Setting up Infrastructure on AWS using Terraform
 Anandhi
AnandhiVirtual Private Cloud
AWS Virtual Private Cloud is commonly known as VPC which is similar to your on-premise network. It is your own isolated network in the AWS cloud associated with a specific region. Network traffic within a VPC is completely isolated from the internet and other VPCs. Using security groups and NACL you can control the traffic coming in and going outside of a VPC.
Subnets
Subnets are segmented networks within a larger network, such as a Virtual Private Cloud (VPC) in AWS. They provide a way to organize and partition IP address space. They are associated with availability zones. There are two types of subnets. Public and Private subnet. Resources in a public subnet can be accessed directly from the internet. Whereas resources in a private subnet cannot be accessed directly from the internet.
Internet Gateway
Internet Gateway is often called 'IGW'. It is a VPC component that acts as a gateway between your VPC and the internet, enabling communication for resources in the VPC with the outside world. It plays a crucial role in providing internet connectivity to instances in your AWS environment. Instances in a public subnet can route traffic to the internet via the Internet Gateway.
Route tables
In AWS, communication is carried out with the help of route tables. Route tables can be associated with VPCs and subnets. Each route table consists of a set of rules called routes. Each route or routing rule has a destination and target.
NAT Gateway
NAT gateway is a managed AWS service that enables instances in a private subnet to initiate outbound traffic to the internet (for software updates, license validations, etc.,) while preventing inbound traffic from reaching those instances.
Security Groups and NACL
Security groups is for a specific resource (Eg: EC2 instance). It is a stateful and contains only allow rules. NACL on the other hand provides a stateless firewall at the subnet level. Each subnet must be associated with a NACL. It acts as an additional layer of security to your resources. Default NACL allows all inbound and outbound traffic. Custom NACL can also be created with a set of inbound and outbound traffic. It supports both allow and deny rules. It goes with the order of priority. The lowest number will be given the higher priority.
EC2 Instance
An EC2 (Elastic Compute Cloud) instance is a virtual server in the AWS cloud. It supports a wide range of instance types optimized for different use cases. Instances can be launched from pre-configured templates called AMIs (Amazon Machine Image). Using Key pairs you can securely connect to the instances using SSH or RDP. It is a pay-as-you-go resource type. Instances can be easily launched, stopped, terminated, and scaled to meet changing workload demands.
Load Balancer
A Load Balancer is a service in AWS that distributes incoming network traffic across multiple servers (instances) to ensure no single server is overwhelmed, improving the availability and fault tolerance of applications. Some of the key characteristics of a load balancer are distribution of traffic, high availability and health check of instances. There are three major types of load balancers in AWS, such as Application load Balancer, Network load Balancer and Gateway load Balancer. They are essential for scaling applications and improving their overall reliability.
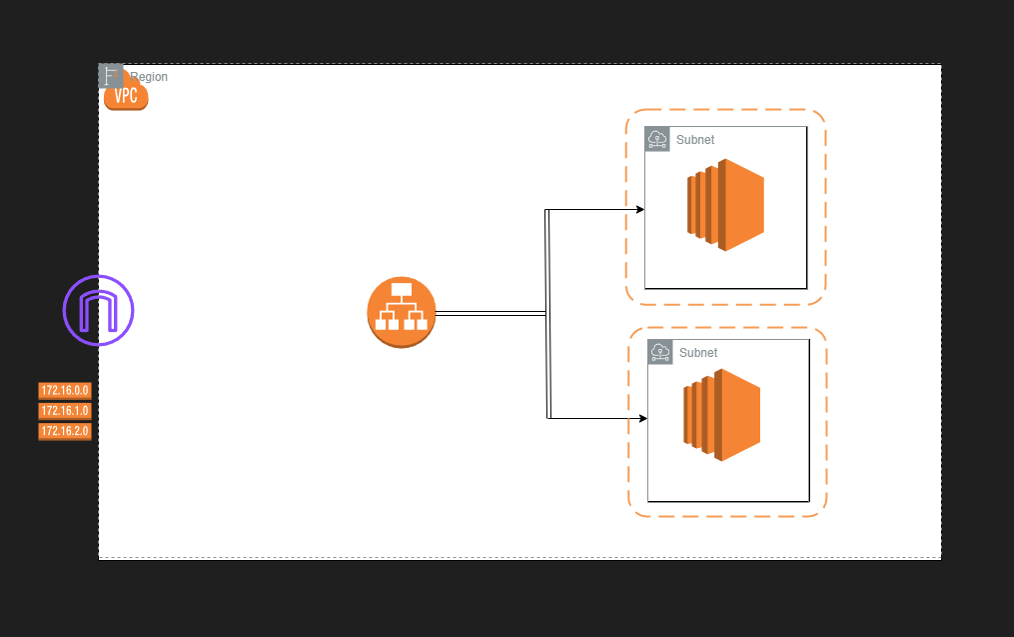
Let's create a basic AWS infrastructure with custom VPC, public subnets, internet gateway, route table, security group to allow HTTP traffic, EC2 instances with apache2 web server installed and distribute the traffic using an application load balancer. We will be using Terraform to automate the whole infrastructure provisioning.
Terraform is an open-source infrastructure as code tool created by HashiCorp. It supports multiple platforms and has hundreds of providers. Due to its simple configuration language, it has a faster learning curve. It can be easily integrated with configuration management tools like Ansible.
Source code: https://github.com/Anandhi-23/AWS/tree/master/aws_basic_infra_using_terraform
Terraform commands to be executed
terraform init
Downloads the required plugin for the provider and save it locally to a .terraform directory. Terraform must initialize the provider before it can be used.
terraform plan
The terraform plan command is used to create an execution plan. It will not modify things in infrastructure. This command is a convenient way to check whether the execution plan for a set of changes matches your expectations without making any changes to real resources or to the state.
terraform apply
The terraform apply is used to apply the changes required to reach the desired state of the configuration. It will also write the data to the terraform.tfstate file
Make sure to destroy all resources (terraform destroy command can be used) created as part of the above project to avoid any AWS costs.
Subscribe to my newsletter
Read articles from Anandhi directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Anandhi
Anandhi
DevOps enthusiast on a mission to automate, collaborate, and transform software delivery