DIDs, DWNs and Web 5, What is it all about?
 Sandy Om'Iniabohs
Sandy Om'Iniabohs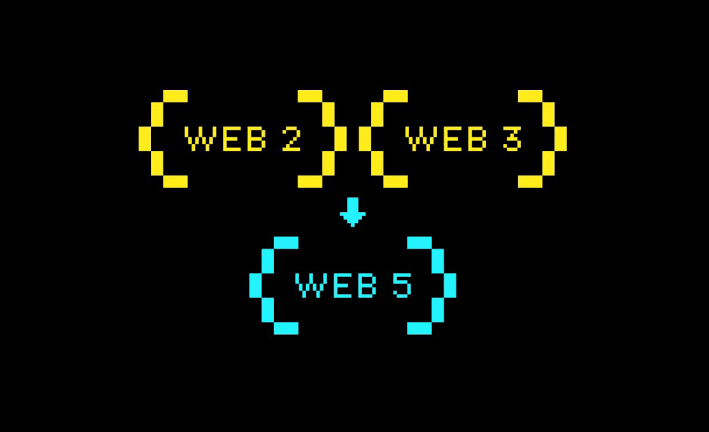
Web 1.0 was the earliest version of the internet which consisted mainly of static websites. Web 2.0, commonly referred to as the second generation of the World Wide Web, brought about a dynamic shift in how individuals interacted with the Internet. It gave rise to user-generated content and platforms such as social media, blogs, and wikis. Web 3.0 is the version of the Internet that incorporates decentralisation and blockchain technology with foundations from Web 1.0 and Web 2.0.
Each version of the web has its pros and cons, which is where Web 5.0 comes in. Web 5.0 combines the intuitive ease of Web 2.0 with the decentralisation perks offered by Web 3.0. It gives users greater control of their data (or identity) and is powered by 3 major pillars:
Decentralised Identifiers (DID)
Verifiable Credentials
Decentralised web nodes (DWN)
THE THREE PILLARS
Decentralised Identifiers (DID): What if you owned and controlled your unique identifier on the web? For example, social media handles are controlled by the companies that provide them. However, a DID is a unique key that gives the owner total control of their identity on the internet. DID is a string made up of three parts - URI scheme identifier (unique sequence of characters), the identifier, and the third part is a code unique to the owner.
Verifiable Credentials: Verifiable Credentials (VCs) enable trustless interactions using cryptographically signed proof. This means that Party A and Party B can interact with one another simply because Party A has a digital certificate that can easily be verified. It is the digital version of a passport.
Decentralised web nodes (DWN): Decentralised Web Nodes (DWNs) allow their owners to hold their data independent of the applications they interact with. Individuals can manage, transfer, and allow interactions with their data without the use of a centralised infrastructure which promotes control and privacy. For example, Twitter stores users' tweets, details, and data in the database called Manhattan but with DWN, the user can store his/her data on any device of their choice.
CREATING YOUR OWN DID
Creating your own Decentralized Identifier (DID) typically involves a few steps. These include:
- Understand DID basics, methods, and standards.
Choose a DID method: DID method refers to how a DID is created, managed, and deleted. There are multiple methods in existence such as the Bitcoin method and the Ethereum method. More details can be found here.
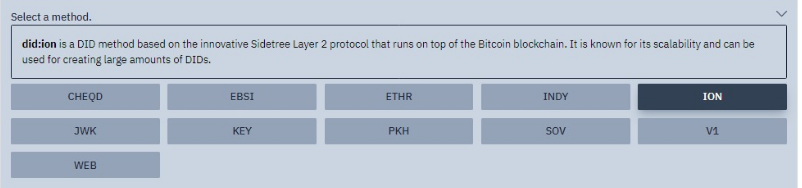
Select a Wallet or Provider:
Choose a wallet that supports DIDs such as Coinbase wallet or Metamask for easy management and is compatible with the DID method of choice.
Generate Your DID:
Use your chosen wallet or provider to generate your DID. This process typically involves creating a key pair (public and private keys) associated with your DID.
Record and Backup:
It is essential to record your private key and back-up your DID information.
Register Your DID:
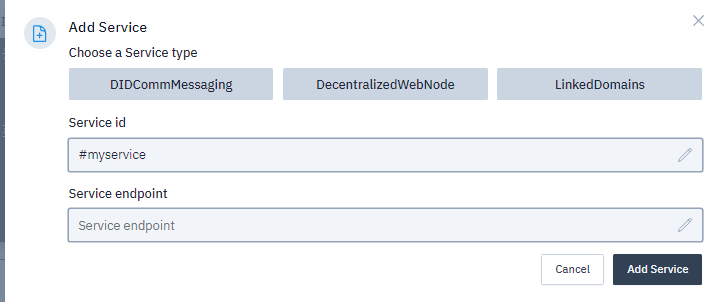
You can choose to link your DID to a domain, method, or DWN depending on your choice. For example, in the image above the DID is added to a dentralised web node service.
Use Your DID:
Begin using your DID for authentication purposes or to interact with decentralized applications (DApps) that support DIDs.
A simplified example using the "did:ion" method:
DID: did:ion:test:EiDXUkhugfL5mhwh2fjZni6C72c_NHUkN18XvAE
Method: "did:ion"
Method-Specific Identifier:"test:EiDXUkhugfL5mhwh2fjZni6C72c_NHUkN18XvAE"
Subscribe to my newsletter
Read articles from Sandy Om'Iniabohs directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
