Advent of Cyber 2023 — Day 18 Writeup
 Anuj Singh Chauhan
Anuj Singh ChauhanLearning Objectives
In this task, we will:
Identify the CPU and memory usage of processes in Linux.
Kill unwanted processes in Linux.
Find ways a process can persist beyond termination.
Remove persistent processes permanently.
Identifying the Process
Linux gives us various options for monitoring a system's performance. Using these, we can identify the resource usage of processes. One option is the top command. This command shows us a list of processes in real time with their usage. It's a dynamic list, meaning it changes with the resource usage of each process.
To exit from this view, press the q key.
Killing the Culprit
At the top of the output of the top command, we find our culprit. It's the process named a, which uses unusually high CPU resources. In normal circumstances, we shouldn't have processes consistently using very high amounts of CPU resources. However, certain processes might do this for a short time for intense processing.
The process we see here consistently uses 100% of the CPU resources, which can signify a hard-working malicious process, like a cryptominer. We see that the root user runs this process. The process' name and resource usage gives a suspicious vibe, and assuming this is the process unnecessarily hogging our resources, we would like to kill it. (Disclaimer: In actual production servers, don't try to kill processes unless you are sure what you are doing.)
If we wanted to perform forensics, we would take a memory dump of the process to analyse it further before killing it, as killing it would cause us to lose that information. However, taking a memory dump is out of scope here. We will assume that we have already done that and move on to termination.
We can use the kill command to kill this process. However, since the process is running as root, it's a good idea to use sudo to elevate privileges for killing this process. Let's try to kill the process. Note that you will have to replace 2062 with the PID that is shown in your top command's output.
Checking the Cronjobs
Our first hint of what happened with the process will be in the cronjobs. Cronjobs are tasks that we ask the computer to perform on our behalf at a fixed interval. Often, that's where we can find traces of auto-starting processes.
To check the cronjobs, we can run the command crontab -l.
Check for Running Services
Maybe we should check for running services that might bring the process back. But the process name is quite generic and doesn't give a good hint. We might be clutching at straws here, but let's see what services are running on the system.
To do this, we use the systemctl list-unit-files to list all services. Since the service we are looking for must be enabled to respawn the process, we use grep to give us only those services that are enabled.
To check the status or to stop the service:
systemctl status service_name
sytemctl stop service_name
This will disable the service running but won't delete/remove the files from the system by locating the file from status command and then removing the source file/files.
What is the name of the service that respawns the process after killing it?
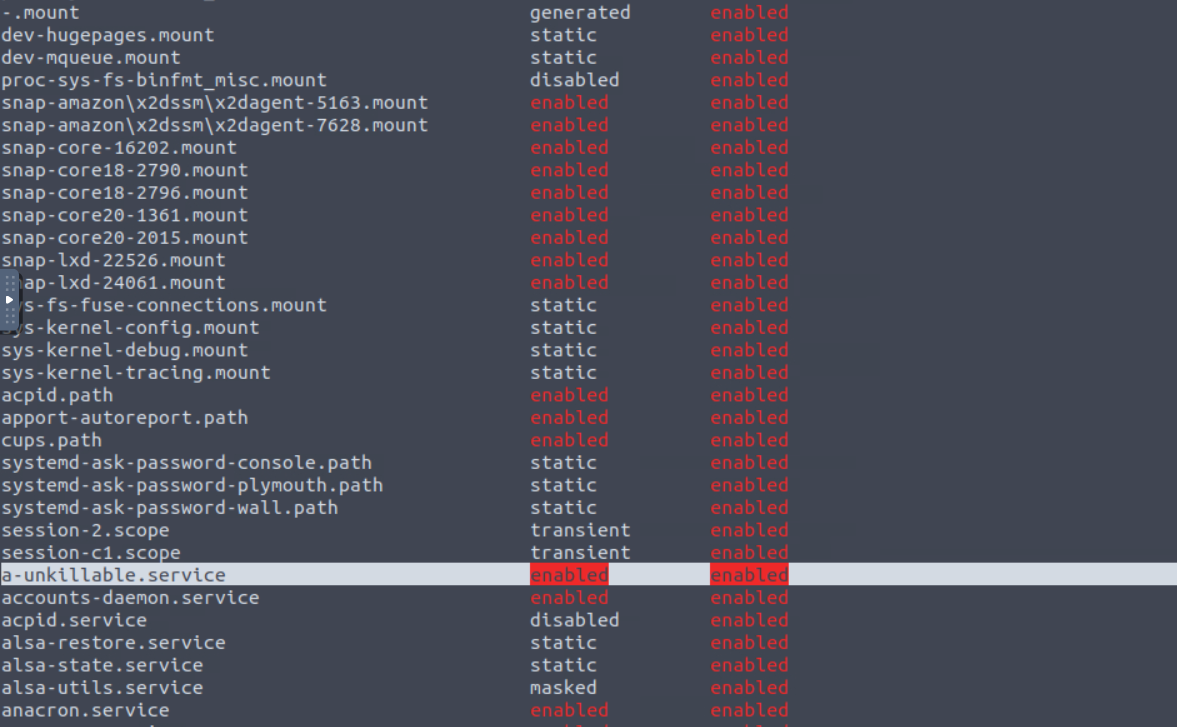
Answer: a-unkillable.service
What is the path from where the process and service were running?
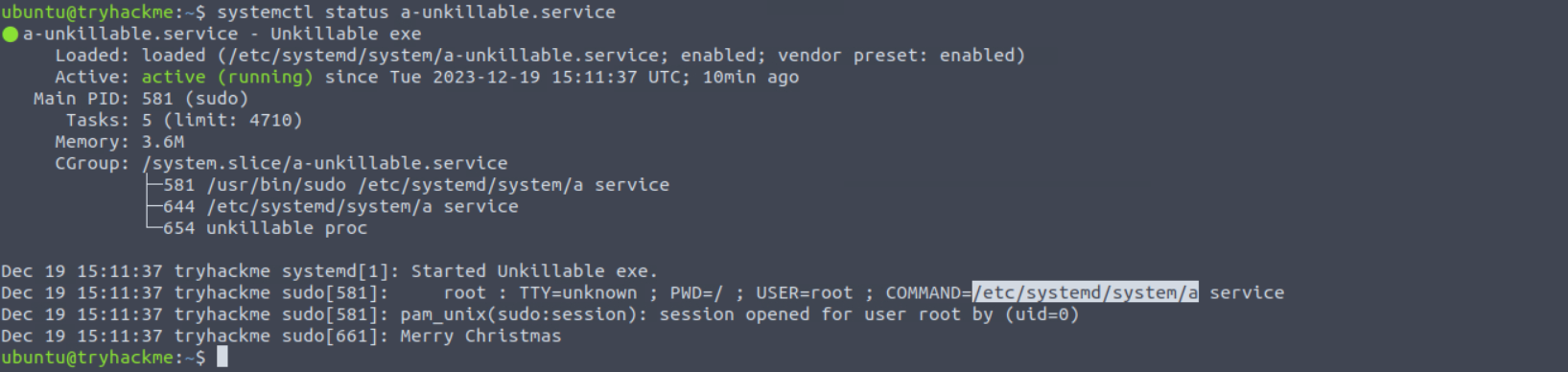
Answer: /etc/systemd/system
The malware prints a taunting message. When is the message shown? Choose from the options below.
1. Randomly
2. After a set interval
3. On process termination
4. None of the above
Answer: 4
thanks for reading!!
Subscribe to my newsletter
Read articles from Anuj Singh Chauhan directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
