My Knowledge On Web5 So Far
 Balikis bamgbose
Balikis bamgboseWeb5 is a decentralized version of the internet where users store their own personal information and can revoke access at will.
Tuesday, November 20th, was the first time I heard about Web5 when I joined the broadcast on Twitch with Rizel, a dev advocate at TBD. She took me through the journey of what it means to be decentralized, after which I did my research and got to know that there is a way to own data using Web5, which actually gives the owner control over his or her own data, and storing data in DWN using the CRUD concept and the DID, which is an address representing who you are on the decentralized web. It can point to a person, organization, thing, data model, or abstract entity. It is through DID that others can send messages and data and be granted access to the information one wishes to share. It is also a "type of identifier that enables verifiable, decentralized digital identity" (DID Core Spec). It is created and managed independently of any centralized authority or organization. The idea behind a DID is to give individuals and organizations control over their own identity information and to allow them to share that information selectively and securely with others as needed. Which means that they can choose when and how to share their identity information and with whom.
DIDs are typically represented as a unique resource identifier (URI) and are designed to be used for identity verification, authentication, and authorization.
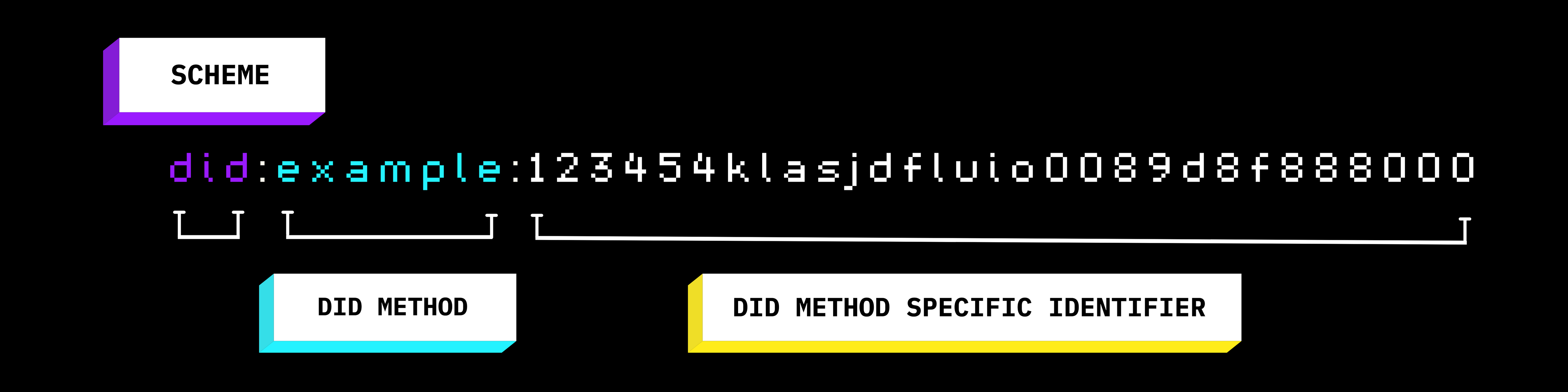
Example of a Decentralized Identifier
The key difference between a traditional centralized identifier, such as a username or email address, and a decentralized identifier is that the latter is not tied to a specific service provider or organization. An example of a centralized identifier you might have would be your Twitter handle or Google email address, where Twitter or Google are the centralized authorities. I went through “On Wednesday we use Web5: A “Mean Girls” Guide to Data Sovereignty,” which was the title of Rizel's broadcast, and the journey of the mean girls and how one of them exposes their secret book. She said we were supposed to build an app to help control that. We set up our environment and wrote some code snippets, which was cool. I was surprised to see how it works perfectly on whatever we give permission for, and she said we can use Web5 to build quite a number of things. We end the section with a quick recap game on [Kahoot.It](file:///C:/Users/IBCIRC~1/AppData/Local/Temp/msohtmlclip1/01/clip_filelist.xml).
Lets get to know what DID document is
What is a DID document?
A DID essentially acts as a URI that associates the subject of the DID (the person, company, or object being identified) with a DID document that lives off-chain in a decentralized storage system such as IPFS.
A DID document is a mini-profile for its DID subject. They are JSON files that serve as a self-contained representation of the DID and provide metadata and cryptographic material associated with the DID.
DID documents define how to engage with the DID subject and provide information that helps others validate the validity and integrity of the DID's data. The document contains information such as the DID subject's public keys, authentication and verification mechanisms, and service endpoints such as DWNs that refer to the subject's data locations.
How to Retrieve a DID Document
If a person tries to identify themselves using their DID in an app, the app will resolve their DID to retrieve their mini-profile (the DID document).
