Exploring Web5: Solution to Identity Control and Data Misplacement
 Julia Ofoegbu
Julia Ofoegbu
Introduction
This article aims to identify the existing problems facing identity management systems globally, loopholes in Web3’s attempt to solve these problems, and the emergence of Web5 - the light at the end of a very long tunnel.
Web2 Giants and Users’ Data
Scenario #1
On the 13th of November 2023, Samsung UK customers received an apology email from the company notifying them of a breach that has led to the exposure of their names, email addresses, phone numbers, postal addresses, and other personal identifiable information. According to the mail sent to the customers (screenshot below), the attackers who were responsible for the breach got unauthorized access to the PII of customers who purchased products from their e-store, Samsung Electronics (UK) Ltd from July 2019 to June 2020 and this was caused by a vulnerability in the third-party application the company used.
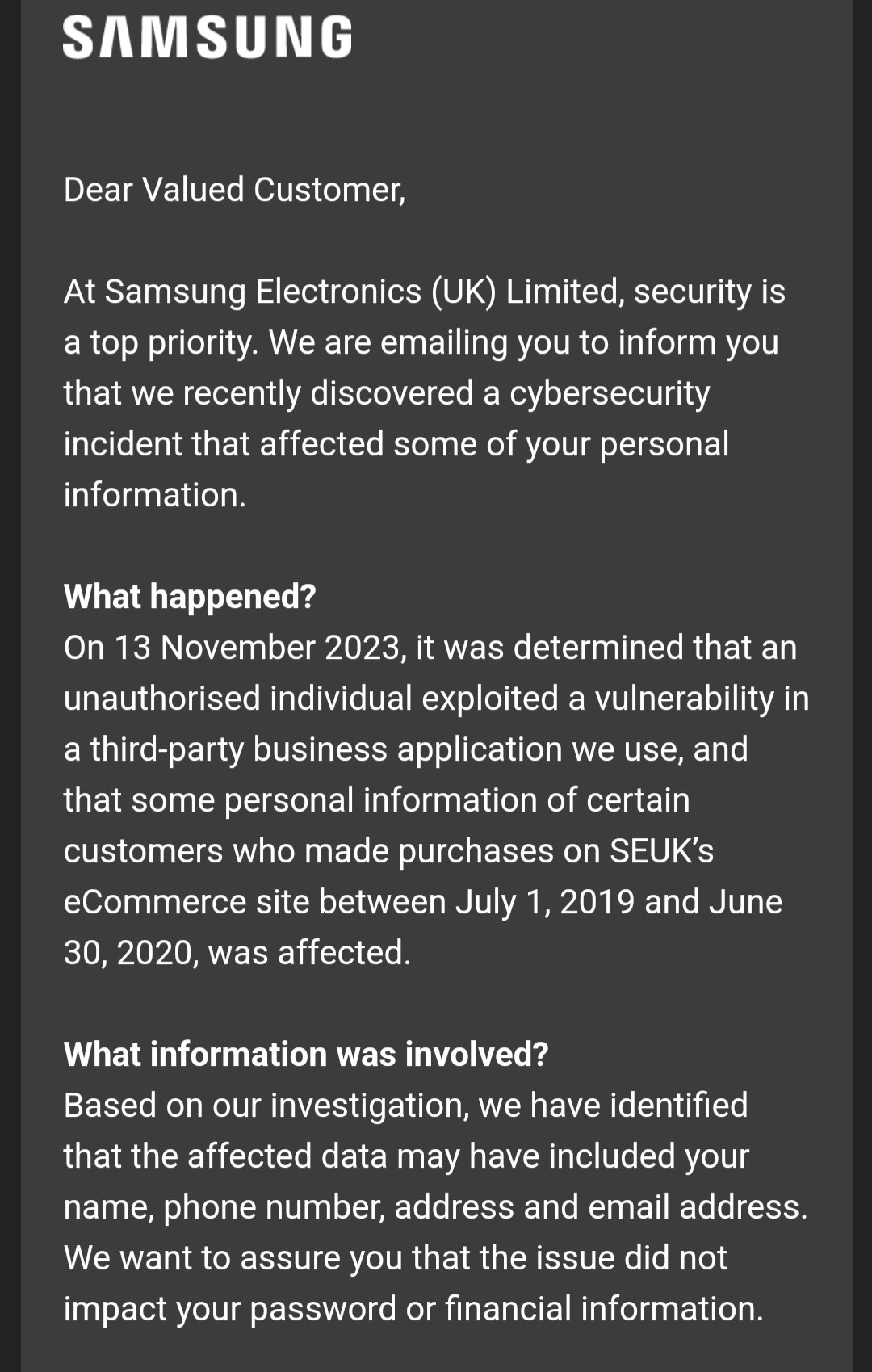
Now here’s the tricky part. Though the breach took place over 3 years ago, Samsung itself only got wind of what happened recently.
