Streamline Your AWS CI/CD Workflow: Creating a CloudFormation Template for Pipeline Automatio
 Mahira Technology Private Limited
Mahira Technology Private Limited
Introduction :-
In modern #softwaredevelopment, #ContinuousIntegration and #ContinuousDeployment (CI/CD) pipelines play a crucial role in automating the build, test, and deployment processes. #CloudFormation, AWS’s #infrastructure-as-code service, allows us to define and manage our infrastructure resources using templates. In this tutorial, we will explore how to create a #CI/CD pipeline using CloudFormation and a template.yaml file.
Prerequisites:
Basic understanding of #AWS services, including AWS CodePipeline, AWS CodeBuild, and #AWS CloudFormation.
An AWS account with appropriate permissions to create and manage resources.
Step 1:- Create a folder named code-pipeline-cf in your home directory and create a template.yaml file with in the code-pipeline-cf folder.
Step 2:- create params.json files in the code-pipeline-cf directory to define the environment variables.
Step 3:- open the template.yaml file with vscode and Define the parameters and resources required for pipeline creation as shown like below.
AWSTemplateFormatVersion: '2010-09-09'
Parameters:
GitHubRepo:
Type: String
Description: Name of the GitHub repository
GitHubBranch:
Type: String
Description: Branch to trigger the pipeline
GitHubOwner:
Type: String
Description: Branch to trigger the pipeline
GitHubOAuthToken:
Type: String
Description: Branch to trigger the pipeline
Resources:
CodePipeline:
Type: AWS::CodePipeline::Pipeline
Properties:
Name: MyCICDPipeline
RoleArn: !GetAtt PipelineRole.Arn
ArtifactStore:
Type: S3
Location: my-artifact-bucket
Stages:
- Name: Source
Actions:
- Name: SourceAction
ActionTypeId:
Category: Source
Owner: ThirdParty
Provider: GitHub
Version: 1
Configuration:
Owner: !Ref GitHubOwner
Repo: !Ref GitHubRepo
Branch: !Ref GitHubBranch
OAuthToken: !Ref GitHubOAuthToken
OutputArtifacts:
- Name: SourceArtifact
RunOrder: 1
- Name: Build
Actions:
- Name: BuildAction
ActionTypeId:
Category: Build
Owner: AWS
Provider: CodeBuild
Version: 1
Configuration:
ProjectName: !Ref CodeBuildProject
InputArtifacts:
- Name: SourceArtifact
OutputArtifacts:
- Name: BuildArtifact
RunOrder: 1
RestartExecutionOnUpdate: true
PipelineRole:
Type: AWS::IAM::Role
Properties:
AssumeRolePolicyDocument:
Version: 2012-10-17
Statement:
- Effect: Allow
Principal:
Service: codepipeline.amazonaws.com
Action: sts:AssumeRole
Path: "/"
Policies:
- PolicyName: CodePipelinePolicy
PolicyDocument:
Version: 2012-10-17
Statement:
- Effect: Allow
Action:
- s3:PutObject
- s3:GetObject
- s3:ListBucket
Resource: "*"
CodeBuildProject:
Type: AWS::CodeBuild::Project
Properties:
Name: MyCodeBuildProject
ServiceRole: !GetAtt CodeBuildRole.Arn
Source:
Type: CODEPIPELINE
Artifacts:
Type: CODEPIPELINE
CodeBuildRole:
Type: AWS::IAM::Role
Properties:
AssumeRolePolicyDocument:
Version: 2012-10-17
Statement:
- Effect: Allow
Principal:
Service: codebuild.amazonaws.com
Action: sts:AssumeRole
Path: "/"
Policies:
- PolicyName: CodeBuildPolicy
PolicyDocument:
Version: 2012-10-17
Statement:
- Effect: Allow
Action:
- s3:GetObject
- s3:PutObject
Resource: "*"
Step 4:- Save the configuration and pass the environment variables in params.json files.
Step 5:- Next login to the #AWS console and navigate to the cloud formation service. Once the #CloudFormation dashboard opens, click on create stack.
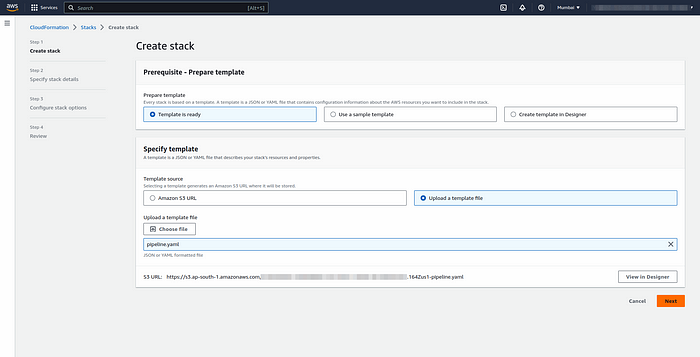
Step 6:- Upload the template file and name the stack.
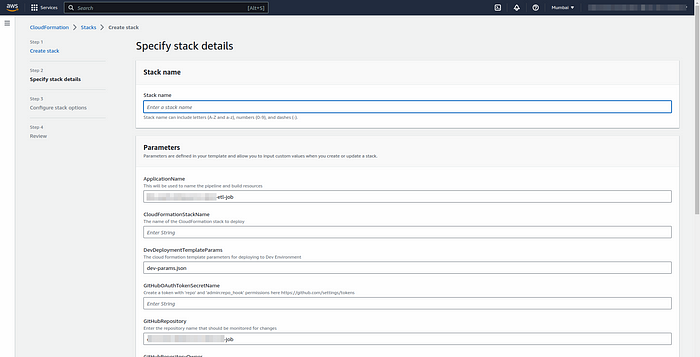
Step 7:- select the env and click on submit to create the stack.
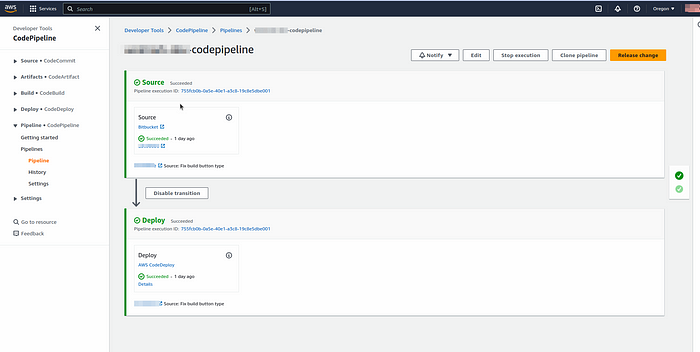
Step-8 :- After creating the stack, navigate to #code pipline and check whether the pipeline is running or not
Conclusion :-
Creating a #CI/CD pipeline using #CloudFormation and a template.yaml file allows you to define and manage your infrastructure resources in a structured and #automated manner. This approach ensures consistent and reproducible #deployments, saving time and effort in setting up and maintaining your #CI/CD workflows. By leveraging the power of #AWS services like #CodePipeline and #CodeBuild, you can achieve efficient and reliable software delivery, accelerating your #development cycles and improving overall #software quality.
Subscribe to my newsletter
Read articles from Mahira Technology Private Limited directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Mahira Technology Private Limited
Mahira Technology Private Limited
A leading tech consulting firm specializing in innovative solutions. Experts in cloud, DevOps, automation, data analytics & more. Trusted technology partner.