create an AWS account, you begin with one sign-in identity that has complete access to all AWS services and resources in the account. This identity is called the AWS account root user and is accessed by signing in with the email address and password that you used to create the account.
Features of IAM :
Shared access to your AWS account
You can grant other people permission to administer and use resources in your AWS account without having to share your password or access key.
Granular permissions
You can grant different permissions to different people for different resources.
- Secure access to AWS resources for applications that run on Amazon EC2
You can use IAM features to securely provide credentials for applications that run on EC2 instances.
- Identity federation
You can allow users who already have passwords elsewhere
Integrated with many AWS services
For a list of AWS services that work with IAM.
Multi-factor authentication (MFA)
You can add two-factor authentication to your account and to individual users for extra security.
Main Components of IAM :
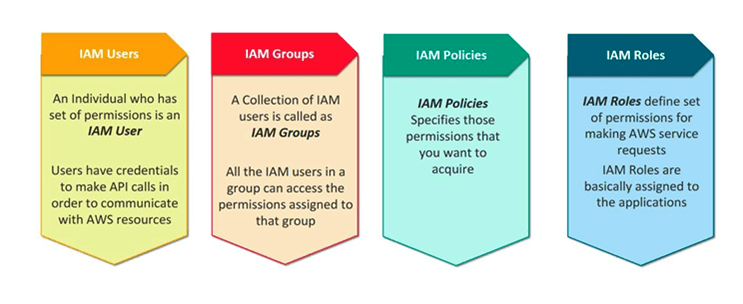
IAM User
IAM Groups
IAM Policies
IAM Roles
In the previous blog we understood how to create users, group and add users to the group and set permissions for the same.
IAM policies:
IAM policies are JSON-based statements that define access control and permissions.
IAM policies can be “inline” or “managed” and can be attached to a user or a group
Inline policies – policies that you create and manage, and that are embedded directly into a single user, group, or role.
Managed policies – standalone policies that you can manage separately from the IAM users, groups, or roles to which they are attached.
IAM Roles:
An IAM role is like a user, in that it is an AWS identity with permission policies that determine what the identity can and cannot do in AWS.
You can authorize roles to be assumed by humans, Amazon EC2 instances, custom code, or other AWS services for specific access to services.
Roles do not have standard long-term credentials such as a password or access keys associated with it, instead, when you assume a role, it provides you with temporary security credentials for your role session.
Difference between IAM Roles & IAM Users
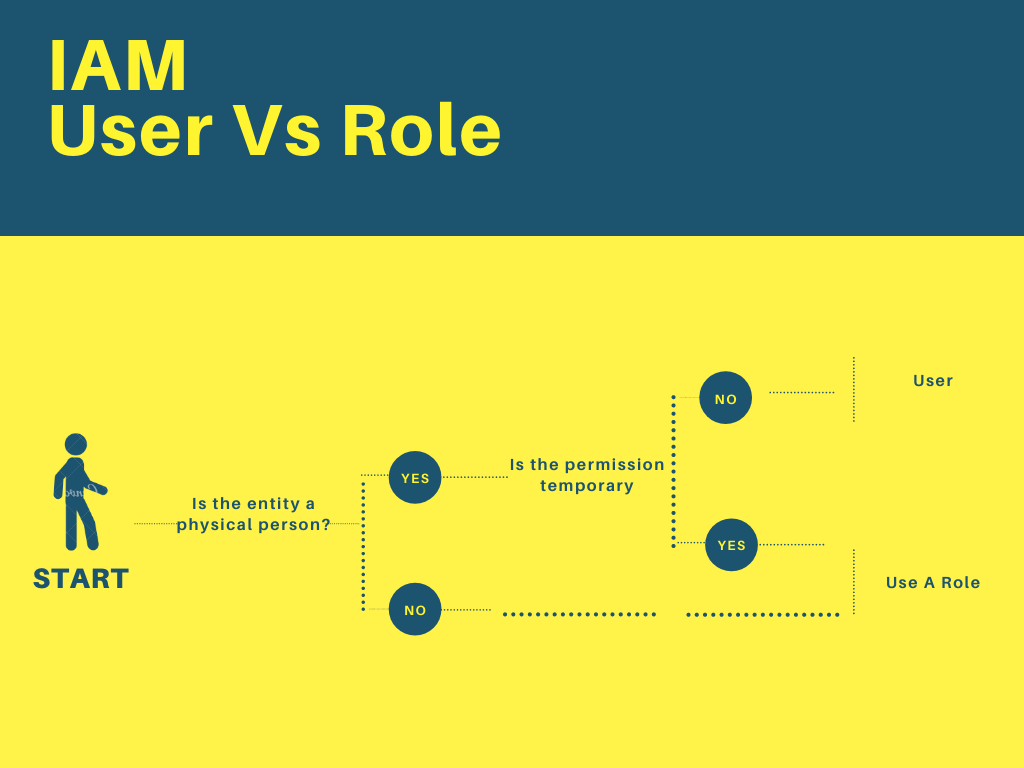
IAM Roles is not for a specific person and will have temporary permissions.