The company however reassured their customers that the data breach didn’t affect their passwords or financial information. Maybe Samsung didn’t get the memo but data is the new oil!
What have the attackers been up to with these stolen data? No idea.
Scenario #2
Last month, Spanish’s third-largest airline, Air Europa suffered a data breach on its online payment system that led to customers’ credit card details being exposed. An email sent to the affected individuals advised that they cancel and replace the credit cards as they had been compromised and can be used for future fraudulent activities.
As a matter of fact, that wasn’t the first time the company had suffered a data breach. In 2021, Air Europa was fined for not reporting a data breach that occurred in 2018 which affected 489,000 of its customers within 72 hours of its occurrence as required by its legislation.
Scenario #3
This August, the UK’s Electoral Commission published a statement that notified the public about a cyber attack that had led to illegal access to the personal information of over 40 million people. The attack however occurred over a year ago.
Believe me when I say these three highlighted scenarios are not even close to 1% of data breaches that have been revealed this year, talk more of the ones that have happened over the years. These breaches have affected companies and corporations in various industries.
According to Statista, between November 2021 to October 2022, 5,199 organizations globally experienced data breaches that led to loss of data, and in Q1 of 2023 alone, more than six million data records belonging to individuals worldwide were exposed due to data breaches.
These data breaches have resulted in a number of unfortunate incidents like identity thefts, people’s personal information being exposed on the dark web, impersonation, and more. What’s even worse is that it takes a long period of time for data breaches to be identified, so most times, damages have already been done before the situations can be resolved. Another undiscussed issue is the fact that these web2 giants are not all innocent themselves as some have made millions of dollars illegally selling their customers’ data to the wrong people.
All of these begs the question. When will we stop blaming vulnerabilities on third parties and start taking responsibility?
A look at these problems has led to proposed measures that have, although already implemented, proven futile. Then when web3 found its way, there was a glimmer of hope or was it?
Web3: The Glimmer of Hope…or not?
The term "web3" was coined by Ethereum’s co-founder, Gavin Wood in 2014 and has stuck since then. Basically, web3 implies further evolution of the first version of the web created by Tim Berners-Lee.
It is a decentralized internet built on open-source, distributed ledger technology (blockchain) not owned or controlled by large, centralized entities. This definition insinuates that users will now have more control and freedom over their data and identities as there will be no over-centralization by big companies. Web3 intends to solve the problems of data privacy and ownership. However, the reverse is the case. Many web3 companies are going about it the wrong way.
Web3 which is supposed to be fighting centralization is run mostly by centralized entities.
Web3 products which are supposed to be eliminating the need for third-parties are integrating third-parties in their applications.
