Docker Scout
 Abid Moon
Abid Moon
Docker CLI
Docker Installation
COPY
# Add Docker's official GPG key:
sudo apt-get update
sudo apt-get install ca-certificates curl gnupg
sudo install -m 0755 -d /etc/apt/keyrings
curl -fsSL https://download.docker.com/linux/ubuntu/gpg | sudo gpg --dearmor -o /etc/apt/keyrings/docker.gpg
sudo chmod a+r /etc/apt/keyrings/docker.gpg
# Add the repository to Apt sources:
echo \
"deb [arch=$(dpkg --print-architecture) signed-by=/etc/apt/keyrings/docker.gpg] https://download.docker.com/linux/ubuntu \
$(. /etc/os-release && echo "$VERSION_CODENAME") stable" | \
sudo tee /etc/apt/sources.list.d/docker.list > /dev/null
sudo apt-get update
Install Docker
COPY
sudo apt-get install docker-ce docker-ce-cli containerd.io docker-buildx-plugin docker-compose-plugin
Note
You must have the Editor or Owner role in the Docker organization to activate image analysis on a repository.
Login to docker
COPY
docker login
There is a 3 GB size limit on images analyzed by Docker Scout in Docker Desktop.
To install Scout plugin on Instance
COPY
curl -fsSL https://raw.githubusercontent.com/docker/scout-cli/main/install.sh -o install-scout.sh
sh install-scout.sh
Note
Always examine scripts downloaded from the internet before running them locally. Before installing, make yourself familiar with potential risks and limitations of the convenience script.

