Exploiting & Remediating WordPress’ User Enumeration Vulnerability.
 Tonny Gitonga
Tonny Gitonga
Introduction.
WordPress is a popular content management system (CMS) that is used to create websites and blogs. It is a free and open-source software.
WordPress contains a known username enumeration vulnerability that can be exploited if a malicious hacker finds the admin URL of a WordPress-powered website. This is a security concern because according to W3Techs, WordPress powers over 43.1% of all websites on the internet. This means that over two out of every five websites are built using WordPress and thus have this vulnerability.
Preliminary Task: Enumerating the admin URL of your target site.
One would first need to get a target website’s admin URL. Some of the most commonly used admin URLs are:
mywebsite.com/wp-adminmywebsite.com/adminmywebsite.com/wp-login.phpmywebsite.com/login
This is bad practice as one could easily get access to your website’s admin log-in page. A good number of WordPress-powered websites use unique names to make it harder to enumerate & access the admin log-in pages.
On Linux, you can install a WordPress using docker-compose to test, exploit and remediate this vulnerability.
Docker Compose allows the use of multiple docker containers in orchestration at once without having to manually set up those connections.
It’s recommended [though not mandatory] that you install them in a Linux server that is networked to your Linux machine. Use VMs in this case.
What does this vulnerability look like?
Once an attacker has access to your admin log-in page, they can enumerate the username(s) used to log in and later on enumerate the password(s).
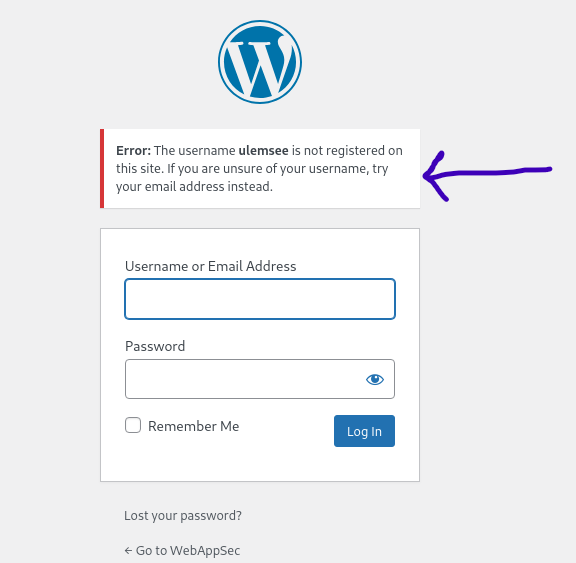
As you can see, WordPress displays an error notifying the user that the entered username is not registered.
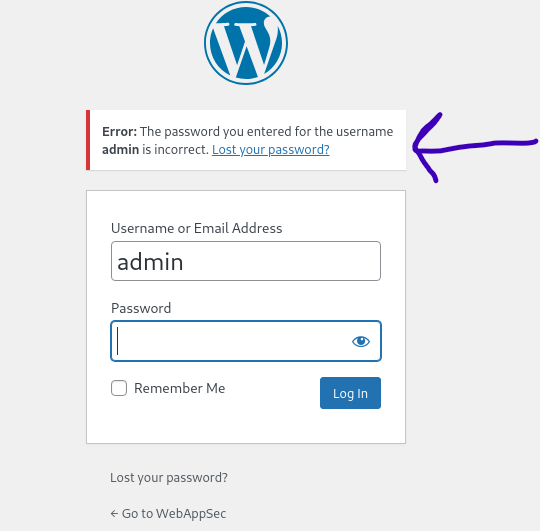
When you enter a correct username with a wrong password, WordPress will notify you that the password for the entered username is incorrect. This is a vulnerability that can be exploited by attackers.
How can this vulnerability be exploited?
This can be executed via fuzzing to check which username will bring back a message without 'not registered' in the body by using regex while sending the fuzzed request.
A suitable tool for this use case is OWASP ZAP.
Procedure.
Open ZAP and then the WordPress login page. Make sure you’ve set up a proxy.
Refresh the login page and add the website as a new Context.
Perform a Spider scan, this will reveal a lot of URLs linked to the website. One of them will be a POST request sent by ZAP when it was trying to log in.
Add your payload; list of potential usernames.
