AWS Security Groups and Network Access Control Lists (NACLs)
 Rajat Chauhan
Rajat Chauhan
What Are Security Groups?
AWS Security Groups act as virtual firewalls that control inbound and outbound traffic for EC2 instances, providing a layer of security at the instance level. Each instance can be associated with one or more security groups, and these groups essentially act as a set of firewall rules.
Key Features and Functions
Stateful Filtering: Security Groups are stateful, meaning if an inbound rule allows traffic, the return traffic is automatically permitted, simplifying rule configurations.
Security Group Rules: Rules can be configured based on IP protocols, port ranges, and source/destination IP addresses.
Application-Level Security: They can be used to define rules that allow specific applications or services to communicate with the instances they're associated with.
Configurations and Best Practices
Least Privilege Principle: Security Groups follow the principle of least privilege, meaning only necessary ports and protocols should be opened.
Ephemeral Ports: Ensure outbound rules allow traffic for ephemeral ports if applications require responses from external servers.
Regular Review: Periodically review and audit security group configurations to ensure they align with security requirements and minimize any unnecessary exposure.
Use Cases
Web Applications: Security Groups can be used to control traffic to web servers, allowing HTTP (port 80) and HTTPS (port 443) traffic.
Database Access Control: Restrict access to databases like MySQL (port 3306) or PostgreSQL (port 5432) to specific IP ranges.
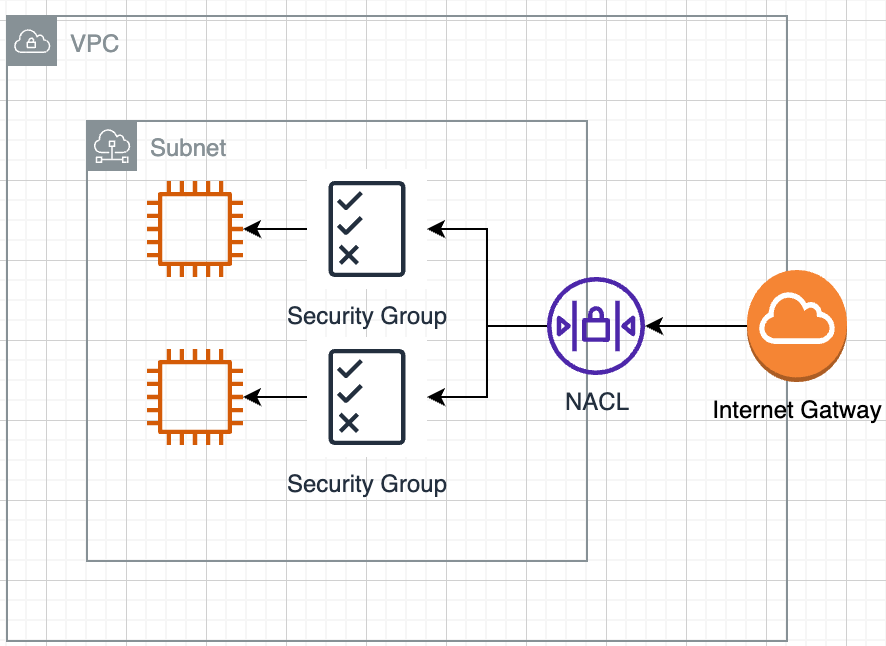
What Are Network Access Control Lists (NACLs)?
AWS NACLs are stateless network-level security measures that control traffic in and out of subnets. Unlike Security Groups, which are instance-specific, NACLs operate at the subnet level.
Key Features and Functions
Ordered Rule Evaluation: NACLs follow numbered rules in sequential order from lowest to highest, processing rules based on their order.
Stateless Filtering: Unlike Security Groups, NACLs require explicit rules for both inbound and outbound traffic. If an inbound rule permits traffic, an outbound rule permitting the response traffic is required.
Allow/Deny Rules: NACLs allow defining rules to explicitly allow or deny traffic based on IP addresses, protocols, and port ranges.
Configurations and Best Practices
Careful Rule Configurations: Due to their stateless nature, ensure proper ingress and egress rules to allow necessary traffic while maintaining security.
Regular Auditing: Similar to Security Groups, perform periodic audits to ensure NACLs align with security policies and minimize unnecessary exposure.
Use Cases
Segmenting Workloads: NACLs can be used to segment workloads within a VPC, applying different levels of access control to different subnets.
Additional Layer of Security: They provide an extra layer of security by filtering traffic at the subnet level, complementing the security provided by Security Groups.

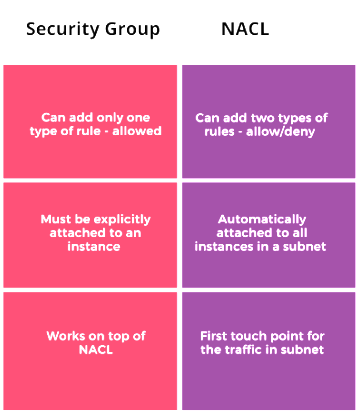
Conclusion
In the AWS ecosystem, Security Groups and NACLs play vital roles in controlling and securing network traffic. While Security Groups operate at the instance level with stateful filtering, NACLs function at the subnet level with stateless filtering. Both are essential components for implementing a robust security posture within AWS environments.
Understanding their functionalities, configuring them according to best practices, and regularly reviewing their settings are crucial steps to ensure a secure and well-managed AWS infrastructure.
Subscribe to my newsletter
Read articles from Rajat Chauhan directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Rajat Chauhan
Rajat Chauhan
Rajat Chauhan is a skilled Devops Engineer, having experience in automating, configuring, deploying releasing and monitoring the applications on cloud environment. • Good experience in areas of DevOps, CI/CD Pipeline, Build and Release management, Hashicorp Terraform, Containerization, AWS, and Linux/Unix Administration. • As a DevOps Engineer, my objective is to strengthen the company’s applications and system features, configure servers and maintain networks to reinforce the company’s technical performance. • Ensure that environment is performing at its optimum level, manage system backups and provide infrastructure support. • Experience working on various DevOps technologies/ tools like GIT, GitHub Actions, Gitlab, Terraform, Ansible, Docker, Kubernetes, Helm, Jenkins, Prometheus and Grafana, and AWS EKS, DevOps, Jenkins. • Positive attitude, strong work ethic, and ability to work in a highly collaborative team environment. • Self-starter, Fast learner, and a Team player with strong interpersonal skills • Developed shell scripts (Bash) for automating day-to-day maintenance tasks on top of that have good python scripting skills. • Proficient in communication and project management with good experience in resolving issues.