SECPlayground Christmas CTF 2023
 Ar3mus
Ar3mus
Well met!! Everyone This is the first write-up that I have written in English Language :P
In this blog, I write up only challenges that I can get the flag.
SECPlayground had a CTF Event at every Festival and I really liked it :)

flag format : encryption{} , crypto{} , RE{} , forensic{}

Ar3mus : As you can see here is the map of SECplayground Christmas CTF 2023, interestingly, you can see If players who can solve challenges will show on the map.

Ar3mus : Let's have a look at the map. they have six parts to the challenges you can see the categories below
Cryptography

Ar3mus : Let's start with the First category name Cryptography, They have five challenges Difficulty level: Easy - Medium
01 : X0r challenge
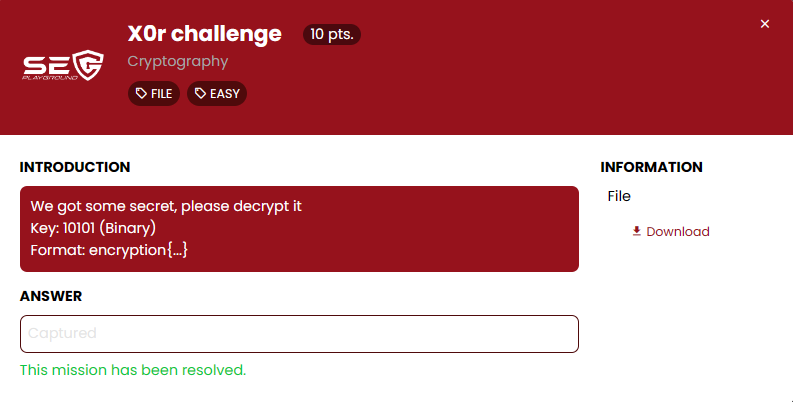

Ar3mus : at first we will get the file name "cipher text.txt"
a}p5sytr5|f5p{vglea|z{nM$gJA&fah
Ar3mus : inside the file "cipher text.txt" you can see there is a cipher here If you take a look at the challenge name is X0R and the Key is a Binary so I think that the type of this cipher is XOR 😂
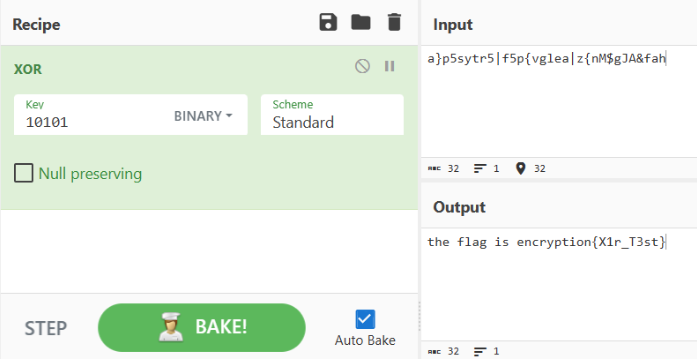
Ar3mus : in this case, you can use a tool called cyberchef to decrypt cipher text
Ar3mus : You got the flag!!
encryption{X1r_T3st}
02 : Gift from Santa Claus!
Ar3mus : Nice! We got a Merry_Christmas song 🎅
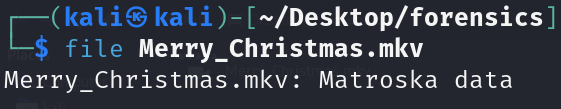
Ar3mus : If you check the file type you can see that is Matroska data 🤔
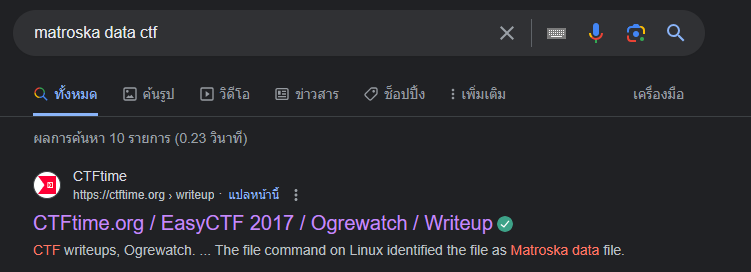
Ar3mus : so I'm moving on to Google and searching about that thing!

