Navigating the Crucial Facets of Software Dependability
 Nayan Raut
Nayan Raut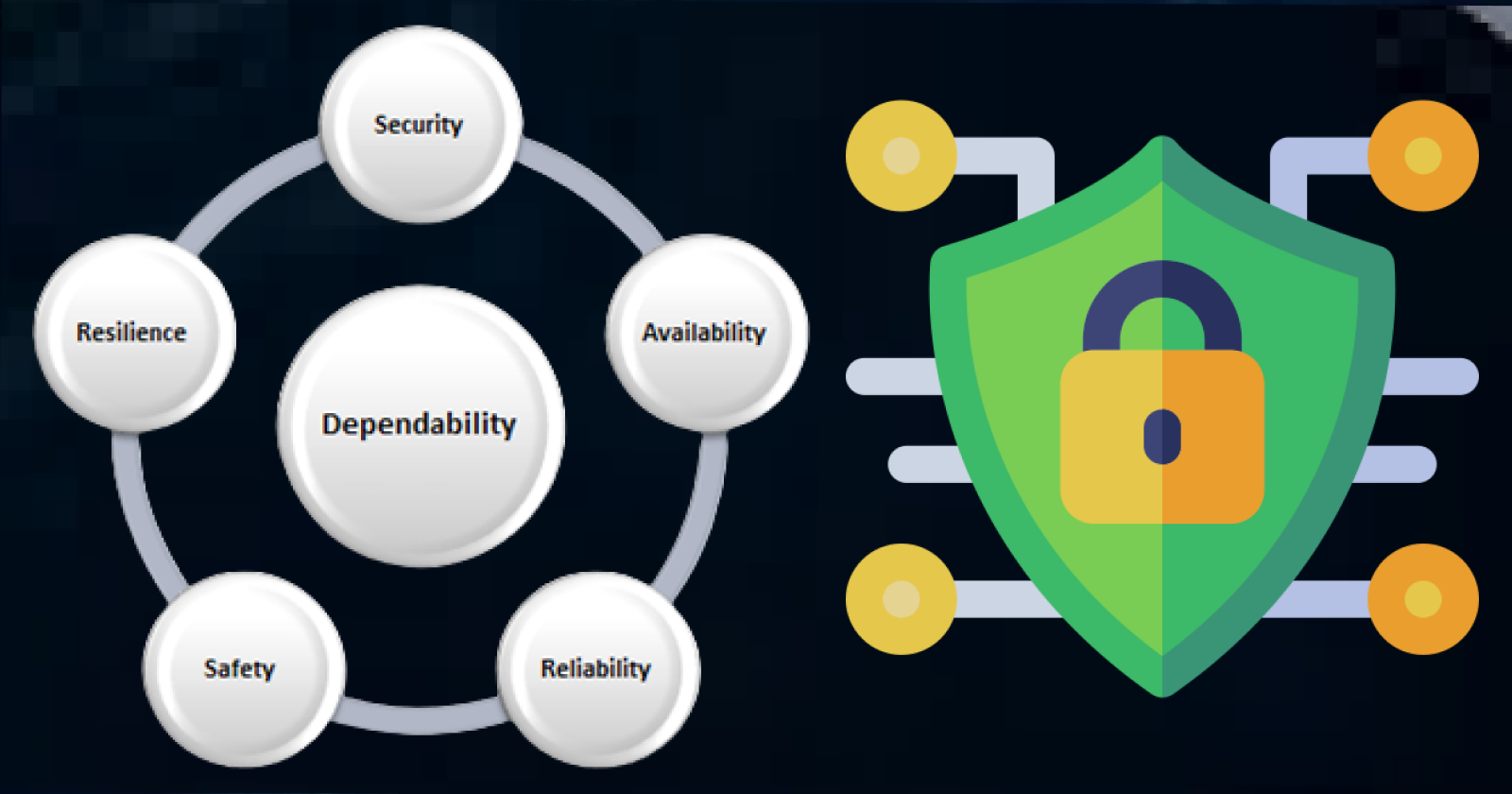
Understanding Dependability
The significance of computers in both personal and business settings underscores the severe ramifications of any malfunction. Consider a crashed website resulting in lost sales or a software glitch in a car that might lead to costly repairs or endanger lives. The term "dependability" emerged in 1995 to encapsulate a system's reliability, safety, and security – interlinked facets ensuring user trust.
Dependability in a computer system is the user's trust degree in its consistent and secure operation.
Dependability reflects user confidence that the system will function as expected without failures or security breaches, an attribute often more crucial than added functionalities.
Key dimensions of dependability:
Availability denotes a system's readiness and accessibility to perform its designated function when required.
Reliability measures the consistency of a system's performance over time, ensuring error-free operation.
Safety evaluates a system's potential to avoid causing harm to individuals or the environment.
Security encompasses a system's resilience against unauthorized access, ensuring data confidentiality, integrity, and availability.
Unveiling Availability and Reliability
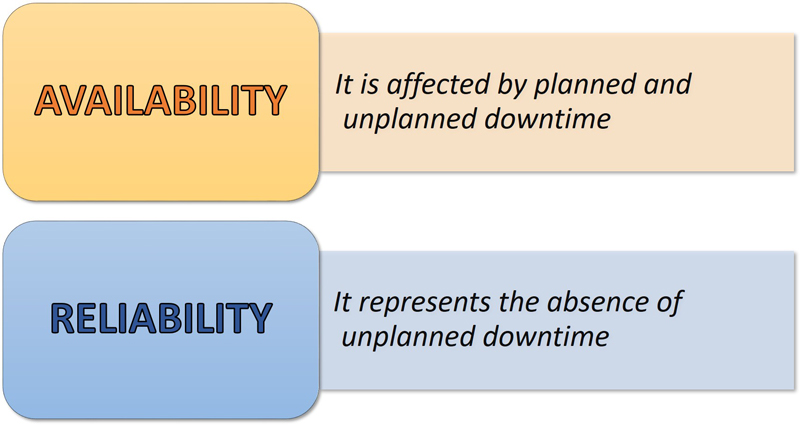
Availability ensures a system's operational readiness, while reliability guarantees consistent performance over time.
