Put some Ziti in your Caddy
 Eugene Kobyakov
Eugene Kobyakov
In this post I'll continue showing the power of OpenZiti and its SDK. This time I'll show you how we zitified Caddy Server.
If you're a regular reader of this blog, the concept of zitification, i.e. embedding OpenZiti SDK into you application, should be familiar to you. We've covered this topic before -- here are some links if you're new to this blog, or missed them:
Zitification allows you as a developer to achieve a true end-to-end secure overlay connectivity between your applications.
What is Caddy Server
Caddy 2 is a powerful, enterprise-ready, open source web server with automatic HTTPS written in Go
- Caddy simplifies your infrastructure. It takes care of TLS certificate renewals, OCSP stapling, static file serving, reverse proxying, Kubernetes ingress, and more.
- Its modular architecture means you can do more with a single, static binary that compiles for any platform.
These two bullet points are really important. I will show how zitifying Caddy Server simplifies your infrastructure, and how easy it was to do it with caddy server's approach to extensibility.
Simplifying Infrastructure
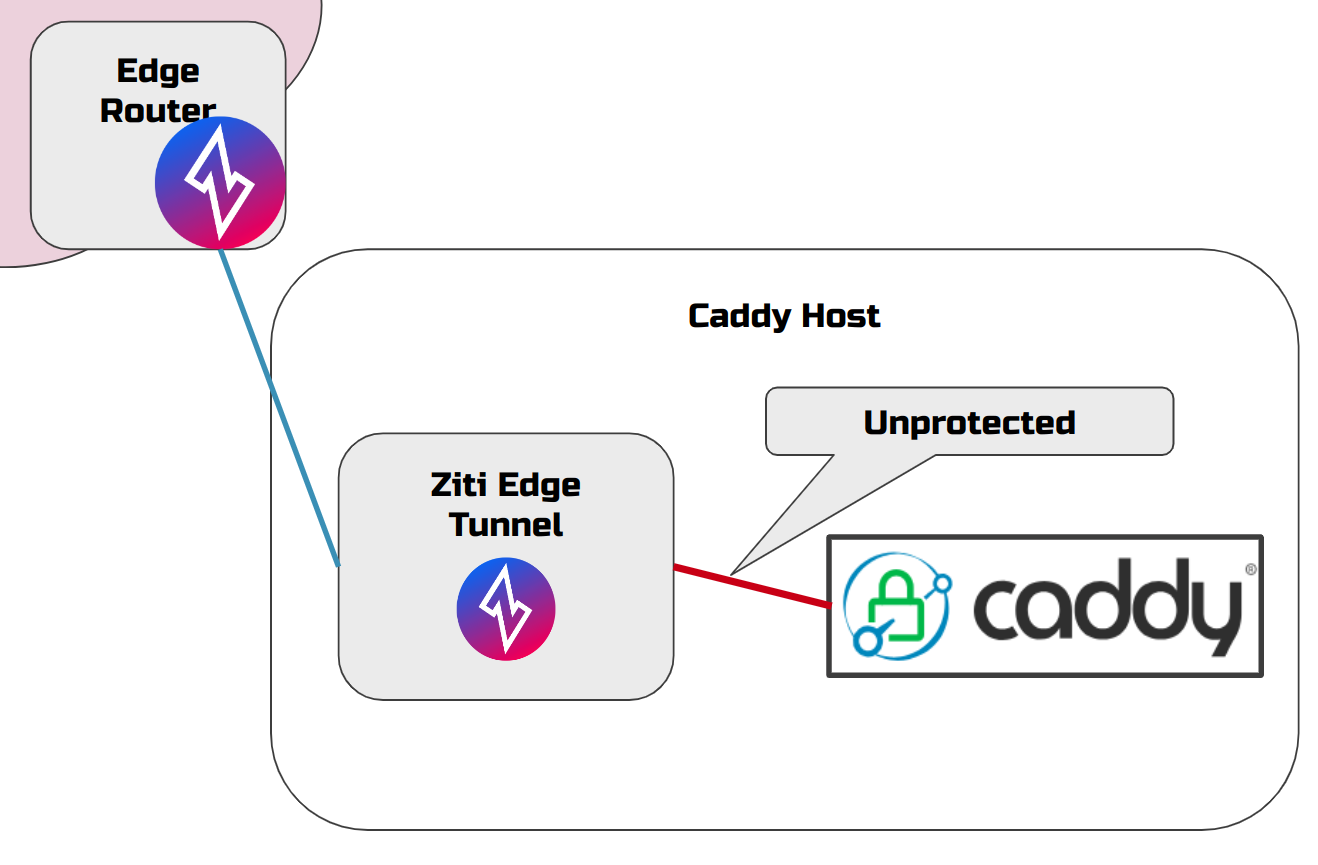
Typically, if you have a website or a web application in a data center (or at home/office), and you want to protect it from outside traffic (no open Internet ports) you need to deploy some kind of proxy agent (like Ziti Edge Tunnel) that would connect to the overlay network, accept service connection requests and proxy them to your target server. This means that