IAM User, a user is created with a specific set of permanent permissions that applies only to that person.
Why do we need IAM Roles when we have IAM Users
When we try to use the aws configure command on the terminal apart from the aws console, as a user you need to enter the access key and secret key every time we try to log in.
So, creating a role with a temporary set of permissions allows multiple members to access iam service without any access key and secret key.
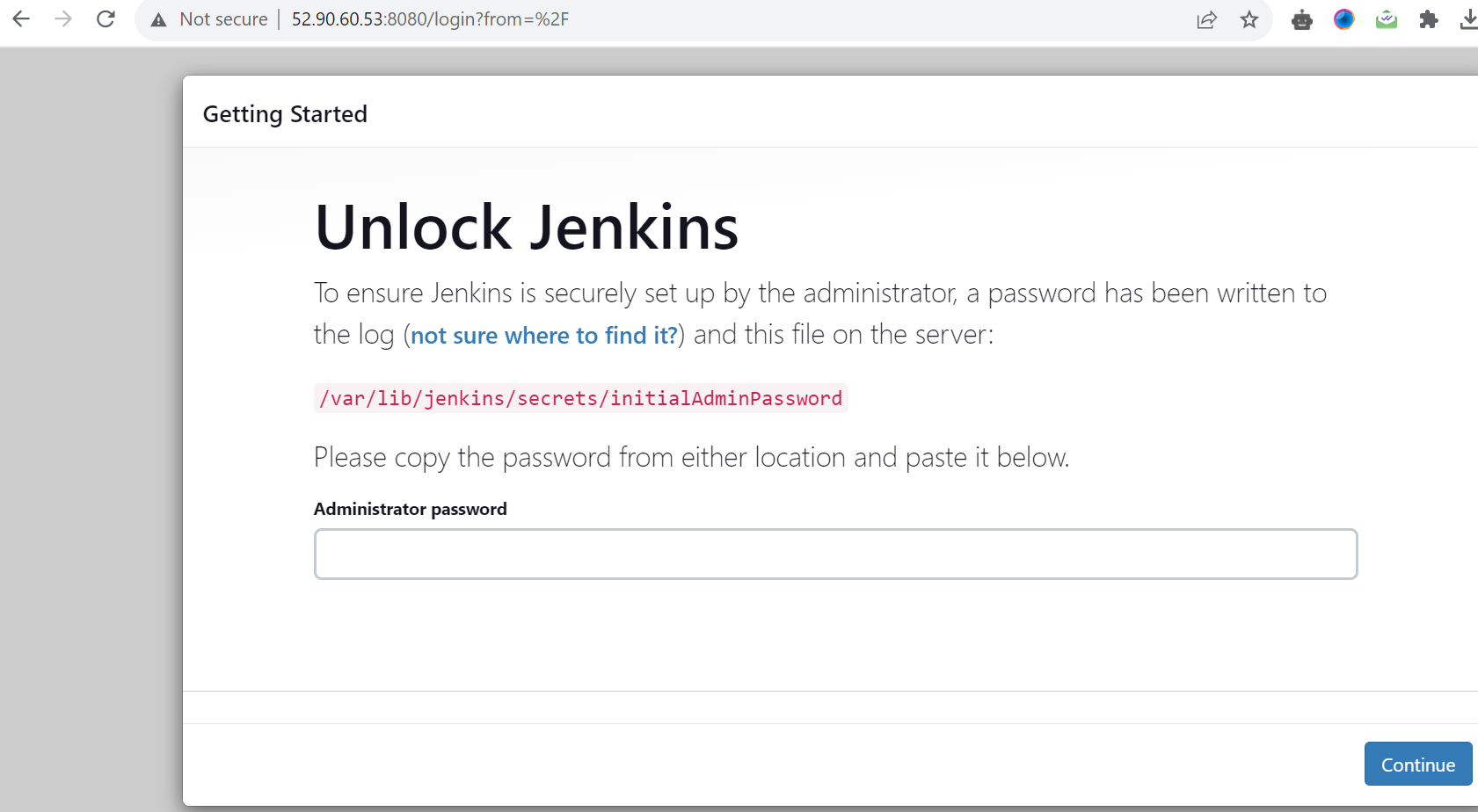
Task 1:
Launch the EC2 instance with already installed Jenkins on it. Once the server shows up in the console, hit the IP address in the browser and your Jenkins page should be visible.
