7 Applicable Steps to Reduce the Attack Surface in 2024
 Eyal Katz
Eyal Katz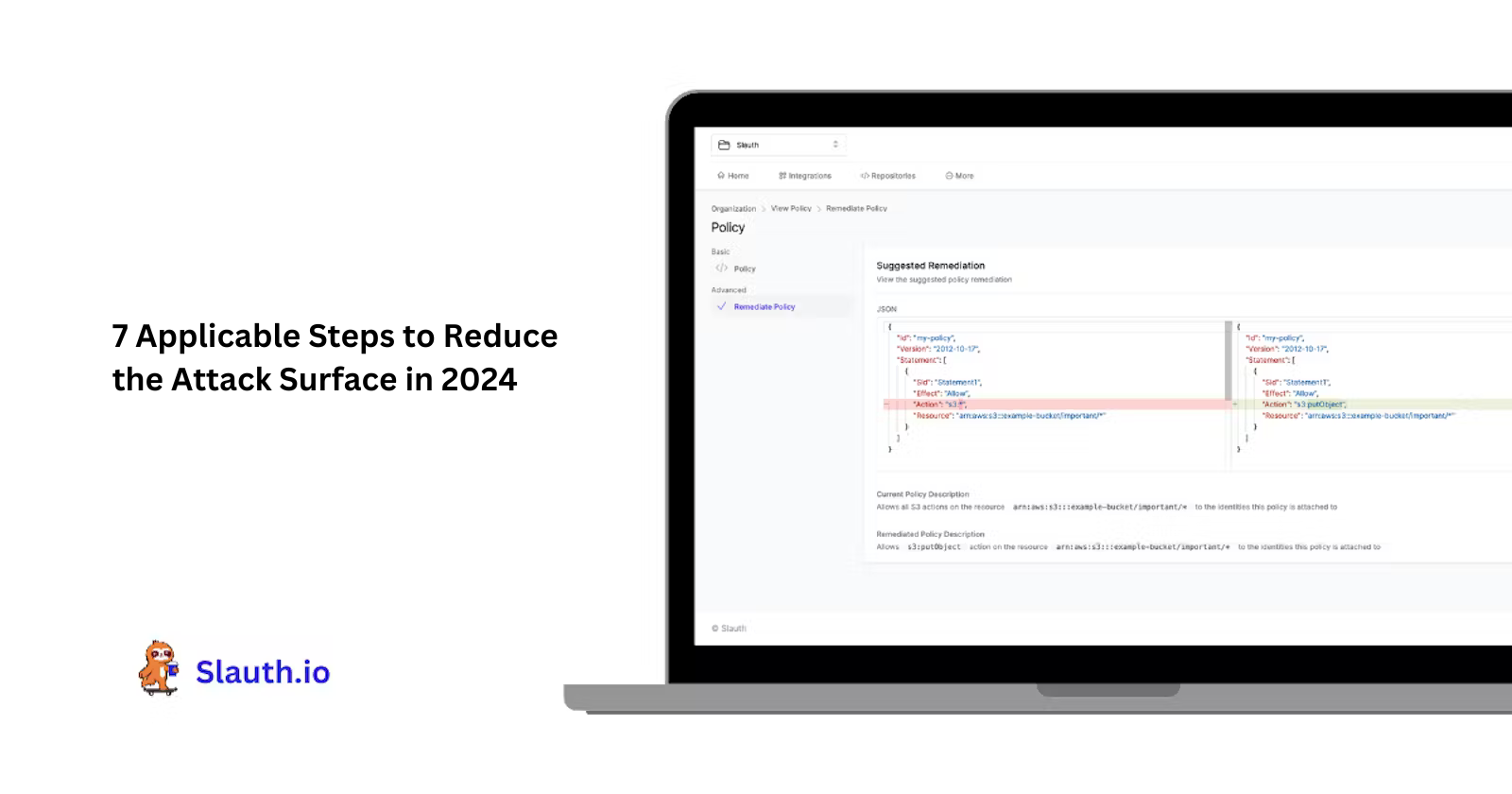
The digital footprint of businesses extends across a broad and often murky expanse, with security perimeters that are anything but fixed. As companies expand and increase their reliance on third-party software, the security battle intensifies, and minimizing attack surfaces becomes paramount.
