Building an CLI for Streamlining Server Access Management with Pangea Vault and AuthN
 Tegar Imansyah
Tegar ImansyahWhy I Made It
As a developer constantly working with various servers, I often found myself grappling with the challenge of managing SSH configurations. The combination of SSH keys, usernames, and server IPs became a mental jigsaw puzzle, leading to frequent instances of forgetting or misplacing crucial information. This inconvenience not only slowed down my workflow but also posed a security risk as I juggled between different configurations.
To address this issue and enhance my efficiency, I decided to create an SSH Manager CLI. The primary goal was to streamline the process of managing SSH configurations, making it easier to recall and access the necessary information securely.
SSM In Action
Since this is a CLI tools, so there is no web app demo. I also prepared a web app, but it's only backend where CLI interacts with it for store and get from Pangea Vault. If you want to try it, please try in this github repo: https://github.com/tegarimansyah/secure-server-manager
or if you prefer a video demo (but please run 1.5x or 2x speed).
The Build Journey
Tech Stack
Main CLI app
Python
Typer
FastApi (for accepting callback from Pangea AuthN)
httpx (for calling Pangea and Backend API)
rich and questionary (for interactivity)
Backend API
- Javascript in Cloudflare Worker
We need a backend API to use Pangea Vault. It's because the CLI is client-side, so there is no way to use server-side token to store and get vault data. We also can't use user authentication token since there is no relation between the user and the vault, maybe later Pangea should integrate both features more. But don't worry, there is a workaround I found below.
Sequence Diagram
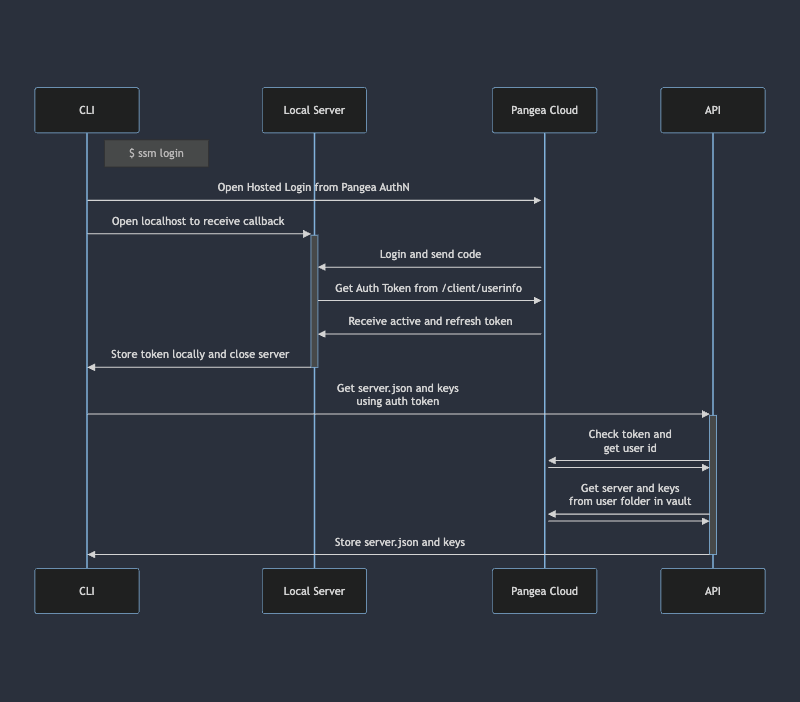
First of all, we need to login. Running ssm login will open your default browser and go to Pangea hosted login. Behind the scene, it will also create a server instance waiting for a callback from Pangea. After we login (or sign up), it will redirect to local server and send a code. Local server will receive the code and call Pangea AuthN API to receive user profile (/client/userinfo). Honestly, this process took me a while and I found this method by looking at js sdk .