In Web5, you'd use the web5.did.resolve() function to accomplish this:
const resolution = await web5.did.resolve(userDid);
const didDocument = resolution.didDocument;
Theresolve function will return aDidResolutionResult, which contains the DIDocument object:
{
"id": "did:ion:EiBMIz-Hhom0_8EUaWLuscD08Riy0Fo5vp8mCXxszy5Gfg:eyJkZWx0YSI6eyJwYXRjaGVzIjpbeyJhY3Rpb24iOiJyZXBsYWNlIiwiZG9jdW1lbnQiOnsicHVibGljS2V5cyI6W3siaWQiOiJhdXRoeiIsInB1YmxpY0tleUp3ayI6eyJjcnYiOiJzZWNwMjU2azEiLCJrdHkiOiJFQyIsIngiOiJ3endxSEY3cEtzS3dkR3NBNkhpS0dyUGRaQ0FoYW9oeGxJS1JraDhGWjZNIiwieSI6ImVsY0tHbnpMTjNsVnpYWHV6YUk3WWFrWVI3MXBxNnBMbzNUNFRVaERJYXMifSwicHVycG9zZXMiOlsiYXV0aGVudGljYXRpb24iXSwidHlwZSI6Ikpzb25XZWJLZXkyMDIwIn0seyJpZCI6ImVuYyIsInB1YmxpY0tleUp3ayI6eyJjcnYiOiJzZWNwMjU2azEiLCJrdHkiOiJFQyIsIngiOiJuOVRDSEtNZS04Z1J6cl9YMC1XZVF1VzlyM1VGNlhZd1pscEtZTnVVdzhBIiwieSI6Im5UTEgxUS1OR05OMy0ySkxyWW9PMnNDSEdUcndpMXVqR0dNSEdKV3ZSNVkifSwicHVycG9zZXMiOlsia2V5QWdyZWVtZW50Il0sInR5cGUiOiJKc29uV2ViS2V5MjAyMCJ9XSwic2VydmljZXMiOlt7ImlkIjoiZHduIiwic2VydmljZUVuZHBvaW50Ijp7Im1lc3NhZ2VBdXRob3JpemF0aW9uS2V5cyI6WyIjYXV0aHoiXSwibm9kZXMiOlsiaHR0cHM6Ly9kd24udGJkZGV2Lm9yZy9kd24xIiwiaHR0cHM6Ly9kd24udGJkZGV2Lm9yZy9kd24yIl0sInJlY29yZEVuY3J5cHRpb25LZXlzIjpbIiNlbmMiXX0sInR5cGUiOiJEZWNlbnRyYWxpemVkV2ViTm9kZSJ9XX19XSwidXBkYXRlQ29tbWl0bWVudCI6IkVpRDJYTV9mRzQ2eFI4NDJVTjRzMTFOTU80LTEzbkwxdXdUVko1cGVVWFFicmcifSwic3VmZml4RGF0YSI6eyJkZWx0YUhhc2giOiJFaUJWLVQyU1dwWGI2bldwVlpyQXUwYTF3Q2hQdS1tRXJMaWtORWpSZ3VQa2hBIiwicmVjb3ZlcnlDb21taXRtZW50IjoiRWlBcGRSR1U4X2JkQ3oyZFpfR1R3QnZGOWw1ZXNRUWFqbXRjN3REdzcxTUUyQSJ9fQ",
"@context": [
"https://www.w3.org/ns/did/v1",
{
"@base": "did:ion:EiBMIz-Hhom0_8EUaWLuscD08Riy0Fo5vp8mCXxszy5Gfg:eyJkZWx0YSI6eyJwYXRjaGVzIjpbeyJhY3Rpb24iOiJyZXBsYWNlIiwiZG9jdW1lbnQiOnsicHVibGljS2V5cyI6W3siaWQiOiJhdXRoeiIsInB1YmxpY0tleUp3ayI6eyJjcnYiOiJzZWNwMjU2azEiLCJrdHkiOiJFQyIsIngiOiJ3endxSEY3cEtzS3dkR3NBNkhpS0dyUGRaQ0FoYW9oeGxJS1JraDhGWjZNIiwieSI6ImVsY0tHbnpMTjNsVnpYWHV6YUk3WWFrWVI3MXBxNnBMbzNUNFRVaERJYXMifSwicHVycG9zZXMiOlsiYXV0aGVudGljYXRpb24iXSwidHlwZSI6Ikpzb25XZWJLZXkyMDIwIn0seyJpZCI6ImVuYyIsInB1YmxpY0tleUp3ayI6eyJjcnYiOiJzZWNwMjU2azEiLCJrdHkiOiJFQyIsIngiOiJuOVRDSEtNZS04Z1J6cl9YMC1XZVF1VzlyM1VGNlhZd1pscEtZTnVVdzhBIiwieSI6Im5UTEgxUS1OR05OMy0ySkxyWW9PMnNDSEdUcndpMXVqR0dNSEdKV3ZSNVkifSwicHVycG9zZXMiOlsia2V5QWdyZWVtZW50Il0sInR5cGUiOiJKc29uV2ViS2V5MjAyMCJ9XSwic2VydmljZXMiOlt7ImlkIjoiZHduIiwic2VydmljZUVuZHBvaW50Ijp7Im1lc3NhZ2VBdXRob3JpemF0aW9uS2V5cyI6WyIjYXV0aHoiXSwibm9kZXMiOlsiaHR0cHM6Ly9kd24udGJkZGV2Lm9yZy9kd24xIiwiaHR0cHM6Ly9kd24udGJkZGV2Lm9yZy9kd24yIl0sInJlY29yZEVuY3J5cHRpb25LZXlzIjpbIiNlbmMiXX0sInR5cGUiOiJEZWNlbnRyYWxpemVkV2ViTm9kZSJ9XX19XSwidXBkYXRlQ29tbWl0bWVudCI6IkVpRDJYTV9mRzQ2eFI4NDJVTjRzMTFOTU80LTEzbkwxdXdUVko1cGVVWFFicmcifSwic3VmZml4RGF0YSI6eyJkZWx0YUhhc2giOiJFaUJWLVQyU1dwWGI2bldwVlpyQXUwYTF3Q2hQdS1tRXJMaWtORWpSZ3VQa2hBIiwicmVjb3ZlcnlDb21taXRtZW50IjoiRWlBcGRSR1U4X2JkQ3oyZFpfR1R3QnZGOWw1ZXNRUWFqbXRjN3REdzcxTUUyQSJ9fQ"
}
],
"service": [
{
"id": "#dwn",
"type": "DecentralizedWebNode",
"serviceEndpoint": {
"messageAuthorizationKeys": ["#authz"],
"nodes": ["https://dwn.tbddev.org/dwn1", "https://dwn.tbddev.org/dwn2"],
"recordEncryptionKeys": ["#enc"]
