Connecting an AWS EC2 Instance of a Private Subnet using Bastion Host
 Sushan Shrestha
Sushan Shrestha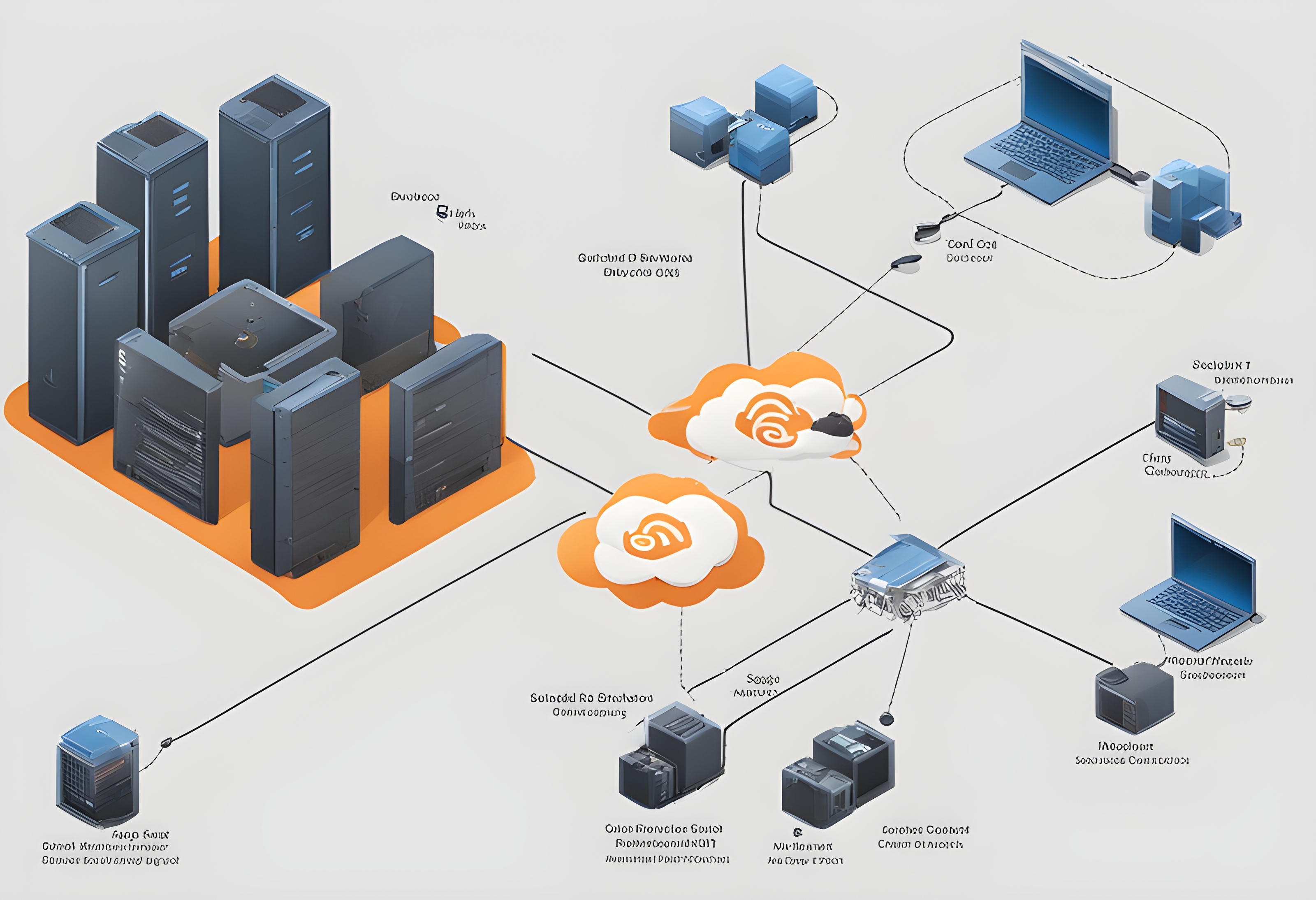
In this article, we will see how we can connect an instance present in a private subnet with the help of an instance present in a public subnet.
Let us first have look over the following mentioned Key terminologies where we will first try to understand few things (like EC2 instance and other things) theoretically and then we will jump into the implementation section.
