Retrieving Secrets from AWS Secret Manager using AWS Lambda: A Comprehensive Guide 🛡️🔄
 Jothi Arul Prakash
Jothi Arul Prakash
Introduction
AWS Secret Manager stands out as a cornerstone for safeguarding your applications, services, and IT resources, eliminating the need for upfront investments and ongoing maintenance hassles. This fully managed service facilitates the rotation, management, and retrieval of critical secrets, such as database credentials and API keys, seamlessly throughout their lifecycle. This blog post delves into the intricacies of retrieving secrets from AWS Secret Manager using the dynamic capabilities of AWS Lambda.
Use Case Examples
Database Credentials: Consider an application interfacing with a database. Storing database credentials directly within your code poses a security risk. AWS Secret Manager provides a secure vault to store and manage these credentials, offering a robust layer of protection against unauthorized access.
🔄 Storing your database credentials in AWS Secret Manager not only enhances security but also streamlines the management process. Imagine the ease of updating credentials without modifying the application code, ensuring a swift response to security requirements or credential changes.
API Keys: In the realm of authentication, API keys play a pivotal role. Rather than embedding these keys directly into your codebase, AWS Secret Manager allows you to securely store and dynamically fetch them during runtime.
🔄 Embracing this approach adds an extra layer of flexibility to your application. It enables you to seamlessly rotate API keys when necessary, reducing the risk of unauthorized access due to compromised or deprecated keys.
Third-Party Integrations: For applications integrating with third-party services, the secure storage of tokens or keys becomes paramount. AWS Secret Manager becomes a central repository for these crucial components, offering a single source of truth.
🔄 This centralized approach simplifies the management of third-party integrations, providing a unified platform to update or rotate keys effortlessly. The enhanced security measures ensure a robust shield against potential vulnerabilities stemming from outdated or compromised tokens.
Steps to Retrieve Secrets
1. Create a Secret in AWS Secret Manager
Navigate to the AWS Management Console, locate Secrets Manager, and initiate the creation of a new secret.
Opt for Other types of secrets and select Plaintext. Define key-value pairs (e.g.,
db_usernameanddb_password).Assign a meaningful secret name (e.g.,
aws-secretkey-demo) and proceed to the next step.🛠️ When creating a secret, it's prudent to establish a nomenclature that aligns with your application's architecture. This ensures clarity and coherence in managing secrets across various components.
2. AWS Lambda Setup
Utilize the AWS Management Console to craft an AWS Lambda function tailored to your needs.
Link to Github: https://github.com/jothiarulprakash/AWS_Secrets_Retreiver.git
Embed the following Python snippet within your Lambda code to seamlessly retrieve the secret:
import boto3
import json
client = boto3.client('secretsmanager', region_name='your_region')
def lambda_handler(event, context):
secret_name = 'aws-secretkey-demo'
get_secret_value_response = client.get_secret_value(SecretId=secret_name)
if 'SecretString' in get_secret_value_response:
secret_data = json.loads(get_secret_value_response['SecretString'])
else:
secret_data = get_secret_value_response['SecretBinary'] # Handle binary secrets
print(f"Secret Name: {secret_name}")
for key, value in secret_data.items():
print(f"{key}: {value}")
Code to retrieve the secret info from AWS Secret Manager
Ensure that the IAM role associated with your Lambda function possesses the
secretsmanager:GetSecretValuepolicy.🚀 Fine-tuning the IAM role ensures that your Lambda function has precisely the required permissions, minimizing potential security risks.