}
}
],
"verificationMethod": [
{
"id": "#authz",
"controller": "did:ion:EiBMIz-Hhom0_8EUaWLuscD08Riy0Fo5vp8mCXxszy5Gfg:eyJkZWx0YSI6eyJwYXRjaGVzIjpbeyJhY3Rpb24iOiJyZXBsYWNlIiwiZG9jdW1lbnQiOnsicHVibGljS2V5cyI6W3siaWQiOiJhdXRoeiIsInB1YmxpY0tleUp3ayI6eyJjcnYiOiJzZWNwMjU2azEiLCJrdHkiOiJFQyIsIngiOiJ3endxSEY3cEtzS3dkR3NBNkhpS0dyUGRaQ0FoYW9oeGxJS1JraDhGWjZNIiwieSI6ImVsY0tHbnpMTjNsVnpYWHV6YUk3WWFrWVI3MXBxNnBMbzNUNFRVaERJYXMifSwicHVycG9zZXMiOlsiYXV0aGVudGljYXRpb24iXSwidHlwZSI6Ikpzb25XZWJLZXkyMDIwIn0seyJpZCI6ImVuYyIsInB1YmxpY0tleUp3ayI6eyJjcnYiOiJzZWNwMjU2azEiLCJrdHkiOiJFQyIsIngiOiJuOVRDSEtNZS04Z1J6cl9YMC1XZVF1VzlyM1VGNlhZd1pscEtZTnVVdzhBIiwieSI6Im5UTEgxUS1OR05OMy0ySkxyWW9PMnNDSEdUcndpMXVqR0dNSEdKV3ZSNVkifSwicHVycG9zZXMiOlsia2V5QWdyZWVtZW50Il0sInR5cGUiOiJKc29uV2ViS2V5MjAyMCJ9XSwic2VydmljZXMiOlt7ImlkIjoiZHduIiwic2VydmljZUVuZHBvaW50Ijp7Im1lc3NhZ2VBdXRob3JpemF0aW9uS2V5cyI6WyIjYXV0aHoiXSwibm9kZXMiOlsiaHR0cHM6Ly9kd24udGJkZGV2Lm9yZy9kd24xIiwiaHR0cHM6Ly9kd24udGJkZGV2Lm9yZy9kd24yIl0sInJlY29yZEVuY3J5cHRpb25LZXlzIjpbIiNlbmMiXX0sInR5cGUiOiJEZWNlbnRyYWxpemVkV2ViTm9kZSJ9XX19XSwidXBkYXRlQ29tbWl0bWVudCI6IkVpRDJYTV9mRzQ2eFI4NDJVTjRzMTFOTU80LTEzbkwxdXdUVko1cGVVWFFicmcifSwic3VmZml4RGF0YSI6eyJkZWx0YUhhc2giOiJFaUJWLVQyU1dwWGI2bldwVlpyQXUwYTF3Q2hQdS1tRXJMaWtORWpSZ3VQa2hBIiwicmVjb3ZlcnlDb21taXRtZW50IjoiRWlBcGRSR1U4X2JkQ3oyZFpfR1R3QnZGOWw1ZXNRUWFqbXRjN3REdzcxTUUyQSJ9fQ",
"type": "JsonWebKey2020",
"publicKeyJwk": {
"crv": "secp256k1",
"kty": "EC",
"x": "wzwqHF7pKsKwdGsA6HiKGrPdZCAhaohxlIKRkh8FZ6M",
"y": "elcKGnzLN3lVzXXuzaI7YakYR71pq6pLo3T4TUhDIas"
}
},
{
"id": "#enc",
"controller": "did:ion:EiBMIz-Hhom0_8EUaWLuscD08Riy0Fo5vp8mCXxszy5Gfg:eyJkZWx0YSI6eyJwYXRjaGVzIjpbeyJhY3Rpb24iOiJyZXBsYWNlIiwiZG9jdW1lbnQiOnsicHVibGljS2V5cyI6W3siaWQiOiJhdXRoeiIsInB1YmxpY0tleUp3ayI6eyJjcnYiOiJzZWNwMjU2azEiLCJrdHkiOiJFQyIsIngiOiJ3endxSEY3cEtzS3dkR3NBNkhpS0dyUGRaQ0FoYW9oeGxJS1JraDhGWjZNIiwieSI6ImVsY0tHbnpMTjNsVnpYWHV6YUk3WWFrWVI3MXBxNnBMbzNUNFRVaERJYXMifSwicHVycG9zZXMiOlsiYXV0aGVudGljYXRpb24iXSwidHlwZSI6Ikpzb25XZWJLZXkyMDIwIn0seyJpZCI6ImVuYyIsInB1YmxpY0tleUp3ayI6eyJjcnYiOiJzZWNwMjU2azEiLCJrdHkiOiJFQyIsIngiOiJuOVRDSEtNZS04Z1J6cl9YMC1XZVF1VzlyM1VGNlhZd1pscEtZTnVVdzhBIiwieSI6Im5UTEgxUS1OR05OMy0ySkxyWW9PMnNDSEdUcndpMXVqR0dNSEdKV3ZSNVkifSwicHVycG9zZXMiOlsia2V5QWdyZWVtZW50Il0sInR5cGUiOiJKc29uV2ViS2V5MjAyMCJ9XSwic2VydmljZXMiOlt7ImlkIjoiZHduIiwic2VydmljZUVuZHBvaW50Ijp7Im1lc3NhZ2VBdXRob3JpemF0aW9uS2V5cyI6WyIjYXV0aHoiXSwibm9kZXMiOlsiaHR0cHM6Ly9kd24udGJkZGV2Lm9yZy9kd24xIiwiaHR0cHM6Ly9kd24udGJkZGV2Lm9yZy9kd24yIl0sInJlY29yZEVuY3J5cHRpb25LZXlzIjpbIiNlbmMiXX0sInR5cGUiOiJEZWNlbnRyYWxpemVkV2ViTm9kZSJ9XX19XSwidXBkYXRlQ29tbWl0bWVudCI6IkVpRDJYTV9mRzQ2eFI4NDJVTjRzMTFOTU80LTEzbkwxdXdUVko1cGVVWFFicmcifSwic3VmZml4RGF0YSI6eyJkZWx0YUhhc2giOiJFaUJWLVQyU1dwWGI2bldwVlpyQXUwYTF3Q2hQdS1tRXJMaWtORWpSZ3VQa2hBIiwicmVjb3ZlcnlDb21taXRtZW50IjoiRWlBcGRSR1U4X2JkQ3oyZFpfR1R3QnZGOWw1ZXNRUWFqbXRjN3REdzcxTUUyQSJ9fQ",
"type": "JsonWebKey2020",
"publicKeyJwk": {
"crv": "secp256k1",
"kty": "EC",
"x": "n9TCHKMe-8gRzr_X0-WeQuW9r3UF6XYwZlpKYNuUw8A",
"y": "nTLH1Q-NGNN3-2JLrYoO2sCHGTrwi1ujGGMHGJWvR5Y"
}
}
]
}
NOTE
Outside of Web5, you can use DIF's Universal Resolver to resolve DIDs.