you need to maintain another piece of networking machinery
the last mile (or a few feet) of your connection goes over an unprotected overlay
common deployment with Ziti Edge Tunnel
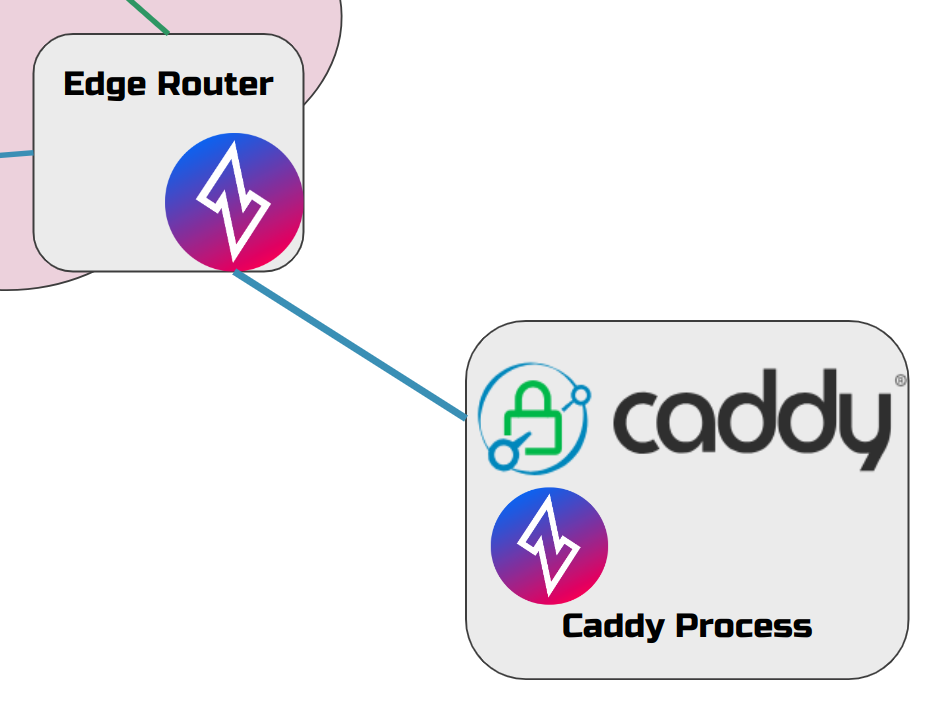
By embedding OpenZiti SDK into your server, you solve both problems at the same time.
app-embedded deployment
Caddy Server plugin
OpenZiti project published a Caddy plugin that makes it all very easy.
All you have to do is import ziti-caddy plugin in your Caddy Server main. Caddy Server plugin framework takes care of bootstrapping OpenZiti SDK (driven by configuration in Caddyfile)
Github project has a sample configuration and bootstrap, but in short steps are like this:
deploy an OpenZiti network
configure Caddy Server
http:// {
# ziti address format: ziti/<service_name>[/<terminator>]@<ziti_identity_file>
bind ziti/caddy-service@caddy-host.json
file_server {
root /usr/share/doc
browse
}
}
There you have it, two lines of code -- one in the your Go file, and one in configuration -- and you website is only accessible on OpenZiti network.
Next Steps
Try it out and give us feedback on Discourse.
Further reading:
Subscribe to my newsletter
Read articles from Eugene Kobyakov directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
