🚀 Introduction of AWS WAF With Project
 Deepika Pandey
Deepika Pandey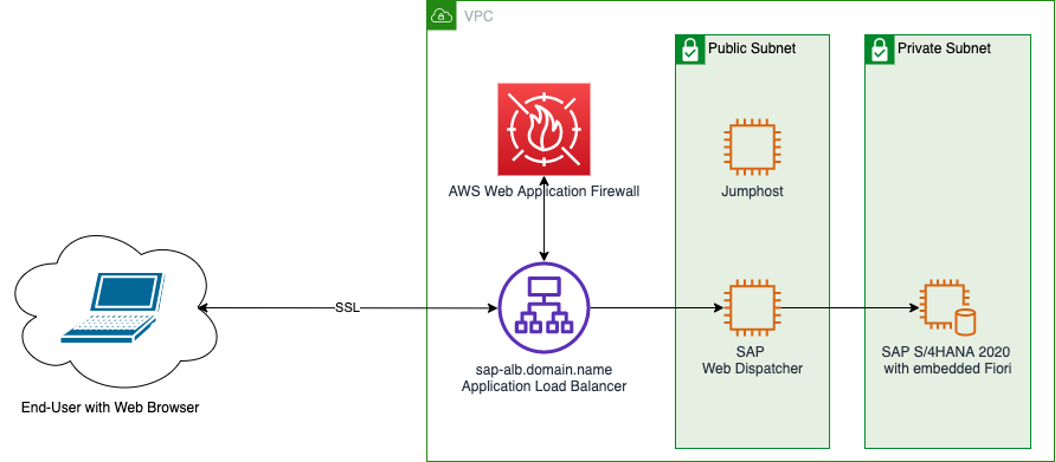
AWS WAF is a web application firewall that lets you monitor and manage web requests that are forwarded to protected AWS resources. With AWS WAF, you can protect resources such as Amazon CloudFront distributions, Amazon API Gateway REST APIs, Application Load Balancers, and AWS AppSync GraphQL APIs. You can use AWS WAF to inspect web requests for matches to conditions that you specify, such as the IP address that the requests originate from, the value of a specific request component, or the rate at which requests are being sent. AWS WAF can manage matching requests in a variety of ways, including counting them, blocking or allowing them, or sending challenges like CAPTCHA puzzles to the client user or browser.
For additional protection against distributed denial of service (DDoS) attacks, AWS also offers AWS Shield Advanced. AWS Shield Advanced provides expanded DDoS attack protection for your Amazon CloudFront distributions, Amazon Route 53 hosted zones, and Elastic Load Balancing load balancers.
Core Functionalities
1 . Filters and Rules : AWS WAF enables users to customize rules and filters for the purpose of examining incoming web traffic. Users specify criteria according to different parameters such as IP addresses, HTTP headers, URI strings, request types, or query strings. Example: creating rules to block requests containing specific SQL injection patterns or allowing traffic only from trusted IP addresses.
Integration with AWS Services : The functionality and scope of AWS WAF are enhanced through its seamless integration with other AWS services. functions in concert with AWS Firewall Manager, Application Load Balancer, Amazon API Gateway, and Amazon CloudFront (CDN). protects web applications and APIs effectively and scalably by offering security at the network's edge.
Managed Rule sets : Highlight the availability of managed rule sets provided by AWS or third-party vendors, offer predefined security rules to protect
against known threats.
Types of AWS WAF
Rule-Based WAF : Explain the concept of rule-based WAF, where users create rules to define which requests to allow or block based on defined conditions.
Rate-Based Rules : Elaborate on the use of rate-based rules to control the rate of incoming requests to prevent various types of attacks, like DDoS (Distributed Denial of Service).
Geo-Matching Rules : Explore how AWS WAF allows users to create rules based on geographic locations, enabling blocking or allowing traffic from specific regions.
Managed Rule Groups : Discuss AWS WAF 's managed rule groups, which offer pre -configured rule sets maintained by AWS or third-party vendors for specific threats or vulnerabilities.
- Implementing AWS WAF for Web Application Protection

Deploy a sample web application on an EC2 instance in your AWS account.
This guide is suitable for beginners. -
1 Setting up an EC2 instance:
Sign in to AWS Console: Log in to your AWS Management Console.
Navigate to EC2: Go to the EC2 dashboard.
2. Launch an EC2 Instance:
Click on "Launch Instance": Choose an Amazon Machine Image (AMI). For instance, select an Amazon Linux AMI.
Select Instance Type: Choose an instance type based on your needs (e.g., t2.micro for a free-tier eligible instance).
Configure Instance: Configure instance details like network settings, security groups, and storage.

3. SSH Access to EC2:
Create a Key Pair: If you haven't already, create a key pair for SSH access to your instance.
Connect to EC2: Use an SSH client like PuTTY (on Windows) or Terminal (on Mac/Linux) to connect to your EC2 instance using the key pair.

4. Installing Web Server Software:
Update Packages: Run sudo apt-get update (for Ubuntu).
Install Web Server: Install a web server like Apache or Nginx.
Run sudo apt-get install nginx

5. Deploy a Sample Web Application:
Upload Your Files: Use SCP or SFTP to upload your web application files (HTML, CSS, JavaScript, etc.) to the EC2 instance.
scp -i /path/to/your/key.pem /path/to/local/file user@ec2-instance-ip:/path/on/ec2
or Use git clone <url>
Place Files in Web Server Directory: the default directory is /var/www/html/. Place your files there.
6. Start the Web Server:
Start Web Server Service: For Apache, use sudo service httpd start to start the Apache service.
sudo systemctl start/stop [service-name]

7. Access Your Web Application:
- Get Public IP: In the EC2 console, note the public IP of your instance.
Access the Web App: Open a web browser and enter the public IP in the address bar. You should see your sample web application if everything is set up correctly.

Defining rules to stop malicious requests aimed at your web applications is part of creating an AWS WAF WebACL. Here's how to make a simple WebACL step-by-step:
1. Access the AWS WAF Console:
Log in to your AWS Management Console.
Navigate to the AWS WAF service.
2. Creating a WebACL:
- Click on "Web ACLs" in the AWS WAF dashboard.
Choose "Create Web ACL."

3. Configure WebACL:
Name your WebACL: Provide a descriptive name for your WebACL (e.g., "BasicWebACL").
Choose resource type: Select the type of resource to associate with your WebACL (e.g., CloudFront distribution, Application Load Balancer).
Associate with Resource: Select the resource you want to protect (if applicable).

4. Define rules for WebACL:
Rule Categories: Choose between "managed rules" or "add rules manually."
- Managed Rules: AWS provides predefined rule sets to protect against common threats.
Add Rules Manually: Define custom rules based on your specific requirement.
/

5 Activate WebACL:
Review your configured rules and settings.
Click "Create" or "Activate" to enable the WebACL.

6. Associate WebACL with AWS Resources:
If not done during WebACL creation, associate the WebACL with the appropriate AWS resources
e.g., CloudFront distribution, Application Load Balancer.

7 Testing WebACL:
Use tools or simulated attacks to test the WebACL's effectiveness in blocking malicious requests.
Monitor the AWS WAF logs to observe the blocked or allowed traffic based on your defined rules.

Subscribe to my newsletter
Read articles from Deepika Pandey directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