The Characteristics of a DID Document
A DID document's main components are:
id: The DID document's unique identifier, which is the same as the DID it represents.
"id": "did:ion:EiBMIz-Hhom0_8EUaWLuscD08Riy0Fo5vp8mCXxszy5Gfg:eyJkZWx0YSI6eyJwYXRjaGVzIjpbeyJhY3Rpb24iOiJyZXBsYWNlIiwiZG9jdW1lbnQiOnsicHVibGljS2V5cyI6W3siaWQiOiJhdXRoeiIsInB1YmxpY0tleUp3ayI6eyJjcnYiOiJzZWNwMjU2azEiLCJrdHkiOiJFQyIsIngiOiJ3endxSEY3cEtzS3dkR3NBNkhpS0dyUGRaQ0FoYW9oeGxJS1JraDhGWjZNIiwieSI6ImVsY0tHbnpMTjNsVnpYWHV6YUk3WWFrWVI3MXBxNnBMbzNUNFRVaERJYXMifSwicHVycG9zZXMiOlsiYXV0aGVudGljYXRpb24iXSwidHlwZSI6Ikpzb25XZWJLZXkyMDIwIn0seyJpZCI6ImVuYyIsInB1YmxpY0tleUp3ayI6eyJjcnYiOiJzZWNwMjU2azEiLCJrdHkiOiJFQyIsIngiOiJuOVRDSEtNZS04Z1J6cl9YMC1XZVF1VzlyM1VGNlhZd1pscEtZTnVVdzhBIiwieSI6Im5UTEgxUS1OR05OMy0ySkxyWW9PMnNDSEdUcndpMXVqR0dNSEdKV3ZSNVkifSwicHVycG9zZXMiOlsia2V5QWdyZWVtZW50Il0sInR5cGUiOiJKc29uV2ViS2V5MjAyMCJ9XSwic2VydmljZXMiOlt7ImlkIjoiZHduIiwic2VydmljZUVuZHBvaW50Ijp7Im1lc3NhZ2VBdXRob3JpemF0aW9uS2V5cyI6WyIjYXV0aHoiXSwibm9kZXMiOlsiaHR0cHM6Ly9kd24udGJkZGV2Lm9yZy9kd24xIiwiaHR0cHM6Ly9kd24udGJkZGV2Lm9yZy9kd24yIl0sInJlY29yZEVuY3J5cHRpb25LZXlzIjpbIiNlbmMiXX0sInR5cGUiOiJEZWNlbnRyYWxpemVkV2ViTm9kZSJ9XX19XSwidXBkYXRlQ29tbWl0bWVudCI6IkVpRDJYTV9mRzQ2eFI4NDJVTjRzMTFOTU80LTEzbkwxdXdUVko1cGVVWFFicmcifSwic3VmZml4RGF0YSI6eyJkZWx0YUhhc2giOiJFaUJWLVQyU1dwWGI2bldwVlpyQXUwYTF3Q2hQdS1tRXJMaWtORWpSZ3VQa2hBIiwicmVjb3ZlcnlDb21taXRtZW50IjoiRWlBcGRSR1U4X2JkQ3oyZFpfR1R3QnZGOWw1ZXNRUWFqbXRjN3REdzcxTUUyQSJ9fQ"
@context: A context definition for the DID document. It has two elements: the standard DID context definition and an object that provides a base identifier.
"@context": [
"https://www.w3.org/ns/did/v1",
{
"@base": "did:ion:EiBMIz-Hhom0_8EUaWLuscD08Riy0Fo5vp8mCXxszy5Gfg:eyJkZWx0YSI6eyJwYXRjaGVzIjpbeyJhY3Rpb24iOiJyZXBsYWNlIiwiZG9jdW1lbnQiOnsicHVibGljS2V5cyI6W3siaWQiOiJhdXRoeiIsInB1YmxpY0tleUp3ayI6eyJjcnYiOiJzZWNwMjU2azEiLCJrdHkiOiJFQyIsIngiOiJ3endxSEY3cEtzS3dkR3NBNkhpS0dyUGRaQ0FoYW9oeGxJS1JraDhGWjZNIiwieSI6ImVsY0tHbnpMTjNsVnpYWHV6YUk3WWFrWVI3MXBxNnBMbzNUNFRVaERJYXMifSwicHVycG9zZXMiOlsiYXV0aGVudGljYXRpb24iXSwidHlwZSI6Ikpzb25XZWJLZXkyMDIwIn0seyJpZCI6ImVuYyIsInB1YmxpY0tleUp3ayI6eyJjcnYiOiJzZWNwMjU2azEiLCJrdHkiOiJFQyIsIngiOiJuOVRDSEtNZS04Z1J6cl9YMC1XZVF1VzlyM1VGNlhZd1pscEtZTnVVdzhBIiwieSI6Im5UTEgxUS1OR05OMy0ySkxyWW9PMnNDSEdUcndpMXVqR0dNSEdKV3ZSNVkifSwicHVycG9zZXMiOlsia2V5QWdyZWVtZW50Il0sInR5cGUiOiJKc29uV2ViS2V5MjAyMCJ9XSwic2VydmljZXMiOlt7ImlkIjoiZHduIiwic2VydmljZUVuZHBvaW50Ijp7Im1lc3NhZ2VBdXRob3JpemF0aW9uS2V5cyI6WyIjYXV0aHoiXSwibm9kZXMiOlsiaHR0cHM6Ly9kd24udGJkZGV2Lm9yZy9kd24xIiwiaHR0cHM6Ly9kd24udGJkZGV2Lm9yZy9kd24yIl0sInJlY29yZEVuY3J5cHRpb25LZXlzIjpbIiNlbmMiXX0sInR5cGUiOiJEZWNlbnRyYWxpemVkV2ViTm9kZSJ9XX19XSwidXBkYXRlQ29tbWl0bWVudCI6IkVpRDJYTV9mRzQ2eFI4NDJVTjRzMTFOTU80LTEzbkwxdXdUVko1cGVVWFFicmcifSwic3VmZml4RGF0YSI6eyJkZWx0YUhhc2giOiJFaUJWLVQyU1dwWGI2bldwVlpyQXUwYTF3Q2hQdS1tRXJMaWtORWpSZ3VQa2hBIiwicmVjb3ZlcnlDb21taXRtZW50IjoiRWlBcGRSR1U4X2JkQ3oyZFpfR1R3QnZGOWw1ZXNRUWFqbXRjN3REdzcxTUUyQSJ9fQ"
}
]
service: a method of interacting or connecting with the DID topic. Each service entry has an ID, type, and URI for the service endpoint. DWN is the only service available in this scenario. The serviceEndpoint specifies URIs for the DID subject's web nodes, which the app uses to determine where the user's data stores are located.
