Nym's Mixnet and how it protects privacy
 AnnaV
AnnaV
A major problem with the Internet, whether Web2 or Web3, is that it is insecure. Nym solves a massive problem on the Internet: traffic patterns are visible to anyone who observes the network.
Governments and large technology companies that are able to observe a significant portion of network traffic can record and analyze traffic patterns that often reveal more than just the content of a message. These small pieces of information are like the digital footprints left behind by every online interaction. By themselves they mean little, but when collated they are used to identify patterns and user profiles that can be both exploited and de-anonymize people.
Even if content is encrypted, metadata and interaction patterns reveal sensitive information about people and systems. Nym protects Internet traffic by routing it through a decentralized global network called Mixnet, which can be accessed anonymously using zk-nyms.
Nym's Mixnet is often confused with blockchain, but is best understood as a separate infrastructure served by blockchain. It protects IP addresses and traffic patterns and can be integrated into any blockchain, wallet or application.
How Mixnet Nym works
The Internet is divided into different layers with different functions, and the basic layer of the network infrastructure is Layer 0 (Layer 0). The Nym mixnet is also Layer 0. It refers to the network layer or transport layer of the Internet.
To make it easier to understand, let's think of this layer as a backbone. Like our life, the roads of the backbone can be seen. Let's imagine that we are looking at the highway from above. We can't see the drivers inside the cars, but we can learn some information about them by their car, how big it is, its color, where it is going, departure time and arrival time. Collectively, this information can tell us a lot about the driver himself, his character, habits, career and life.
Also on the Internet, data packets travel over communication protocols such as TCP and UDP. By observing this data, we get data about the data, called metadata.
Mixnet Nym solves the problem of tracking this data by obfuscating the metadata. The Nym mixnet encrypts Internet traffic into equal-sized packets mixed with "dummy" data packets that contain nothing at all. These are then all transmitted through three layers or "hops" to "nodes" in the mix, which are distributed around the world at random times and intervals before they are reassembled and decrypted on the receiving end. This makes surveillance of network traffic virtually impossible.
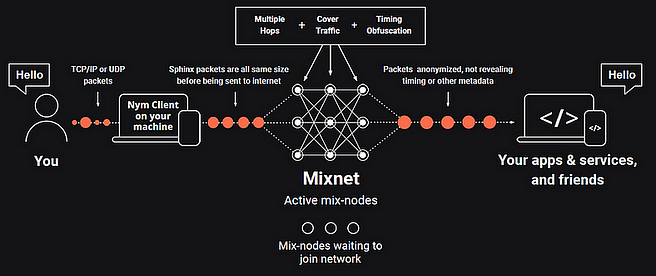
If we go back to the example of cars on the highway, they all become the same to us. They lose identifiers that are unique to us, such as color or size. They drive at the same intervals, making it impossible to infer where they were going and their destination. It becomes completely impossible to understand anything about the driver's character and habits.
The internet does not preserve privacy. By design, traffic data is visible, and powerful interests such as governments and corporations take advantage of this fact. They monitor traffic, collect metadata and build detailed user profiles from it, which can often provide more information than the message content itself.
Because Nym addresses the network layer of the Internet, the Nym mixnet is a holistic approach to privacy for Web 2.0 and Web3.
The goal of Nym is to protect network traffic for the entire Internet.
Metadata
It is now widely recognized that privacy protections ensure secure online communication. Moreover, secure communications are the foundation for meaningful online interactions, from our social lives to commerce.
But as the volume of digital communications continues to grow - and with the advent of artificial intelligence-based surveillance - it is no longer the content of your message that matters, but its metadata . In fact, metadata can often tell a much more accurate story about your life than content. The content of your post may contain your thoughts and opinions, but metadata reveals your actions.
What is metadata really? It's data about your message, including:
Source
Type
Destination
Time
Length
Size
...and virtually any other identifiable pattern of your messages.
Metadata can be analyzed to reveal patterns of Internet traffic. This data is like a fingerprint. There is actually a type of attack called "website fingerprinting," and in these types of attacks, the attacker downloads all the pages of a website, analyzes the metadata of those pages, and then matches it to traffic patterns. They can then learn what specific page a person might be viewing: alarming, for example, in the case of a website that provides health advice.
In short, metadata can reveal:
What specific web page you are visiting, even over HTTPS
What web domain you query through encrypted DNS
What you type, even in an encrypted web application (search, taxes, health)
What you say in a voice conversation over an encrypted voice channel
...and more.
Unfortunately, metadata is largely insecure, meaning that there are many entities that have direct access to it. These include:
Internet service providers
Internet exchanges
Standalone systems
Even your Wi-Fi router
...and interceptors, including, as we know, the ANB.
How does Mixnet Nym help protect your data?
Mixnet doesn't let the spy find out:
What you say
Who you are communicating with (sending or receiving messages)
When you communicate
How long you have been communicating
Where you are communicating from
The amount of data you are sending or receiving
Any patterns in your communications
Whether you communicate at all
The Nym mixnet is an open source decentralized infrastructure designed to protect the privacy of people and the applications and digital services they use.
The Internet is global, and so is Nym: join the Nym community wherever you are and help create a private Internet today.
Discord | Telegram | Twitter | Blog | Telegram_RU
Privacy loves company
Subscribe to my newsletter
Read articles from AnnaV directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