To See Docker scout manual
COPY
docker scout --help

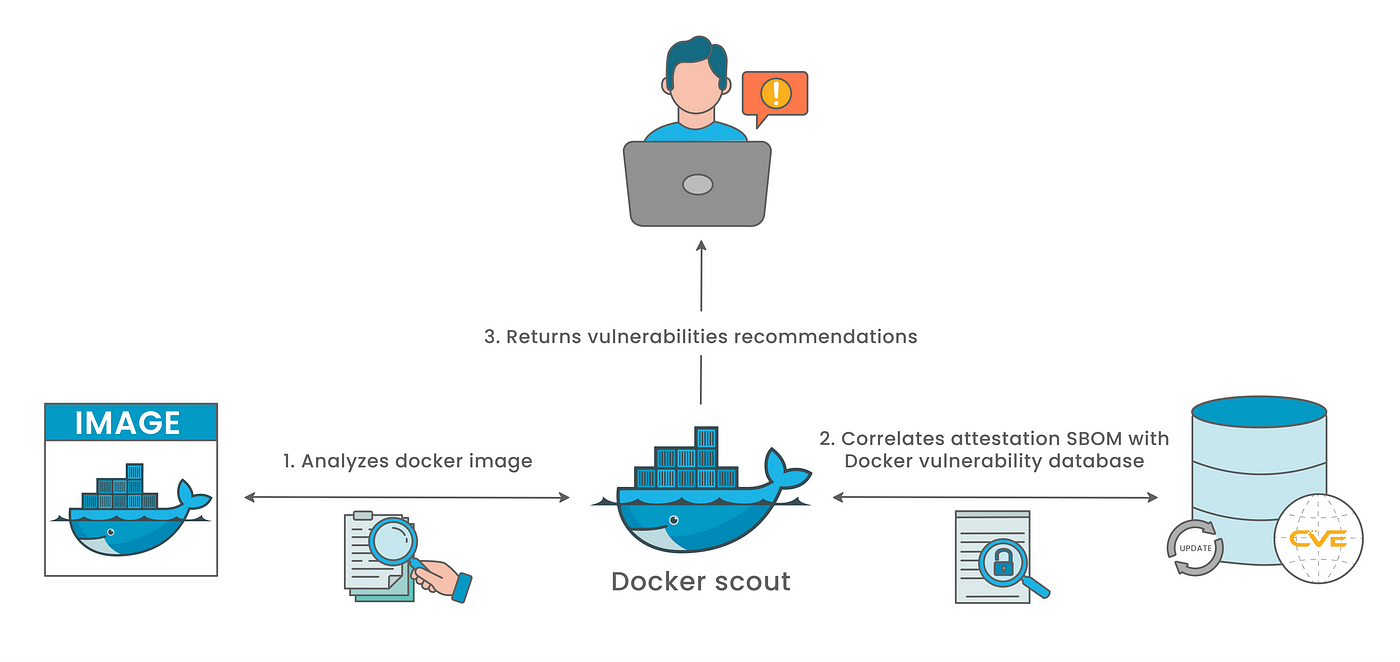
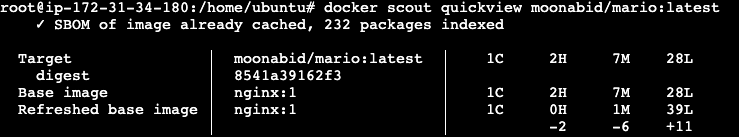
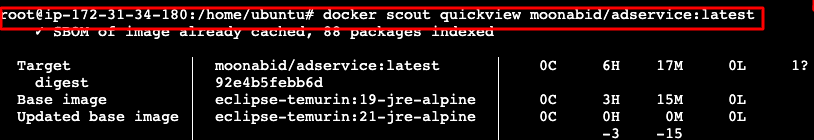
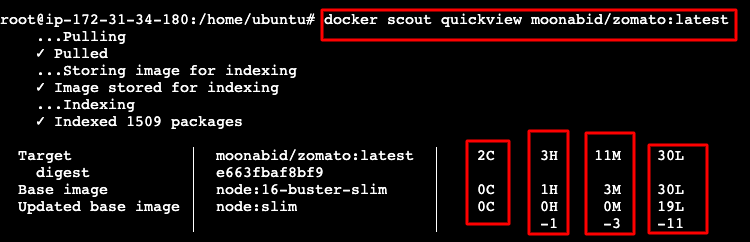
Quickview
The docker scout quickview command provides an overview of the vulnerabilities found in a given image and its base image.
COPY
docker scout quickview <image-name>
COPY
docker scout cves moonabid/zamato:latest
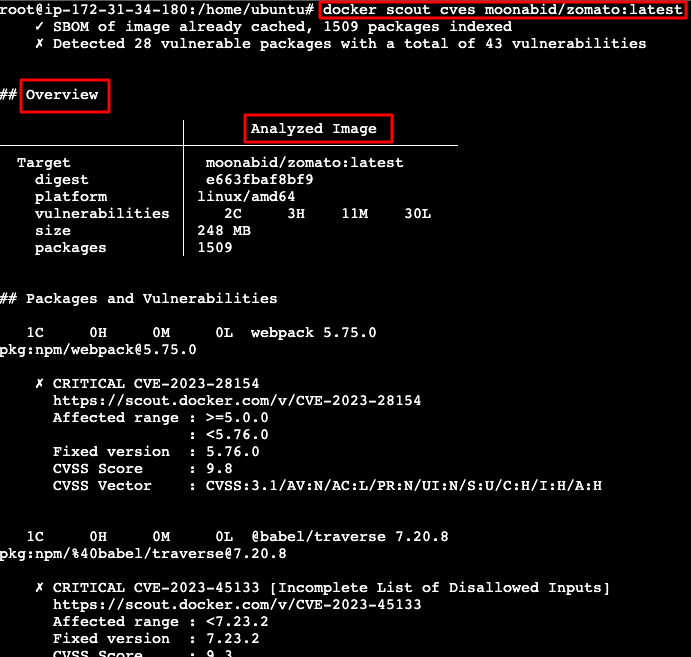
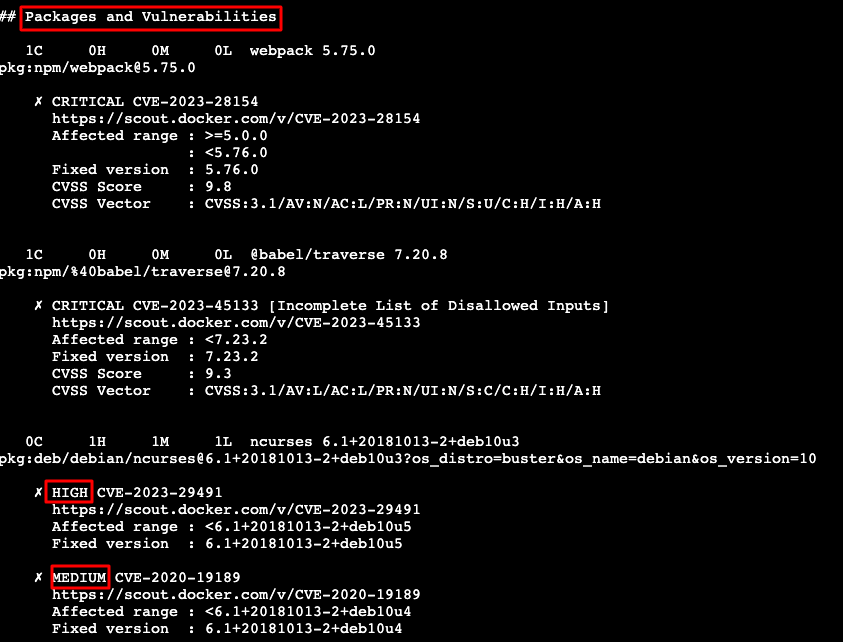
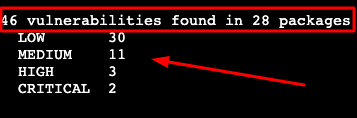
Sample
COPY
docker scout cves --format only-packages --only-vuln-packages \
