Rate Limiting
 Pixel
Pixel
Intro
If you use Twitter regularly, you would have experienced this firsthand in early July 2023. Almost everyone on the platform was rate-limited. It was hilarious. Some people thought this was it for Twitter, and other platforms like Mastodon would take over.
But, scratch all that. We are here to understand:
what is rate limiting?
how does it happen?
and, why it happens?
So put on your geeky hat or grab a coffee/tea or just stare dead into the screen because we're starting now.
What is Rate Limiting?
Rate limiting is a technique used to control the rate at which a service or a resource can be accessed by a client/user.
It's used to set a restriction on - how many times your service/resource can be accessed within a time frame.
Now just to check things out yourself, go visit this webpage - https://cloudflare.com/rate-limit-test/.
After opening up the webpage, hit the refresh button 10 times. You'll be redirected to a page saying you have been rate-limited.
Rate Limiting Example
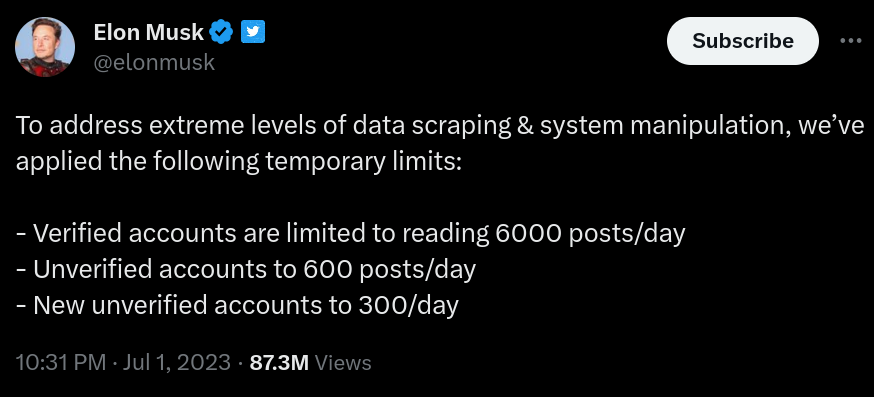
Checkout this screenshot -
Now according to this old tweet by Elon Musk, you can see that Twitter had put a limit on reading/accessing tweets. Which is a good example of rate-limiting. Understand that rate-limiting can be implemented in many ways but the base mechanism of it remains the same.
But you might be wondering:
Why even put a rate limit on anything?
Why can't users freely access the resources?
Don't business owners and service providers want more and more users to use their services?
Why Rate Limiting?
The simple answer is you want to protect your resources. By setting limits on the rate of incoming requests, you can prevent server overloads, congestion, or crashes caused by an overwhelming amount of traffic.
Now how is it implemented? Well, if you were rate-limited on Twitter or you accessed the webpage that I shared above you already know how it's done. Implementing rate limiting involves temporarily blocking or delaying requests that surpass the defined limits.
Conclusion
Rate limiting is a mechanism for managing high volumes of requests and interactions.
It safeguards servers, APIs, and resources, prevents abuse, and promotes fair usage.
Understanding it is essential for building robust and resilient systems.
If you liked this blog, feel free to check out my other blogs here. (<-- tap tap)
Also, if you'd like you can connect with me on Twitter. (<-- tap tap)

Subscribe to my newsletter
Read articles from Pixel directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Pixel
Pixel
Backend Developer, who seldom explores cybersecurity.