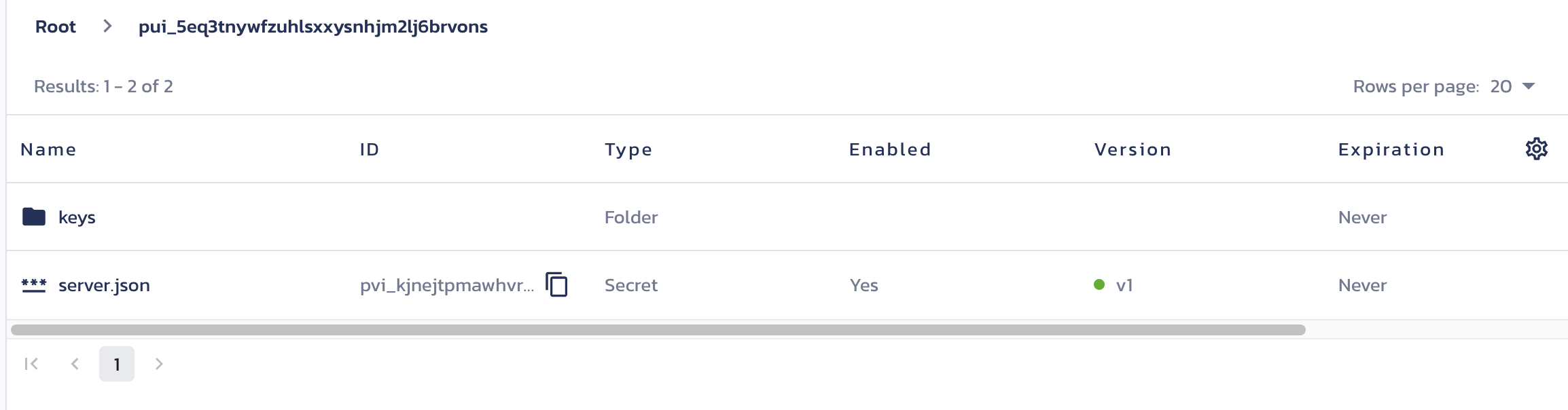
After that, CLI will call backend API to get server.json where configuration is saved and keys from Pange vault. To make sure we got correct server.json and keys, I utilized the user id as a folder name. In the API, we can get secrets by using list endpoint with filtering folder as user_id and name as server.json and include_secret. For keys, I save them in a folder <user_id>/keys and without name (so we will get all files). Here is the example API using curl:
curl -sSLX POST 'https://vault.aws.us.pangea.cloud/v1/list' \
-H 'Authorization: Bearer <server_side_token>' \
-H 'Content-Type: application/json' \
-d '{"filter":{"folder":"<user_id>","name":"server.json"},"include_secrets":true}'
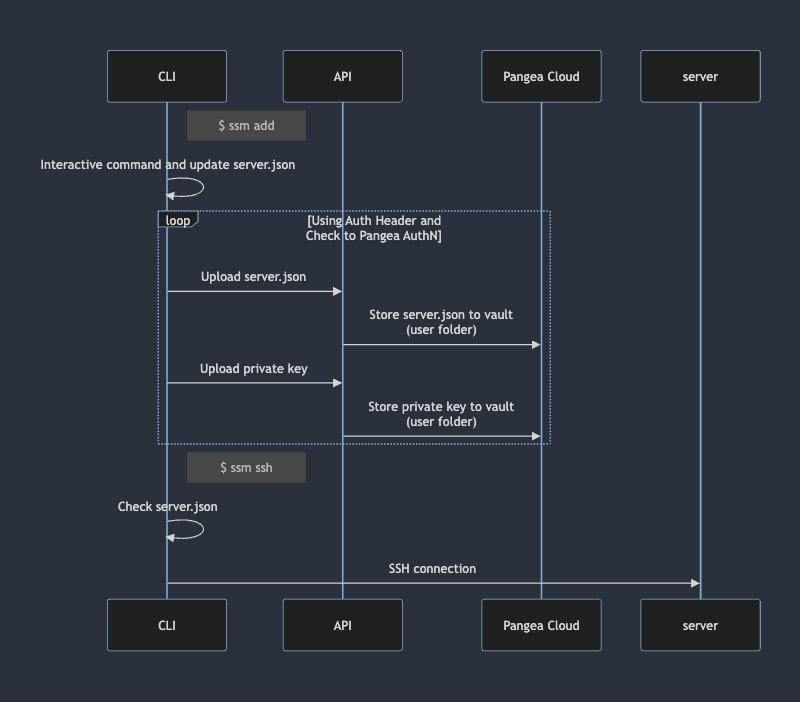
After we login, we get server.json and keys from previously saved session. But if we just getting started, we can use ssm add to add new server configuration. It will sync to pangea cloud so the next time we login, we get our latest configuration.
After that for main command ssm ssh, it will only check the server.json and then run ssh command to connect to server. So there is connection to pange or backend api.
CLI Setup
I call my tool Secure SSH Manager, or ssm in short. After cloning the repo, install the dependency using poetry install. I just remove the extension, chmod +x ssm and added shebang #!/usr/bin/env python3. After that I can invoke the command inside poetry virtual environment.