--only-severity critical moonabid/zamato:latest
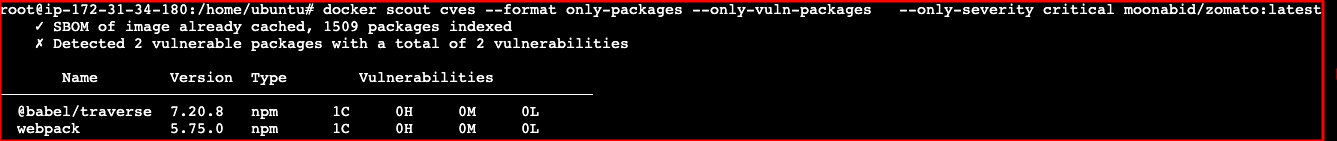
The vulnerabilities in your base image should be aware of and not overlooked. Scout can also help us in this case with the command docker scout reccomendations.
COPY
docker scout recommendations <image-name>
Sample
COPY
docker scout recommendations moonabid/zamato:latest
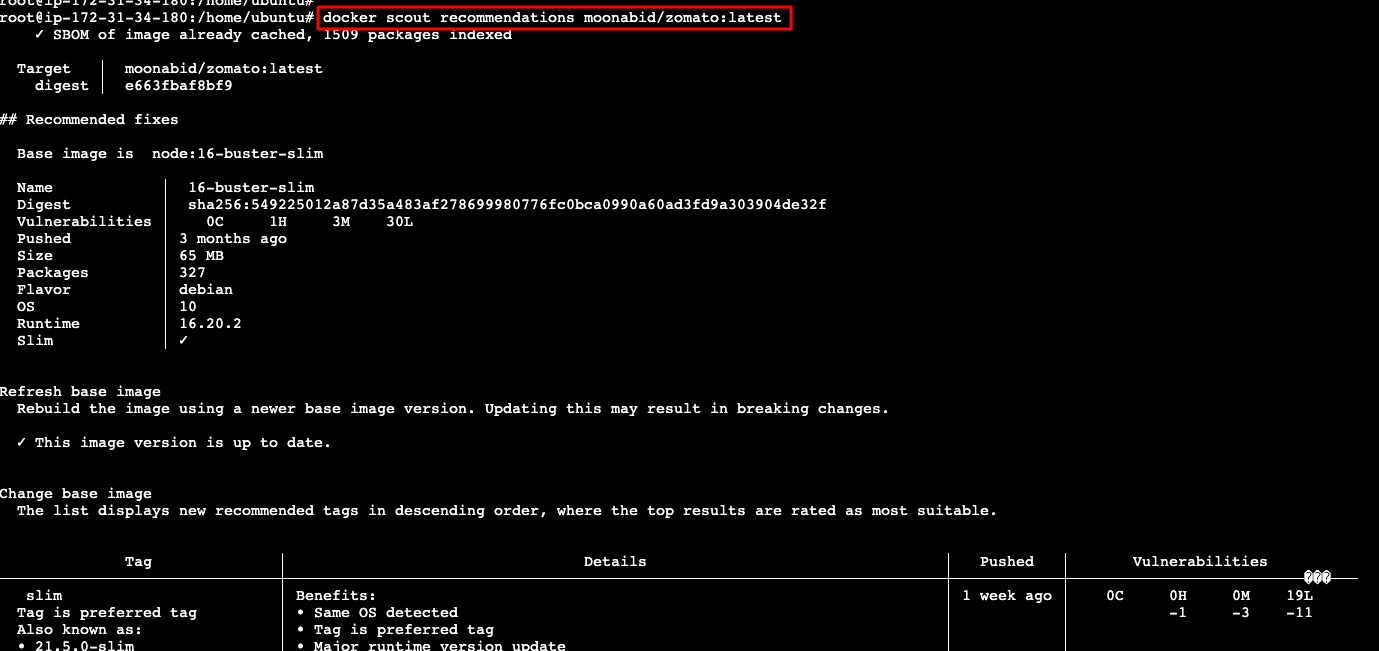
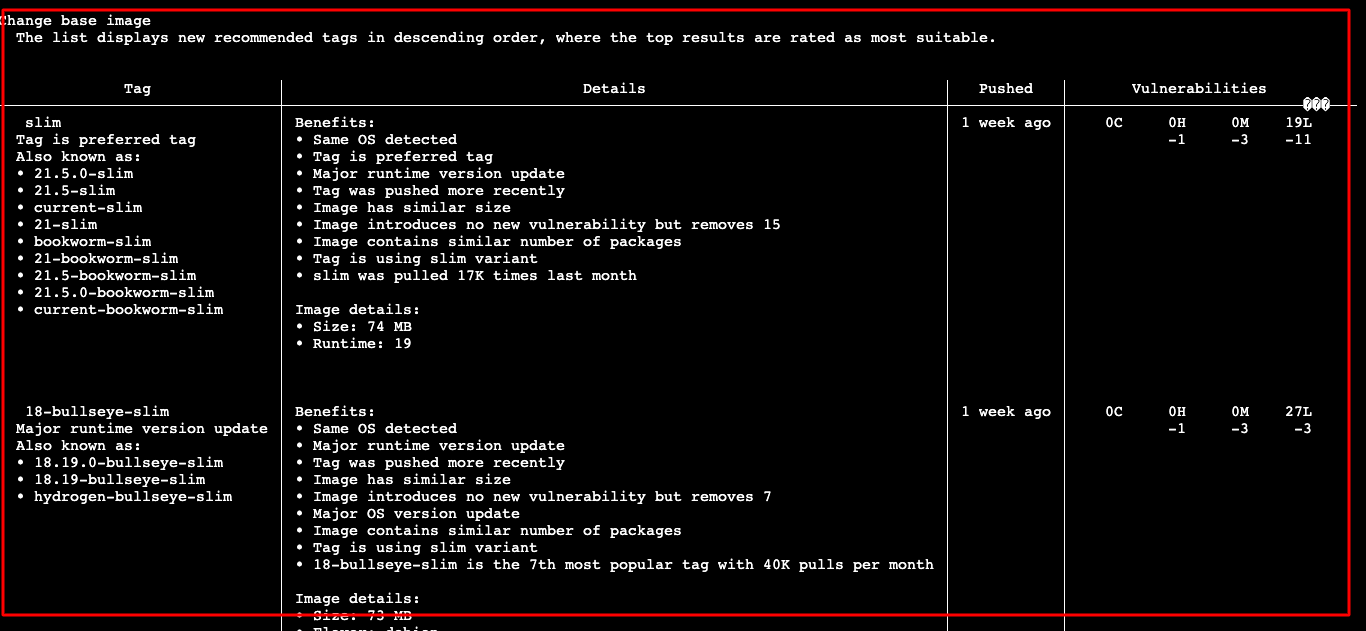
Docker GUI
If you're using Docker Desktop version 4.14 or above, Docker Scout is already installed and readily available.
This is the simplest and most recommended method for most users.