"service": [
{
"id": "#dwn",
"type": "DecentralizedWebNode",
"serviceEndpoint": {
"messageAuthorizationKeys": ["#authz"],
"nodes": ["https://dwn.tbddev.org/dwn1", "https://dwn.tbddev.org/dwn2"],
"recordEncryptionKeys": ["#enc"]
}
}
]
verificationMethod: An array of methods for verifying the DID subject is who they say they are. In this example, there are two methods: authz and enc. Both methods contain:
ID: Identifier of the verification method within this DID document
controller: A reference to the DID that controls this verification method
type: The type of key (in this case, JsonWebKey2020)
publicKeyJwk: A JSON Web Key (JWK) representation of the cryptographic public key in a format suitable for use in web-based protocols and applications
"verificationMethod": [
{
"id": "#authz",
"controller": "did:ion:EiBMIz-Hhom0_8EUaWLuscD08Riy0Fo5vp8mCXxszy5Gfg:eyJkZWx0YSI6eyJwYXRjaGVzIjpbeyJhY3Rpb24iOiJyZXBsYWNlIiwiZG9jdW1lbnQiOnsicHVibGljS2V5cyI6W3siaWQiOiJhdXRoeiIsInB1YmxpY0tleUp3ayI6eyJjcnYiOiJzZWNwMjU2azEiLCJrdHkiOiJFQyIsIngiOiJ3endxSEY3cEtzS3dkR3NBNkhpS0dyUGRaQ0FoYW9oeGxJS1JraDhGWjZNIiwieSI6ImVsY0tHbnpMTjNsVnpYWHV6YUk3WWFrWVI3MXBxNnBMbzNUNFRVaERJYXMifSwicHVycG9zZXMiOlsiYXV0aGVudGljYXRpb24iXSwidHlwZSI6Ikpzb25XZWJLZXkyMDIwIn0seyJpZCI6ImVuYyIsInB1YmxpY0tleUp3ayI6eyJjcnYiOiJzZWNwMjU2azEiLCJrdHkiOiJFQyIsIngiOiJuOVRDSEtNZS04Z1J6cl9YMC1XZVF1VzlyM1VGNlhZd1pscEtZTnVVdzhBIiwieSI6Im5UTEgxUS1OR05OMy0ySkxyWW9PMnNDSEdUcndpMXVqR0dNSEdKV3ZSNVkifSwicHVycG9zZXMiOlsia2V5QWdyZWVtZW50Il0sInR5cGUiOiJKc29uV2ViS2V5MjAyMCJ9XSwic2VydmljZXMiOlt7ImlkIjoiZHduIiwic2VydmljZUVuZHBvaW50Ijp7Im1lc3NhZ2VBdXRob3JpemF0aW9uS2V5cyI6WyIjYXV0aHoiXSwibm9kZXMiOlsiaHR0cHM6Ly9kd24udGJkZGV2Lm9yZy9kd24xIiwiaHR0cHM6Ly9kd24udGJkZGV2Lm9yZy9kd24yIl0sInJlY29yZEVuY3J5cHRpb25LZXlzIjpbIiNlbmMiXX0sInR5cGUiOiJEZWNlbnRyYWxpemVkV2ViTm9kZSJ9XX19XSwidXBkYXRlQ29tbWl0bWVudCI6IkVpRDJYTV9mRzQ2eFI4NDJVTjRzMTFOTU80LTEzbkwxdXdUVko1cGVVWFFicmcifSwic3VmZml4RGF0YSI6eyJkZWx0YUhhc2giOiJFaUJWLVQyU1dwWGI2bldwVlpyQXUwYTF3Q2hQdS1tRXJMaWtORWpSZ3VQa2hBIiwicmVjb3ZlcnlDb21taXRtZW50IjoiRWlBcGRSR1U4X2JkQ3oyZFpfR1R3QnZGOWw1ZXNRUWFqbXRjN3REdzcxTUUyQSJ9fQ",
"type": "JsonWebKey2020",
"publicKeyJwk": {
"crv": "secp256k1",
"kty": "EC",
"x": "wzwqHF7pKsKwdGsA6HiKGrPdZCAhaohxlIKRkh8FZ6M",
"y": "elcKGnzLN3lVzXXuzaI7YakYR71pq6pLo3T4TUhDIas"
}
},
{
"id": "#enc",
"controller": "did:ion:EiBMIz-Hhom0_8EUaWLuscD08Riy0Fo5vp8mCXxszy5Gfg:eyJkZWx0YSI6eyJwYXRjaGVzIjpbeyJhY3Rpb24iOiJyZXBsYWNlIiwiZG9jdW1lbnQiOnsicHVibGljS2V5cyI6W3siaWQiOiJhdXRoeiIsInB1YmxpY0tleUp3ayI6eyJjcnYiOiJzZWNwMjU2azEiLCJrdHkiOiJFQyIsIngiOiJ3endxSEY3cEtzS3dkR3NBNkhpS0dyUGRaQ0FoYW9oeGxJS1JraDhGWjZNIiwieSI6ImVsY0tHbnpMTjNsVnpYWHV6YUk3WWFrWVI3MXBxNnBMbzNUNFRVaERJYXMifSwicHVycG9zZXMiOlsiYXV0aGVudGljYXRpb24iXSwidHlwZSI6Ikpzb25XZWJLZXkyMDIwIn0seyJpZCI6ImVuYyIsInB1YmxpY0tleUp3ayI6eyJjcnYiOiJzZWNwMjU2azEiLCJrdHkiOiJFQyIsIngiOiJuOVRDSEtNZS04Z1J6cl9YMC1XZVF1VzlyM1VGNlhZd1pscEtZTnVVdzhBIiwieSI6Im5UTEgxUS1OR05OMy0ySkxyWW9PMnNDSEdUcndpMXVqR0dNSEdKV3ZSNVkifSwicHVycG9zZXMiOlsia2V5QWdyZWVtZW50Il0sInR5cGUiOiJKc29uV2ViS2V5MjAyMCJ9XSwic2VydmljZXMiOlt7ImlkIjoiZHduIiwic2VydmljZUVuZHBvaW50Ijp7Im1lc3NhZ2VBdXRob3JpemF0aW9uS2V5cyI6WyIjYXV0aHoiXSwibm9kZXMiOlsiaHR0cHM6Ly9kd24udGJkZGV2Lm9yZy9kd24xIiwiaHR0cHM6Ly9kd24udGJkZGV2Lm9yZy9kd24yIl0sInJlY29yZEVuY3J5cHRpb25LZXlzIjpbIiNlbmMiXX0sInR5cGUiOiJEZWNlbnRyYWxpemVkV2ViTm9kZSJ9XX19XSwidXBkYXRlQ29tbWl0bWVudCI6IkVpRDJYTV9mRzQ2eFI4NDJVTjRzMTFOTU80LTEzbkwxdXdUVko1cGVVWFFicmcifSwic3VmZml4RGF0YSI6eyJkZWx0YUhhc2giOiJFaUJWLVQyU1dwWGI2bldwVlpyQXUwYTF3Q2hQdS1tRXJMaWtORWpSZ3VQa2hBIiwicmVjb3ZlcnlDb21taXRtZW50IjoiRWlBcGRSR1U4X2JkQ3oyZFpfR1R3QnZGOWw1ZXNRUWFqbXRjN3REdzcxTUUyQSJ9fQ",