Take a screenshot of the Userdata and Jenkins page, this will verify the task completion.
step 1: Launch an ec2 instance & install Jenkins through the script referred to in the previous blog.
step 2: Under the security, group add a rule for 8080 & save the rule.
Step 3: Take the public ip: 8080 on a new tab.
Task 2:
Read more on IAM Roles and explain the IAM Users, Groups and Roles in your terms.
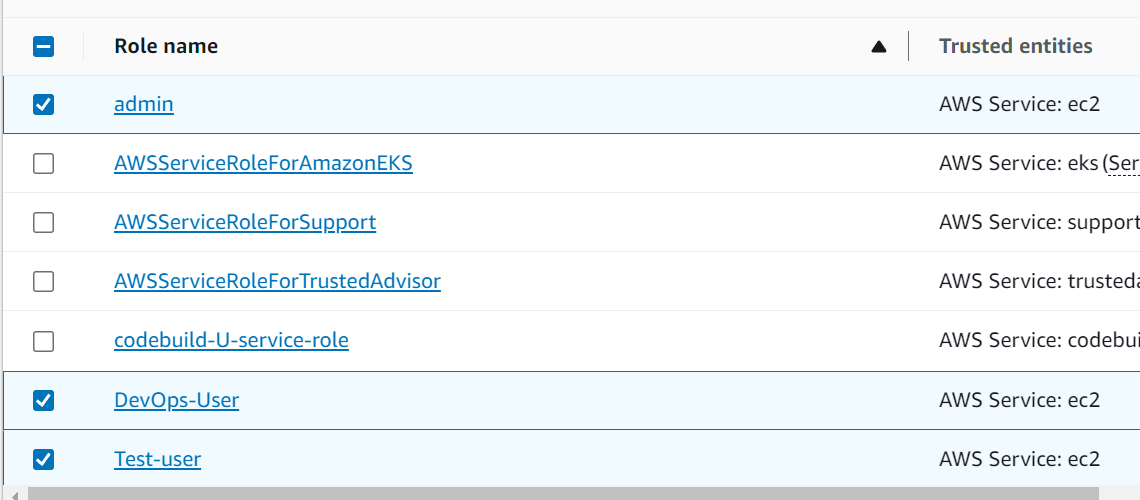
Create three Roles named: DevOps-User, Test-User and Admin.
step 1: Go to IAM services & select Roles.
