BelkaCTF #4: Kidnapper Case
 Ohekpeje Joel Odey
Ohekpeje Joel Odey
I performed and completed this challenge in 2002 for a coursework in Cyber Forensics, just coming around to uploading it on my blog in 2023.
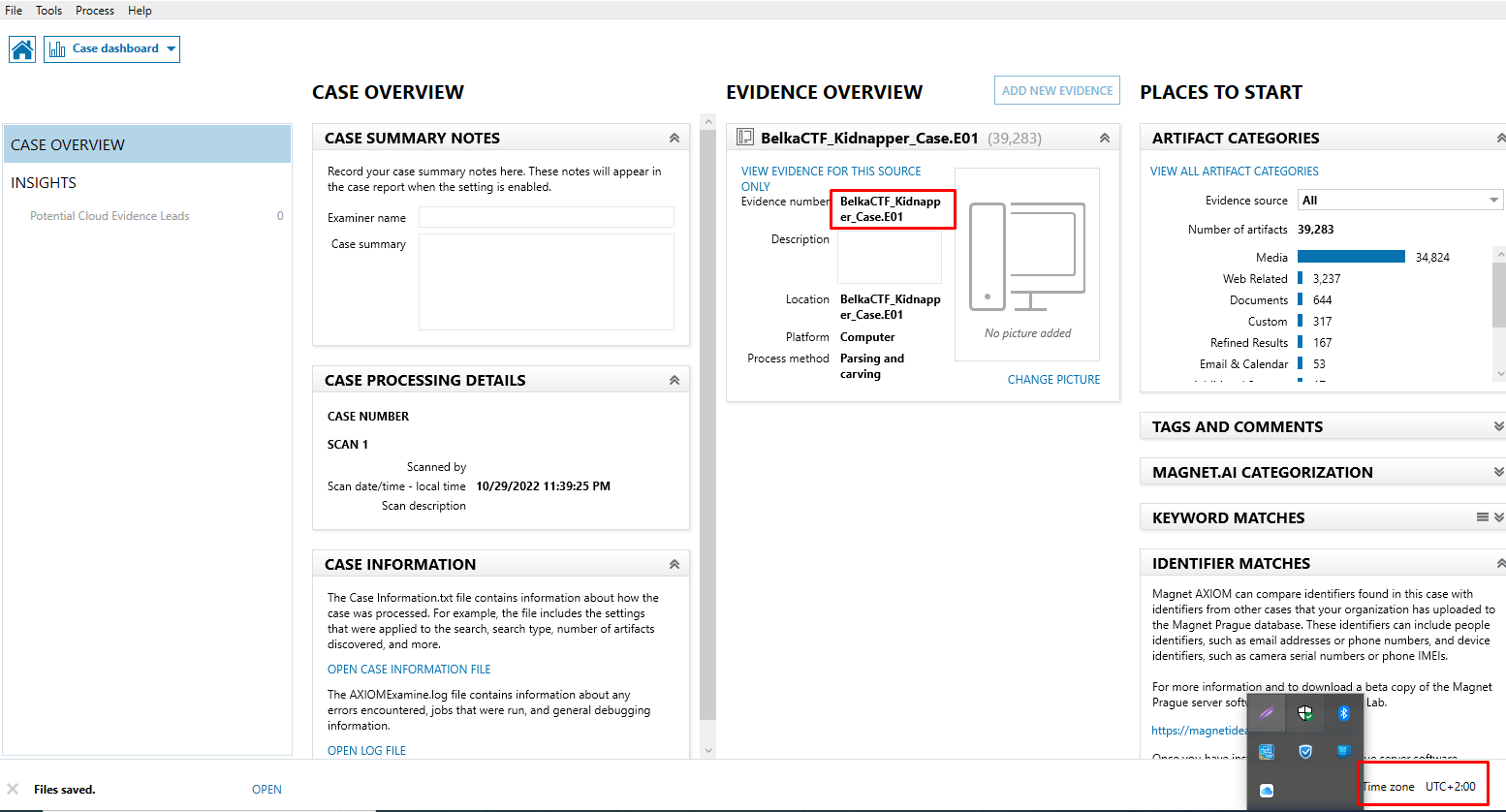
List all users of the laptop
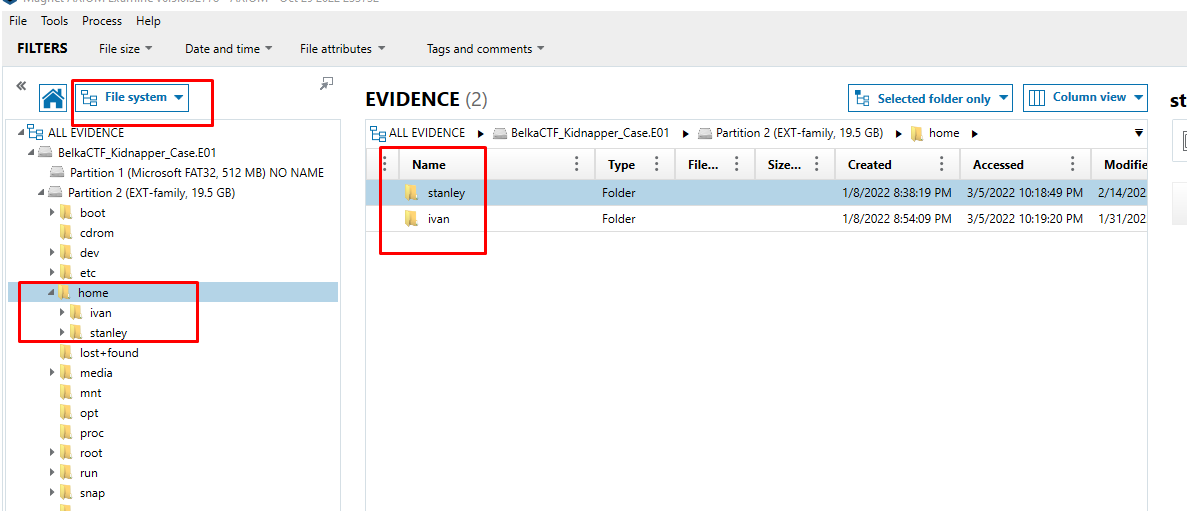
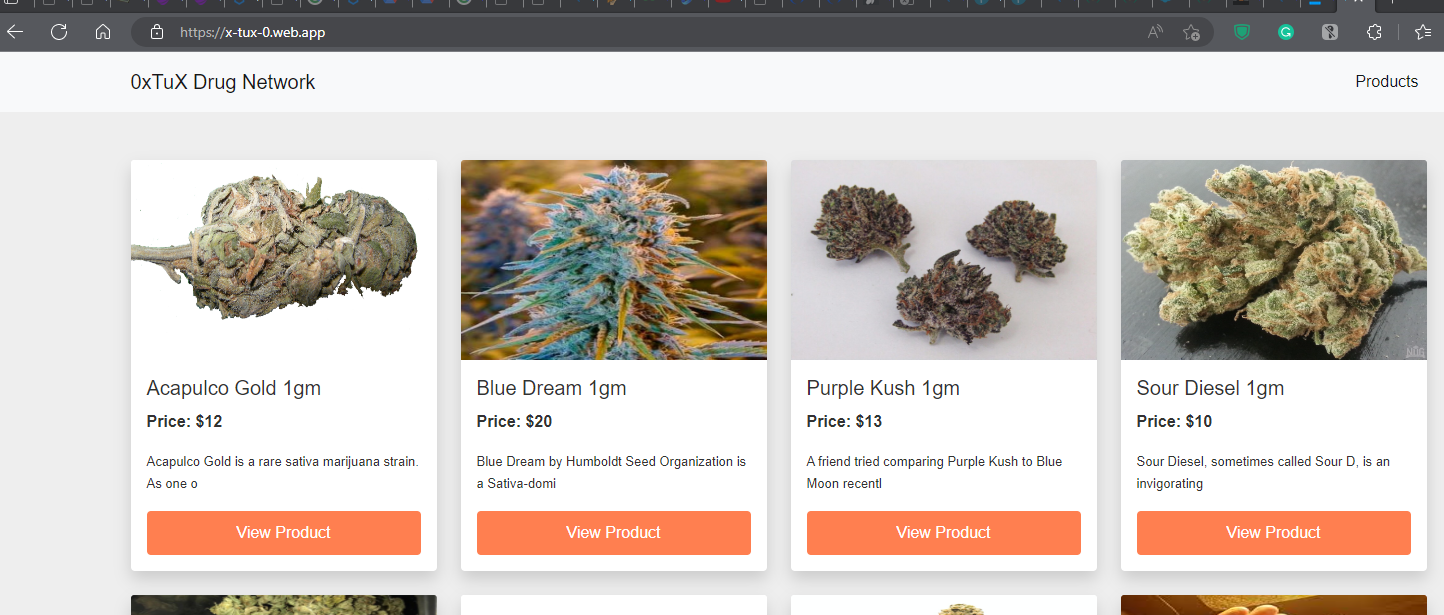
What web application was used by the boy to earn his pocket money?
A simple scan of the Firefox web history indicates several hits for x-tux-0.web.app. There are some intriguing goods for sale, as we can see.