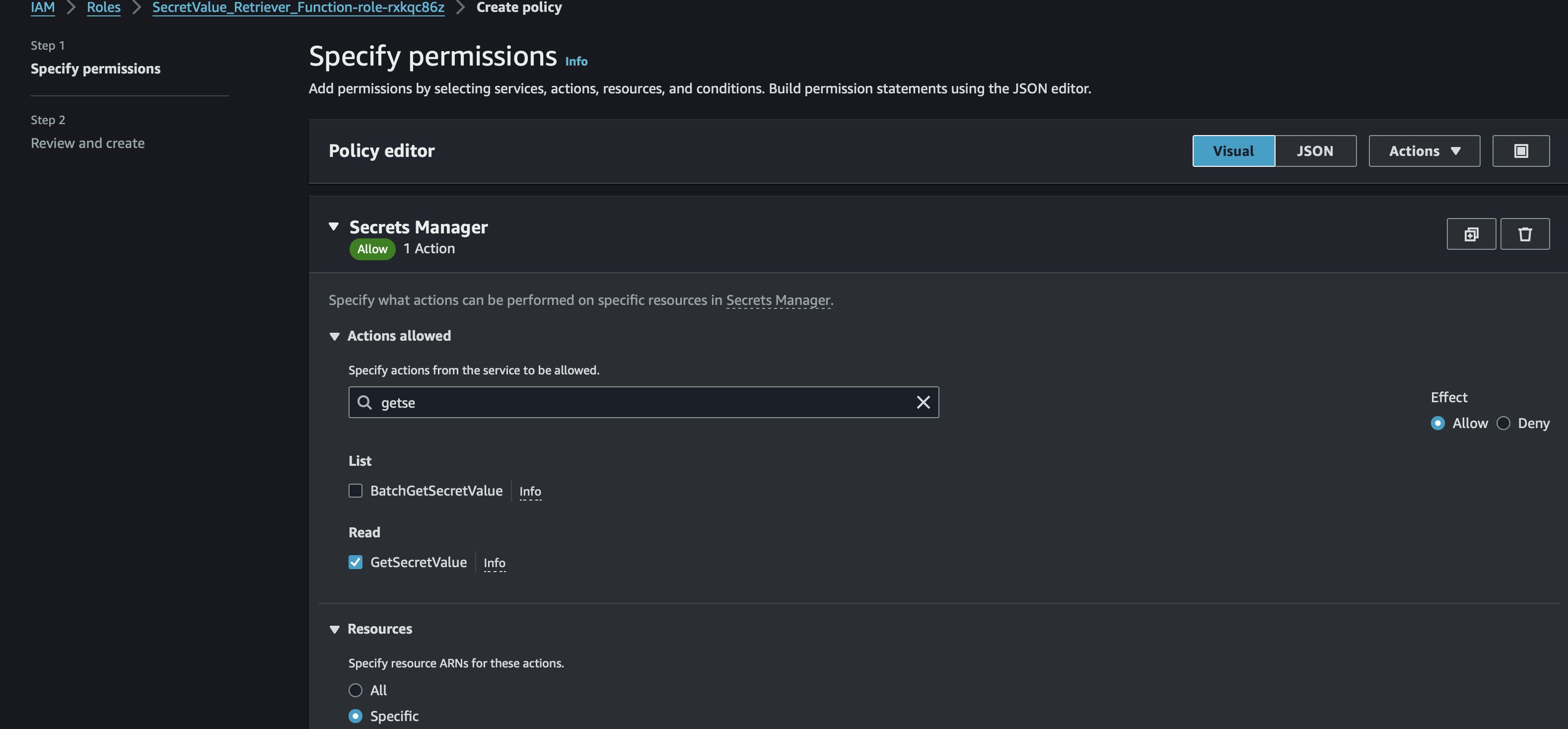
GetSecretValue Policy - attached
3. Deploy and Test
- Deploy your Lambda function, kickstarting the integration between AWS Lambda and AWS Secret Manager.
Execute a comprehensive test, validating the seamless retrieval of secret data showcased in the Lambda function logs.
