Linux Firewalld Setup
 Samson Oladipo
Samson Oladipo
Task Requirements :
To secure our infrastructure in the Datacenter we have decided to install and configure Firewalld on all app servers. We have Apache and Nginx services running on these apps. Nginx is running as a reverse proxy server for Apache. We might have more robust firewall settings in the future, but for now, we have decided to go with the given requirements listed below:
Allow all incoming connections on the Nginx port, i.e. 80.
Block all incoming connections on Apache port, i.e. 8080.
All rules must be permanent.
The zone should be public.
If Apache or Nginx services aren't running already, please make sure to start them.
Execution :
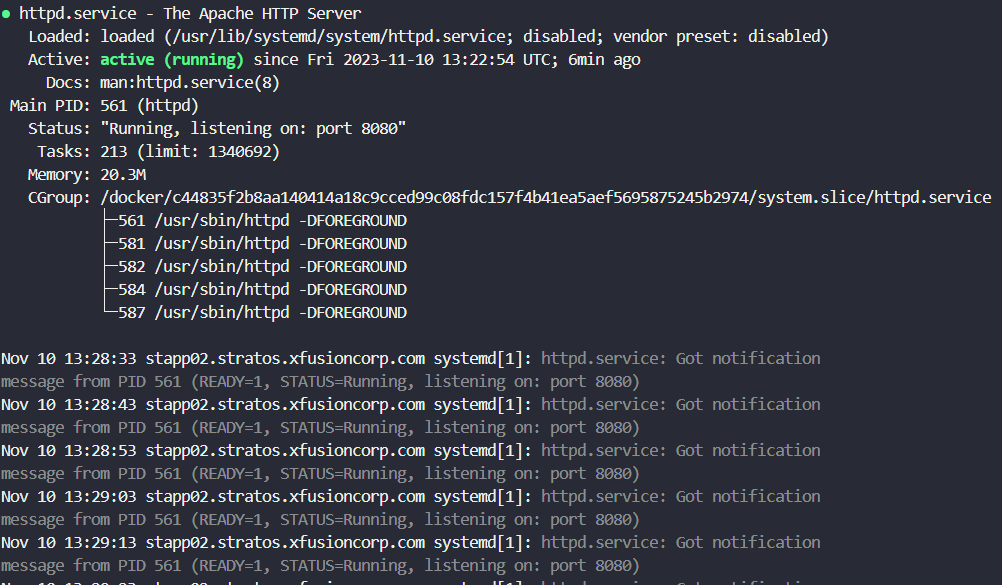
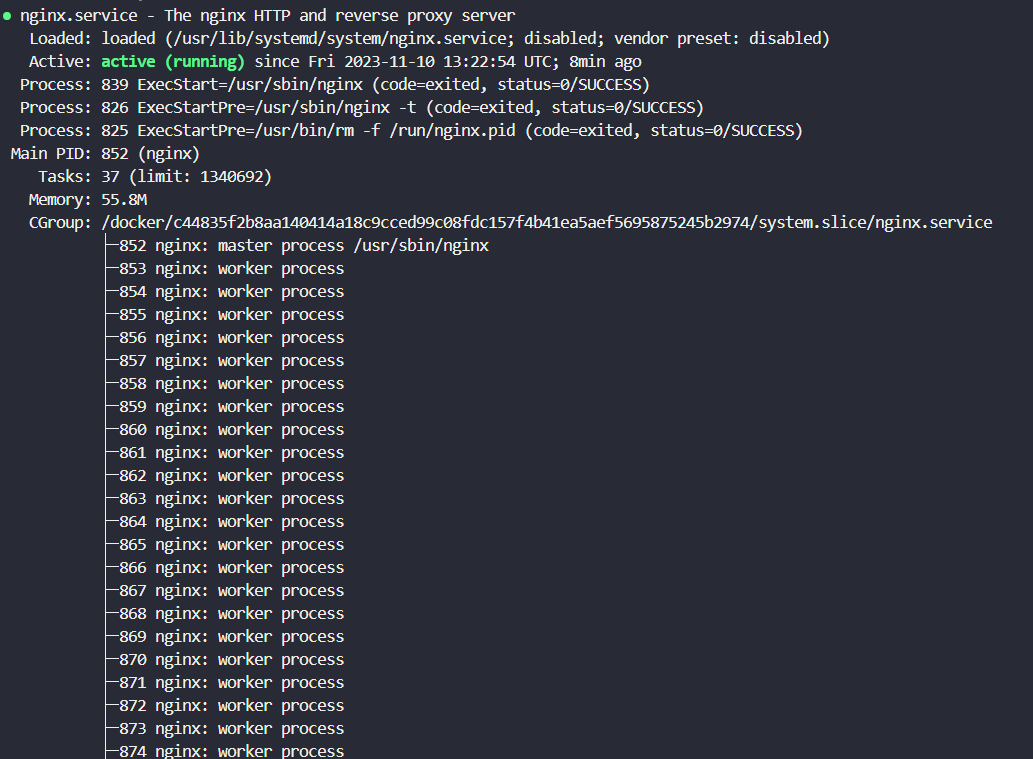
We need to check if the Apache & Nginx services are running, to know run these commands for Rhel and Cent-os Linux distribution.
