Adding HTTP Security Headers Using Lambda@Edge.
 wilmo martinez
wilmo martinez
Security is critical for web applications as they often handle sensitive user data and transactions. Security headers play a crucial role in safeguarding web applications by mitigating common vulnerabilities. AWS Lambda@Edge facilitates the implementation of these security headers by allowing us to execute custom code at the edge locations of the AWS CloudFront CDN.
What are security headers
HTTP security headers are a subset of HTTP headers that are related specifically to security. They are exchanged between a client (usually a web browser) and a server to specify the security details of HTTP communication.
The most important HTTP security headers
Content-Security-Policy: is a crucial security header that helps prevent cross-site scripting (XSS) and data injection attacks. It defines which resources (e.g., scripts, images, styles) can be loaded and executed on a web page. It limits the sources from which content can be loaded, enhancing security.
Strict-Transport-Security(HSTS): HSTS instructs web browsers to enforce secure HTTPS connections for a specified duration, protecting users from potential man-in-the-middle attacks and ensuring all communication with your website is encrypted.
X-Content-Type-Options: This header prevents browsers from interpreting files as a different MIME type than declared, which can help mitigate attacks like MIME sniffing. Setting it to "nosniff" enhances security by reducing the risk of content-type confusion.
XFrame-Options: X-Frame-Options prevents your web pages from being embedded in frames or iframes on other websites. This guards against clickjacking attacks, where attackers attempt to trick users into performing actions without their knowledge.
Referrer-Policy: Referrer-Policy controls what information is included in the HTTP Referer header when a user clicks on a link. This can help protect user privacy and limit the exposure of sensitive information.
X-XSS-Protection: This header is designed to block or sanitize potential cross-site scripting (XSS) attacks in the browser. Enabling this header helps protect users by preventing malicious scripts from executing.
What is lambda edge how it can help us?
Lambda@Edge provides the ability to execute a Lambda function at an Amazon CloudFront Edge Location. This capability enables intelligent processing of HTTP requests at locations that are close (for latency) to your customers. You can run a Lambda@Edge function in response to four different CloudFront events.
Some of the use cases :
Dynamic Content Delivery
Security and Compliance
Real-time Image Optimization
Bot Detection and Mitigation
User Authentication and Authorization
How it works?
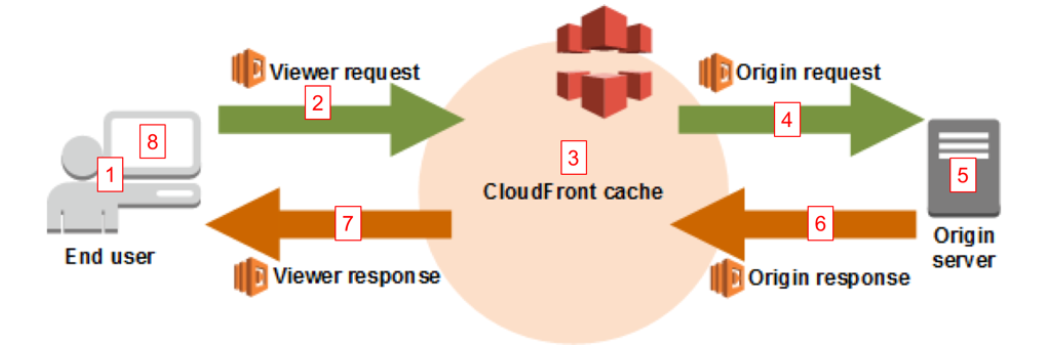
The viewer navigates to the website.
Before CloudFront serves content from the cache it will trigger any Lambda function associated with the Viewer Request trigger for that behavior.
CloudFront serves content from the cache if available, otherwise, it goes to step
Only after CloudFront cache ‘Miss’, Origin Request trigger is fired for that behavior.
S3 Origin returns content.
After content is returned from S3 but before being cached in CloudFront, Origin Response trigger is fired.
After content is cached in CloudFront, Viewer Response trigger is fired and is the final step before the viewer receives content.
Viewer receives content.
Conclusion
In this section, we covered the essentials of Lambda@Edge and web security headers. In the second part of this article, We will explore the practical aspects of implementing a Lambda function to improve your online security.
Subscribe to my newsletter
Read articles from wilmo martinez directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

wilmo martinez
wilmo martinez
Hello! I'm a Cloud Engineer passionate about finding and solving challenges in the ever-evolving world of cloud tech, especially AWS. Constantly learning, I'm here to share my experiences and insights. Let's dive into this journey together!