A problem with clustered Redis and a solution
 Rahul Kumar
Rahul Kumar
Two problems are highlighted when using Redis in cluster mode.
Unreliable Partial Data Sync
The two connection issue
The Problem - Unreliable Partial Data Sync
The client requests to write to the master node.
Slave receives a replication command from master.
The master gives the client an OK response.
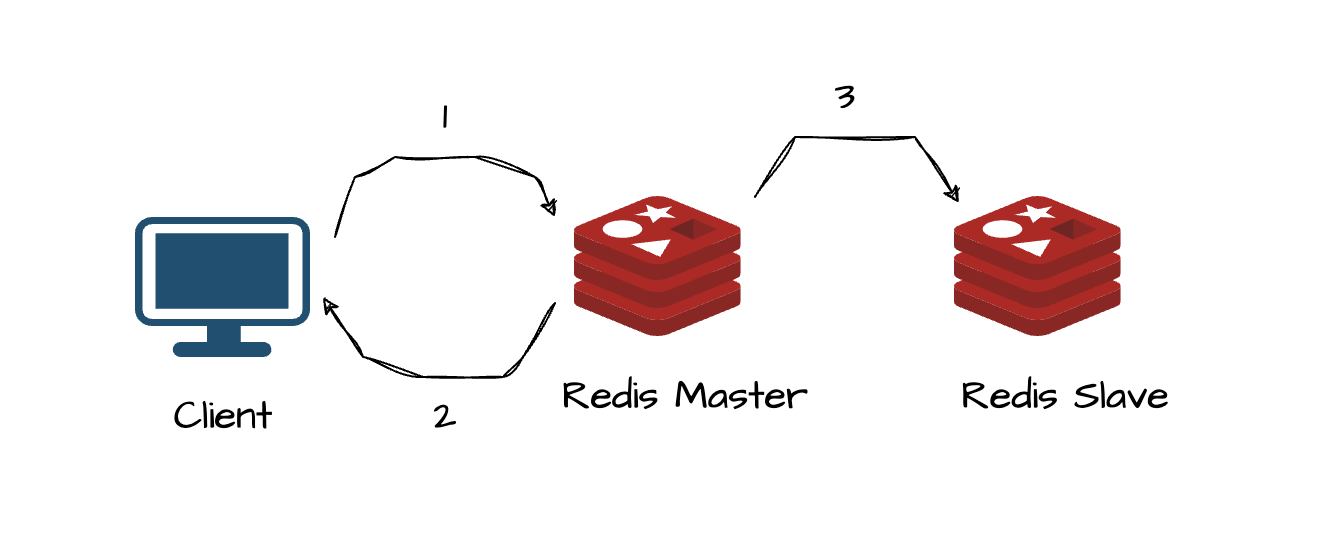
In this case, should the system crash after step 2, the client may believe that the data is secure because it obtained approval from the master prior to the replication instruction being issued.
The Solution: Partial Data Synchronisation
The client sends the master node a write request.
The master instructs the slave to replicate.
The master gives the client a "OK."

In this case, the client is certain that the slave receives a replication command. Since the slave returned to the client with an OK after receiving a replication request from the master, it is assumed that data replication has been successful in this instance.
Although it's not ideal, this works best when taking into consideration the performance, cost of utilising full data synchronisation.
The Problem : Two Connection Issue

The client sends a read request to a node using a key.
The Node doesn’t have the slot that owns the key and replies with MOVED command.
The client sends a read request to the appropriate node using a key.
The value is provided to the client against that key.
The Solution : Client side key-to-node cache

The client checks for the key in the cache. A request goes to a "default" node if the key cannot be found.
The correct node is updated in the cache in the event that a MOVED error is received.
The client calls the correct node.
The value is handed over to the client using that key.
Have Questions or Suggestions ?
Let's connect.
Subscribe to my newsletter
Read articles from Rahul Kumar directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Rahul Kumar
Rahul Kumar
👋 Hey there, I'm a DevOps enthusiast! 🚀 Passionate about architecting highly scalable infrastructures and implementing DevOps practices with unwavering focus on security. 💻✨ 🔧 With a relentless drive to optimize software development processes, I dive deep into designing robust systems that effortlessly handle rapid growth and evolving demands. Leveraging my expertise in DevOps methodologies, I continuously fine-tune deployment strategies, automate workflows, and ensure seamless integration between development and operations teams. 🛡️ Security is always my top priority. I meticulously construct robust security frameworks to safeguard applications, data, and infrastructure, making sure vulnerabilities are sealed and compliance regulations are met. I thrive on staying up-to-date with the latest security practices and industry standards. 💡 My toolkit includes a wide range of cutting-edge DevOps tools such as Docker, Jenkins, Ansible, and more. I excel at orchestrating efficient deployment pipelines, managing large-scale production environments, and monitoring systems for optimal performance. 💬 Want to discuss designing scalable infrastructure, implementing DevOps best practices, or fortifying security measures? Let's connect! Feel free to reach out and let's empower your organization to achieve new heights in software development and operations. 🌟