Organizations face an average of 1248 attempted attacks on their systems each week. Data doesn't lie – cyber attacks continue to rise rapidly, creating a hostile digital environment for businesses. But more alarming is that identity-related breaches now form the epicenter of most of these targeted attacks. This shift demands a strategy recalibration from IT professionals – placing IAM solutions at the forefront of their agenda.
Every additional user, application, and device expands your attack surface and, therefore, your vulnerability. Even if you’re already having conversations around reducing your attack surface and tightening access controls, is that enough to prepare for what’s to come in 2024? When the stakes are this high, it’s worth revising your strategy.
What constitutes your attack surface?
Your attack surface is all possible points where an unauthorized user can access your IT environment or where data can seep out. As enterprises adopt new technologies, these “entry points,” or attack vectors, continue to grow.
Key attack vectors include:
Network Perimeter – Includes all external-facing assets like firewalls, routers, and intrusion detection systems that control incoming and outgoing network traffic.
User Accounts and Privileges – Concerns human and non-human (machine) identities, necessitating stringent access controls and privilege management to avoid privilege escalation attacks.
Web Applications – Encompasses all internet-facing applications, which could be vulnerable to exploits such as SQL injection or Cross-Site Scripting (XSS).
Operating Systems – Covers all underlying operating systems of servers and endpoints, where vulnerabilities can be exploited if not regularly patched.
Software and Applications – Refers to installed first-party and third-party software, requiring continuous vulnerability assessment and patch management.
APIs – Includes all application programming interfaces, particularly those exposed to the public, which require security measures against unauthorized access and data exfiltration.
Data – Consists of data at rest and in transit, requiring encryption, access controls, and data loss prevention strategies.
Cloud Services – Involves assets hosted off-premises in cloud environments, mandating robust access controls and configurations to prevent breaches.
Third-party Services / Supply Chain – Relates to external services and vendor connections, where vendor risk assessment and continuous monitoring are essential.
Physical Infrastructure – Encompasses all physical devices and access points, requiring physical security controls to prevent unauthorized access.
As listed above, your attack surface includes user accounts and human and machine privileges. Unfortunately, machine identities – designated to be silent laborers like automated scripts, bots, and service applications – often slip under the radar within Identity and Access Management strategies. Because these machine entities operate under the guise of routine, their credentials are a backdoor rarely guarded with the same vigor as the front-facing human identities.
Analyzing your attack surface
Before you can map out a plan to reduce your attack surface, you need to analyze its current state. Start by listing all your digital assets, both in-house and cloud-based, pinpointing potential targets like endpoints, servers, and mobile devices, as well as their operating systems, applications, and services.
After identifying assets and vulnerabilities, evaluate the likelihood and impact of breaches with a comprehensive risk assessment. This includes examining security policies and the systems of third-party partners connected to your network.
It’s well-known in the cybersecurity industry that stolen credentials are the number one way hackers infiltrate secure systems. To bolster your defenses, focus intensively on strengthening IAM. This proactive approach is crucial for safeguarding your broader attack surface against user or machine identity breaches.
7 Applicable Steps to Reduce Attack Surface in 2024
1. Implement Zero Trust Security
Zero Trust dismantles the idea of a trusted internal network, operating under the principle of "never trust, always verify." To do this, you'd configure your infrastructure to treat every access request as a potential threat, irrespective of its origin.
In the Zero Trust model, the network is carved into micro-segments, each functioning as its secure enclave. Implementing this requires granular control policies, where you'll need to design ACLs (Access Control Lists) and firewall rules that govern traffic at a very fine level. It's a detailed task involving network topology analysis to define segments based on the sensitivity and function of the resources they contain.
A segmented, compartmentalized network environment can effectively control and limit access, reducing the potential for unchecked lateral movement that could lead to data breaches.
2. Least Privilege Access
The principle of least privilege (PoLP) means granting only the minimum levels of access needed to perform a function. The access rights must be tightly controlled, whether a human user or a machine entity like a service account, container, or API. The risk of overprovisioning is real and potentially catastrophic for machine identities, which typically operate with elevated privileges required for automated tasks.
Regular audits and adjustments of access levels, coupled with stringent control mechanisms, are indispensable in maintaining a secure and resilient IT environment.