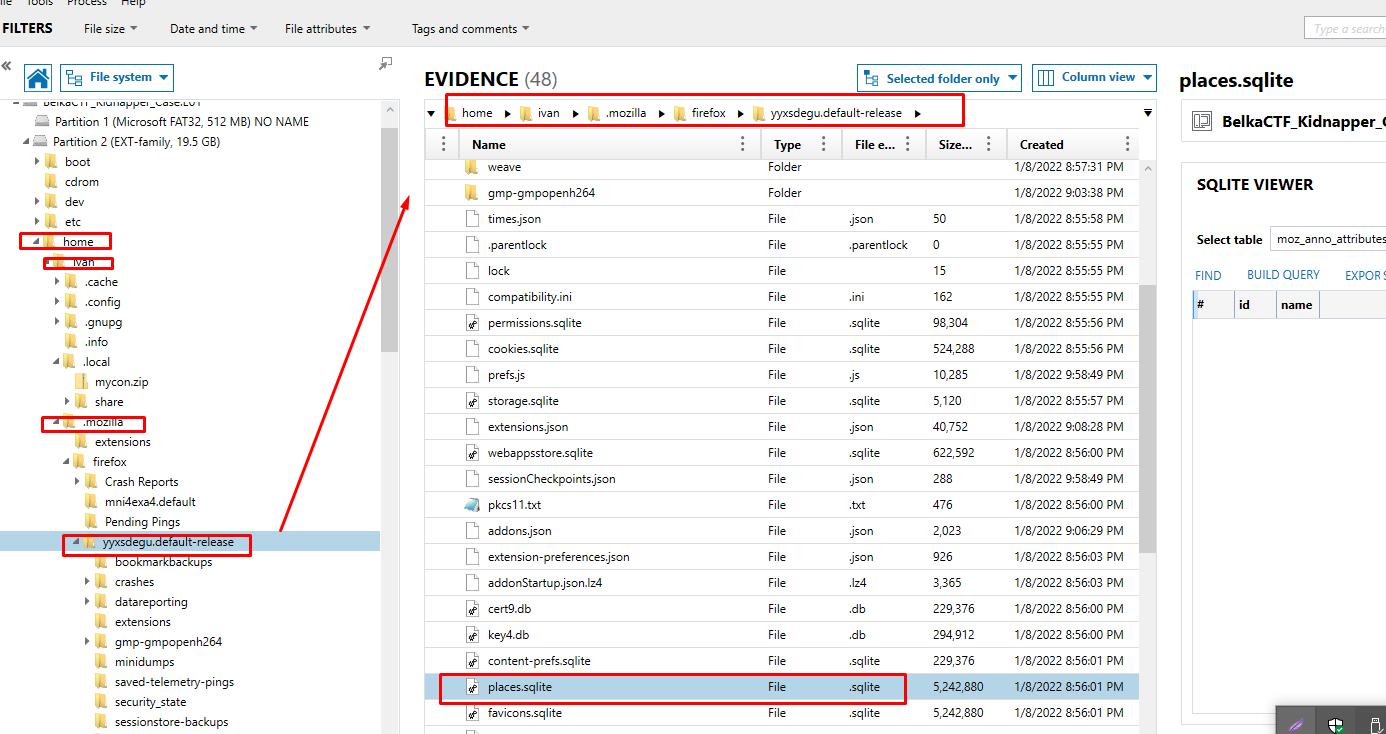
Open places.sqlite with Visual studio SQL Lite and you will find the web application.
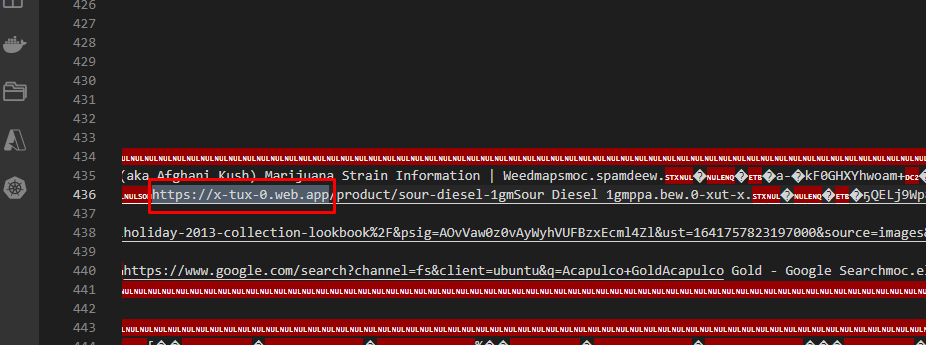
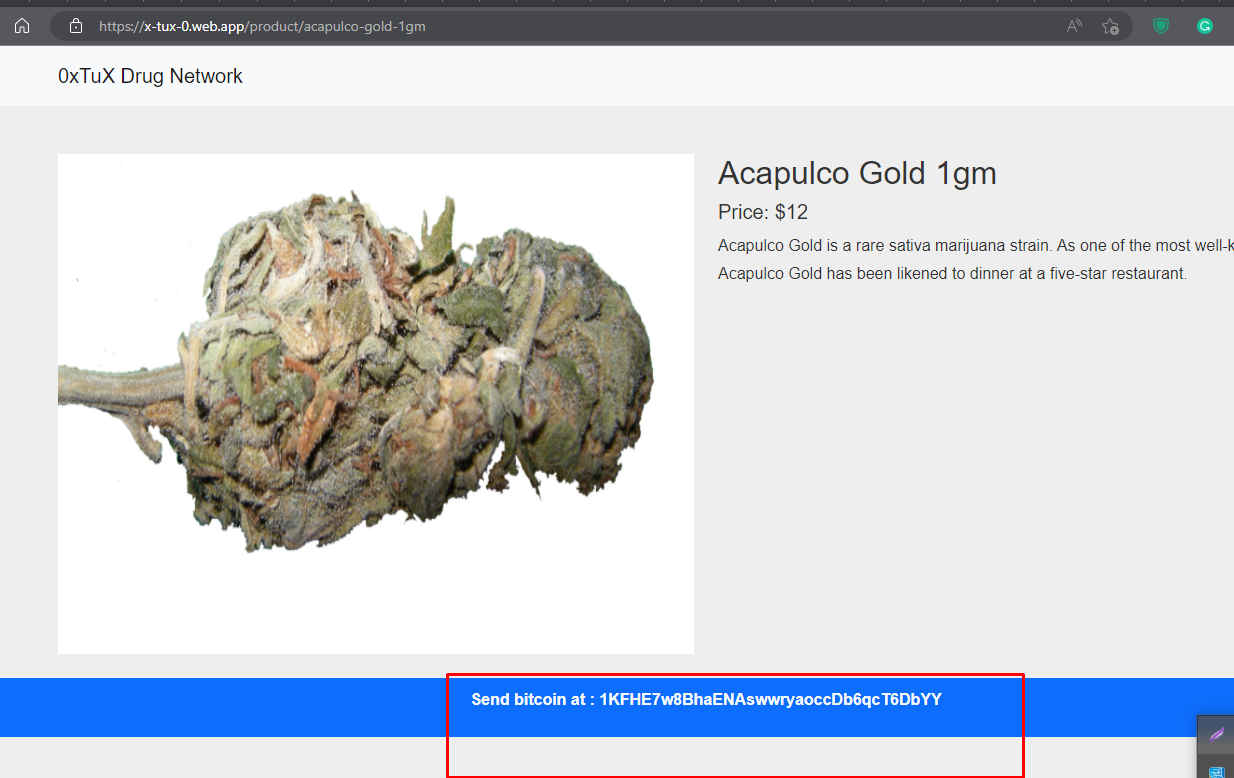
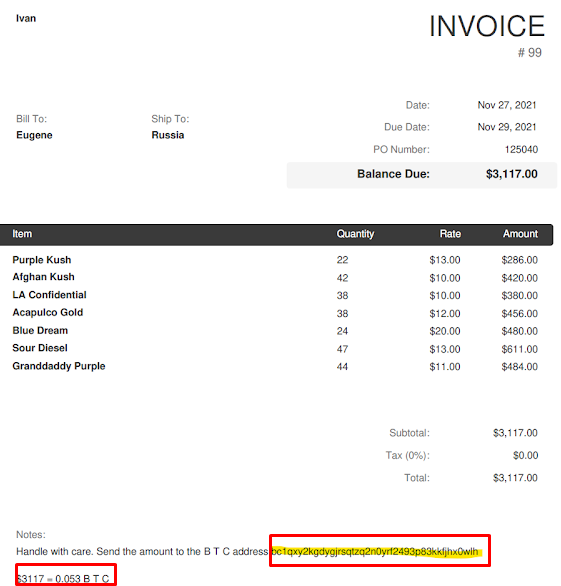
Which BTC wallet did the boy use to sell drugs?
Visiting the link for the above task https://x-tux-0.web.app you will access the drug dealer's business page with his wallet address.
