Simplifying CI/CD Pipelines: Enabling CodeBuild to Connect with Cross Account S3 Bucket
 Ankit Singh
Ankit SinghScenario:-
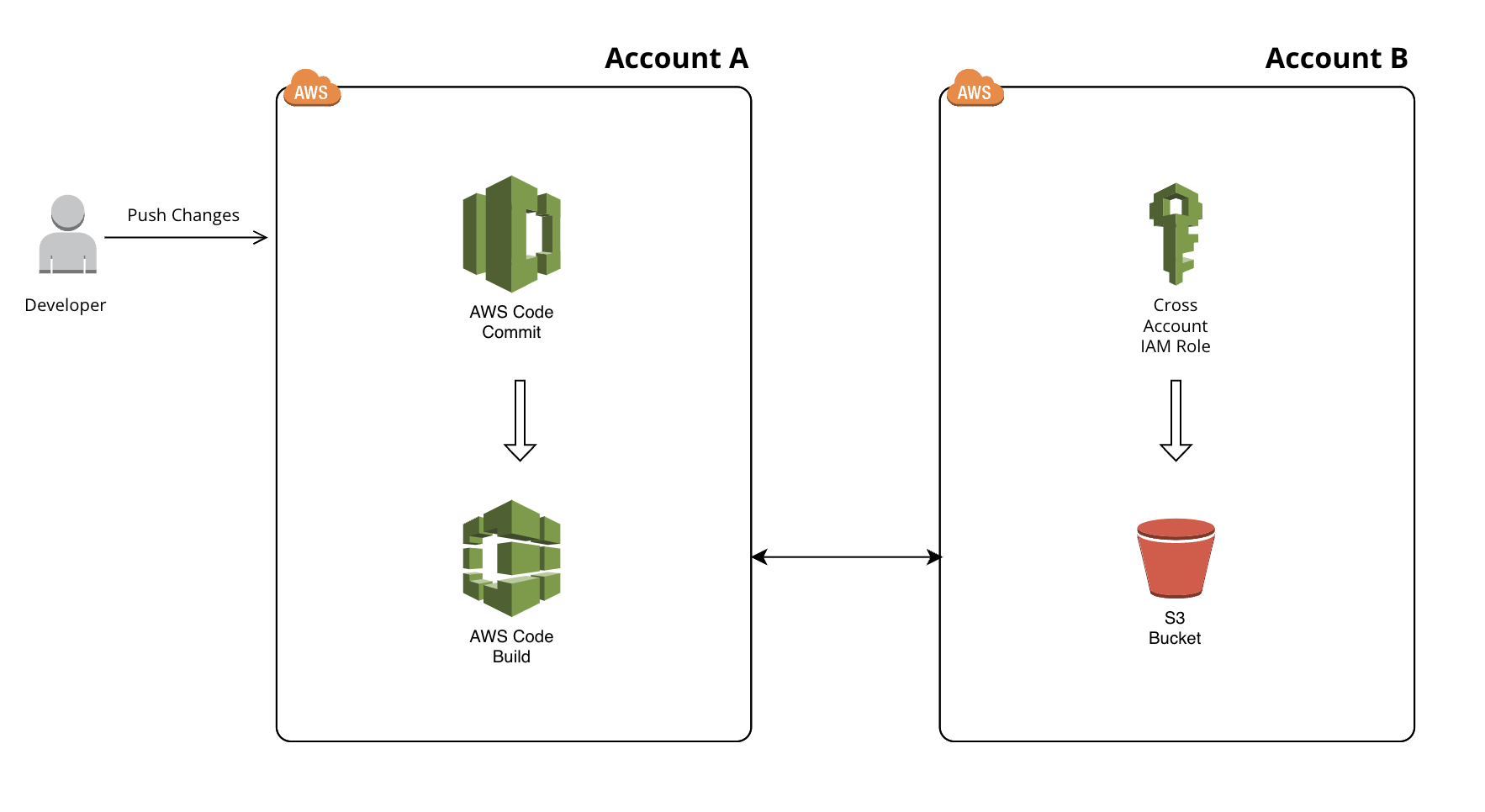
- In many organizations, the CI/CD pipeline may be set up in one AWS account, while the deployment takes place in a different account using CodeBuild. In such a scenario, you might need CodeBuild to communicate with resources in the other account, such as an S3 bucket, ECS, or EC2. This article will guide you through the process of enabling CodeBuild to interact with a cross-account S3 bucket.
Prerequisite:-
To begin working with this blog, you need to have:
- CodePipeline setup in Account A having CodeCommit & CodeBuild. In the another Account B you need to have an S3 bucket created assuming public access is denied.
Steps to Set Up the Architecture:-
Cross Account Role Creation in Account B:-
This Cross Account role will allow the CodeBuild to access the S3 Bucket Cross Account.
Open the AWS Management Console with Account B.
In the navigation pane, choose Roles.
Choose Create role.
For Select type of trusted entity.
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": { "AWS": "arn:aws:iam::<AccountA ID>:root" }, "Action": "sts:AssumeRole" } ] }Choose Next: Permissions.
Attach a policy to the role that delegates access to Amazon S3. For example, this policy grants access for s3:GetObject, s3:ListBucket, s3:PutObject on objects stored in the bucket.
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "s3:GetObject", "s3:ListBucket", "s3:PutObject" ], "Resource": [ "arn:aws:s3:::AccountB-BUCKET-Name/*", "arn:aws:s3:::AccountB-BUCKET-Name" ] } ] }
S3 Bucket Permission Policy in Account B:-
Open the AWS Management Console with Account B.
In the navigation pane, choose S3.
Go to the permission section of s3 bucket which you want to provide access to CodeBuild.
Update the policy with the ARN of CodeBuild IAM Roles present in Account A.
{ "Version": "2012-10-17", "Id": "SSEAndSSLPolicy", "Statement": [ { "Sid": "", "Effect": "Allow", "Principal": { "AWS": "<ARN of CodeBuild IAM Role in AccountA>" }, "Action": [ "s3:GetObject", "s3:ListBucket", "s3:PutObject" ], "Resource": [ "arn:aws:s3:::AccountB-BUCKET-Name/*", "arn:aws:s3:::AccountB-BUCKET-Name" ] } ] }
CodeBuild IAM Role Modification:-
Open the AWS Management Console with Account A.
In the navigation pane, choose Roles.
Choose the IAM role attached to the CodeBuild.
Click on Add Inline Policy & create these two Policies given below.
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": "sts:AssumeRole", "Resource": "<Cross Account Role ARN in AccountB>" } ] }{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "s3:GetObject", "s3:ListBucket", "s3:PutObject" ], "Resource": [ "arn:aws:s3:::AccountB-BUCKET-Name/*", "arn:aws:s3:::AccountB-BUCKET-Name" ] } ] }
Now CodeBuild present in Account A should be able to Get or Put Object in the S3 bucket present in Account B by assuming the Cross Account Role in Account B.
Conclusion:-
- Allowing CodeBuild to communicate with a cross-account S3 bucket involves creating a cross-account role in Account B, updating S3 bucket permission policy in Account B, and modifying the CodeBuild IAM role in Account A. By following these steps, you can successfully establish a connection between CodeBuild in Account A and an S3 bucket in Account B, facilitating seamless data exchange and improving the efficiency of your CI/CD pipeline.
Subscribe to my newsletter
Read articles from Ankit Singh directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Ankit Singh
Ankit Singh
I am a DevOps engineer looking to exchange knowledge and gain insights from fellow professionals.