src : CTFtime.org / EasyCTF 2017 / Ogrewatch / Writeup
Ar3mus : Migdalo said that We can use a tool called Mkvtoolsnix but you can install on Kali Linux by type mkvinfo command
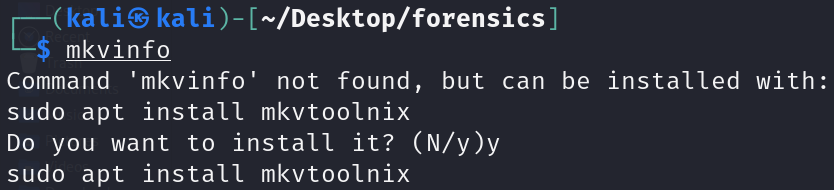
mkvinfo Merry_Christmas.mkv
+ EBML head
|+ EBML version: 1
|+ EBML read version: 1
|+ Maximum EBML ID length: 4
|+ Maximum EBML size length: 8
|+ Document type: matroska
|+ Document type version: 4
|+ Document type read version: 2
+ Segment: size 3096537106
|+ Seek head (subentries will be skipped)
|+ EBML void: size 81
|+ Segment information
| + Timestamp scale: 1000000
| + Multiplexing application: Lavf58.45.100
| + Writing application: Lavf58.45.100
| + Segment UID: 0x9d 0x5c 0xd7 0xe0 0x14 0x8d 0x83 0xed 0x5f 0xd5 0x0d 0x09 0xd4 0xef 0x27 0xb7
| + Duration: 00:03:34.760000000
|+ Tracks
| + Track
| + Track number: 1 (track ID for mkvmerge & mkvextract: 0)
| + Track UID: 12671067688762041170
| + "Lacing" flag: 0
| + Language: und
| + Track type: video
| + Default duration: 00:00:00.040000000 (25.000 frames/fields per second for a video track)
| + Codec ID: V_MS/VFW/FOURCC
| + Video track
| + Pixel width: 1280
| + Pixel height: 720
| + Display unit: 4
| + Video color information
| + Color range: 2
| + Codec's private data: size 40 (FourCC: 0x4d504e47 "MPNG")
| + Track
| + Track number: 2 (track ID for mkvmerge & mkvextract: 1)
| + Track UID: 773114496817618234
| + "Lacing" flag: 0
| + Language: und
| + Codec ID: A_PCM/INT/LIT
| + Track type: audio
| + Audio track
| + Channels: 2
| + Sampling frequency: 44100
| + Bit depth: 16
|+ Tags
| + Tag
| + Targets
| + Simple
| + Name: ENCODER
| + String: Lavf58.45.100
| + Tag
| + Targets
| + Track UID: 12671067688762041170
| + Simple
| + Name: DURATION
| + String: 00:03:34.760000000
| + Tag
| + Targets
| + Track UID: 773114496817618234
| + Simple
| + Name: DURATION
| + String: 00:03:34.760000000
|+ Cluster
| + Track number: 1 (track ID for mkvmerge & mkvextract: 0)
| + Track type: video
| + Track number: 2 (track ID for mkvmerge & mkvextract: 1)
| + Track type: audio
mkvextract tracks Merry_Christmas.mkv 0:video 1:audio
Ar3mus : after extracted file Matroska data, you will get video and audio files. but I try to Forensics there File but I don't see any interest.
Ar3mus: so Sudlit recommended me to use This Tool
itxKAE/Video-Steganography: School Assignment (github.com)
General Flow

src :
https://github.com/itxKAE/Video-Steganography?tab=readme-ov-file#general-flow
Ar3mus : as you can see at General Flow This tool can split video into Frames and Audio so the interesting point is Extract Frames and Show Hidden Message

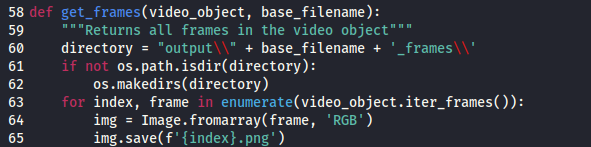
Ar3mus : I recommend you must modify aviGUI.py code at line 65 by deleting {directory} because when you use decode.py function read-only number file name
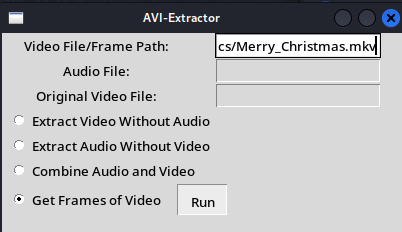
Ar3mus : There you go, Nicely file name.