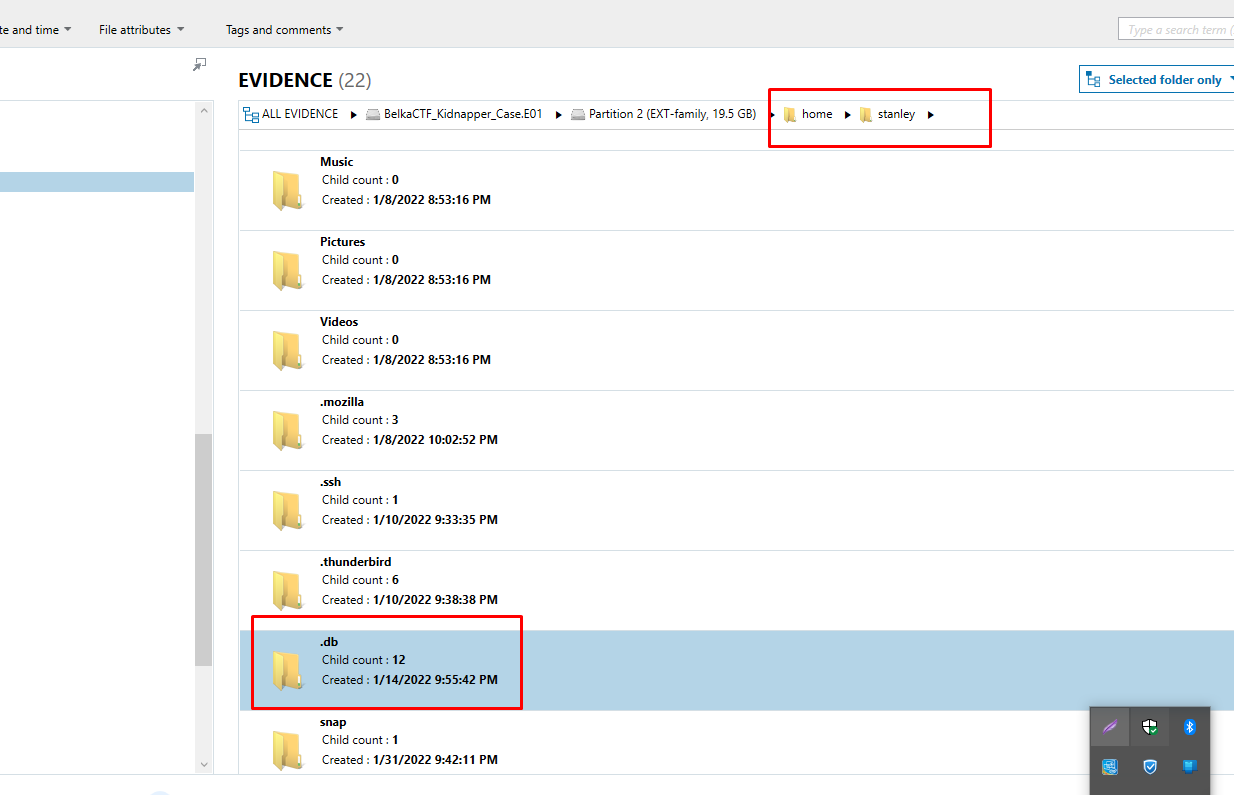
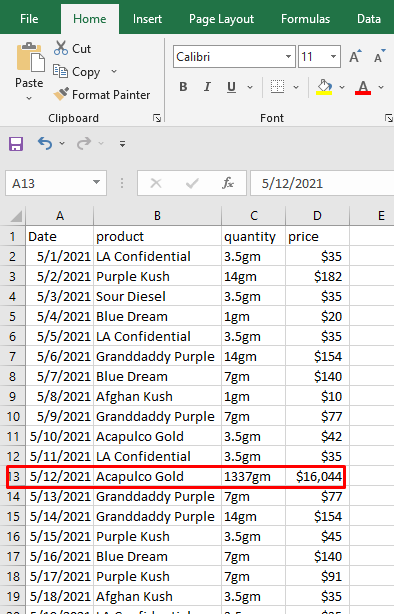
On which date does the kid's database show the most sales for "Acapulco Gold"?
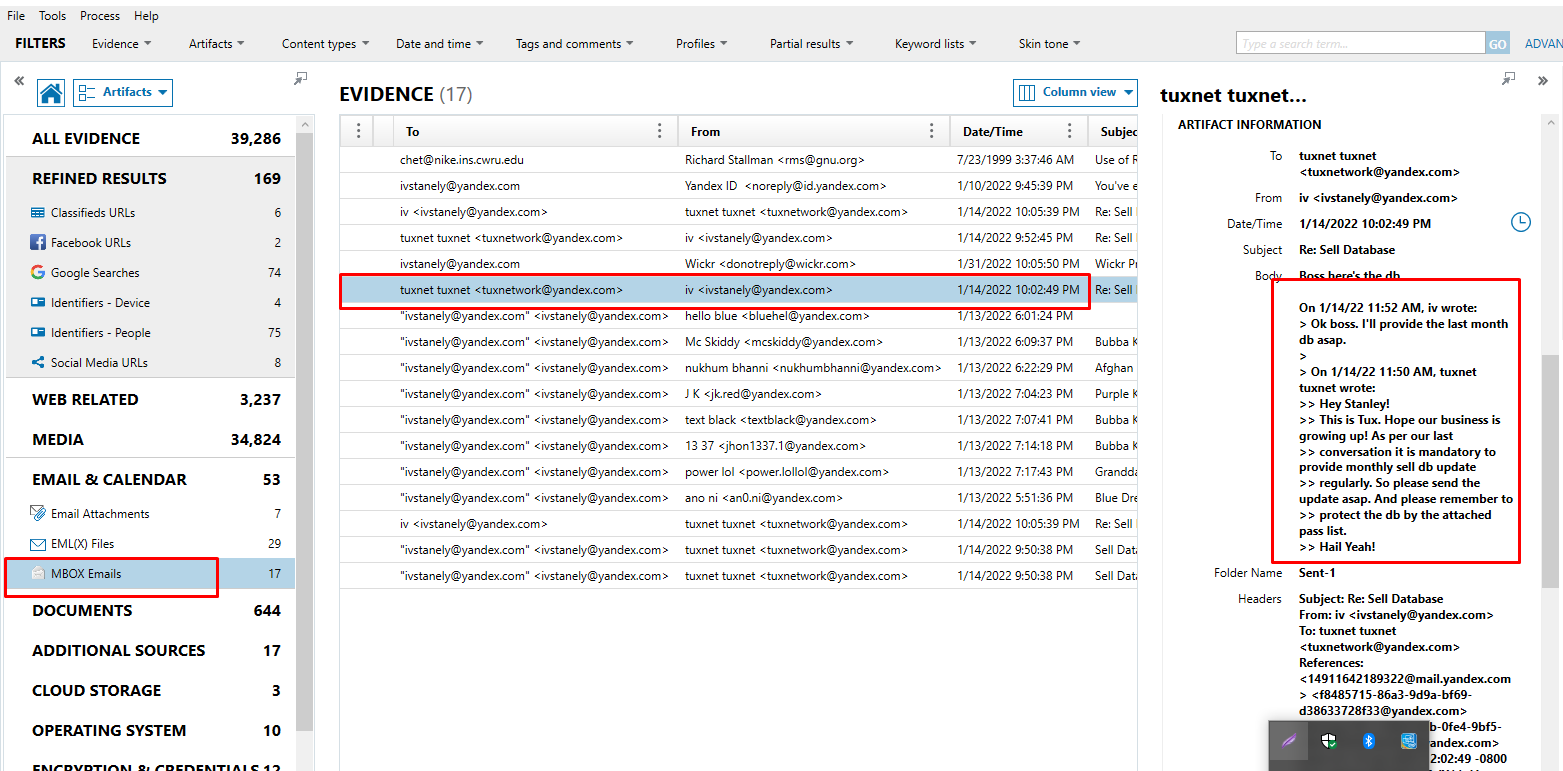
There are several talks from a "Tux" with the subject "Sell Database" after going through email communications.
In the chat, the victim asks his friend Tux for his monthly sales, most likely to keep track of his drug supplies and the money he makes from his sales.
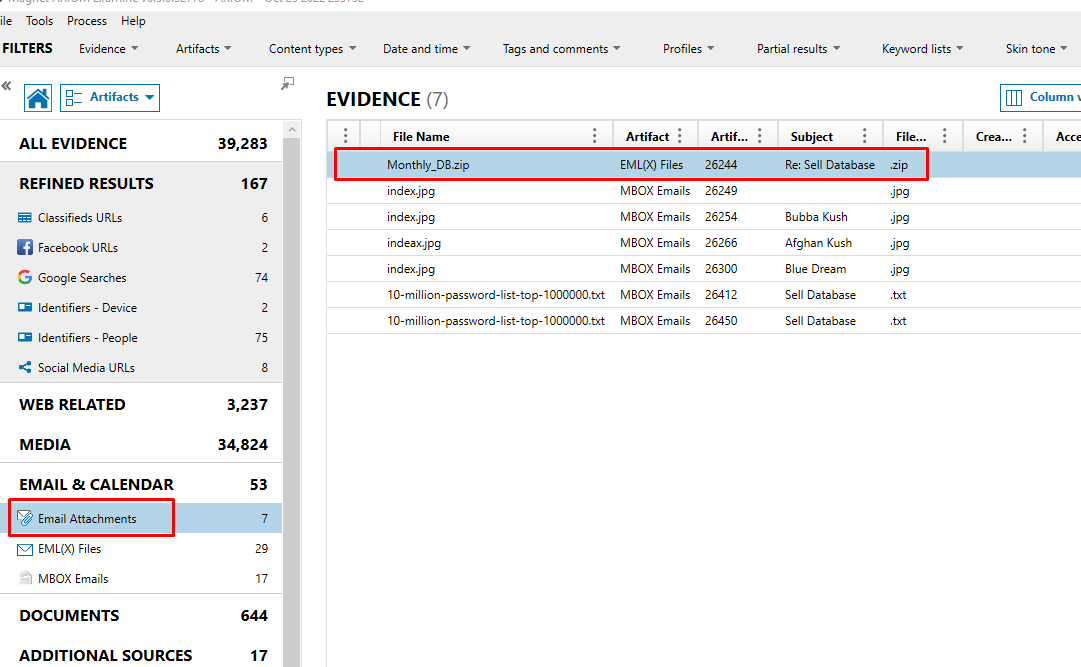
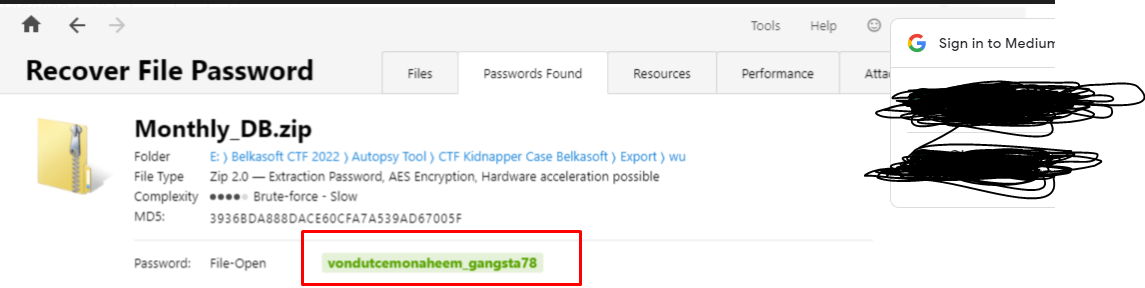
As seen in the image above, the dictionary attack was successful and the password was vondutcemonaheem gangsta78. The zip file was cracked using Passware Kit Forensic and the 10-million-password-list-top-1000000.txt file.