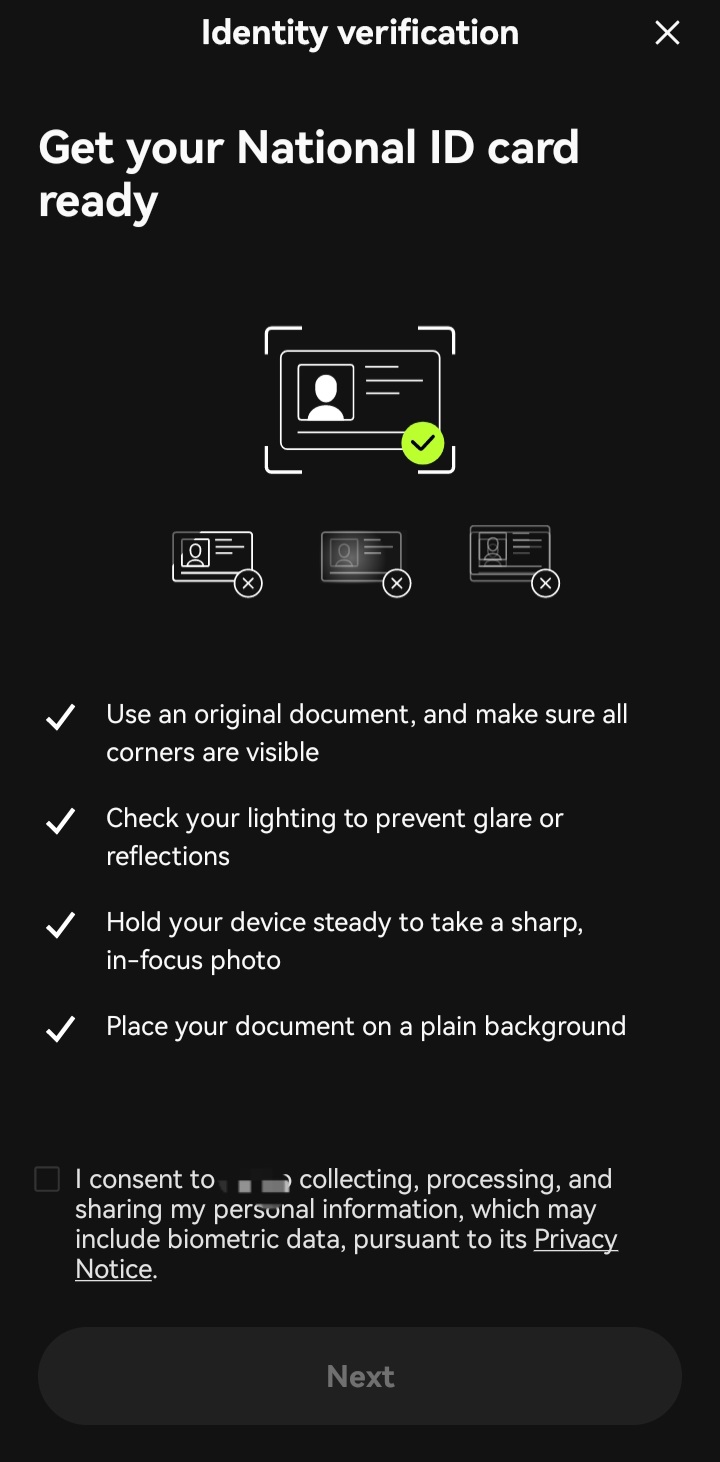
The above image is a screenshot from a crypto wallet I use. In order to perform a certain level of transactions, I needed to verify my KYC. My ID card was my preferred means of identity verification. Now, to further complete my KYC, I was required to take a snapshot of my ID card and to give consent for the information on my ID to be collected by the third-party application that this crypto wallet used. Names are withheld for obvious reasons.
I didn’t fret as this isn’t unusual in the web3 space which is now saturated with centralized companies purporting as decentralized platforms, centralized entities that integrate third-party apps to retrieve users' personal information. Yep, the same web3 that is supposed to be all about decentralization and giving users back ownership and control of their data can’t do without these centralized bodies. So web3, beyond the “decentralization” hype, is still far from its original objective.
Web3, no doubt, has achieved a lot this past decade but it is crystal clear at this point that more needs to be done. The web3 approach of giving users true control over their data and identities needs to be evaluated intensely to see where it all went wrong. This isn’t a call to scrap web3 but rather to improve it in the aspect of true decentralization.
Web5: The Light at the End of a Very Long Tunnel
What seemed like the light at the end of a very long tunnel came last year when the concept of Web5 came alive. On the 10th of June 2022, TBD (@TBD54566975 on X) announced the launch of Web5. TBD is a subsidiary of Block, a company comprising various businesses built on financial technology. It was co-founded by Jack Dorsey, former founder and CEO of Twitter (now X).