Ar3mus : and then this file Decoder.py you must modify by delete "\\" at line 13
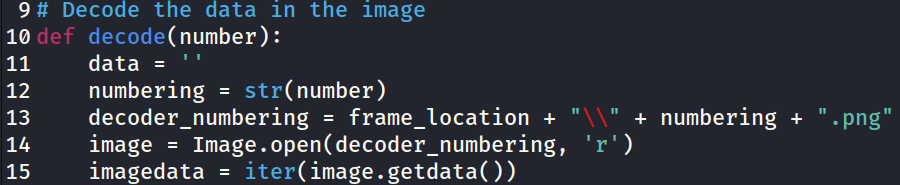
Ar3mus : now Let's test it!
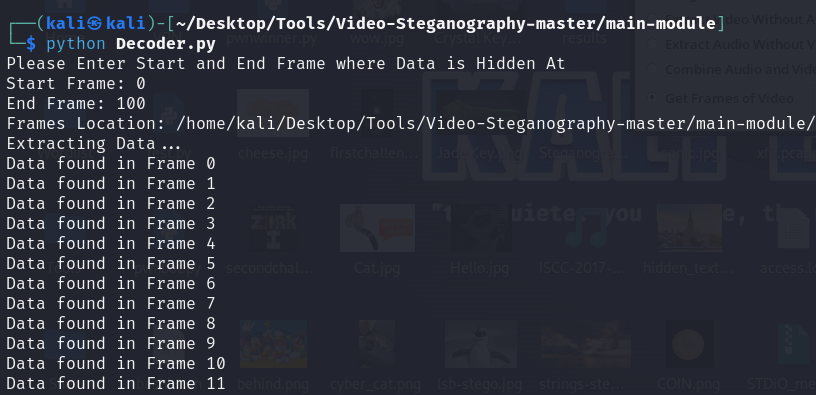
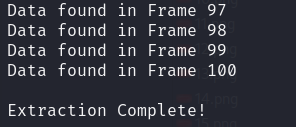
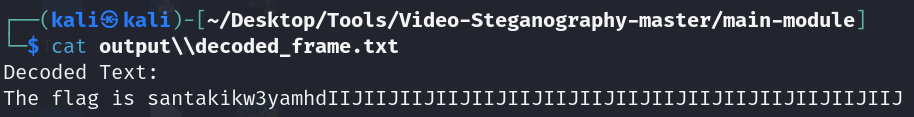
Ar3mus : You got the Flag!!!
cryptography{santakikw3yamhd}
03 : Secret message on the notice board