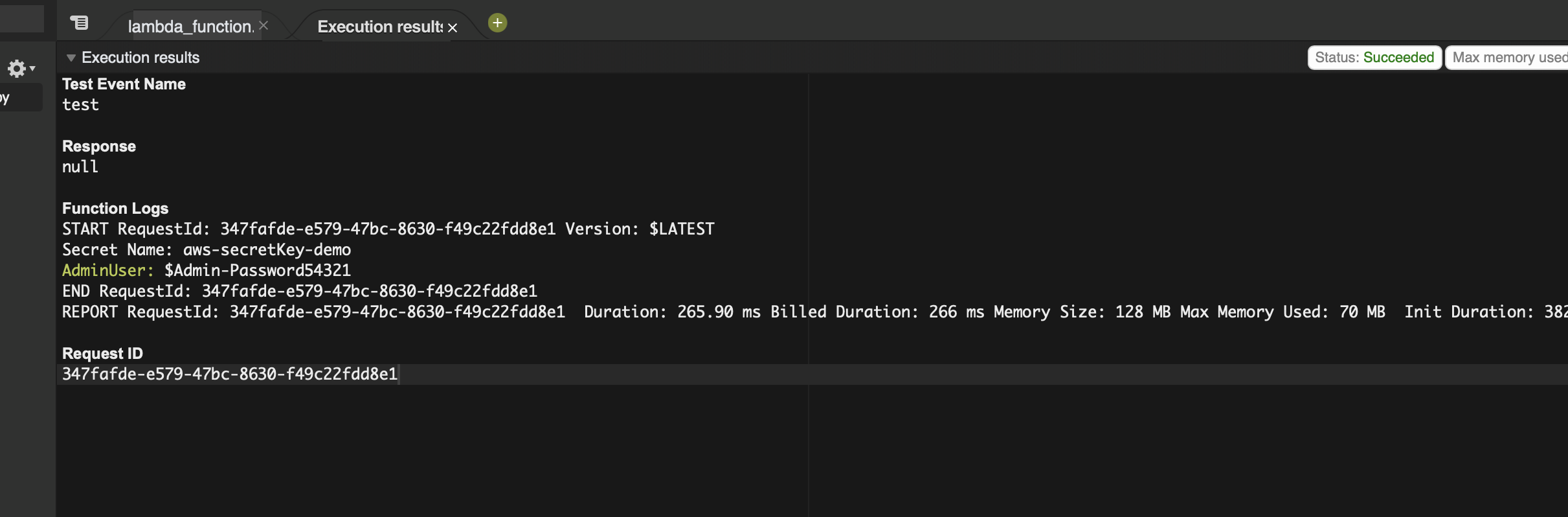
Secret Key: AdminUser ; Secret Value: $Admin-Password54321
Experiment further by modifying the secret value within AWS Secret Manager and rerun the Lambda function. Witness the automatic retrieval of the updated secret value, highlighting the dynamic nature of the integration.
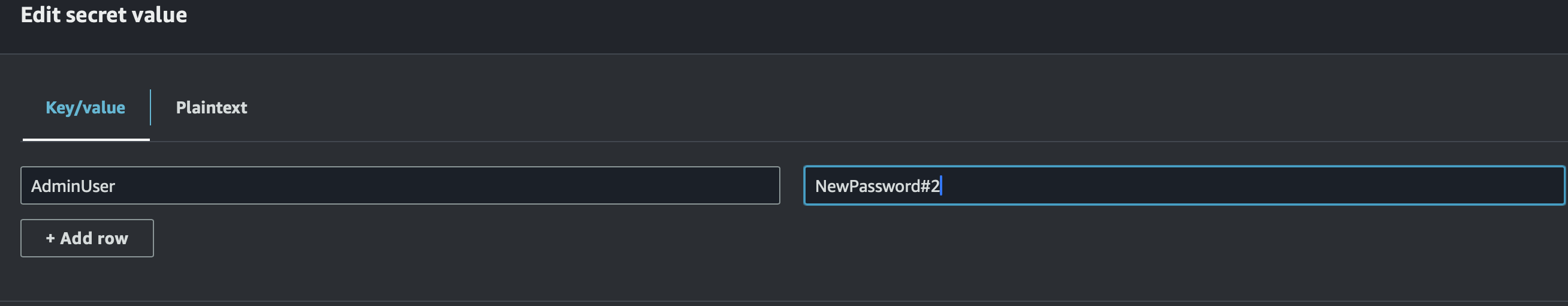
Edited the Value to a different text
Now the changed value should be retrieved by the same code. Let's try.
Here it is...!