Key terminologies :
Following are the key terminologies that you should be familiar with before proceeding ahead with the article:
EC2 instance: Ec2 instance is like a laptop or PC or any computer device in which you can run your operating system like Linux, windows, etc.
Ami(Amazon Machine Image): It contains the operating system which we use to launch an ec2 instance.
Subnet: A subnet is like a subsection of a large network or in other words we may also illustrate subnet as a small sub part of a network. For example, we can take an analogy of the Internet service provider as a large network in our town or city and our home network as a small network. So in that case our home network can be considered as a subnet of our Internet service provider network.
Availability Zones: These are distinct locations that are engineered to be isolated from failures in other availability zones.
Public Subnet: It has a route table that is connected to an Internet gateway which allows information and data to go in and out from the subnet and to and from the internet.
Private Subnet: It is also associated with a route table but it is not attached to an internet gateway which means information flows from one subnet to another but within the VPC which means traffic from this subnet cannot go through the internet gateway and out to the internet.
Route Table: A route table is a set of rules called routes that are used to determine where network traffic is directed.
VPC: A private sub-section of AWS that we control, in which we can place AWS resources such as ec2 instances and databases. We have full control over who has access to the AWS resources that we place inside VPC.
Internet Gateway: A combination of hardware and software that provides our private network with a route to the outside world (meaning internet) of the VPC.
Security Groups: These are like firewalls that allow or deny the traffic. When we launch an instance, we associate one or more security groups with the instance. We add rules to each security group that allows traffic to or from its associated instances. We can modify the rules for a security group at any time; the new rules are automatically applied to all instances that are associated with the security group.
Key pair: A key pair has a public key and a private key. So basically this is a set of security credentials that we use to prove our identity while connecting to an ec2 instance.
Bastion host: The ec2 instance which is present in the public subnet from which we try to connect to an instance present in a private subnet is called a Bastion host.
After analyzing all the theoretical aspects of all the Key terminologies, now let’s get started with the proper analyzation of our problem statement (illustrated above). So first of all to get started with the problem statement we need to follow some steps which are as follow :
Step 1: Create an Aws ec2 instance in a public subnet of any AWS region.
- Select an AWS Ami (Amazon Machine image) like this :
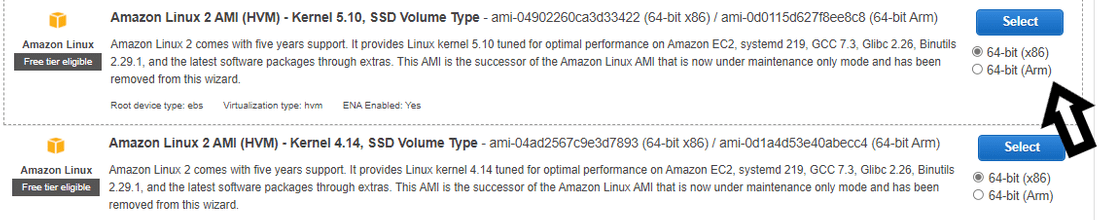
Selecting an Amazon Machine image
- Then select an instance type for your ec2 instance. Instance types are the hardware that we need to launch an AWS ec2 instance like how much memory and number of CPUs you require in your instance.
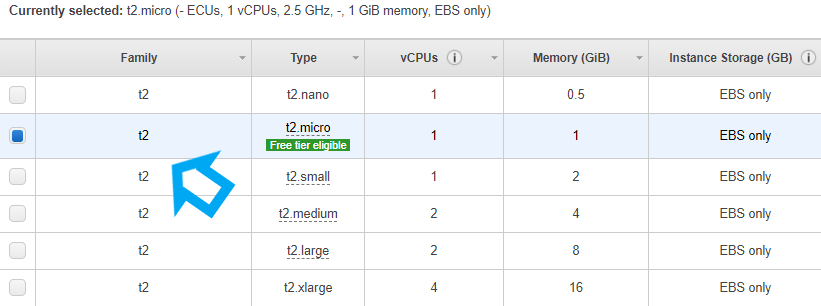
Selecting an AWS ec2 instance type
- Now Configure the instance details and keep all other options as default. Now just select a subnet in any of the availability zones which is nearer to us in order to avoid any chance of latency.