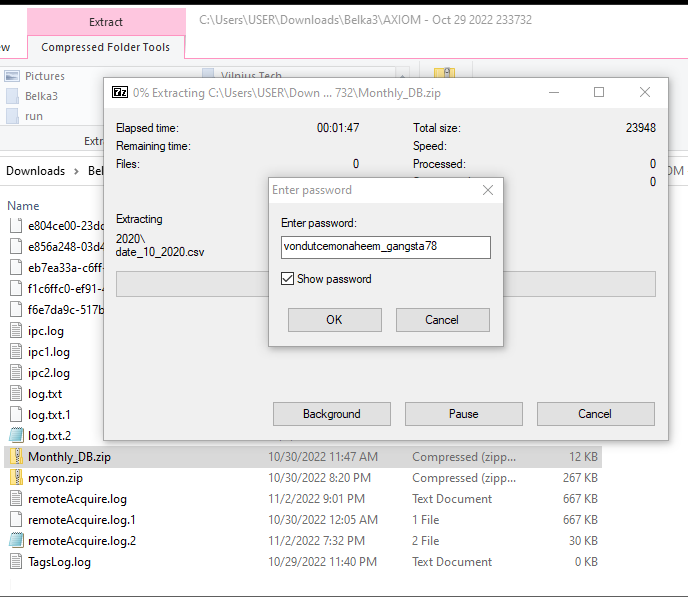
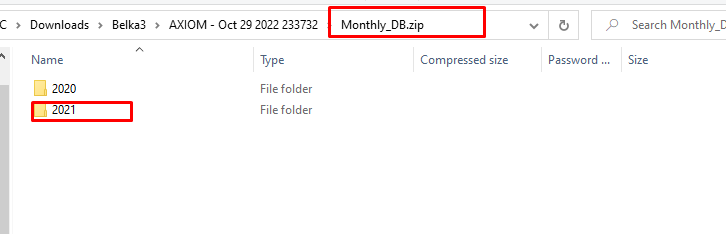
We can see two folders for different years. Each folder contains Excel documents and after going through each one of them we can see the month with the most sales.
What was the other BTC wallet of the victim, which he used to hide his "under the counter" sales from his superior?
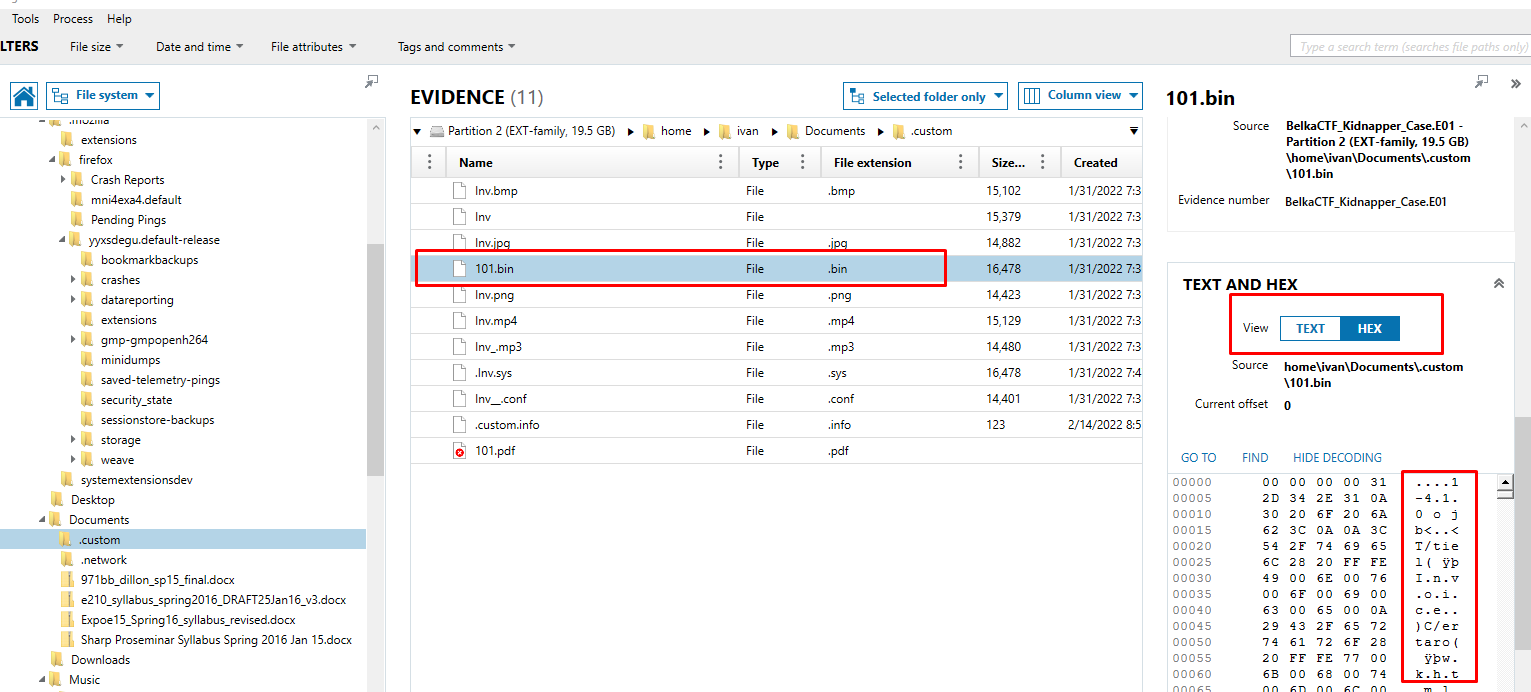
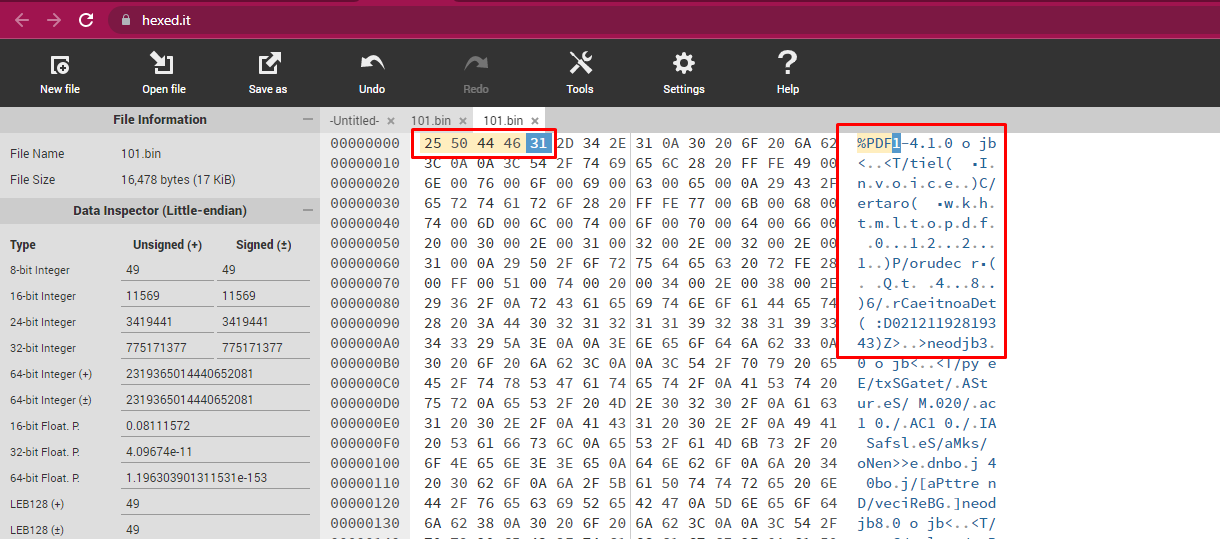
Before changing first 4 bytes
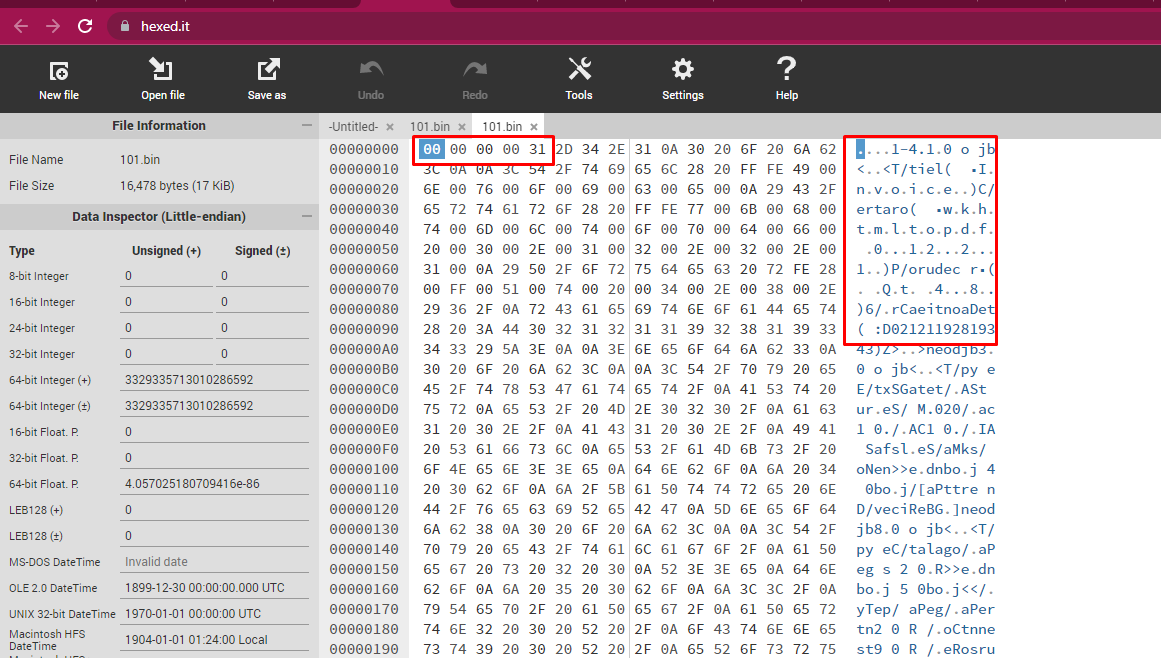
Replace the first 4 bytes on the file titled "101.bin" to a PDF header "25 50 44 46" and the document will show up as an invoice.