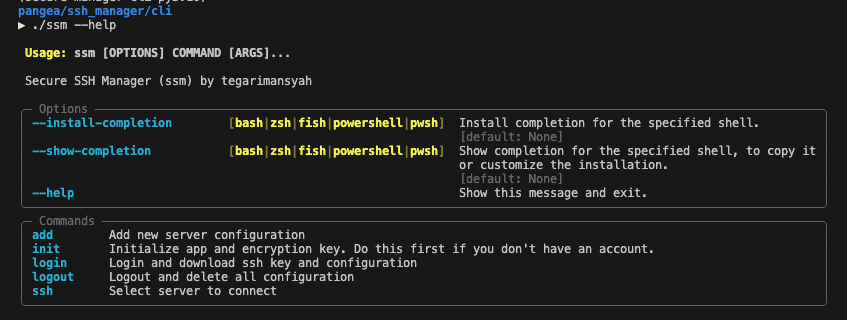
This beautiful help is auto-generated by typer. It can also open your default browser and start a fastapi server locally.
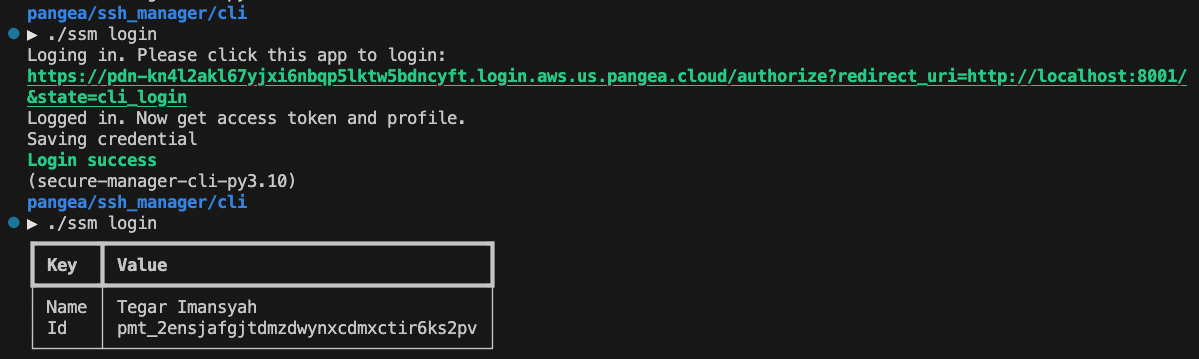
After we log in, the same command will show us the profile that we logged into. The cool thing when we build with pangea is how interactive the API docs are. Look at this page, you can use your existing token, add only required params or also add optional params.
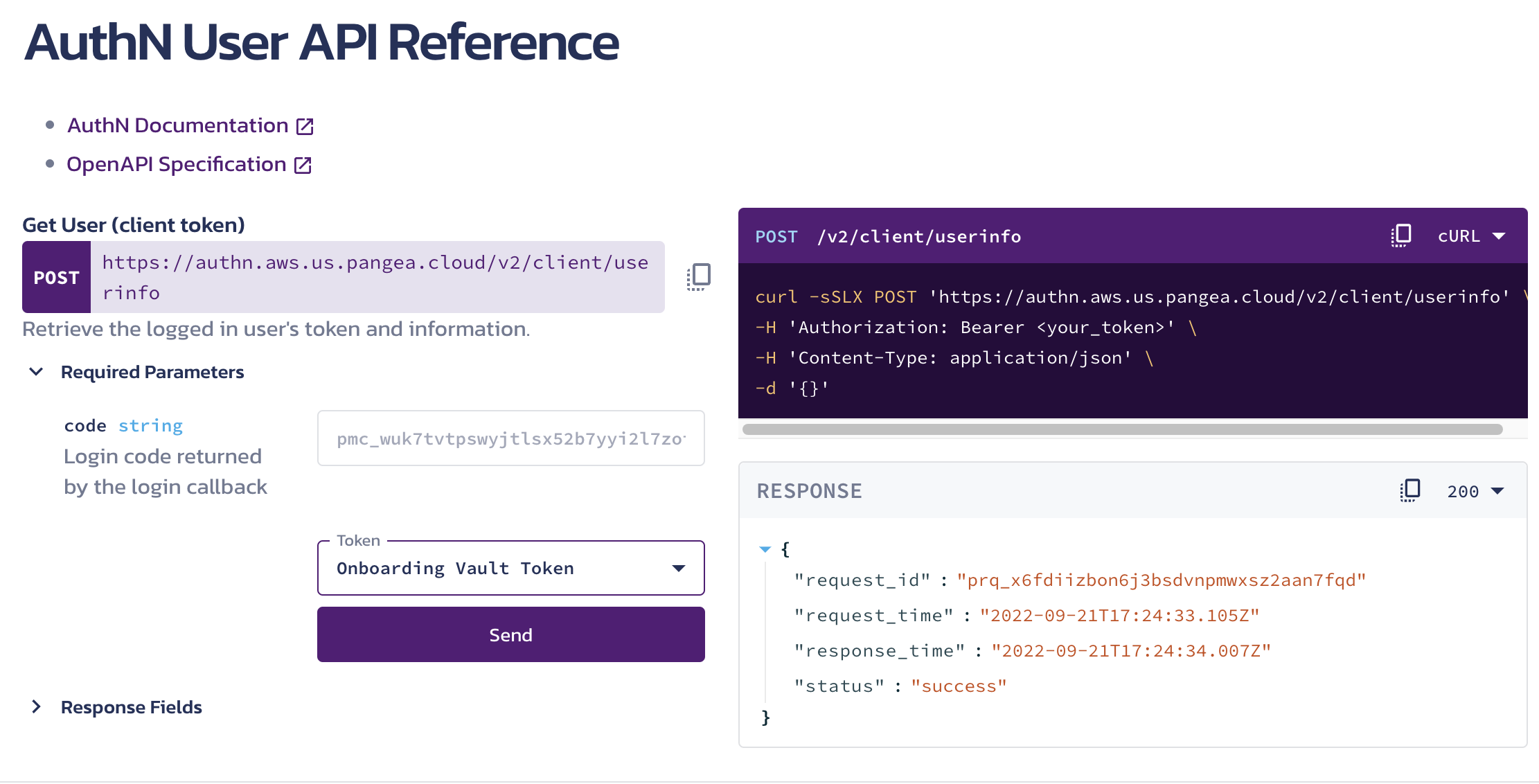
Okay back to the cli. Behind the scene after we login, we also get the stored server.json and keys in vault copied to local.