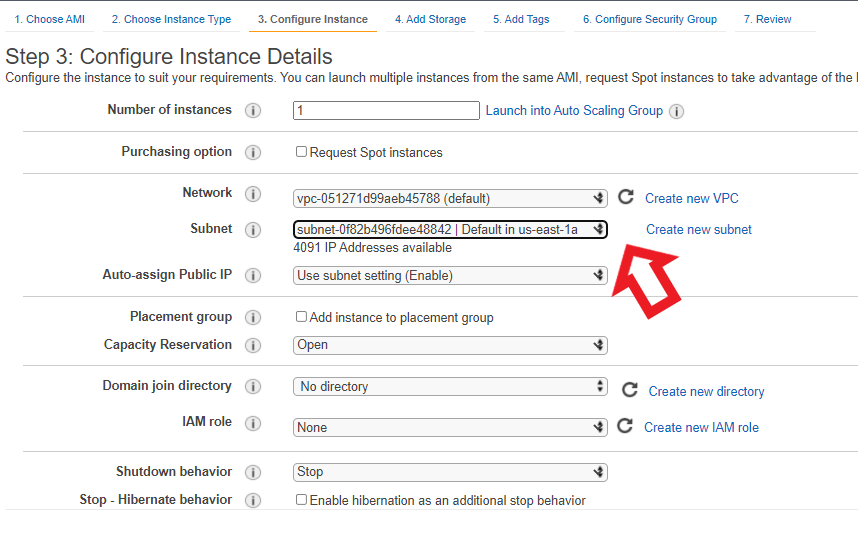
Configuring Instance
- Now we have to add storage to our ec2 instance like this:
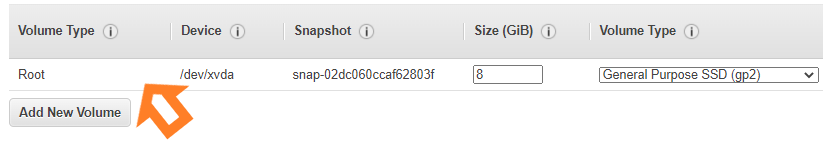
Adding Storage to the instance
Note: We can add more volumes as per your use case to increase the storage of your ec2 instance by clicking on add new volume.
- Now we can add a friendly name to your ec2 instance with the help of tags
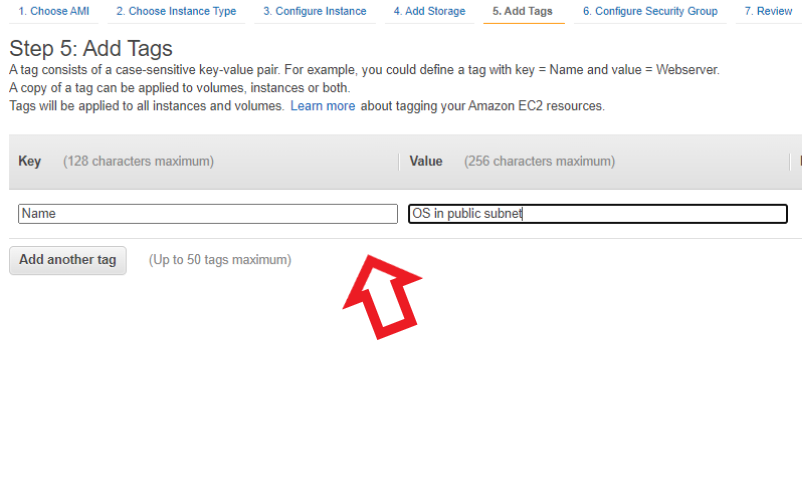
Giving Tags to the instance
- Now we have to configure a security group for our ec2 instance which is a set of rules that control the traffic coming to our instance.
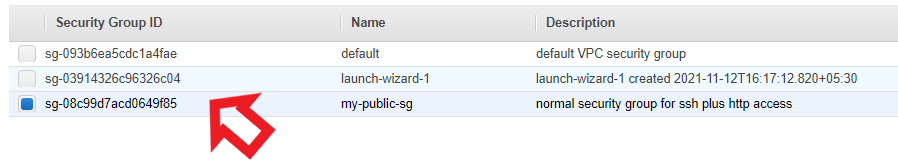
Selecting a Security Group
So here we have selected a security group that allows only traffic which comes using SSH and HTTP protocol. We can create a new security group or use an existing one.