"type": "JsonWebKey2020",
"publicKeyJwk": {
"crv": "secp256k1",
"kty": "EC",
"x": "n9TCHKMe-8gRzr_X0-WeQuW9r3UF6XYwZlpKYNuUw8A",
"y": "nTLH1Q-NGNN3-2JLrYoO2sCHGTrwi1ujGGMHGJWvR5Y"
}
}
]
These are just some of the common fields you might encounter in a DID document. The structure and contents of a DID document can vary depending on the specific DID method being used and the requirements of the application or use case.
DID Document Management
Maintaining the integrity, usefulness, and security of a DID document requires management. A DID subject can signal a change to their authorized user agent (e.g., wallet), and that agent will assess whether the DID document needs to be amended and, if so, will do it on the subject's behalf. Here are some actions you could take:
Update
The DID document must be updated when the circumstances of the DID subject change. Assume a DID subject has a new DWN and wants to add it to their DID Document as a service endpoint, or that one of their DWN nodes has changed hosts. This modification must be recorded in the DID document.
Revoke
At times, it might be essential to revoke certain keys or service endpoints, making them inactive.
Delete
Although not always advisable due to the immutable nature of some ledgers, a DID document might sometimes need to be deleted or deactivated.
Web 5.0, the highly anticipated future iteration of the World Wide Web, is set to revolutionize decentralized web application (DWA) development by providing programmers with advanced tools and functionality. A key goal of Web 5.0 is to allow independent use of dent credentials and to decentralize websites away from centralized control.
It is amazing that Web5 brings decentralized identity and data storage to applications. It lets developers focus on creating delightful user experiences while returning ownership of data and identity to individuals.
The first thing to do is Install, followed by creating a directory, installing Web5, and then importing Web5
If installed, then we have the Web5 SDK installed and are ready to start building!
Then, to build a local DWN, below are the steps:
Instantiate Web5 and Create DID
Write DWN Records
Read DWN Records
Update DWN Records
Delete DWN Records
The Web5 SDK helps create a decentralized app in minutes.
A brief check on DWN
A decentralized web node (DWN) is a data storage and message relay mechanism that entities can use to find public or private permissioned data associated with a particular decentralized identifier (DID).
Personal Information Storage
A DWN is a personal data storage device. This means that you can:
Take control of your data. You choose where your node will be hosted. You have complete control over who has access.
Make a backup of your data. Host numerous nodes in different locations and effortlessly keep them all connected. If one fails, you have a backup.
Send and receive data: Alice uses her DID to manage her DWN. Bob's DWN is controlled by his DID. By resolving Bob's DID, Alice can communicate data to him.
