Accessing employees video recordings via leaked API keys in a public github repository
 Lawrence Mburu
Lawrence MburuIntroduction
I received an invitation to a HackerOne private program. This came after being away from the bug bounty scene for close to 5 months straight. So I decided to take a look in hopes of finding something.
The Target
The program had a small scope. It's main production and staging applications were the only ones in scope, dashboard.redacted.co and staging-dashboard.redacted.co. I created an account in the production app and started checking out the functionalities of the application.
It was day two of testing the application and still could not find anything significant worth reporting. So I decided to switch tactics and do a little bit of recon. Given that only two domains were in scope, I did'nt have much options for recon other than JavaScript analysis and GitHub recon.
GitHub Recon
The program had a GitHub org for sharing their public plugins with the developer community. I navigated all the public repositories looking at the commit history for any information that could be of interest.
After a few hours, one repo piqued my interest, due to references to apiKey parameters. I digged into the source code and managed to find working apiKeys for the staging environment.

Among other attack vectors, the program was also mostly interested in the ability of an attacker to gain access to other users' video recordings. They offered services similar to Google Meets, with the ability of recording meeting sessions which were stored in S3 buckets.
Using a valid apiKey, you could retrieve AWS S3 presigned URLS to download recordings in the S3 buckets via the API if the apiKey had the permissions to. I was lucky in that the apiKey leaked in the GithHub repo had admin permissions across the org, allowing me to retrieve download URLS for every recording in the org.
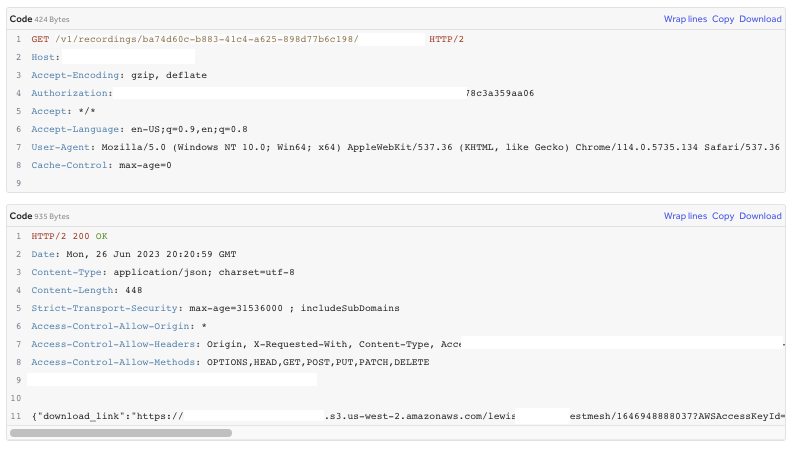
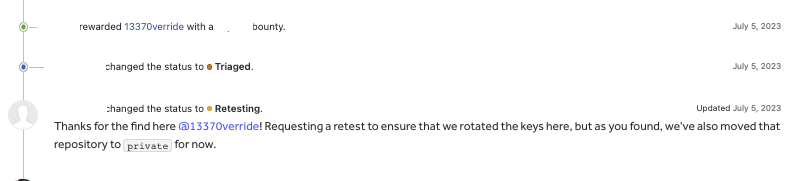
I was able to access meeting recordings of employees of the company, testing new features of the product and having private discussions. I filed a report on HackerOne and they triaged it as a High severity issue, paying a 4 digit bounty and an additional $50 for completing a retest.
Conclusions
It's common to face a target with a narrow scope. In such cases always try to widen the attack surface within limits that could still fall into scope as dictated by the bug bounty program policy.
Subscribe to my newsletter
Read articles from Lawrence Mburu directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
Lawrence Mburu
Lawrence Mburu
I am a DevOps Engineer & Security Researcher. I'm currently working as a Senior DevOps Engineer at BuckHill Software, building infrastructure to support large scale cloud based Insurance software. You can shoot me a message :) consult@webspearsecurity.com.