- After this, we may have a final review of our instance. We can check the security group, instance details, storage, and tags of the instance. After making the final review of our instance click on launch. On clicking the launch button it will prompt us for selecting a key pair.
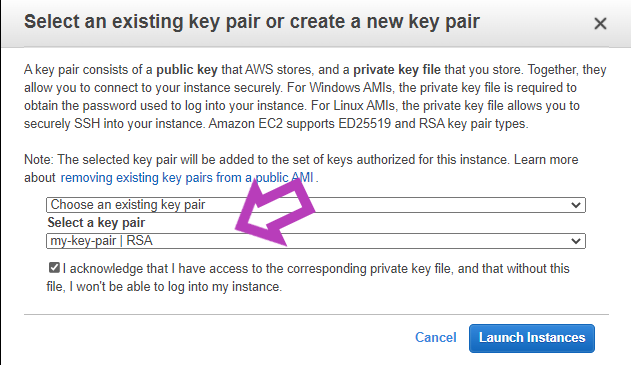
Selecting the key pair
After selecting the key pair we may click on launch instances and ou instance will be launched.
Step 2: Create a private subnet in the same availability zone where we have launched our instance in the public subnet.
- To create a subnet click on the Services and then click on VPC on clicking VPC will open up a VPC dashboard for you there you will find an option of subnets just click on it and here you can create your subnets.
Searching for VPC
- To create a private subnet here I will be using my already created private subnet or you can just create a new private subnet by clicking on Create subnet so the workflow will be like this:

Clicking on Create Subnet button
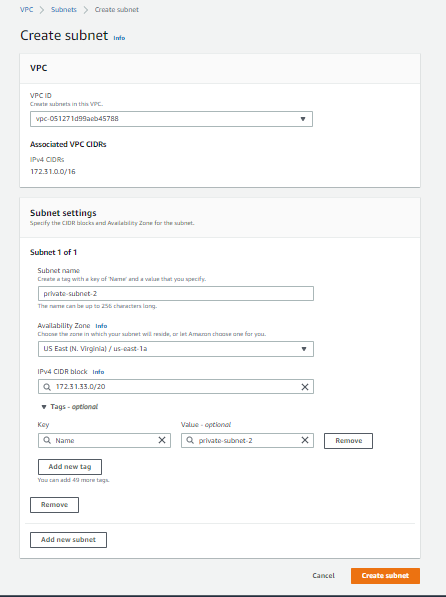
Configuring a private subnet
For configuring a new private subnet the procedure is above in the picture here I will be using my existing private subnet named private subnet
Now launch an ec2 instance the procedure is the same which I have written in step 1 for launching an ec2 instance the difference is only in the subnet you have to select your private subnet, not the default public subnet.
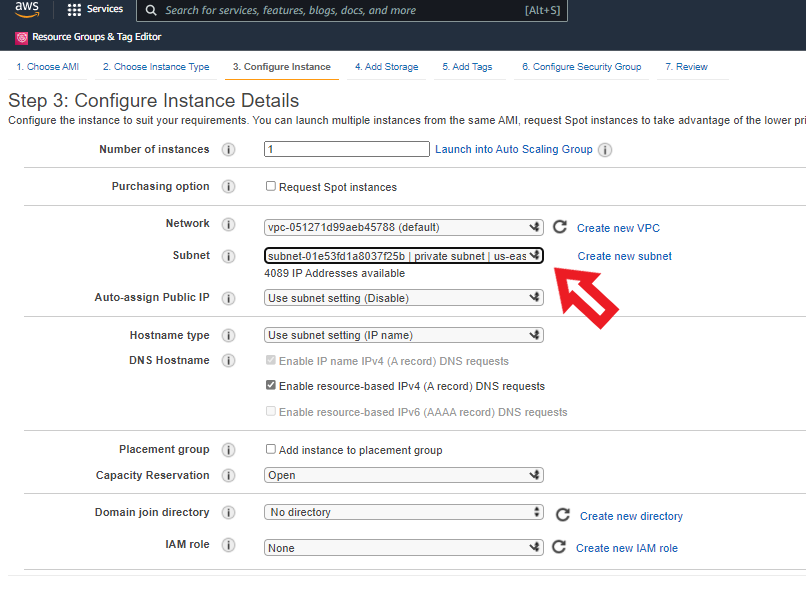
Selecting the private subnet in subnets
Step3: After that, we need to attach a route table to our private subnet which does not allow any IP address from outside for that we need to create a route Table and then associate that route table with the private subnet by just clicking on edit subnet association. Here I have already created the route table and associated it with the private subnet. But let me show you the steps for associating the route table to the subnet.