Availability is the likelihood of the system delivering services as requested. 💬 Reliability represents the probability of system services meeting specified requirements.
Reliability and availability are fundamental aspects of a system's performance. Reliability represents the probability of error-free operation over a specified time, while availability indicates the likelihood of a system being operational and delivering services at any given point in time. Both are expressed as probabilities and can influence system design based on their importance in specific contexts.
For systems with high availability requirements, such as telephone exchanges, uninterrupted service is crucial. Even if faults occur during setup, swift recovery mechanisms often mask failures without significant impact. On the other hand, systems with low reliability requirements might tolerate quick recoverable faults without serious consequences.
However, defining reliability and availability isn't straightforward. Environmental factors and user behavior in different settings can significantly affect system performance. Moreover, the severity of system failures and their impact on users isn't always reflected in these metrics. For instance, users might accept minor issues but strongly object to failures resulting in data loss.
System availability isn't solely determined by uptime percentages; the timing of failures also matters. For example, a system down during off-hours may affect fewer users than a short outage during peak times. Additionally, the time taken to recover from failures significantly impacts overall availability; a system with shorter recovery time may have better availability despite more frequent failures.
In summary, reliability and availability metrics provide valuable insights, but their strict definitions might not fully capture user expectations or the impact of system failures on users.
Highly available systems are generally reliable. However, certain scenarios prioritize availability over reliability. For instance, a phone system requires high availability, although an interrupted call might not lead to serious consequences, emphasizing availability over reliability.
Conversely, a nuclear reactor control system necessitates high reliability, even if availability fluctuates. Tailoring systems to user needs and environmental factors ensures meeting requisite levels of availability and reliability.
Techniques for enhanced reliability:
Fault avoidance focuses on preventing faults through error-free languages and meticulous code writing.
Fault detection and removal involve identifying and rectifying existing faults through testing and debugging.
Fault tolerance ensures system operation despite faults by integrating self-checking mechanisms and redundant components.
Navigating the Realm of Safety
Safety-critical systems must always operate safely, avoiding harm to individuals or the environment.
Primary safety-critical software directly embedded in control mechanisms could cause hardware malfunction. Secondary safety-critical software indirectly contributes to accidents, demanding meticulous design and development to mitigate risks.
Approaches to ensure safety:
Hazard avoidance involves system design to prevent hazards.
Hazard detection and removal focus on identifying and eliminating hazards before causing accidents.
Damage limitation involves system features to minimize the impact of accidents.
Elevating System Security
System security is paramount to protect against deliberate and accidental attacks, especially in networked systems.
Three security threat types in networked systems:
Confidentiality threats involve unauthorized data disclosure.
Integrity threats aim to damage or corrupt data or software.
Availability threats restrict authorized access.
Security vulnerabilities, often rooted in human errors, underscore the importance of robust security controls.
Controls for heightened security:
Vulnerability avoidance designs systems to evade security weaknesses.
Attack detection and neutralization monitor and repel attacks.
Exposure limitation and recovery focus on recovering from breaches.
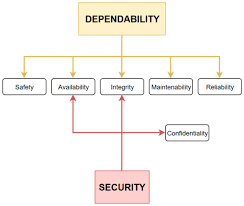
Security and dependability assurance processes involve various data, including test outcomes, development methodologies, and review records. These serve as evidence for a system's trustworthiness and are vital in determining its suitability for operational use.
Safety and dependability cases, often known as assurance cases, compile comprehensive evidence supporting a system's safety or achieved security and dependability levels. In many critical systems, producing a safety case is a legal requirement, satisfying regulators or certification bodies before deployment.
Regulators play a crucial role in ensuring system safety or dependability. They collaborate with development teams to ascertain the content and compliance of safety cases, ensuring adherence to prescribed processes and procedures.
The development of dependability cases, often concurrent with or post-system development, can pose challenges if development activities don't produce ample evidence of system dependability. Integrating the development of these cases with system design and implementation helps avoid costly decisions that might complicate case development.
These cases are extensions of safety cases and are comprised of documents detailing system descriptions, development processes, and convincing arguments demonstrating the system's safety or dependability. The structure and contents of these cases vary based on industry and operational context.
Software safety cases, integral to larger computer-based systems, must illustrate how software failures relate to broader system failures and either prevent these failures or ensure they won't lead to hazardous system malfunctions."
The Symbiosis of Dependability Dimensions
Dependability hinges on the alignment of availability, reliability, safety, and security. Inadequate security can compromise system availability, reliability, and safety, undermining their integrity.
Certification assumes operational software matches the original, invalidating reliability and safety if compromised. Unreliable systems make ensuring safety and security challenging, prone to system failures.
References:
Malkawi, M.I. The art of software systems development: Reliability, Availability, Maintainability, Performance (RAMP). Hum. Cent. Comput. Inf. Sci. 3, 22 (2013).https://doi.org/10.1186/2192-1962-3-22Sommerville, Ian. Software engineering / Ian Sommerville. — 9th ed. (2011)
Subscribe to my newsletter
Read articles from Nayan Raut directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