Ar3mus : after you extracted the file zip name "Secret message on the notice board" you can see there are some pictures and one audio file.
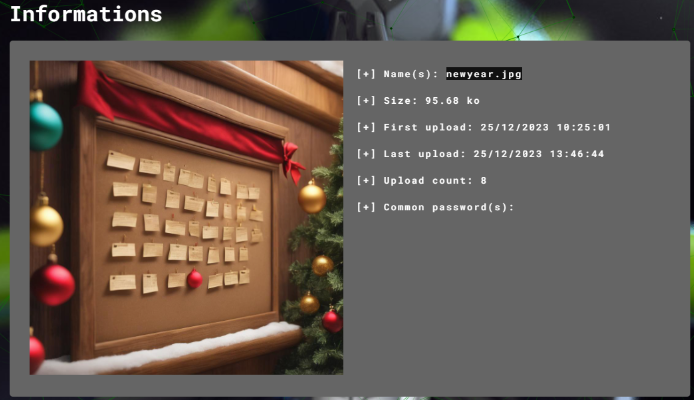
Ar3mus : I assumed details from the challenge they said that the company**'s** notice board has a secret message so I thought file picture newyear.jpg was suspicious
Ar3mus : about Steganography I usually use a tool called Aperisolve
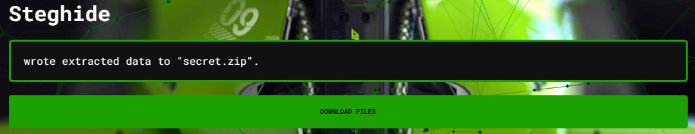
Ar3mus : take a look at Steghide output we can extract "secreat.zip" inside picture
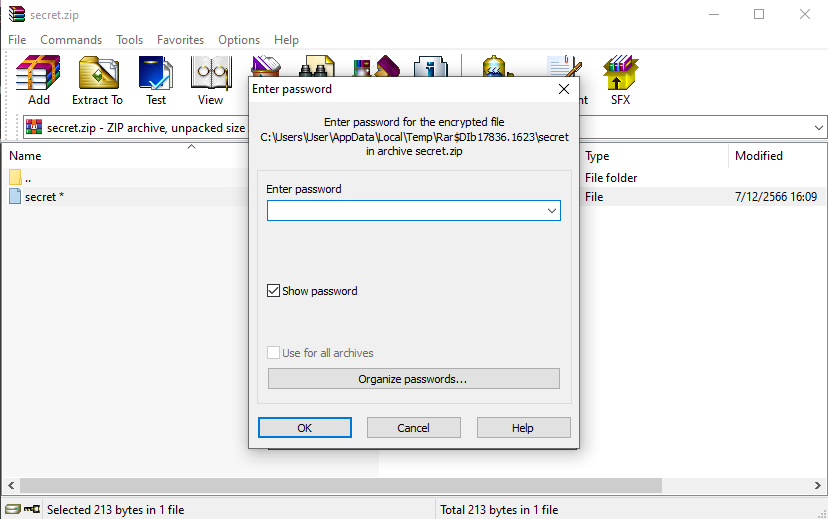
Ar3mus : if you click on secret.zip you will see file secret is encrypted
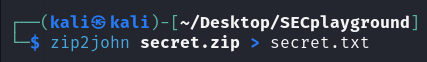
Ar3mus : you can use a tool called JohnTheRipper to crack encrypted files in this case is a zip file encrypt
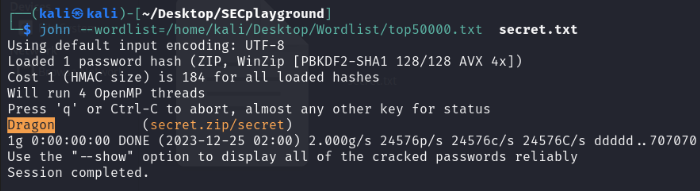
Ar3mus : I recommend using top50000.txt wordlist because it cracks faster than rockyou.txt
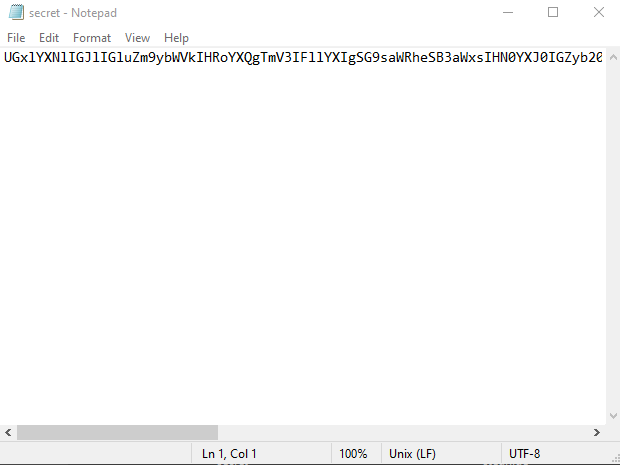
Ar3mus : as you can see inside the secret file got cipher text
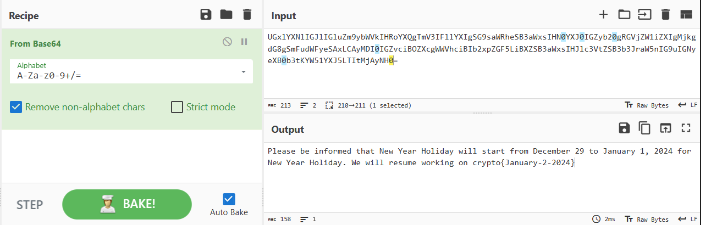
Ar3mus : so we put it in cyberchef you will see the flag decode from Base64
Ar3mus : You got the flag!!!
crypto{January-2-2024}
04 : Keep your Christmas-heart open all the year round
Ar3mus : Keep your Christmas-heart open all the year round, What a lovely challenge