- Create a route table:
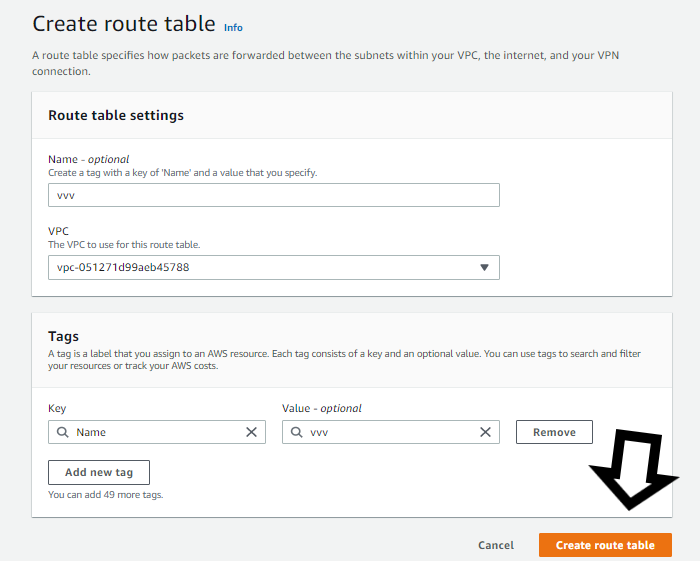
Creating a route table
- Associating the route table with subnet:
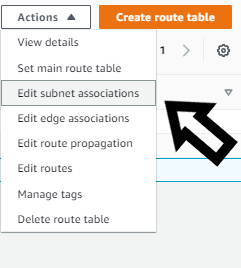
Associating subnet with route table
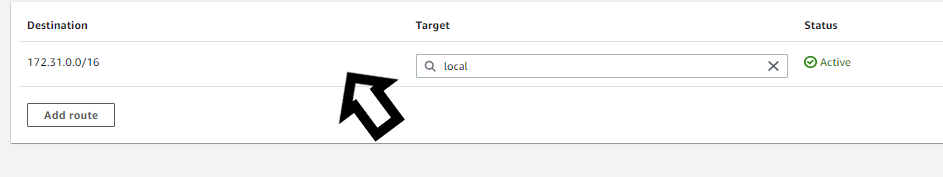
Routes of the private subnet
After that, you need to select your private subnet and then associate that subnet with the Route table so now no one from outside i.e internet can communicate with our instance in a private subnet only instances within the VPC in public and private subnets will have the possibility to communicate with each other.
Step 4: Now we will be using a tool called pageant
- Open pageant and click on view keys then the pageant will be opened and there click the add key to add the key which we used for launching instances.
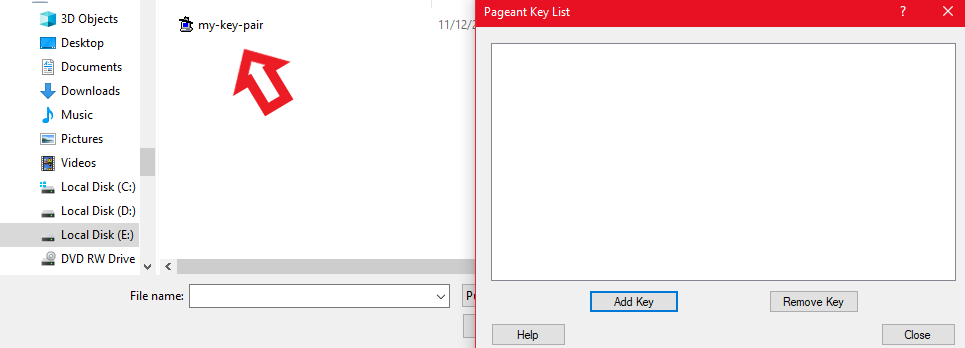
Selecting the key pair to be added
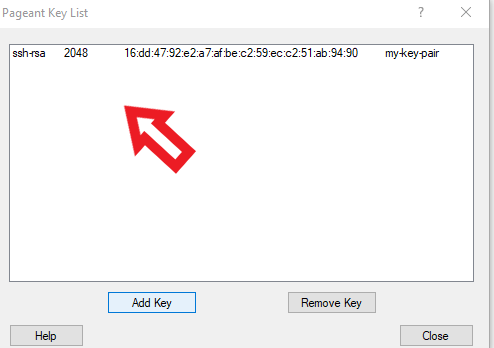
keypair added
Step5: Now we will be using putty to connect instances
Open putty and type in the hostname of your instance in the public subnet and enable agent forwarding on putty.