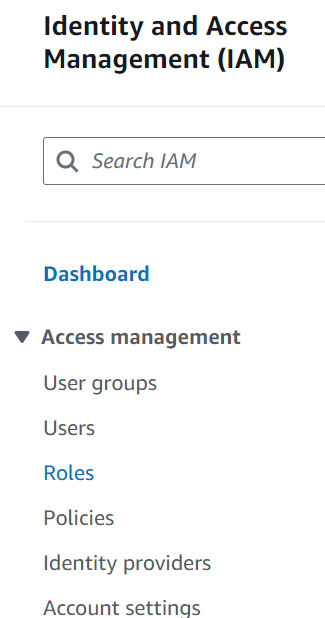
step 2: Click on Create Role.
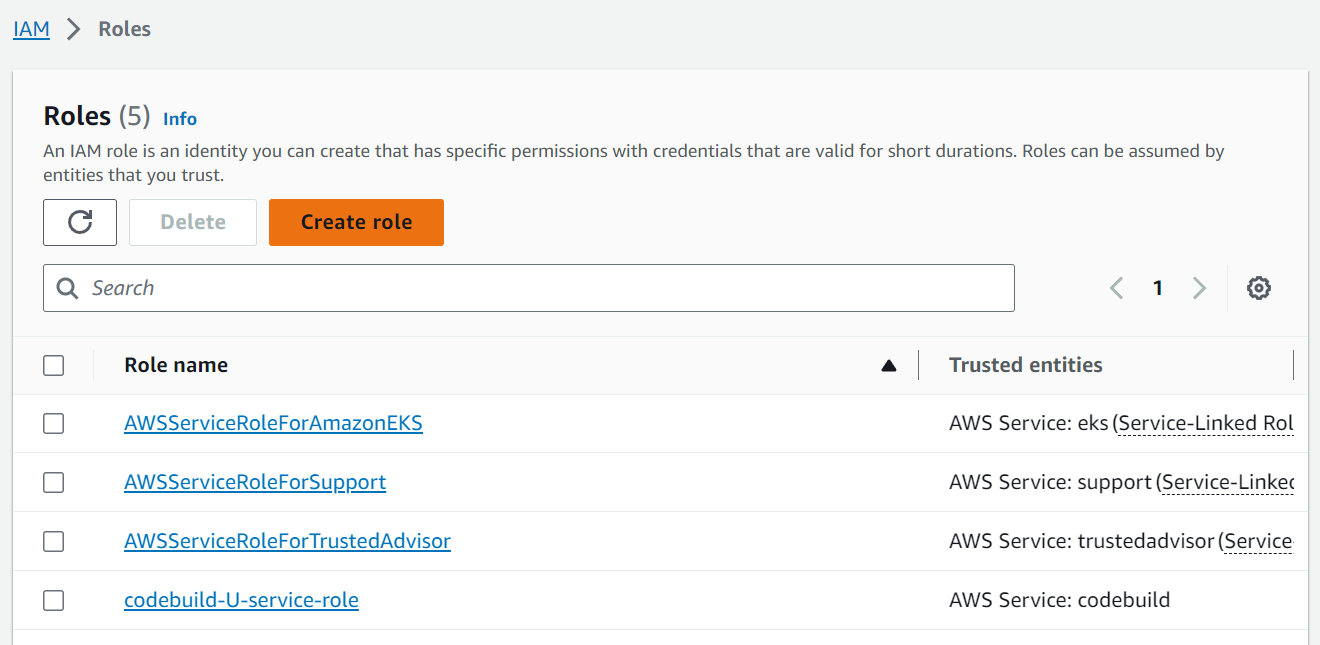
step 3: Type the name of the Role "Devop-User" and select the service.