Web5, similar to Web3, is a decentralized version of the Internet where users actually get full control of their personal information. However, Web5 combines some features and components of web2 and web3 to make this long-term vision a reality.
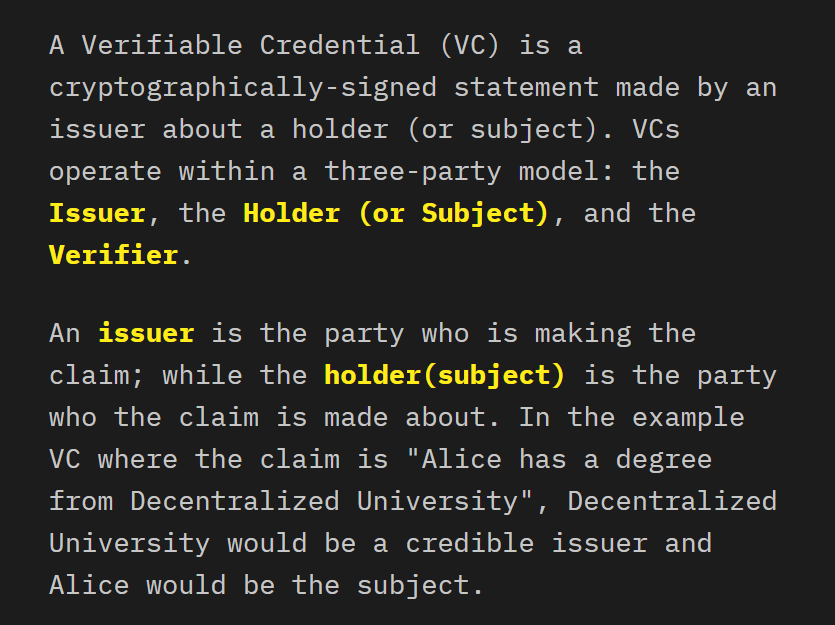
According to the slide presentation released on the launch date, “Web5 is a decentralized web platform that enables developers to leverage Decentralized Identifiers (DIDs), Verifiable Credentials (VCs), and Decentralized Web Nodes (DWNs) to create Decentralized Web Apps (DWAs), returning ownership & control of identity and data back to individuals.”
What are Decentralized Web Apps (DWAs)?
Think of Web5 as a decentralized web infrastructure that aims to relinquish the control that centralized entities have over users by giving them complete power over their online identities and data, thereby empowering them with self-owned identities. If there’s a proper data storage system and a decentralized identity platform, then people’s identities and data wouldn’t be put at risk all the time. Web5 is simply introducing an identity layer to the web.
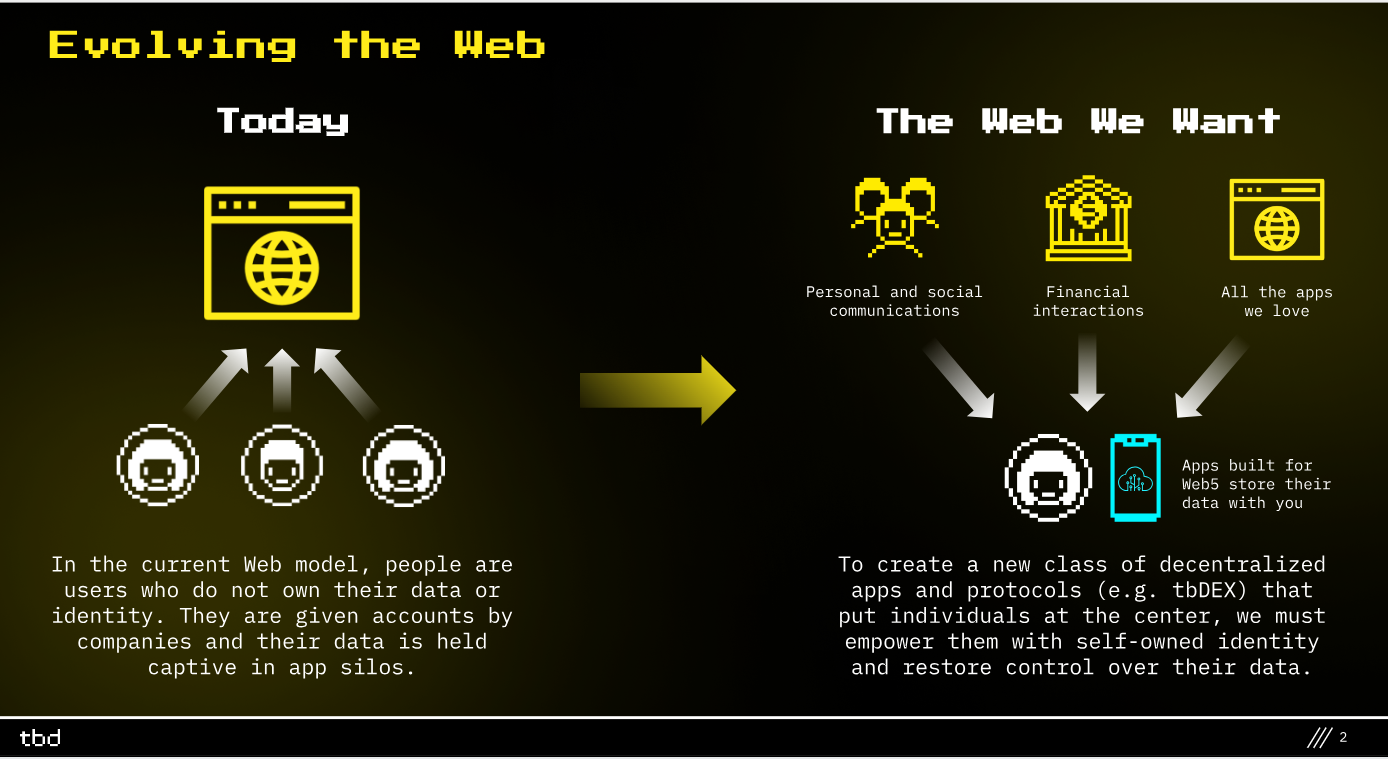
Core Pillars of Web5
There are three major components that developers can employ in building and deploying decentralized web apps that allow users to generate their own identities. This is done with the aid of the Web5 SDK (Software Development Kit).
Decentralized Identifiers (DIDs): these are digital identities created by individuals and also controlled by them, eliminating the constraints of over-reliance on centralized organizations in providing these services.
You could say I have a personal beef with these centralized platforms. I mean, what can I say? I woke up one fine morning earlier this year only to find my Twitter (now X) account suspended for no justifiable cause. That was an account I had been building my personal brand on but I guess the account wasn’t mine to begin with when the platform had full control of my data.
Back to DIDs. They are pieces of information (think email addresses, usernames, phone numbers, etc.) that can be used to easily identify individuals on the decentralized web. Users can keep in contact through their DIDs. Users can also choose whom they share their information with and the specific information to share.
DIDs are represented with a string of alphanumeric characters and are independent of any centralized body as the users themselves create them. They are usually stored on the blockchain which has a permanent record of them.