Format for writing Hostname: username@public_ip_address_of_your_instance also you can just write public IP in the hostname and then connect but then it will ask for your username on login so to avoid that you can use the above format.
For writing hostname click on the Session option present in the putty window and there you will see an option for writing the hostname so just type in your hostname there.
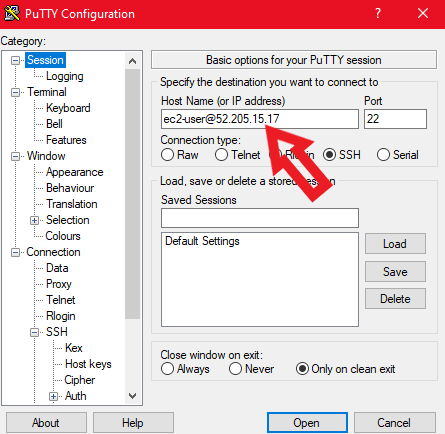
Format of writing hostname
Why do we enable agent forwarding here?
So the advantage of enabling agent forwarding here is it will not ask you for your key to be in authentication to be uploaded in the private key file for authentication as you can see in the picture. As you click the open button it will automatically detect your key pair and will connect to your instance. So, now the purpose of adding a key in the pageant was only that when we enable agent forwarding it will automatically detect my key pair and will connect to my instance.
Step 5: Enabling agent forwarding
- Click on SSH and then click on Auth and tick the option allow agent forwarding:
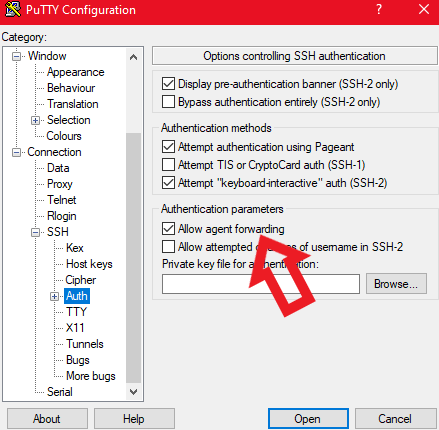
Enabling agent forwarding
Step 6: Connecting an EC2 instance present in the private subnet using a bastion host
Now click on the open button as we have written the hostname and enabled the agent forwarding.
After this, you will be connected to your bastion host.
There use this command ssh user-name@ip_address_of_your_private_instance and you will be connected to your private ec2 instance.
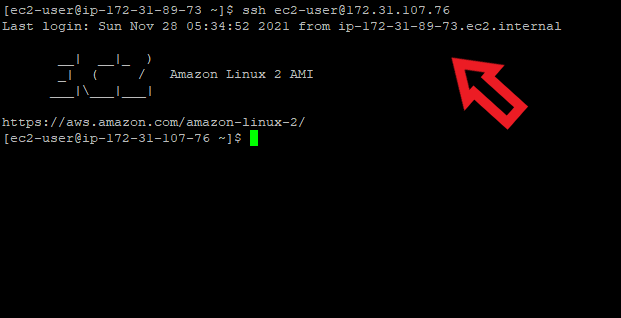
Connected to the private ec2 instance
Subscribe to my newsletter
Read articles from Sushan Shrestha directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Sushan Shrestha
Sushan Shrestha
I'm a DevOps Engineer, Open Source Enthusiast and a Technical Writer. I'm passionate about sharing knowledge, Concise documentations, and making it easy for others to understand technical concepts.