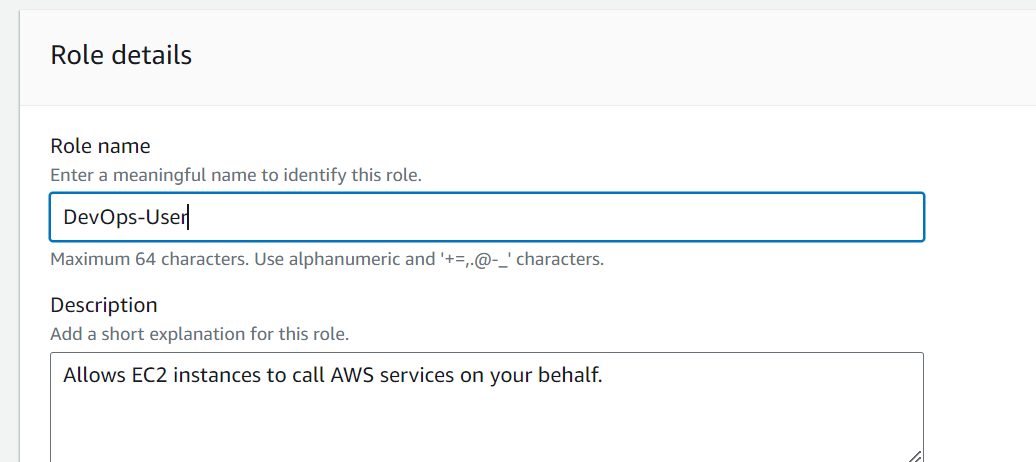
step 4: Repeat the same steps for creating the other roles as well.
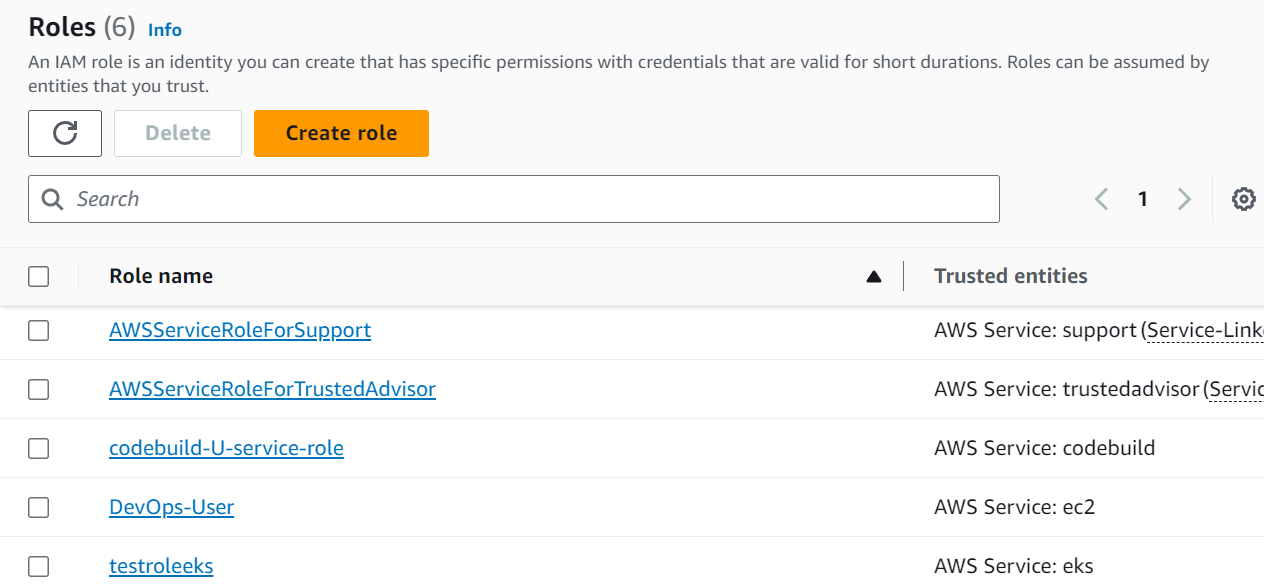
step 5: Here we have created 3 Roles - Devops-User, Test-user, admin
Subscribe to my newsletter
Read articles from sonal singh directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