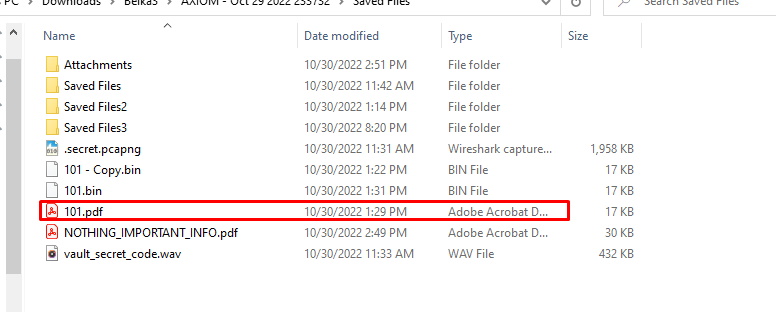
Saving converted .bin file to .pdf.
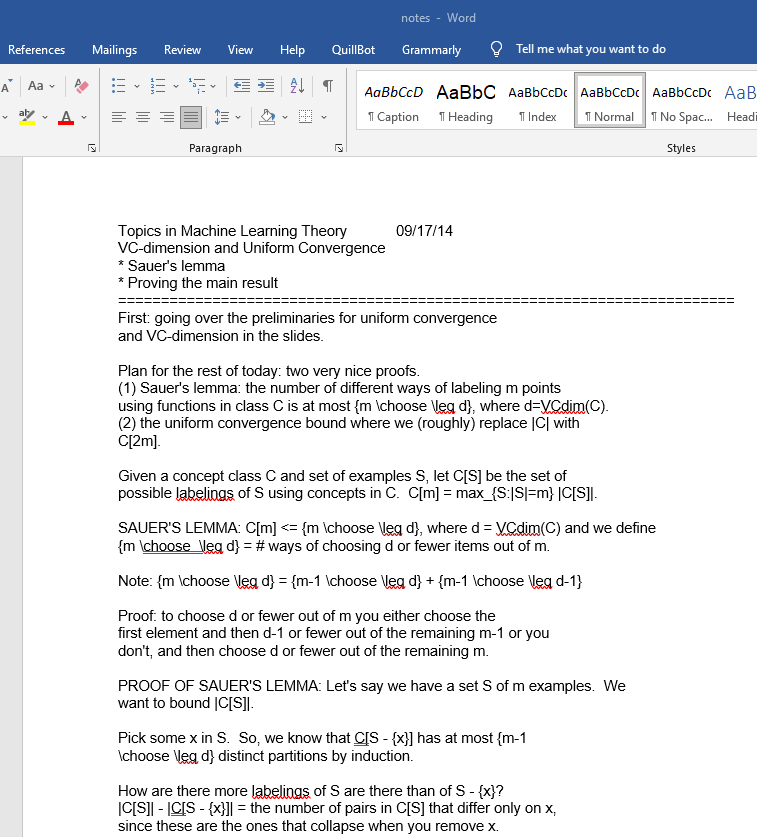
What is the password to the boy's notes?
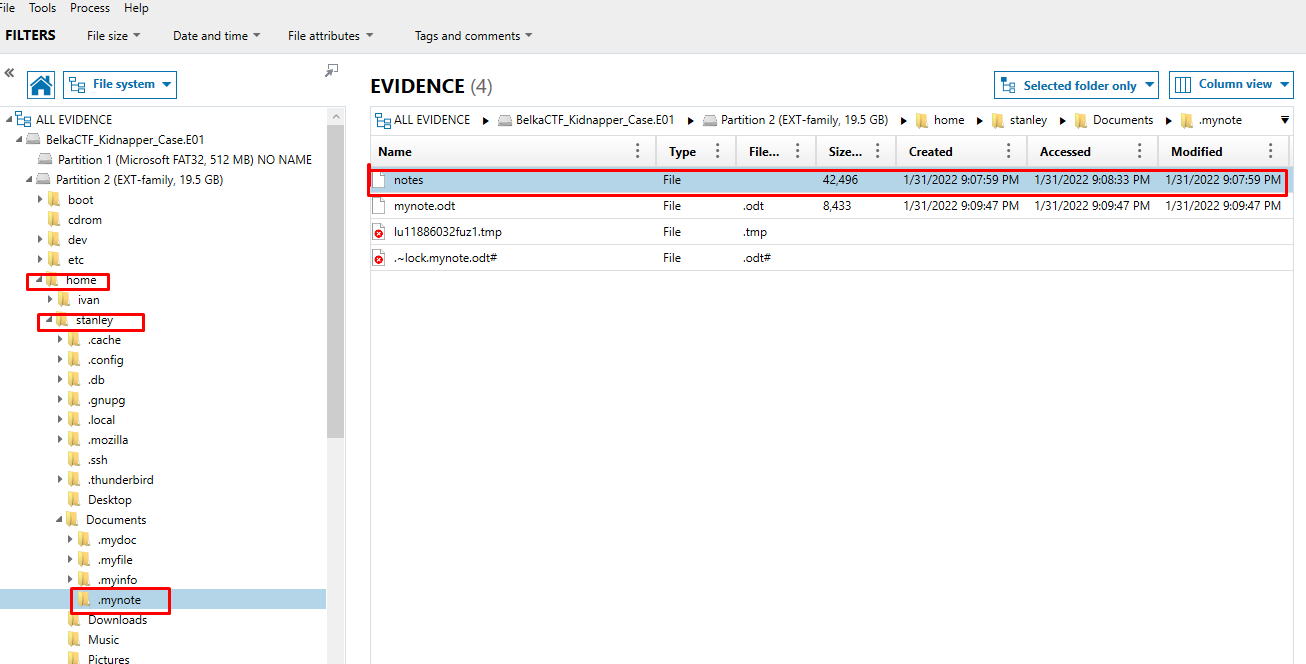
You had to locate both the note itself and the password for it in order to answer this two-part question. Fortunately, locating the memo was simple (sort of). More file system exploration led me to the following path:
/img BelkaCTF Kidnapper Case.E01/vol vol6/home/stanley/Documents/.mynote
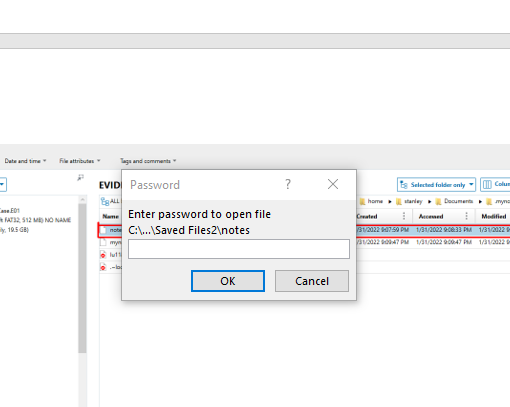
There were two files inside: "notes" and "mynote.odt" (extensionless). The first one was uninteresting, but the second felt strange due to the absence of an extension. It appeared promising that this was what I was supposed to be looking for when I attempted to access it in Microsoft Word and was prompted for a password.