Ar3mus : After you extract the zip file there are many file types.🤯
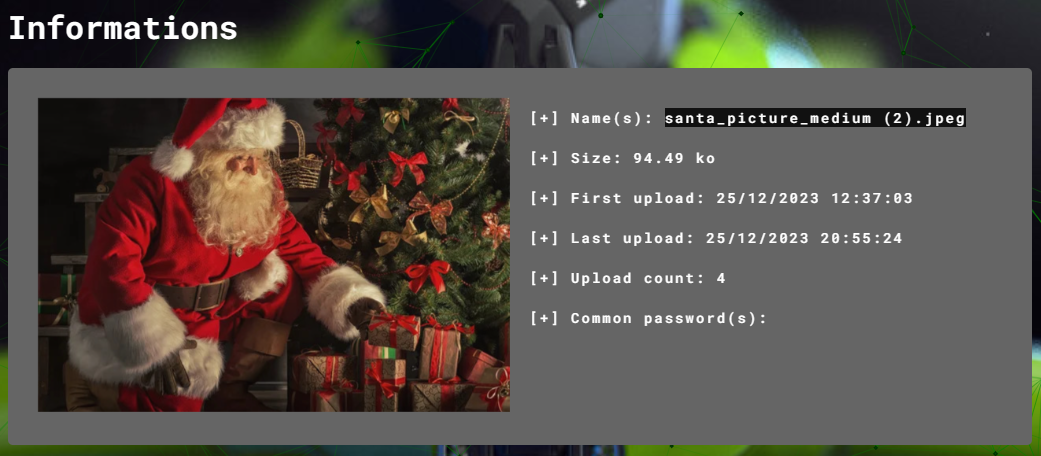
Ar3mus : challenge introduction Help open Santa gift box so I thought "santa_picture_medium (2).jpg" was the key to getting the flag in this challenge but after I uploaded it to Aperosolve nothing interesting but I had another solution that you can find a hidden passphrase from the picture.
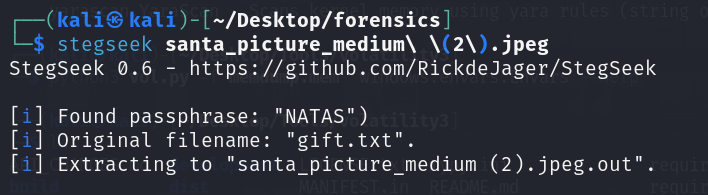
Ar3mus : you can use a tool called stegseek.
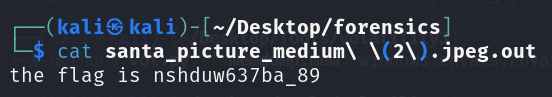
Ar3mus : I didn't realize that it would be easy like this.
Ar3mus : as always, You got the flag!!!
cryptography{nshduw637ba_89}
Reverse Engineer

Ar3mus : Let's move on to the next category name Reverse Engineer!!!, I love this map because it is an ice Rink and It's so cool. Difficulty level: Easy