But what if we need to add a new server for initial data? We use questionary to interactive create user prompts.

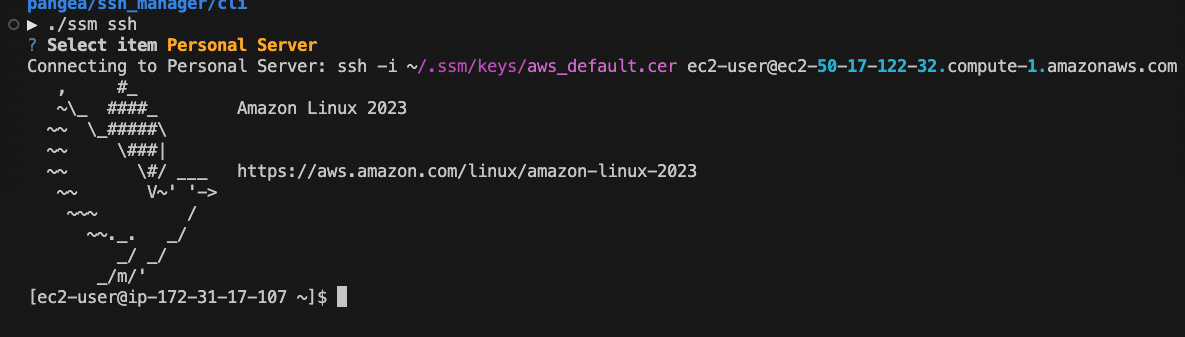
Lastly, we will ssh to the server
Backend Setup
Since I only need this backend as a proxy to call Pangea to store and get the secret without giving token to client side, I need to make it as simple as possible. First I think I need a framework like Django or Svelte (well, with beautiful frontend or sophisticated backend with ease). But for first MVP, I don't need it, even I don't need a database.
So my choice is to use cloudflare worker. It's really easy that I only use built in editor to make it. First of all I add environment variables.