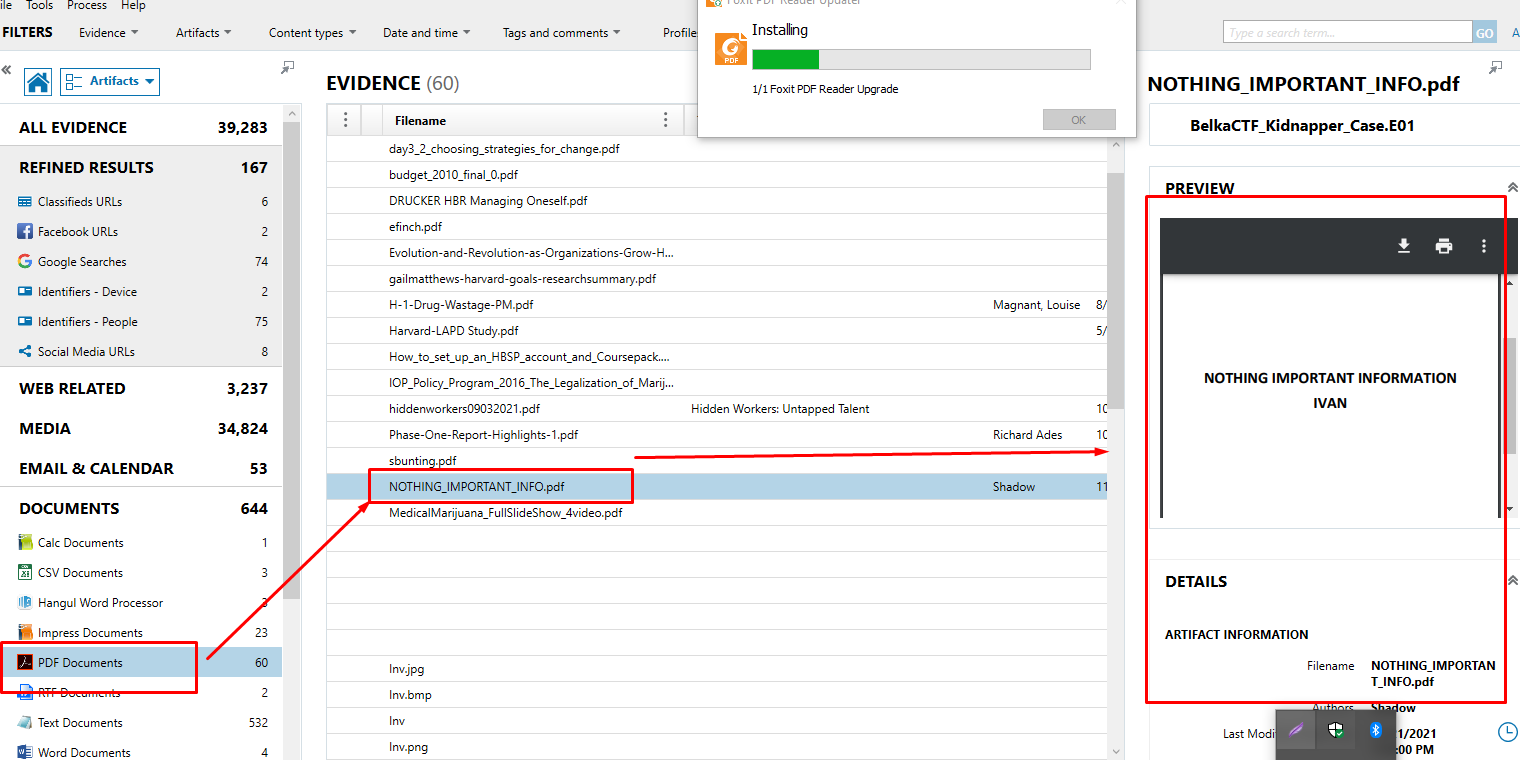
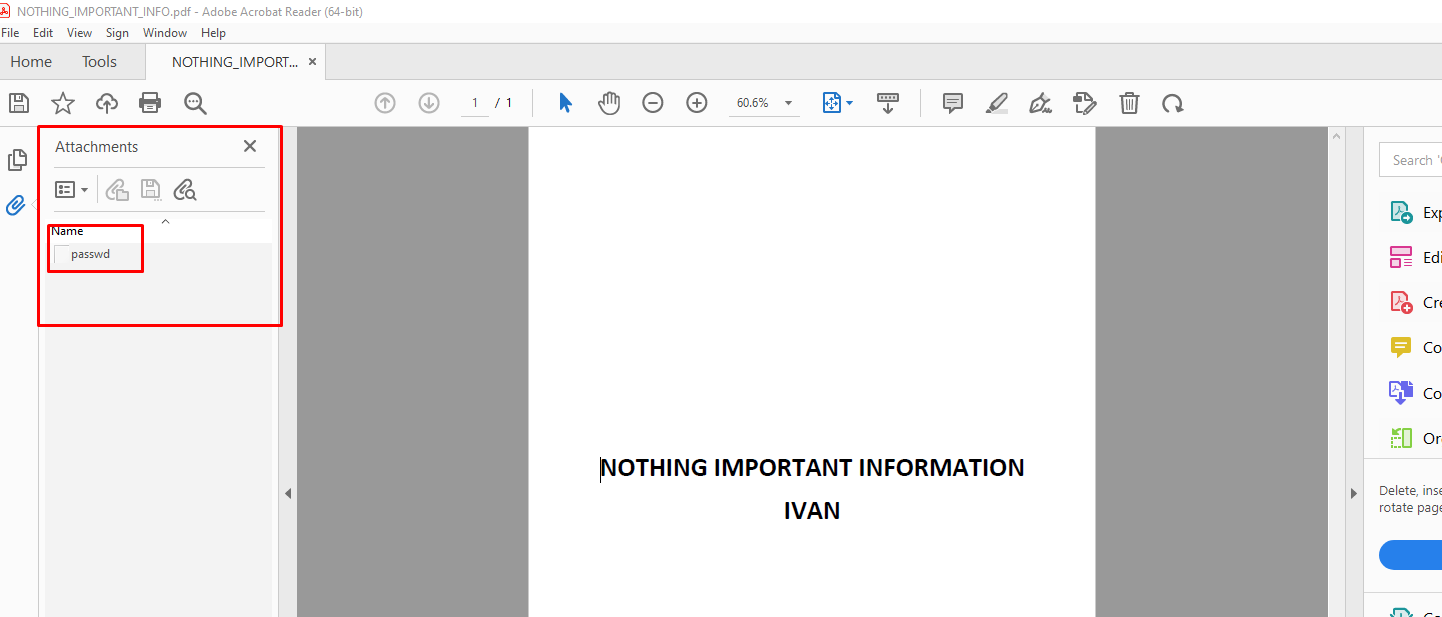
Throw the file into an online tool like Cyberchef and decrypt it using "from Base32" and "Rot13". All passwords are displayed.
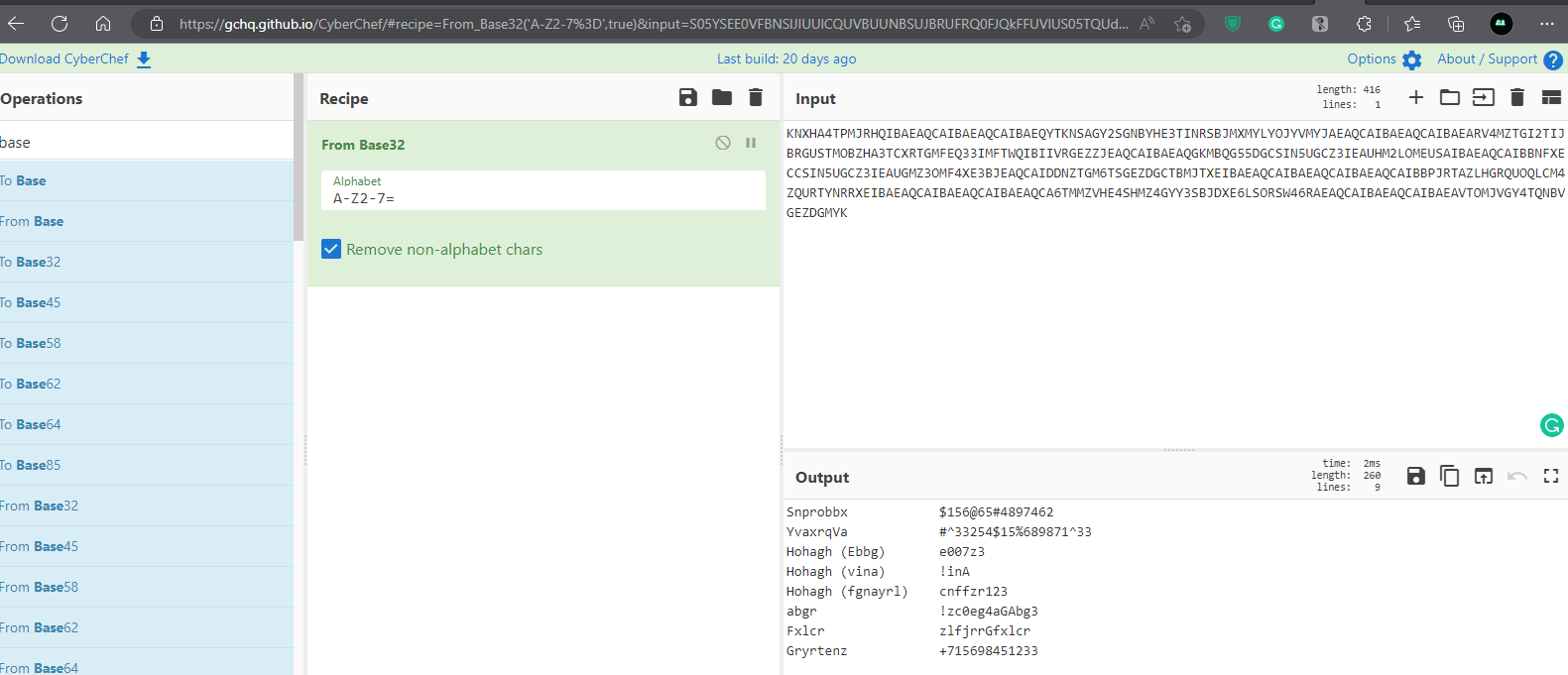
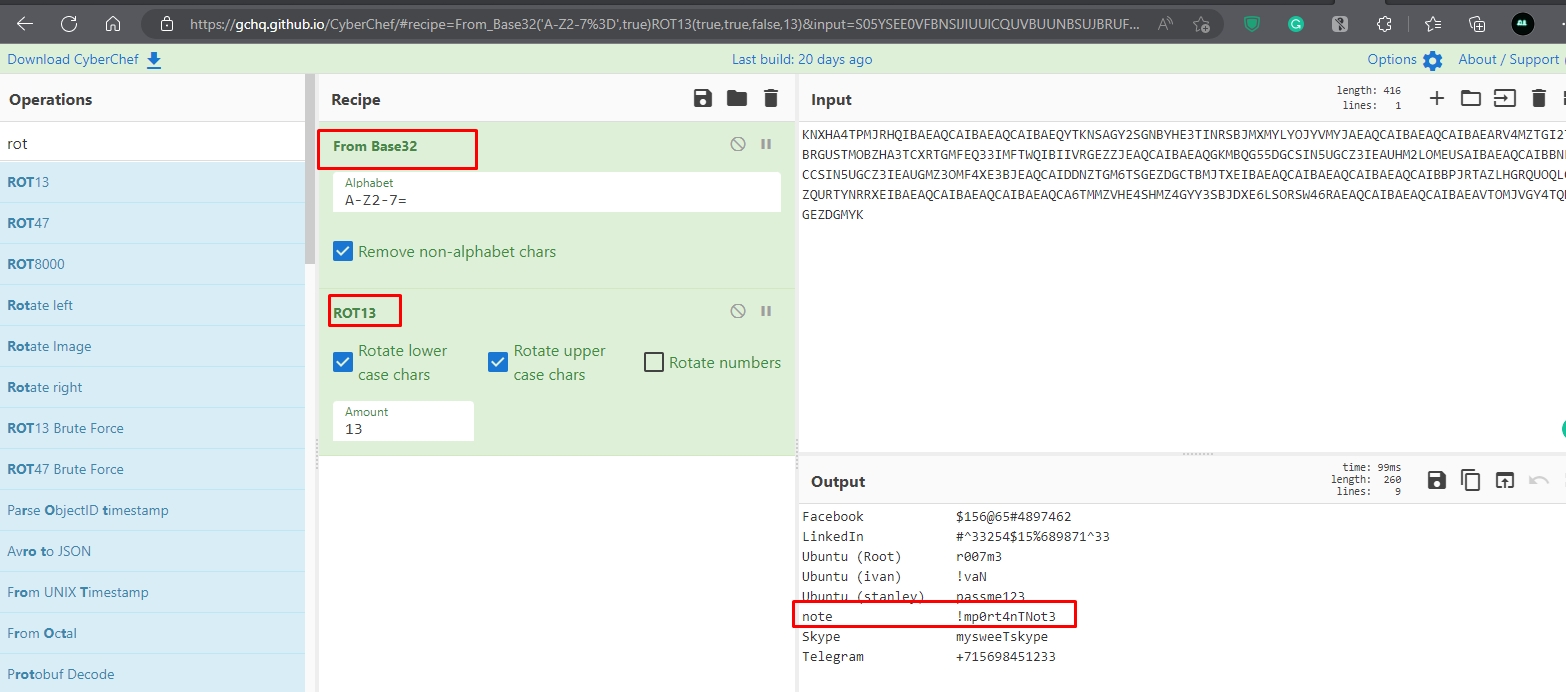
Use the password above to open the notes file. "!mp0rt4nTNot3"
What is the "secret pin" mentioned in the notes?