Login to Docker hub
Click On profile beside like in below image
Click on Docker scout

Again go back to Docker scout from hub
You will see image report and analysis like this
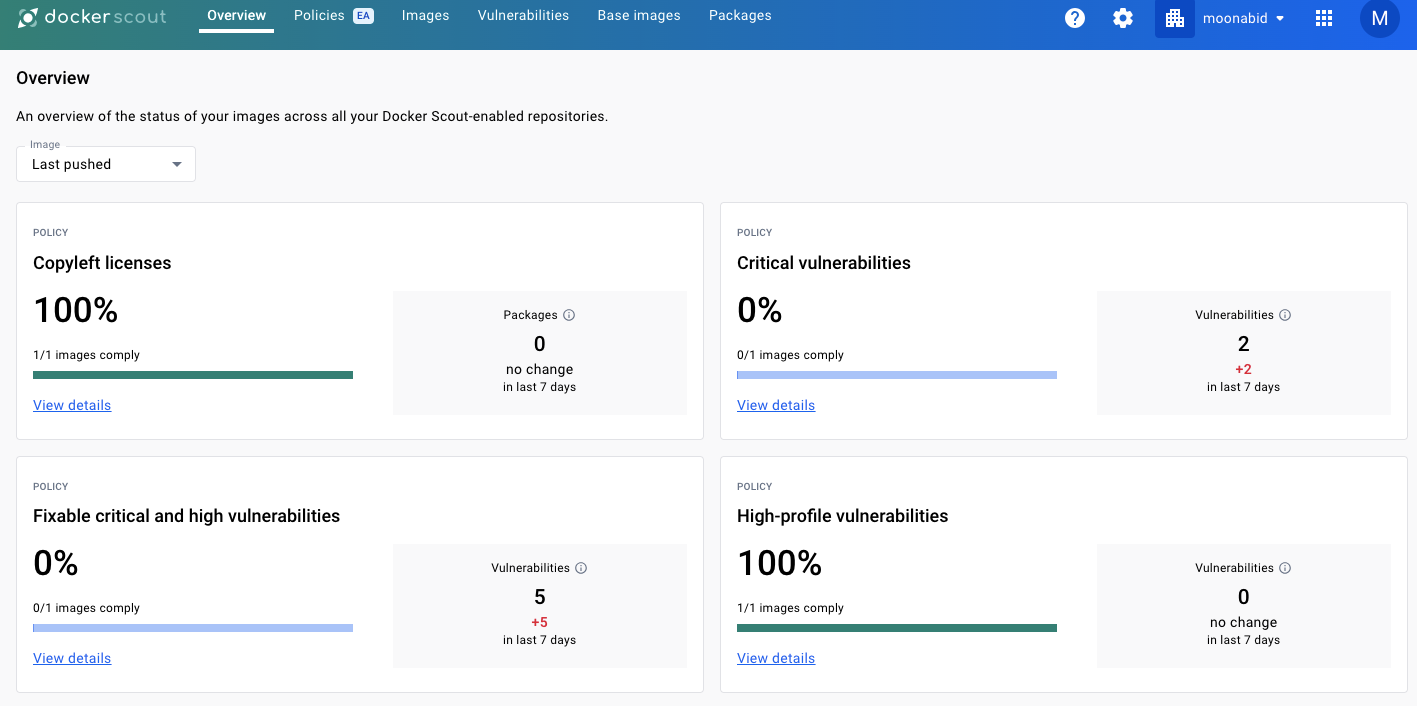
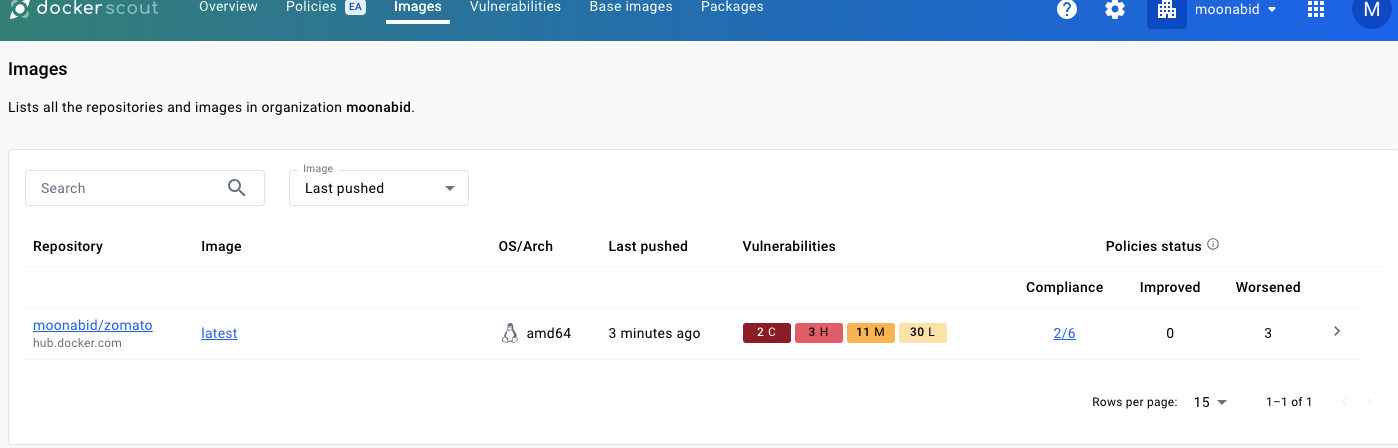
- Done.
Integrating Docker Scout with other systems
By default, Docker Scout integrates with your Docker organization and your Docker Scout-enabled repositories on Docker Hub. You can integrate Docker Scout with additional third-party systems to get access to even more insights, including realtime information about you running workloads.
Integration categories
You'll get different insights depending on where and how you choose to integrate Docker Scout.
Container registries
Integrating Docker Scout with third-party container registries enables Docker Scout to run image analysis on those repositories, so that you can get insights into the composition of those images even if they aren't hosted on Docker Hub.
The following container registry integrations are available:
Continuous Integration
Integrating Docker Scout with Continuous Integration (CI) systems is a great way to get instant, automatic feedback about your security posture in your inner loop. Analysis running in CI also gets the benefit of additional context that's useful for getting even more insights.
The following CI integrations are available:
Environment monitoring
Environment monitoring refers to integrating Docker Scout with your deployments. This can give you information in realtime about your running container workloads.
Integrating with environments lets you compare production workloads to other versions, in your image repositories or in your other environments.
For more information about environment integrations, see Environments.
Code quality
Integrating Docker Scout with code analysis tools enables quality checks directly on source code, helping you keep track of bugs, security issues, test coverage, and more. In addition to image analysis and environment monitoring, code quality gates let you shift left your supply chain management with Docker Scout.