3. Automate IAM Policies
Accurate IAM policies facilitate swift and precise account management—from initiation to modification and eventual deactivation. You can automate the creation of policies with tools like Slauth, which monitors actual machine identity activity by tracking API calls from end-to-end tests to AWS. Based on this data, Slauth automatically determines what each machine identity needs access to and codifies this into IAM policies ready to be deployed.
Aside from simplifying the policy formulation and supporting seamless operations, Slauth ensures that every policy adheres strictly to the Least Privilege principle to reduce your attack surface. You can also get custom IAM roles that meet your infrastructure and business needs - further simplifying your IAM plan with automation.
4. Strengthen Authentication and Verification
Mutual TLS (mTLS) establishes a robust two-way authentication by requiring both communicating parties to present valid certificates for identity verification. It's akin to a digital version of verifying identities at both ends of the conversation, thus preventing unauthorized access. This measure is particularly crucial when machines such as servers and automated clients communicate within a network.
Alongside mTLS, leveraging Hardware Security Modules (HSMs) offers a secure enclave for cryptographic operations, safeguarding keys and certificates from external compromise and facilitating a fortified authentication landscape for automated processes. By handling sensitive operations in an isolated hardware environment, HSMs ensure that even if a network is compromised, the keys remain out of reach, maintaining the integrity of the authentication process and reducing the risk of key compromise.
5. Continuous Monitoring and Auditing
Integrating continuous monitoring and auditing into your cybersecurity measures is critical for detecting and responding to emerging threats. This involves setting up systems that continuously analyze and validate user and machine behaviors, ensuring they align with established security policies.
Slauth focuses on machine identity surveillance, which is often overlooked in security planning. With its automated system, Slauth gives you complete visibility of your machine identities’ activity through logs placed throughout different SDLC stages. This 360-degree monitoring lets your engineering team check machine behavior against security policies and spot anomalies such as IAM access changes. The faster your team discovers suspicious behavior, the faster it is to remediate it before it escalates into a severe security attack.
These logs can also support your compliance efforts. Regulations such as GDPR, HIPAA, and SOC require an evidence-based overview of your IAM strategies, so you can use these logs to prove that your data and systems are protected.
6. Secure your Supply Chain