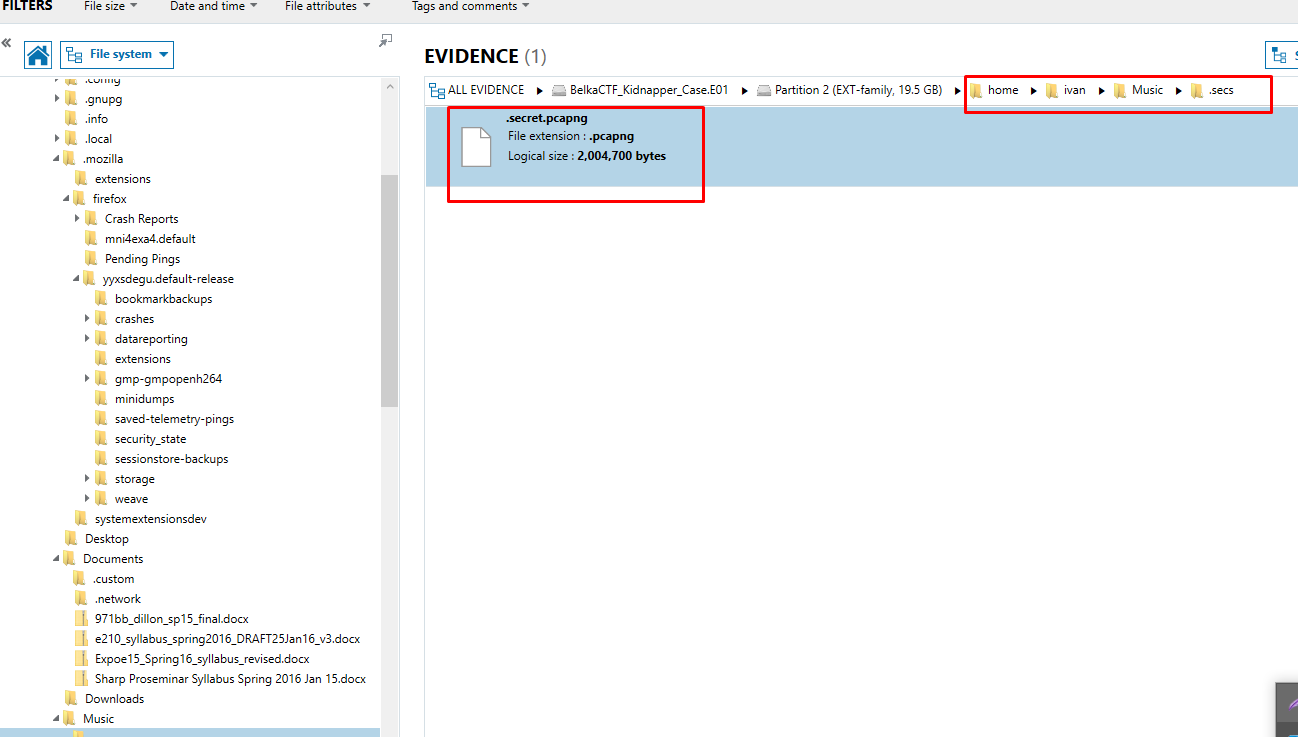
Opening the file in Wireshark we can look for any packets of interest. We see some HTTP GET requests for a file called "vault_secret_code.wav".
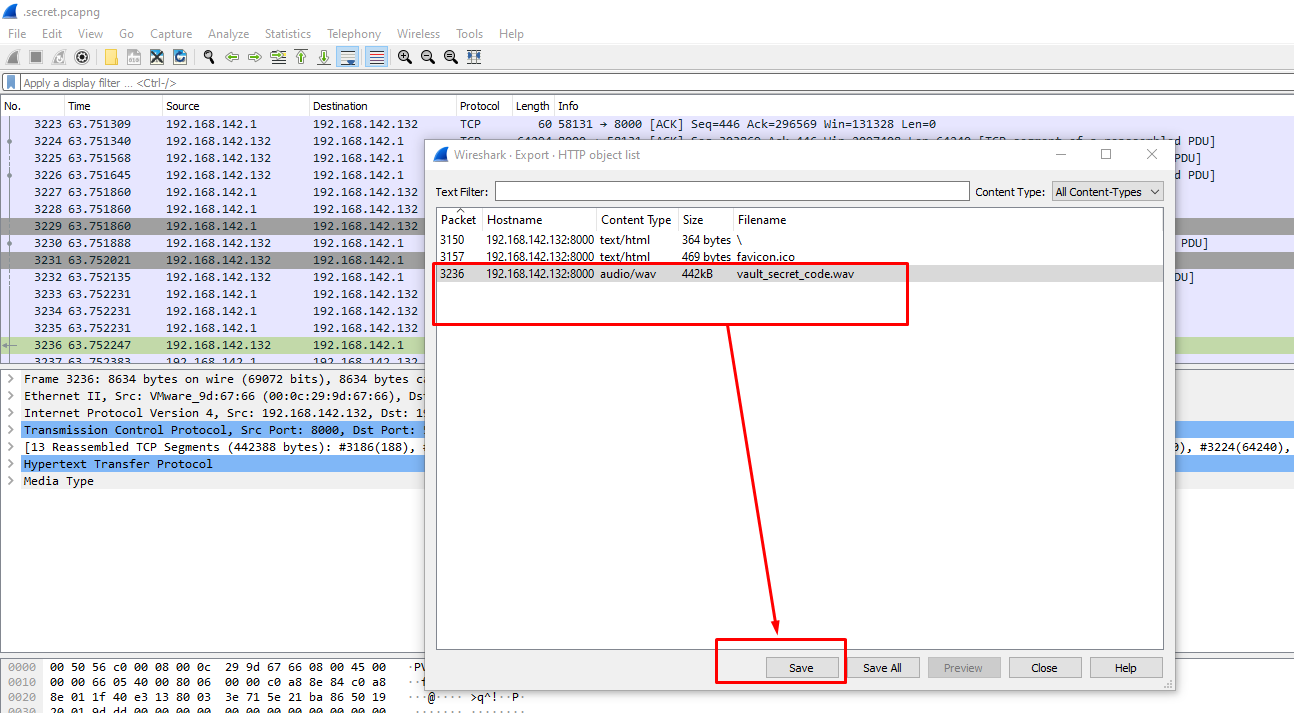
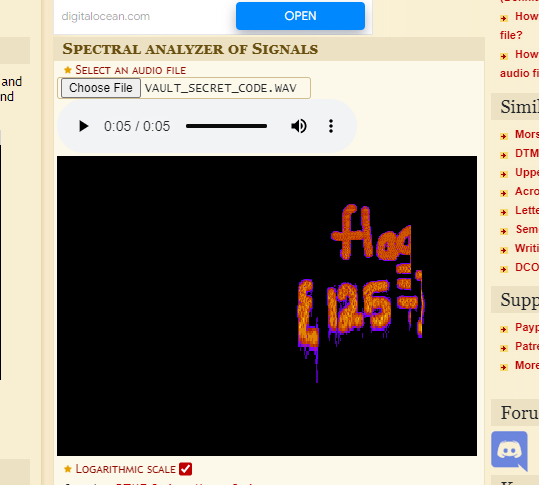
Notice the audio/wav record that became located in the PCAP record. Export this record and try and play it with a general audio/mp3 participant. You will notice, it's far truly an audio record with no significant sound inside, so that you can require a few kinds of spectrum analyzers. Using a free online tool //www.dcode.fr/spectral-analysis. Load the record into this and you will see the message.