Once you enable a code quality integration, Docker Scout includes the code quality assessments as policy evaluation results for the repositories where you've enabled the integration.
The following code quality integrations are available:
Overview for multiple images
Benefits of using Docker Scout:
Enhanced security: Docker Scout helps you proactively identify and address vulnerabilities in your images, mitigating security risks and preventing potential exploits.
Improved efficiency: By automating vulnerability scanning, Docker Scout saves you time and effort compared to manual processes.
Greater transparency: Gain detailed information about the dependencies within your images, allowing for better understanding and control.
Seamless integration: Docker Scout integrates seamlessly with Docker Desktop, making it readily accessible and easy to use.
Understanding the reports:
After scanning, Docker Scout generates a detailed report that includes:
Vulnerability details: Information about identified vulnerabilities, such as their severity, CVSS score, affected packages, and historical references.
Dependency list: A breakdown of all libraries and packages used within the image, including their versions and historical dependencies.
Actionable recommendations: Guidance on how to address vulnerabilities and improve your image security, including historical patches and mitigation strategies.
Advanced features:
Docker Scout also offers several advanced features, including:
Policy creation: Define custom rules and checks to ensure your image adheres to specific security standards and historical guidelines.
Integration with CI/CD pipelines: Automate vulnerability scanning within your development workflow for continuous monitoring.
Vulnerability prioritization: Focus on addressing the most critical vulnerabilities first based on historical risk assessments.
Subscribe to my newsletter
Read articles from Abid Moon directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Abid Moon
Abid Moon
I’m a DevOps Engineer & digital marketer who grows brands and website traffic using content, search and social media marketing. 👍