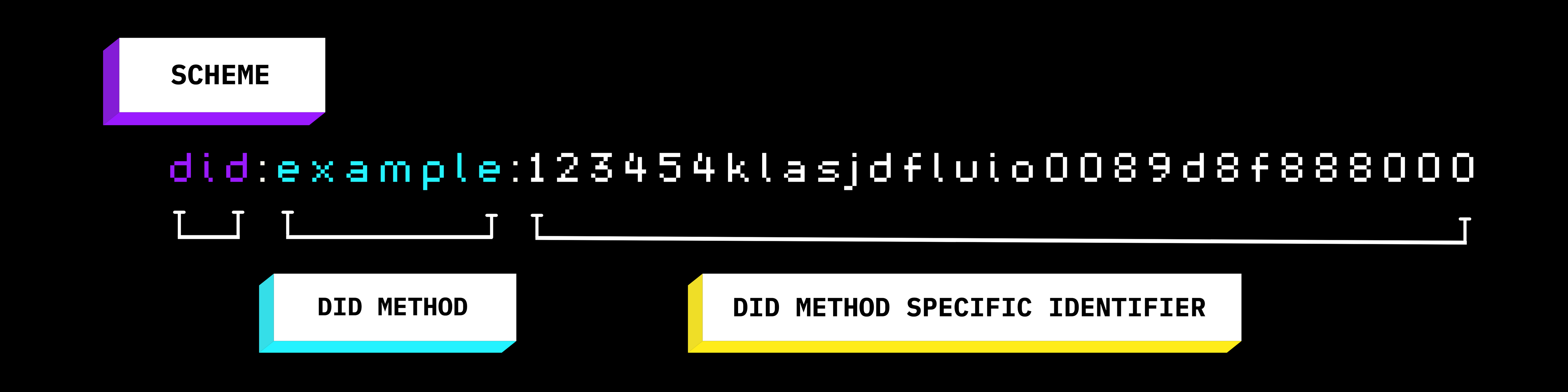
The first three letters “did” indicate that the string of characters is a decentralized identifier.
The next set of alphabets after the first colon represents the methods that the developers used in implementing the DID. There are different methods of implementing DIDs but Web5 currently supports two (did:ion & did:key).
Next is the alphanumeric string of words that is unique to every user.
Verifiable Credentials (VCs): As someone deeply involved in the Web3 space, the moment I read about VCs, my mind immediately related them to Zero Knowledge Proofs (ZKPs) which is the buzzword in the Web3 space these days.
The images below show screenshots explaining what Zero Knowledge Proofs are (for image 1) and what Verifiable Credentials are (for image 2).
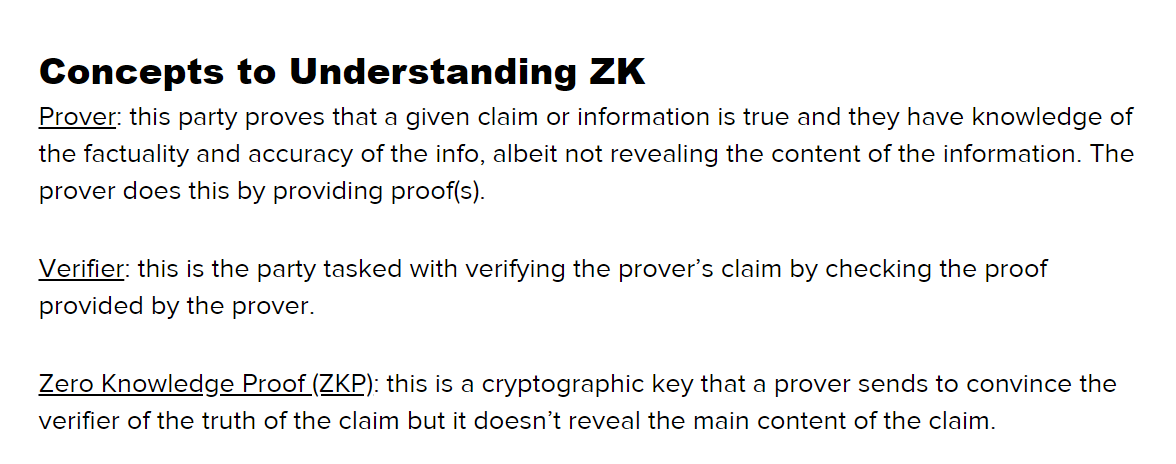
Notice the similarity? VCs, just like ZKPs, are attempts at salvaging identity & data crises.
Practical Use Case:
I read this article where Angie Jones, the Global Vice President of Developer Relations at TBD, shared how she was able to order her favorite wine from a wine store without needing to give any extra personal information about herself, except the fact that she was over 21. She was able to do this with her Louisiana Wallet which uses Verifiable Credentials.