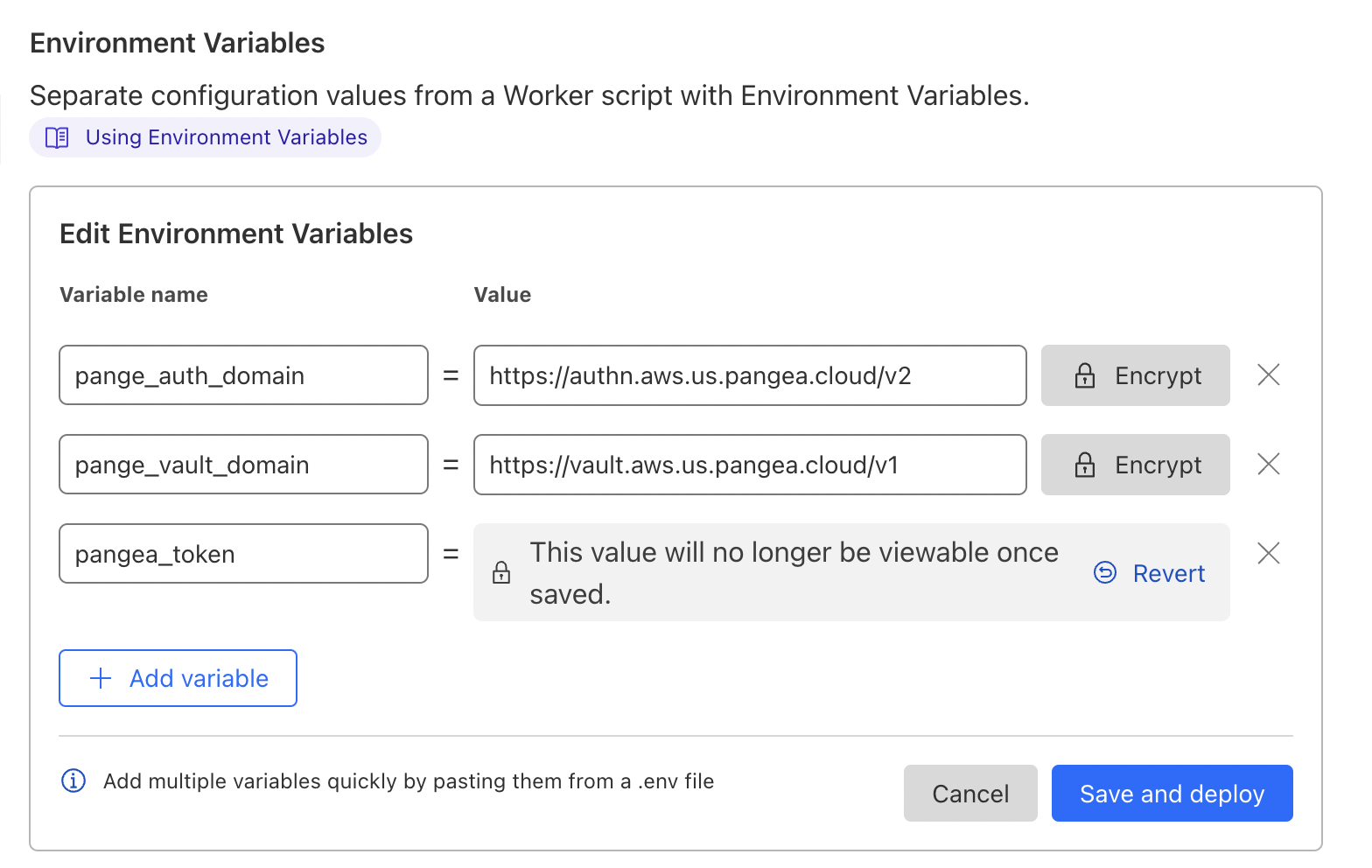
And here is the list of endpoints. All endpoints need a JWT token and check via Pangea AuthN, so we can get the user_id (or reject the request if not authenticated)
| Endpoint | Description |
| POST /server-config | Receive application/json of server configuration content, and create or update server.json in user_id folder. |
| GET /server-config | Return content of server.json |
| POST /private-keys?filename=<filename> | Receive plain/text of private key content, and create or update <filename> in <user_id>/keys folder |
| GET /private-keys | Return all files in <user_id>/keys folder |
What I Achieved
In conclusion, it's a lot easier to build the SSH Manager CLI with Pangea's AuthN and Vault. By centralizing and securing SSH configurations, I've eliminated the risk of forgetting or misplacing crucial information. The step-by-step synchronization and selection process ensures a seamless and secure user experience.
This project stands as a testament to the power of innovation when coupled with cutting-edge security solutions. With Pangea, I've successfully turned the complexity of server access into a simple, efficient, and secure process. Now, developers can focus on their app logic without compromising on security, thanks to the simplified set of APIs provided by Pangea.
Next time, I will add a encryption key, so everything that uploaded to server will be encrypted first in local. So user can store their private key in peace.
Subscribe to my newsletter
Read articles from Tegar Imansyah directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
