How to Create an S3 Bucket and Assign Full Access to One IAM User Using Terraform
 Mahira Technology Private Limited
Mahira Technology Private Limited
Introduction :-
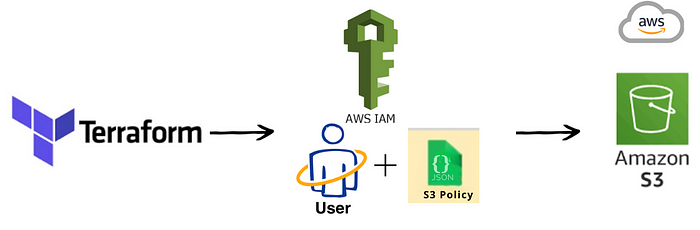
Amazon S3 is a widely used object storage service that provides industry-leading scalability, durability, and security. With #Terraform, a popular infrastructure as code (IaC) tool, you can easily create and manage S3 buckets and their associated access policies. In this blog post, we will walk you through the steps to create an S3 bucket and assign full access to one IAM user using #Terraform.
Prerequisites:
An AWS account
AWS CLI installed and configured
#Terraform installed on your machine
Step 1: Configure AWS CLI Make sure that you have configured your AWS CLI with the necessary access keys and secrets. You can check this by running the following command in your terminal:
aws configure
If you haven’t configured AWS CLI yet, you can follow the official AWS documentation to set it up.
Step 2:- Create a folder named iam-s3-bucket in your home directory, with in the folder create #Terraform configuration files such as main.tf, variable.tf, outputs.tf and provider.tf files.
- Open a visual editor and copy the below code to main.tf file to create s3 bucket and assign full access to the Iam user.
resource "aws_s3_bucket" "mahira" {
bucket = var.s3_bucket_name
}
resource "aws_s3_bucket_policy" "bucket_policy" {
bucket = aws_s3_bucket.mahira.id
policy = jsonencode({
Version = "2012-10-17"
Statement = [
{
Effect = "Allow"
Principal = {
AWS = "${aws_iam_user.mahira-user.name}"
}
Action = [
"s3:*"
]
Resource = [
"${aws_s3_bucket.mahira.arn}/*",
"${aws_s3_bucket.mahira.arn}"
]
}
]
})
}
resource "aws_iam_user" "mahira-user" {
name = var.user_name
}
resource "aws_iam_user_policy_attachment" "iam_policy" {
policy_arn = "arn:aws:iam::aws:policy/AmazonS3FullAccess"
user = aws_iam_user.mahira-user.name
}
we create an S3 bucket with the name “mahira-s3-bucket” and an IAM user with the name “mahira-user”. Finally, we attach the AmazonS3FullAccess policy to the IAM user.
open provider.tf file,In this file, we first define the AWS provider and specify the region we want to use.
terraform {
required_providers {
aws = {
source = "hashicorp/aws"
version = "3.0"
}
}
}
provider "aws" {
region = var.aws_region
}
open variable.tf file and define the variables.
variable "aws_region" {
description = "storing of region from aws console"
default = "ap-south-1"
}
variable "s3_bucket_name" {
type = string
default = "mahira-s3-bucket"
}
variable "user_name" {
type = string
default = "mahira_user"
}
define the required ouputs in output.tf file.
output "bucket_arn" {
value = aws_s3_bucket.mahira.arn
}
output "bucket_acl" {
value = aws_s3_bucket.mahira.acl
}
output "user_id" {
value = aws_iam_user.mahira-user.id
}
Step 3: Initialize #Terraform In your terminal, navigate to the directory where you saved the #Terraform file and run the following command:
terraform init
The above command will download the necessary #Terraform plugins and modules.
terraform apply
Above command will show you a summary of the changes that #Terraform is going to make. If everything looks good, type “yes” to confirm and proceed with the changes.
Step 5: Verify the S3 bucket and IAM user is being created in aws console After the Terraform apply completes successfully or else you can verify that the S3 bucket and IAM user were created by running the following commands in your terminal:
aws s3 ls s3://mahira
aws iam list-users | grep mahira-user
The first command should list the contents of the “Mahira” bucket, which should be empty. The second command should show you the details of the “mahira-user” user.
Conclusion :-
Congratulations! You have successfully created an S3 bucket and assigned full access to one IAM user using #Terraform. You can now use #Terraform to manage your S3 buckets and their associated access policies with ease.terraform destroy ==>will destroy the infrastructure created using terraform in aws
Subscribe to my newsletter
Read articles from Mahira Technology Private Limited directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Mahira Technology Private Limited
Mahira Technology Private Limited
A leading tech consulting firm specializing in innovative solutions. Experts in cloud, DevOps, automation, data analytics & more. Trusted technology partner.