Single Sign On( SSO) and it's main components.
 Ian Carson
Ian CarsonSingle sign-on is one of the major authentication processes. It differs from other Authentication processes such as OAuth in that SSO is a security authentication process that allows users to log in to multiple applications with a single set of credentials.
SSO is made up of the following major components:
Identity Provider(IDP).
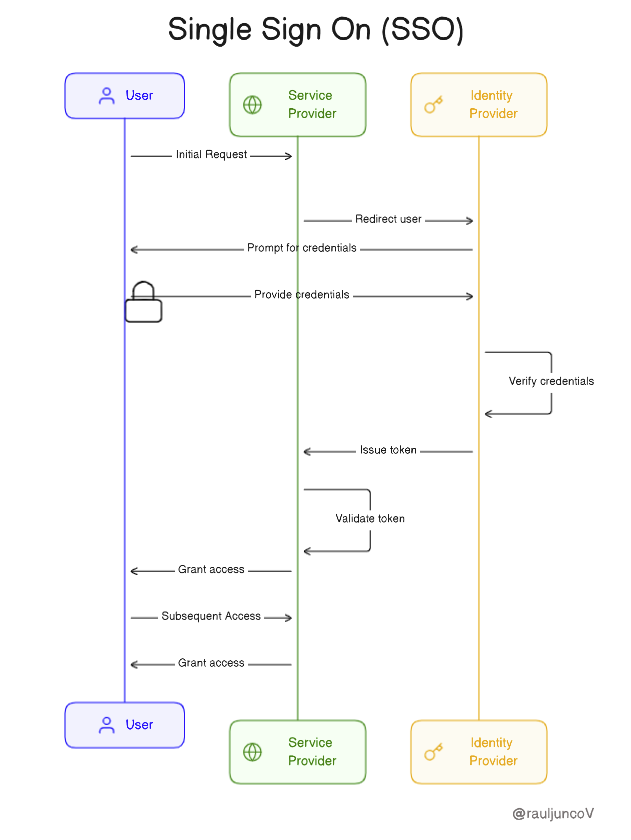
Authenticates user identities and provides tokens to prove their identities to others. When a user tries to access a service, the service then redirects the user to the IDP. The IDP asks the user to log in and validate the credentials. Once validated, it sends a token back to the service provider.
Service Provider(SP).
This provides the end service(like the dashboard, or app) the user wants to use. When a user tries to access the service, the SP receives a token from the IDP. The SP validates the token and grants access to the service.
Identity Broker.
Sits between the IDP and multiple SPs to translate the authentication credentials. The best scenario for this is when multiple IdPs or SPs are using different standards. The Identity broker receives the token from the IDP and translates it into a format that the SP can understand, or Vice versa.
The workflow:
Initial request: The user accesses one of the service providers for the first time. The service provider redirects the user to the Identity Provider(IDP).
Authentication: The IDP prompts the User for credentials. After verifying them, the IDP generates a token.
Token Issued: The IDP sends this token back. The service provider validates the token and grants the user access to the service.
Next access: The system reuses the same token or session when the user attempts to access another service within the SSO scope. This way, the user doesn't have to log in again.
Pros:
Easier for users.
Centralizes the account management.
Reduces password fatigue.
Cons.
Multiple services are at risk if the IDPs are compromised.
Huge complexity in Setup and maintenance.
SSO is complicated in reality but a very handy feature.
Thank you and see you in the next.
Special credits to @RauljuncoV on X(Formerly Twitter).
Subscribe to my newsletter
Read articles from Ian Carson directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Ian Carson
Ian Carson
A Disciplined, keen on details, and curious problem solver. I read and code a lot. I believe in Teamwork, Accountability, Transparency, and Competency.