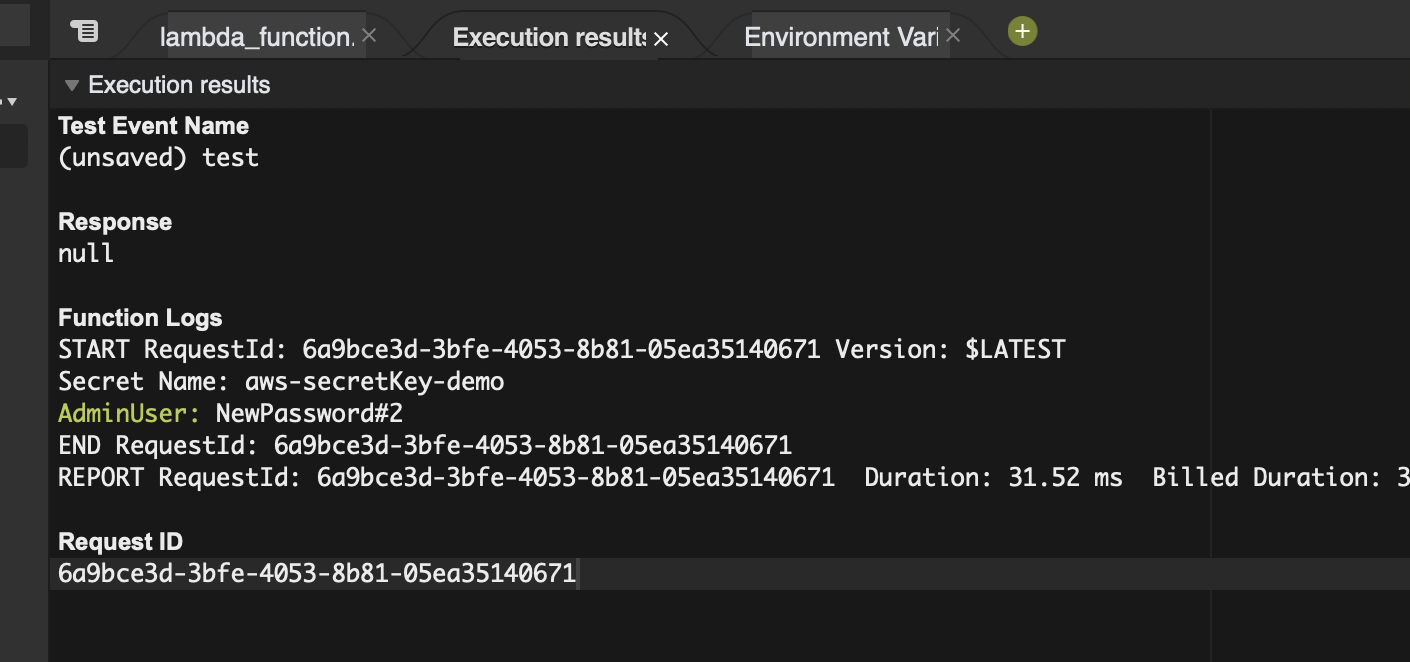
🧪 Implementing an automated testing strategy ensures the resilience and adaptability of your solution. Regular testing, especially after secret updates, ensures the continued efficacy of your secrets management strategy.
Introduction to Services and Their Synergy
In addition to AWS Secret Manager and AWS Lambda, AWS offers a suite of services that synergistically contribute to a comprehensive secrets management strategy.
AWS Key Management Service (KMS): Enhance the security of your secrets by leveraging AWS KMS for encryption. Integrate AWS KMS with AWS Secret Manager to implement robust encryption mechanisms for stored secrets.
AWS Identity and Access Management (IAM): Augment the security posture by finely tuning permissions through IAM roles associated with AWS Lambda functions. Limit access to secrets based on the principle of least privilege.
🔒 Utilizing IAM roles judiciously adds an extra layer of security, ensuring that only authorized entities can access critical secrets.
AWS CloudWatch Logs: Monitor and analyze the behavior of your Lambda functions through AWS CloudWatch Logs. Implement robust logging practices to capture relevant information, aiding in troubleshooting and security audits.
📊 Leveraging AWS CloudWatch Logs provides insights into the interactions between AWS Lambda and AWS Secret Manager, facilitating proactive identification of potential issues or security incidents.
Conclusion
AWS Secret Manager, coupled with AWS Lambda, offers a resilient and scalable solution for managing secrets in the cloud. By adopting this dynamic integration, your applications gain heightened security and flexibility, ensuring a proactive response to evolving security requirements.
Incorporating additional AWS services, such as AWS KMS, IAM, and CloudWatch Logs, fortifies your secrets management strategy. This holistic approach not only safeguards your secrets but also establishes a robust foundation for secure and scalable cloud-native applications.
☁️Stay AWSome!🌐
🔐🚀 #AWS #SecretsManagement #AWSLambda #SecurityInCloud
#jothiarulprakash
Subscribe to my newsletter
Read articles from Jothi Arul Prakash directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Jothi Arul Prakash
Jothi Arul Prakash
I'm a Software Engineer👨💻 focused on securing applications and data protection. 💼 Led cloud migration projects, ensuring seamless transitions to Azure Cloud for diverse clients. 💻 Developed and deployed web applications, enhancing user experiences and business efficiency. 💼 Collaborated with cross-functional teams to understand client requirements and deliver tailor-made solutions.