sudo systemctl status httpd
sudo systemctl status nginx
As the case maybe if it's not running, kindly start them by running these commands, and make sure they are running.
sudo systemctl start httpd
sudo systemctl status httpd
sudo systemctl start nginx
sudo systemctl status nginx
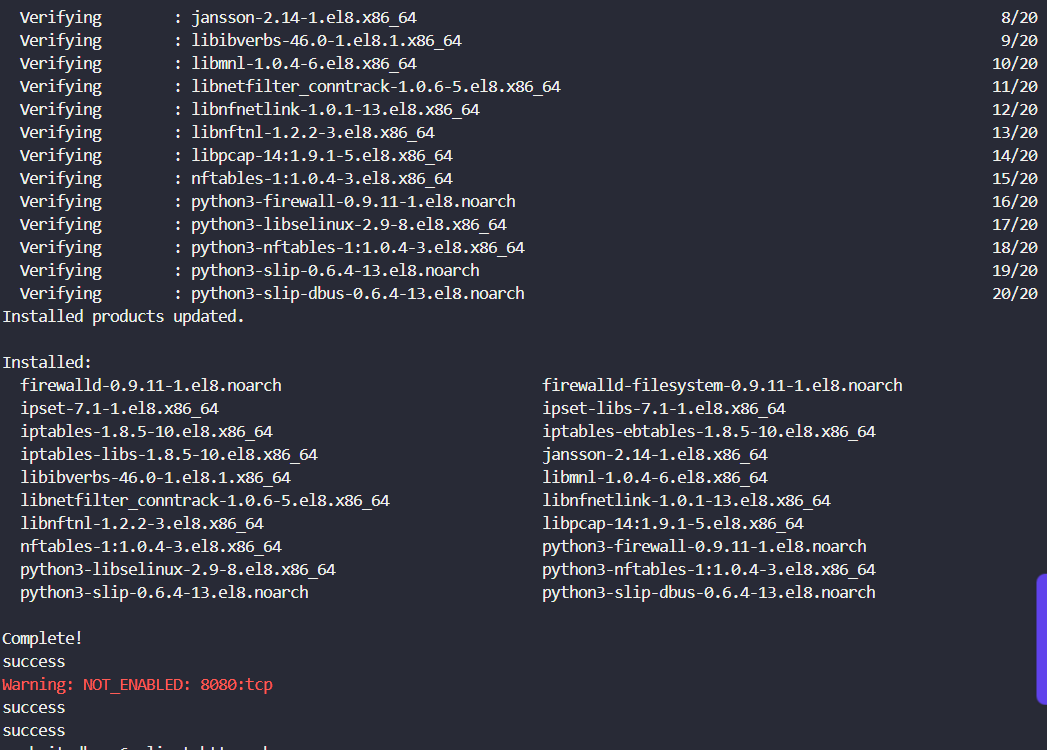
Once that has been sorted, we install the Firewalld package and set the rules to;
Allow all incoming connections on Nginx port 80 and block all incoming connections on Apache port 8080.
Also making the rules permanent even after an app server restarts/reboots.
Since we are to execute this task across different app servers in the datacenter, a bash script can be created to execute the task required accordingly across all app servers, here is the sample of the script used.
#!/bin/bash
#Start Apache (assuming systemd)
sudo systemctl start httpd
sudo systemctl status httpd
#Start Nginx (assuming systemd)
sudo systemctl start nginx
sudo systemctl status nginx
#Install firewalld
sudo yum install firewalld -y
sleep 7s
#Initialize and start firewalld (assuming systemd)
sudo systemctl enable firewalld
sudo systemctl start firewalld
#Allow incoming connections on Nginx port (80)
sudo firewall-cmd --permanent --zone=public --add-service=http
#Block incoming connections on Apache port (8080)
sudo firewall-cmd --permanent --zone=public --remove-port=8080/tcp
#Reload firewall settings to apply changes
sudo firewall-cmd --reload
#Display active zones
sudo firewall-cmd --get-active-zones
#List services allowed in the public zone
sudo firewall-cmd --zone=public --list-services
Subscribe to my newsletter
Read articles from Samson Oladipo directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Samson Oladipo
Samson Oladipo
DevOps enthusiast sharing real-world insights. 🚀 #Automation #CI/CD #InfrastructureAsCode