Typically, VCs verify information about people but don’t reveal the contents of the information. This is very helpful indeed. If only I could have proven the authenticity of my ID to that crypto wallet I mentioned earlier without having to reveal the contents of my ID, as they required me to, maybe I’d have been the next to share my VC story. Haha!
So while DIDs are digital identities created and controlled by individuals, VCs are proofs that verify those identities in a way that doesn’t reveal substantial data about the identities.
Decentralized Web Nodes (DWNs): these are decentralized data storages or vaults, if you may. They act as platforms where users with DIDs can store their data/personal information and in addition, communicate with one another (message relay). DWNs can be used to hold both public and privately encoded data. Users have a local DWN (personal node) and also DWNs that are hosted across multiple devices. These nodes are synchronized such that the data in all of them are the same and one going missing doesn’t affect the users.
Think of DWNs this way:
DWN is a vault where all your data and personal information are stored.
You have the vault personally but it is also shared across various networks or devices.
Anytime you want to visit a web or mobile application or a website, you simply connect to your decentralized wallet where your DID exists - no need to input passwords every time.
All interactions you have with the app are stored as data in your DWN and are also stored in your other DWNs spread across multiple networks.
Web5 Projects
There are projects and apps built on Web5 components. Some of them are:
Zion: This is a Web5 social network. It is a peer-to-peer content distribution platform that allows the seamless sharing of content from one party to another without reliance on a third party. This platform makes use of three main technologies: DIDs (for users to create their identities on the platform), DWNs (for users to store their data), and Bitcoin Lightning Network (for payments).
Every user with a Zion account automatically has a Zion wallet attached to it, which is built on the Bitcoin Lightning Network for any transactions that happen within the app.
Damus: “A social network that you can control,” as it is described. This is a social media platform that is built on Nostr - a decentralized, open-source protocol that enables developers to build censorship-resistant social networks. Damus doesn’t require personal information to create an account and it integrates end-to-end encrypted messaging. Users can also send each other Bitcoin directly.
Benefits of Web5
Cases of corporate data mismanagement wouldn’t exist if these companies didn’t have the data in the first place, so, naturally, Web5 wouldn’t appeal to them. The main target is for individuals, me and you.
Here are ways in which Web5 can be beneficial.
Prove the validity of certificates and documents without relying on third parties.
Prevent unwarranted access to users’ data, thereby avoiding impersonation and other crimes.
No need to remember multiple passwords as individuals can use multiple apps with their DID, without needing to log in to every single app they interact with.
Ensures data privacy and protection.
There’s no pressure to invest in any tokens as Web5 doesn’t make use of cryptocurrencies.
Even for organizations, Web5 has some advantages:
It helps save time spent reaching out to issuers to verify the credentials of individuals.
It greatly reduces the problem of certificate fraud.
It keeps organizations in the clear from cyber attacks. According to Statista, the average cost of a data breach across companies worldwide is $4.45 million. If these companies don’t have users' data, there’s no point in an attack.
I really hope you found this article enlightening and insightful. To learn more about Web5, visit the TBD website and go through the docs
Conclusion
The importance of innovative solutions like Web5, when fully implemented and adopted, will immensely affect the way things are done, changing the status quo. While some may argue that Web3 hasn’t even started, some would question what happened to Web4, while others (like Snoop Dogg) would joke about launching a Web6, the fact still remains that as long as humans exist, there will be a constant hunger for change and improvements. Such is what we’re experiencing with Web5.
References
https://developer.tbd.website/blog/what-is-web5
https://developer.tbd.website/docs/
http://developer.tbd.websitedeveloper.tbd.website
An Intro into TBD's Web5 and Decentralized Web Nodes:
https://youtu.be/Vw3i2LeVa_Y?si=mBUk554rm10m9naQ
What Is Web5 & How Is It Different From Web3?
What Is Web5?
Subscribe to my newsletter
Read articles from Julia Ofoegbu directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Julia Ofoegbu
Julia Ofoegbu
I'm Julia, a web3 researcher and content writer. I explore blockchain protocols and write extensively about them such that non-technical readers can easily comprehend.