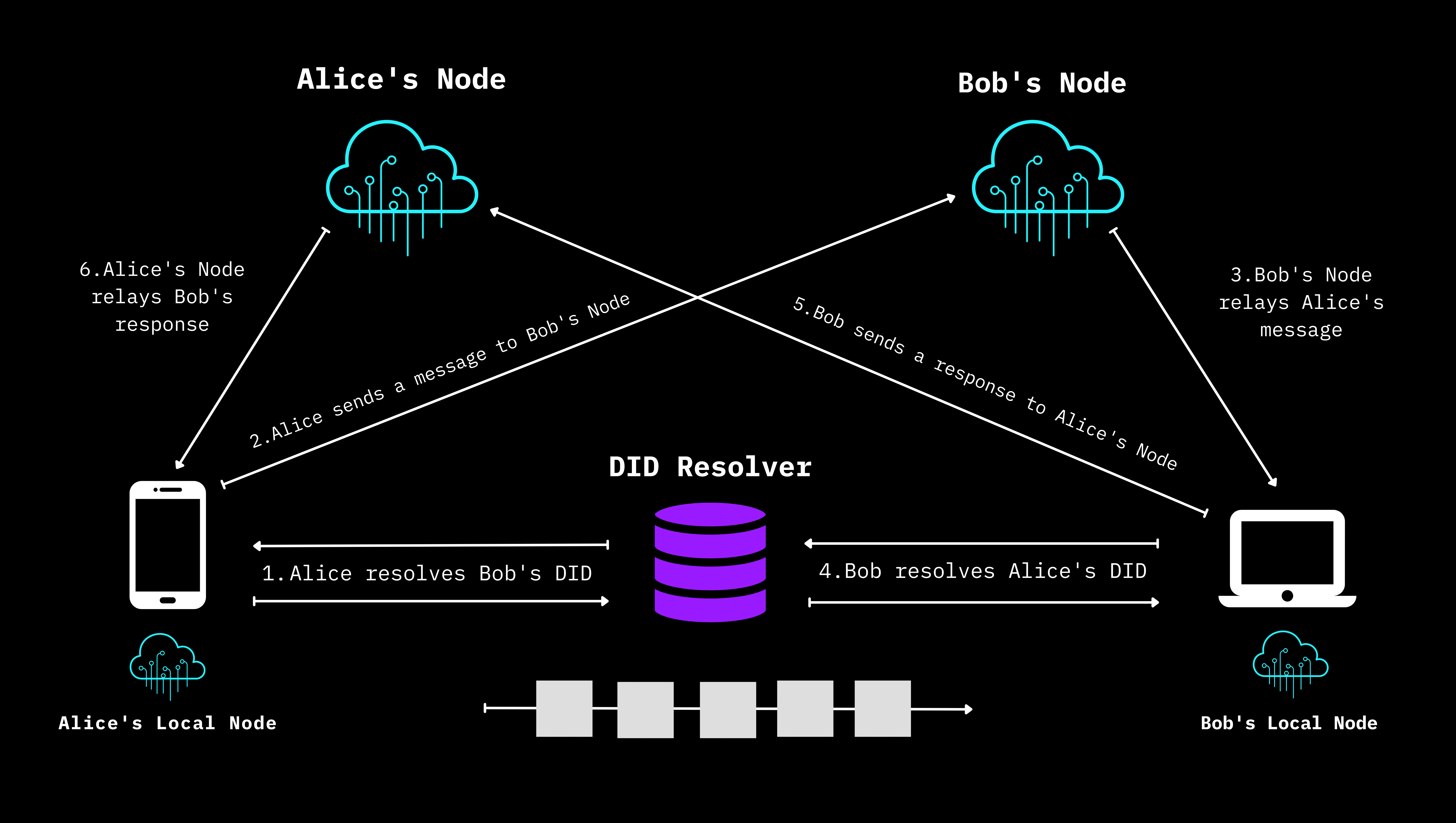
Topology of an exchange between Decentralized Web Nodes, duplicated from the DIF Decentralized Web Node specification
Authorization
DWNs have two mechanisms to allow others access to read, write, or delete data on your node.
Permissions: Allow someone access to read, write, or delete specific data records on your node.
Protocols: Install a protocol that lets you define data types and authorization for a decentralized web app.
The easiest way to understand this distinction is to think of permissions as active, explicit, and manual, whereas protocols are passive, syntactic, and contractual.
Data Model
Data types are associated with well-known schemas, allowing applications to agree on data models. This enables programs to interact in ways that were previously impossible with standard development platforms.
User-defined schemas are not checked on the record payload since this type of validation is impossible for encrypted payloads because the DWN lacks the secret keys to decrypt them. If such validation is to be performed on the data, it is up to the application layer.
Messaging
All communication takes place via basic JSON objects known as messages. By resolving a recipient's DID and obtaining the address of their decentralized web node, Web5 creates messages and assists you in sending them to their destination. A message has the ability to install protocols, provide rights, and read, write, update, query, or delete records. A message writing a record to a DWN, for example, might look like the example below.
{ // Message
"recordId": "b65b7r8n7bewv5w6eb7r8n7t78yj7hbevsv567n8r77bv65b7e6vwvd67b6",
"descriptor": {
"parentId": CID(PREVIOUS_DESCRIPTOR),
"dataCid": CID(data),
"dateCreated": 123456789,
"published": true,
"encryption": "jwe",
"interface": "Records",
"method": "Write",
"schema": "https://schema.org/SocialMediaPosting",
"commitStrategy": "json-merge",
"dataFormat": "application/json"
}
}
Its owner said:
"This may be our most important contribution to the development of the Internet. I'm proud of the team. (“RIP Web3 Investors”),” Dorsey tweeted on the morning of June 10. According to TBD's presentation on Web5, the main problem with the Internet is the lack of an "identity" layer: "In today's Web, identity and personal data become the property of third parties," and that is why Web5 will focus on decentralizing identity, data storage, and applications."
What is Web5?
Web 5.0 aspires to establish an advanced online environment that is operationally superior to its predecessors. It is a breeding ground for the purest kinds of decentralization, blockchain, artificial intelligence, the Internet of Things, and cryptocurrency. Web 5.0's primary purpose is to enable developers to build decentralized apps (DApps) with verifiable data and decentralized nodes. This ambitious project attempts to reclaim ownership from a few business titans and place it in the hands of users.
Combining the strengths of Web 2.0 and Web 3.0, Web 5.0 places Tron's focus is on creating a network of interconnected websites that are not only intelligent but also emotionally attuned. This initiative aims to strengthen the emotional rapport between humans and machines. The central concept revolves around independence and control, delivering interactive experiences that prioritize user engagement and satisfaction.
Web5 will give users full ownership of their data, giving them the freedom to use, share, and even make money from it. Web5's main focus will be on protecting data privacy and preventing businesses from using users' personal information. Unlike the current version of the Internet, which lacks emotional intelligence, Web4 aims to create connections between computers and machines. However, with the advent of Web5, we can expect a transformational shift in this paradigm.
Although the modern network serves as a platform for universal information exchange, it is missing an important layer. This missing component must be addressed to enhance the Internet experience.
“We struggle to protect personal data with hundreds of accounts and passwords we can't remember. Today, on the Internet, personal data has become the property of third parties.” ~ TBD Web5 Website
Jack Dorsey urged people to remember the events taking place in the new era of Web3. He expressed concern about the lack of transparency regarding ownership and governance of Web3.
By addressing these very problems, Web5 strives to provide solutions. The core idea behind Web5 is to decentralize our data in a safe and secure way while improving usability.