Ar3mus : But they got only one challenge. 😭
01 : Forgetful Santa
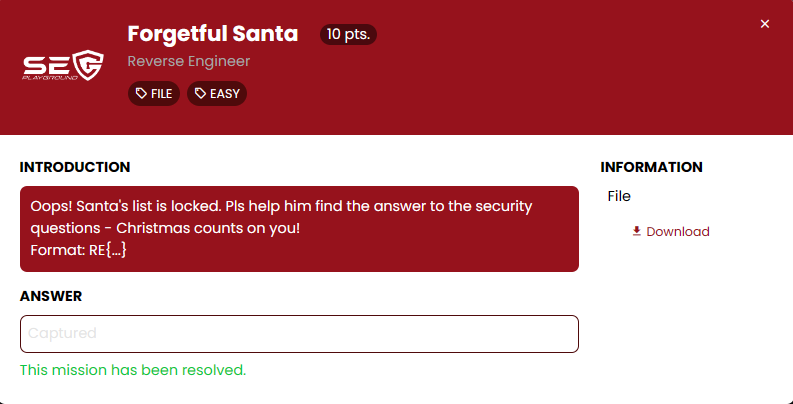
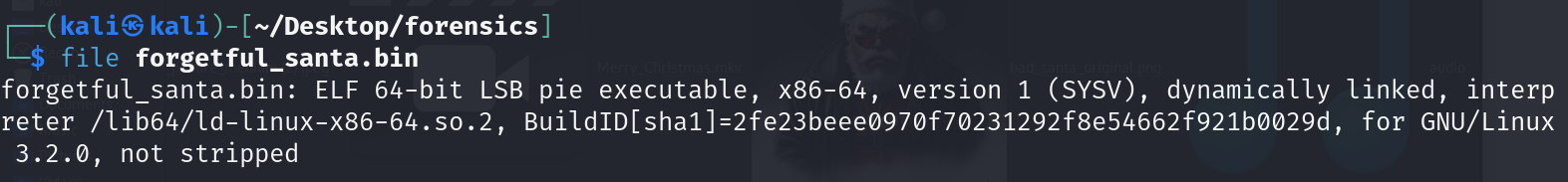
Ar3mus : as you can see we can execute this file and I try to enumerate data in a file by strings.
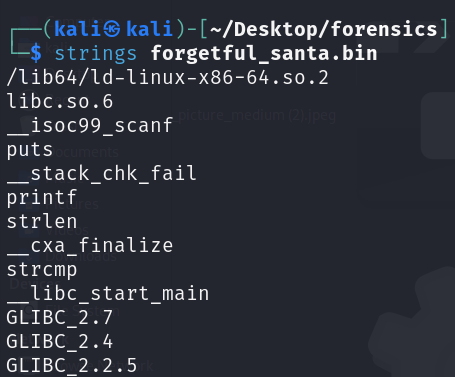
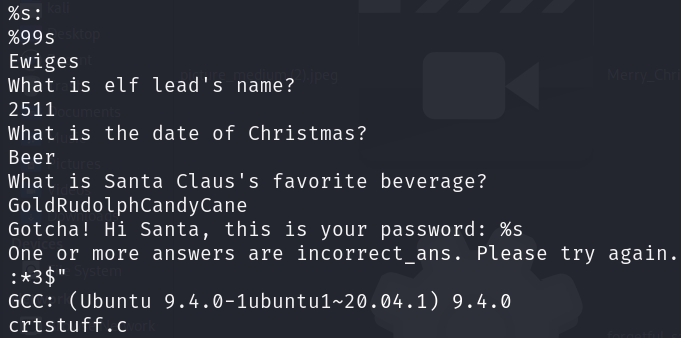
Ar3mus : after you use the strings command and scroll down to see data you will see that is security questing in the challenge.
Ewiges What is elf lead's name?
2511 What is the date of Christmas?
Beer What is Santa Claus's favorite beverage?
GoldRudolphCandyCane Gotcha!
Hi Santa, this is your password: %s
One or more answers are incorrect_ans. Please try again. ;P
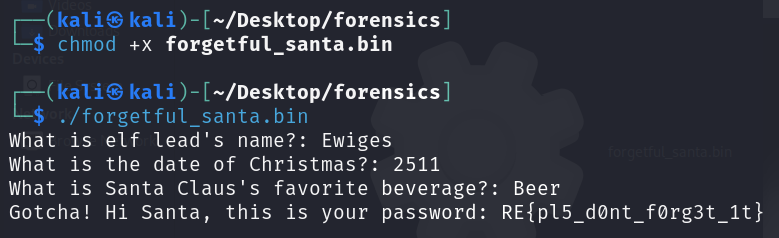
Ar3mus : I think it's an unintended solution for this challenge 😅
Ar3mus : You got the flag!!!
RE{pl5_d0nt_f0rg3t_1t}
Ar3mus : Thank you for Reading my blog I hope you enjoy it and Merry Christmas!!

⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⣀⣤⣤⣤⣤⣤⣤⣤⣤⣀⣀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠀⠀⠀⠀⠀
⢀⣤⣶⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣶⣤⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⣠⣾⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣷⣄⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⢠⣾⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⠟⠛⠻⣿⣿⣿⣿⣿⣿⣿⣷⣄⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⣰⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⡇⠀⠀⠀⢸⣿⣿⣿⣿⣿⣿⣿⡿⠂⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⣸⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣦⣤⣴⣿⣿⣿⣿⣿⡿⠛⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⢰⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⠿⠛⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⣾⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⠿⠋ ⢀⣀⠀⠀⠀⠀⠀⠀
⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⠟⠋⠁⠀⠀ ⣴⣿⣿⣿⣦⠀⠀⠀
⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣷⣦⣀⠀⠀⠀ ⢿⣿⣿⣿⡟ Ar3mus@ SECPlayground Christmas CTF 2023
⢿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣷⣦⣄ ⠉⠉⠁⠀⠀⠀⠀
⠸⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣦⣄⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⢻⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣶⣄⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠻⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣷⡄⠀⠀⠀⠀⠀
⠀⠀ ⠙⢿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⡿⠋
⠀⠀⠀ ⠀⠛⢿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⡿⠋⠁
⠀⠀ ⠀⠀⠀⠀⠉⠻⢿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⠿⠛⠉⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀ ⠀⠀⠉⠙⠛⠛⠻⠿⠿⠟⠛⠛⠋⠉⠀⠀⠀⠀⠀
Subscribe to my newsletter
Read articles from Ar3mus directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Ar3mus
Ar3mus
Student at NKRAFA who interesting about Cyber Security and Head of NKRAFA Cyber Club 2024