To safeguard your supply chain, thoroughly screen your third-party vendors for security weaknesses to assess supply chain risk. Establish a comprehensive vetting process that includes detailed security evaluations based on industry standards and stipulate strict security requirements for vendors as part of your Service Level Agreements (SLAs).
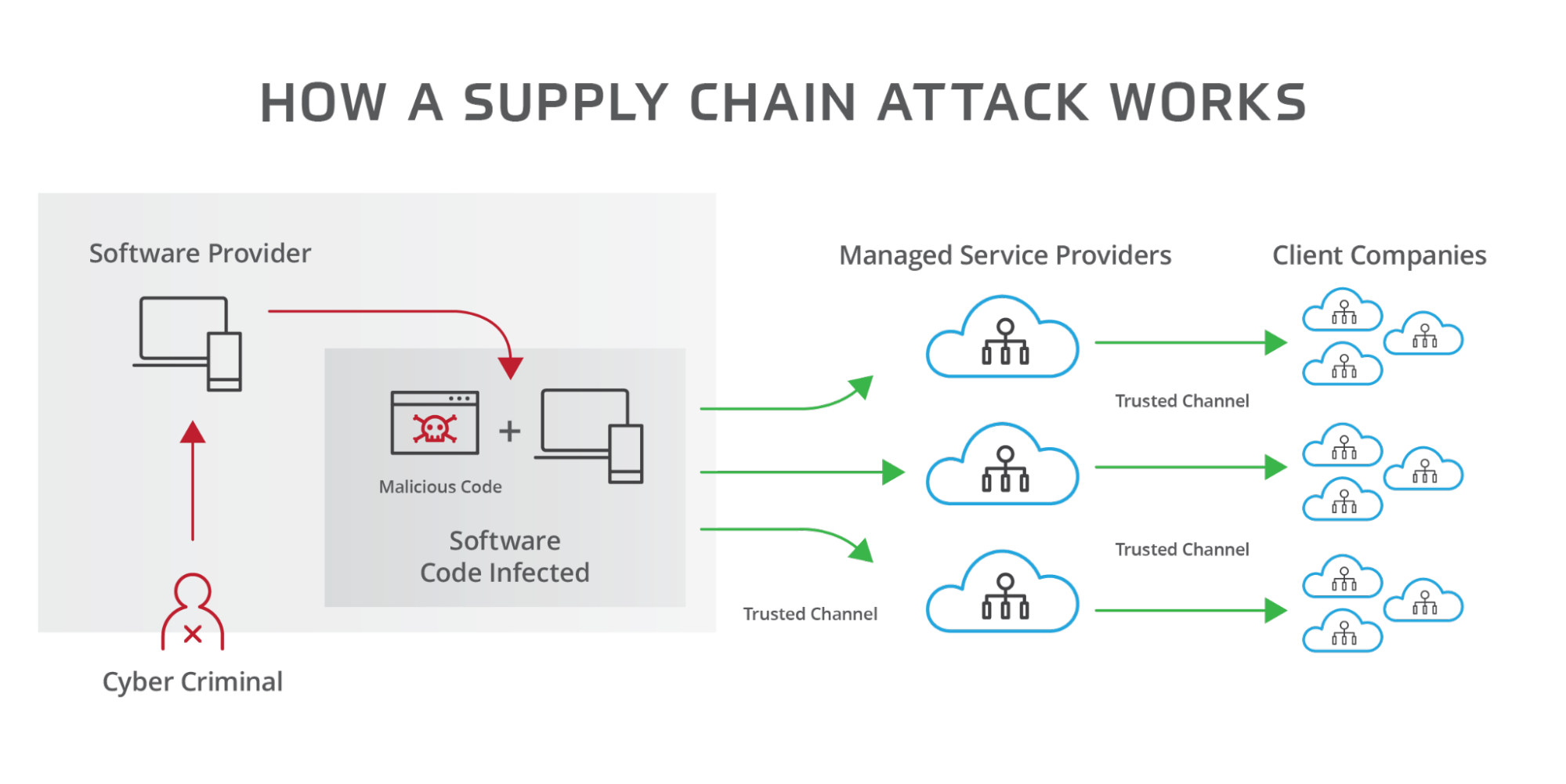
You should also employ Secure Software Development Lifecycle (SSDLC) protocols for overseeing third-party software development and deployment. This will help you embed security throughout the software's lifecycle and reduce the chance of introducing flaws into your systems. Keep your SSDLC methods up-to-date to address new threats and integrate automated security tools in your CI/CD pipeline for early detection and correction of security issues.
Continuously watch over your third-party integrations and insist on transparency regarding their security practices. In case of a breach in your supply chain, be prepared with a response plan to contain the threat and prevent it from spreading across your network.
7. Secure Storage of Keys and Certificates
To enhance your security posture, you must securely store and manage cryptographic keys and certificates, foundational elements of machine identity protection. Utilizing Hardware Security Modules (HSMs) or managed cloud-based vault services ensures these sensitive components are safeguarded in tamper-resistant hardware or secure, scalable storage solutions.
When configuring such storage solutions, enforce encryption-at-rest to protect your keys and certificates from being compromised if the storage boundary is breached. Set strict access controls so only authorized users can access or alter them, reducing the risk of misuse, especially given their potential for high-level access.
Regularly rotate keys and automate certificate renewals to avoid outages and vulnerabilities from expirations. Careful lifecycle management and secure storage of cryptographic materials can significantly narrow the opportunities for attackers, strengthening your overall security.
Reducing your Attack Surface with Slauth
The breadth of your attack surface is a measure of your exposure. As the number of cyber attacks escalates, businesses must use IAM automation to their advantage. It starts with discussing your IAM plans with stakeholders, ensuring that all your team members are on the same page and have a clear path forward. But the next step is implementing technologies that will tighten your access controls, help you gain visibility, and smoothen your day-to-day operations.
Slauth completely automates the IAM policy creation and deployment process, ensuring tighter security with no extra work required. But it doesn’t leave it at that: you also get continuous visibility into IAM behavior to monitor activity properly and set up mitigation workflows as soon as any suspicious action pops up. Learn more here.
Subscribe to my newsletter
Read articles from Eyal Katz directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