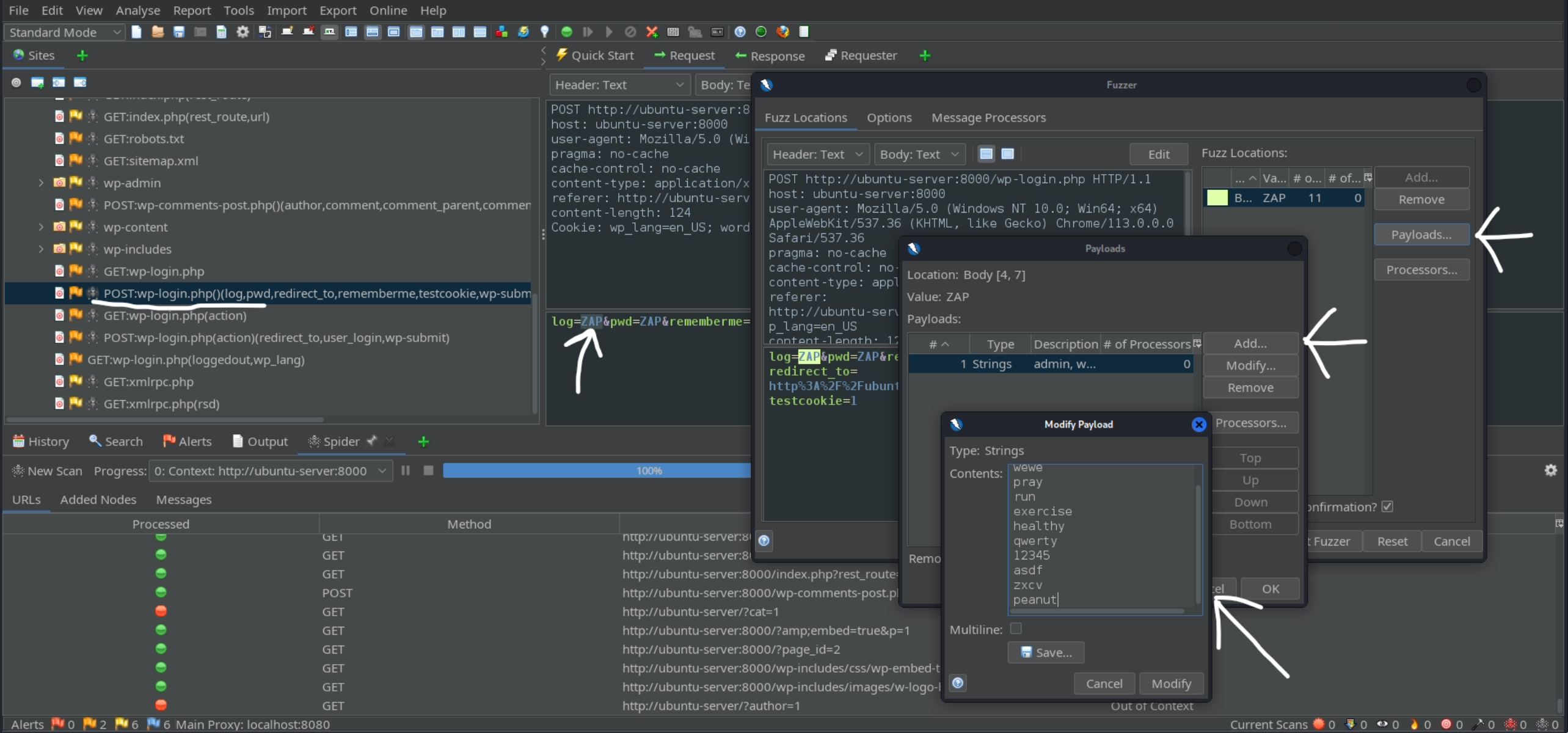
- Use regex to check for ‘not registered’ and return ‘Incorrect Username’ for the entries that display it. Then fuzz that request.
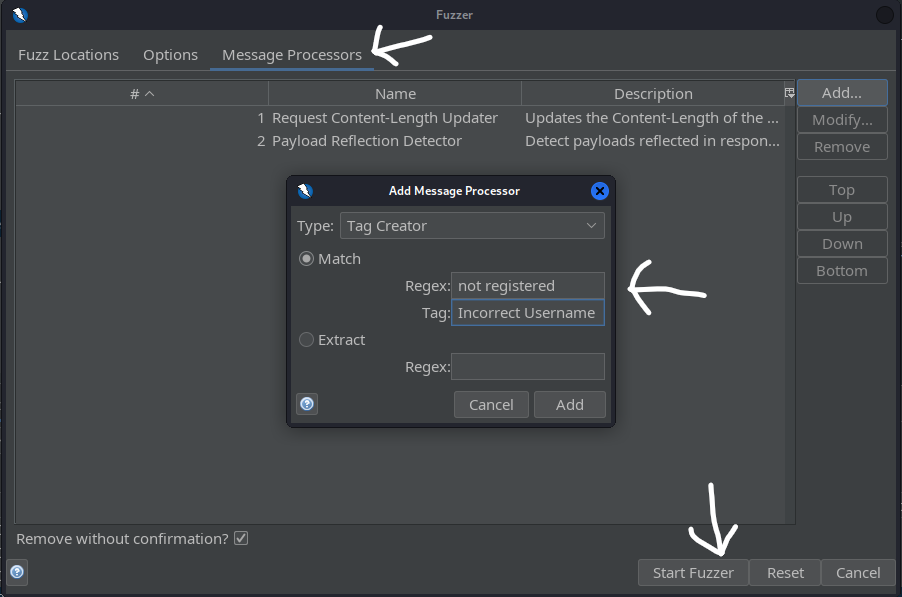
- Check for the response that does not return ‘Incorrect Username’. That is the username used to log in.