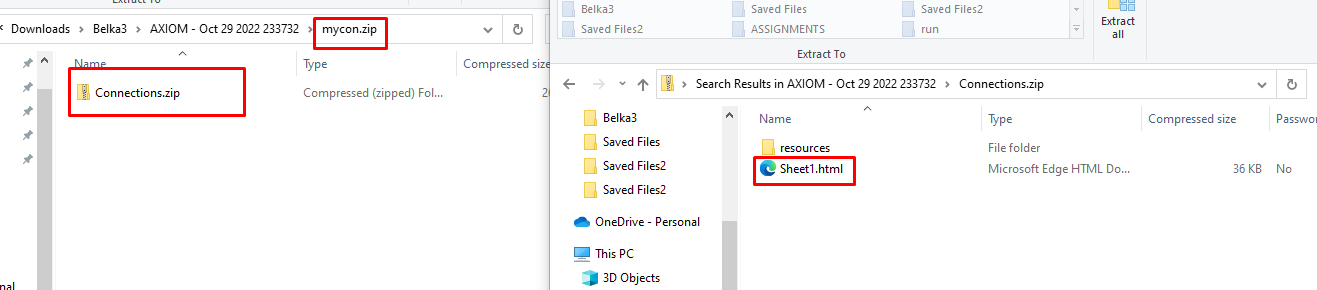
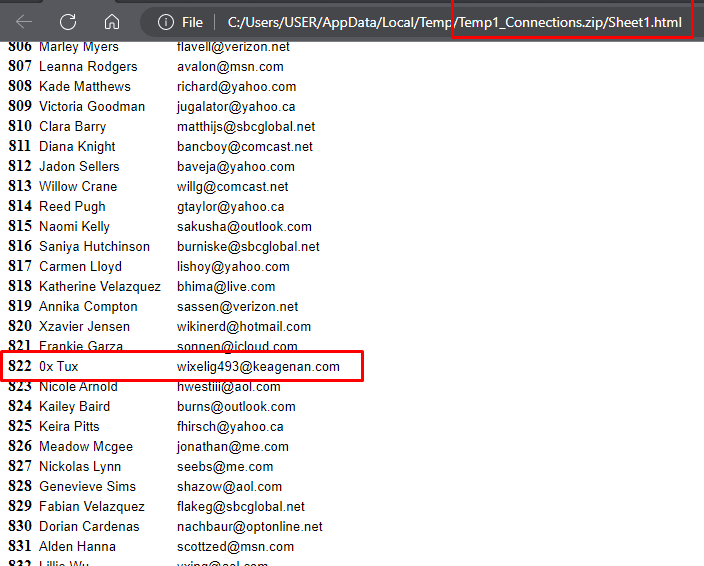
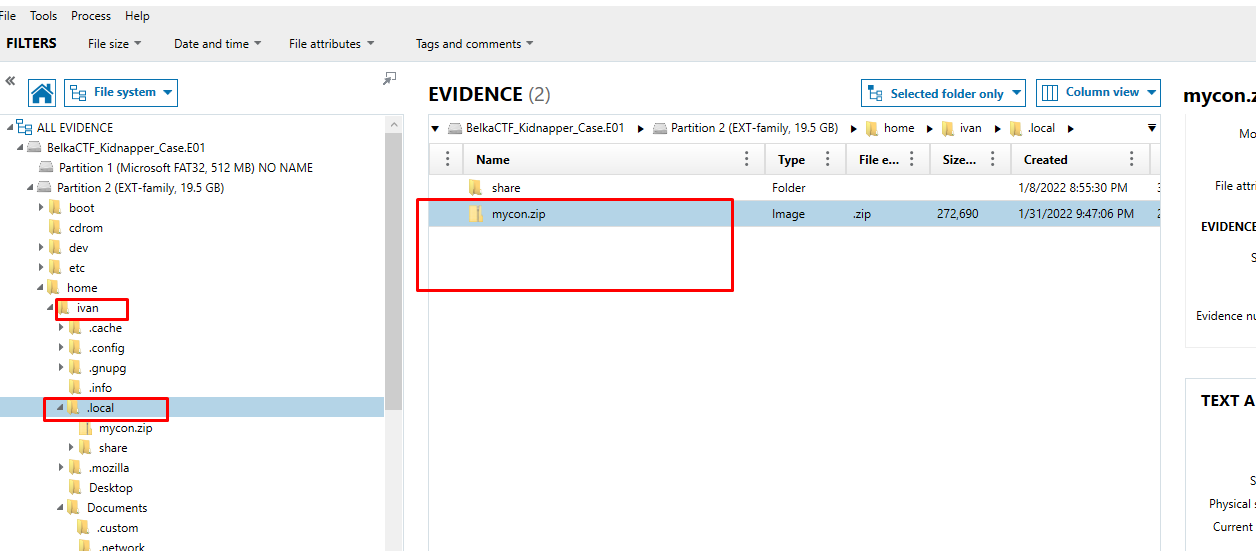
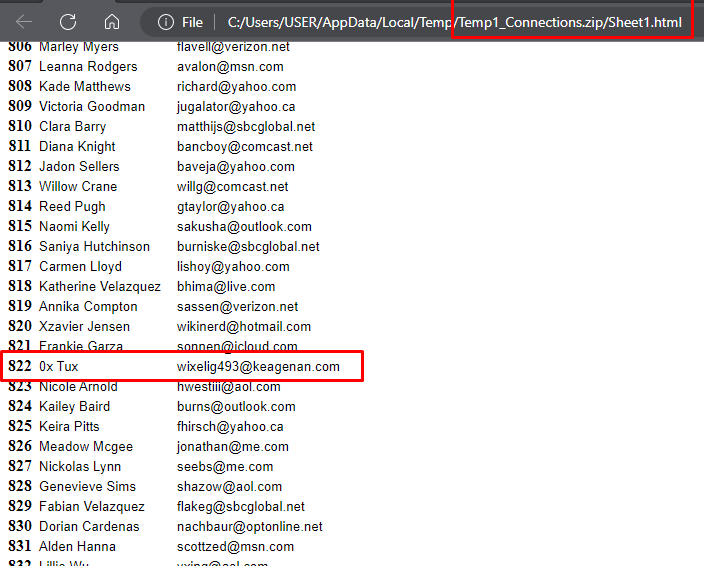
Fortunately, "Connections.zip," another file contained inside "mycon.zip," was not password-protected. There was a "Sheet1.html" file within that had a complete list of names and email addresses. We figured Tux was definitely the bad guy, so I quickly searched the text.
When did the boy receive a threat?
Since I had already located the "notes" file, this problem was essentially solved. Even though a timestamp is already visible in Unix Epoch, you must read the entire post to fully get the context of the question and the desired response.

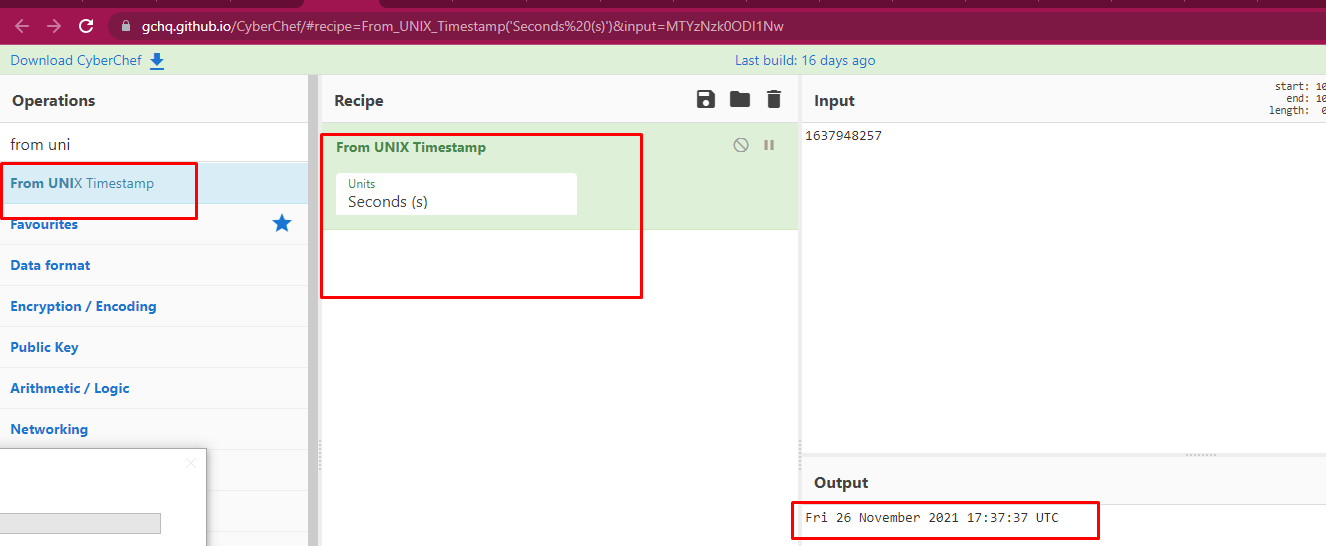
Who was the kidnapper?
There was a "Sheet1.html" file within that had a complete list of names and email addresses. We figured Tux was definitely the bad guy, so I quickly searched the text.
Tools used: Magnet Axiom, Cyberchef, John the Ripper, Wireshark, dcode, hexed.it, Passware Kit Forensic, Autopsy
Resource
Subscribe to my newsletter
Read articles from Ohekpeje Joel Odey directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Ohekpeje Joel Odey
Ohekpeje Joel Odey
Cybersecurity professional sharing insights on securing ecosystems, exploring cloud tech, and simplifying concepts for pros, enthusiasts, and beginners alike.