In his 2009 TED talk, Tim Berners-Lee called Web5 the "emotional web." He envisioned a system in which users could create a digital dent and have complete control over their data. Additionally, users will have the option to monetize their data if they so choose. This vision encapsulates the essence of Web5's goal of empowering people and empowering them to exercise complete control over their personal information.
How will Web 5.0 work?
In the Web 5.0 realm, virtual assistants will have the ability to anticipate users' needs by observing their behavior, emotions, and other human aspects. They will have the ability to accurately discern user requirements even if explicit commands are not provided through certain keywords. Web 5.0 is essentially an advanced version of predictive virtual assistants. This advanced version of the network will be able to understand various elements of data at more complex levels, leading to conclusions based on human logic and emotion.
Notably, Dorsey's vision for Web 5.0 will focus on meeting user needs. Users will be central to this ecosystem, with the goal of delivering a completely unique and personalized experience to each individual. Interactions will vary from person to person based on how the system recognizes emotions and generates appropriate responses accordingly.
Web 5.0 will promote a symbiotic relationship between technological resources, the web, and people. The goal will be to create a system that will meet the daily needs of users by actively interacting with machines. This integration will happen when the web becomes seamlessly intertwined with users' daily lives. Advances in artificial intelligence (AI) are allowing computers to communicate in ways that resemble human speech. This innovation allows computers to reason, consider options, and respond to user input. Thus, with the integration of artificial intelligence, blockchain, and the Internet of Things, Web 5.0 has the potential to revolutionize global dynamics, although the exact scale of this revolution remains speculative.
Web3 and Web5 Comparison
Comparing Web3 and Web5, we find that both have a common vision, but each has its own distinctive features. Web3 applications are often characterized as smart contracts on public blockchains, such as Ethereum. Many people call these applications decentralized applications (DApps) because their underlying code resides on a decentralized network built on blockchain technology.
In contrast, Web5 covers decentralized web applications (DWA), which are not necessarily based on blockchain technology. However, DWAs can still interact with decentralized web nodes (DWNs). This creates a peer-to-peer relay network that runs without any public blockchain.
Web5 gives users control over their data, which can be stored on decentralized web nodes (DWNs). On the other hand, Web3 stores data on a decentralized network or distributed file system such as IPFS, which is capable of distributing and storing data in a peer-to-peer network system.
Key features of Web 5.0
A discussion of Web 5.0 would be incomplete unless we looked at its features and how they improve things. It is crucial to note, however, that Web5 is still in development, which means that information on its characteristics is limited. However, once the platform is fully built and implemented, consumers may expect a vast range of functions. Defi Web 5.0 emphasizes two key features: dent management and actual data ownership.
Control over your identity One of the main use cases for Web 5.0 revolves around giving users control over their identity. For example, consider John, who has a digital wallet that helps him manage authorization, dent, and connection data to various applications and external services.
With this wallet, John can seamlessly log into the decentralized social media application without having to create a new profile. The application recognizes John's dent, and all of his interactions with the application are stored on a decentralized website. John can then switch to other social media apps using his social persona created in the original app.
Ownership of data. Another important aspect of Web 5.0 is data ownership. While the promise of true ownership of user data has been implicit in decentralized web models, concerns about centralization still remain. Web 5.0 aims to empower users by giving them full ownership of their data.
For example, let's consider Ryan, who enjoys watching movies but doesn't want his personal data locked into one streaming service provider. In a Web 5.0 scenario, Ryan can store his preferences and settings on a decentralized web host. This allows him to access his preferences and settings across various streaming apps, providing a smooth and personalized movie experience across multiple platforms.
Advantages and disadvantages of Web 5.0
Web 5.0 is currently in development, and it will be some time before the world learns about the actual use cases. Regardless, it's natural to speculate about the potential advantages this could provide users. However, it is equally crucial to spot the flaws that can negatively effect the user experience. Here's a rundown of the Web 5.0 platform's main benefits and drawbacks.
Advantages
Increasing creativity. Web 5.0's emotional intelligence feature might provide users with a perfect platform for enhancing their creativity.
E-commerce communication has improved. The e-commerce sector can employ Web 5.0's emotional intelligence component to build infrastructure for real-time communication with users. E-commerce may improve the user experience and offer value by reading users' emotions.
Dent and data management The ability to preserve complete control over your own data is a big advantage of Web 5.0. Unlike previous centralized web versions, Web 5.0 gives people autonomy over their data and the ability to determine how to utilize it. Users can utilize their digital identity securely across a wide range of applications and services.
Security Inspired by Bitcoin: The foundations of Web 5.0 take inspiration from Bitcoin, which is considered the most secure decentralized network. Web 5.0 aims to offer the benefits of decentralization and cryptographic security through the use of blockchain technology.
Flaws
Current Development: Web 5.0 is still under development, and the final outcome and shape of the project remain uncertain. This introduces an element of unpredictability and potential problems.
Dependent on Adoption: The benefits of Web 5.0 rely heavily on widespread adoption. For the platform to reach its full potential, it requires significant user understanding and acceptance.
While Web 5.0 has clear benefits, it is important to consider these factors and the ongoing evolution of the platform as it moves toward adoption.
It was another nice section on the role of data science in a decentralized identity talk show with Rizel and Wale (Ace), and the guest, Zaida Rivai, a data scientist and an engineer of machine learning who works with a co-founder, started using DID because she wanted to solve a problem that is already on the internet and to maximize privacy. She took us through the awesome journey of how data analysis is applied with DID and how to do it, especially when there is a need for someone to change an endpoint. She talked about "Godiddy," a platform to create and update DIDs that can also be versioned, containing 180 DID methods, a tracker that tracks all DIDs from all over the world, and the use of graphs to monitor its scale. Also, a quick review of what we learned previously, where I re-learned that Web5 is basically an ecosystem to build applications that prioritize data ownership and user privacy. And a brief check on what decentralized identifiers are, which are a W3C open standard based on cryptographic principles, not tied to one web application or system, and give one access to a decentralized web node (DWN) or a personal data store. The section ended with fun questions.
Subscribe to my newsletter
Read articles from Balikis bamgbose directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