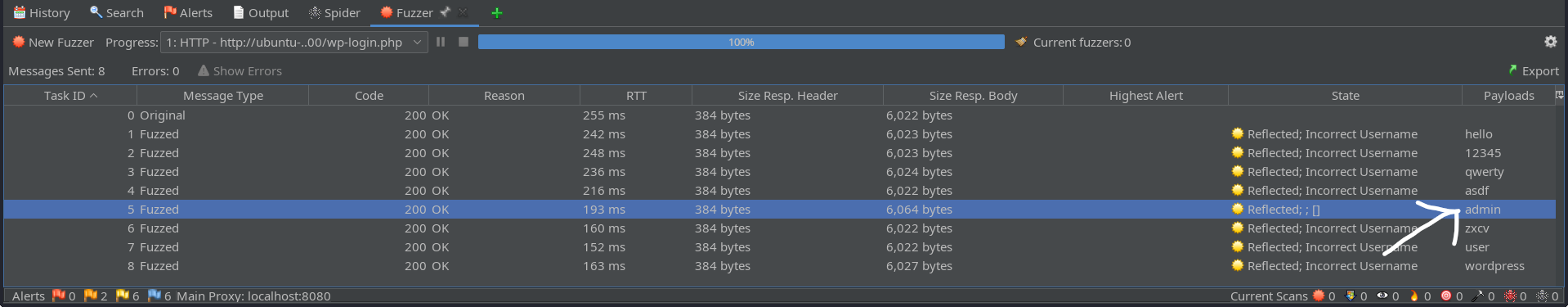
Locate the correct username based on the response
- After finding the correct username, the attacker will repeat the fuzzing process by using a payload (upload a custom list or use the ones in ZAP) to enumerate the password. If one of the entries in the fuzzed list returns a 302 (redirect), then that's the correct password.
This is how WordPress accounts can be easily accessed especially if the user uses common credentials.
How can you remediate this vulnerability?
Step 1: Using a strong password and a unique username.
The username should not be related to the website’s contents and should not be a common credential such as admin and user.
You can opt to use a username with a combination of different characters.
The password should be at least 8 characters long and should include all the different types of characters such as qA45&p?Hty6
Implementing this will make it harder to brute force and obtain the login credentials.
Step 2: Add the ‘Login Lock Down’ plugin to your WordPress Website.
Login Lockdown Plugin
This plugin offers a lot of useful security features that protect against unauthorized access including tackling the vulnerability being discussed here.
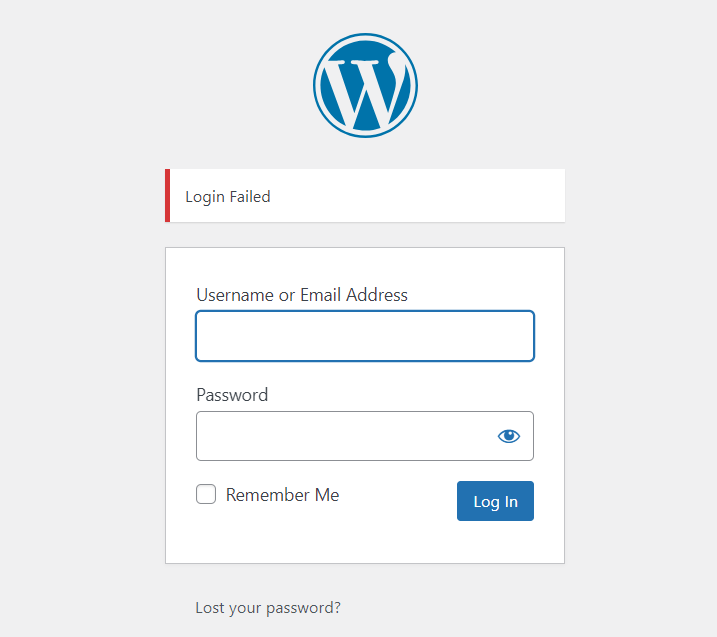
It will always display ‘Login Failed’ only for all incorrect entries.
It also has a couple of other useful features:
Limiting the number of failed login attempts.
Blocking suspicious IP addresses.
Logs.
Lockout Whitelisting [Paid]
Requiring two-factor authentication. [Paid]
Use of Captcha. [Paid]
This is how the log-in page will look like after adding the Login Lock Down plugin and activating the ‘Mask Login Errors’.
Subscribe to my newsletter
Read articles from Tonny Gitonga directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
