Lab: 2FA simple bypass
 Ohekpeje Joel Odey
Ohekpeje Joel Odey
Introduction: Two-factor authentication (2FA) is a widely adopted security measure, but like any system, it may have vulnerabilities. In this article, we'll explore a lab that demonstrates a simple 2FA bypass scenario. By understanding this process, we can enhance our knowledge of potential security weaknesses.
Lab Overview: 2FA Simple Bypass
Step 1: Login to Your Own Account Begin by logging into your own account on the target platform. The 2FA verification code will be sent to your registered email address. Click the "Email client" button to access your emails.
Step 2: Note the Account Page URL After logging in, navigate to your account page and make a note of the URL. This step is crucial for later stages of the bypass.
Step 3: Log Out of your account to simulate a scenario where an attacker gains unauthorized access to a victim's credentials.
Step 4: Login Using Victim's Credentials Attempt to log in using the victim's credentials. As expected, you will be prompted for the 2FA verification code.
Step 5: Manually Change the URL When prompted for the verification code, manually alter the URL to navigate to /my-account. This change in the URL is a key part of the bypass. The lab is considered solved when the /my-account page successfully loads.
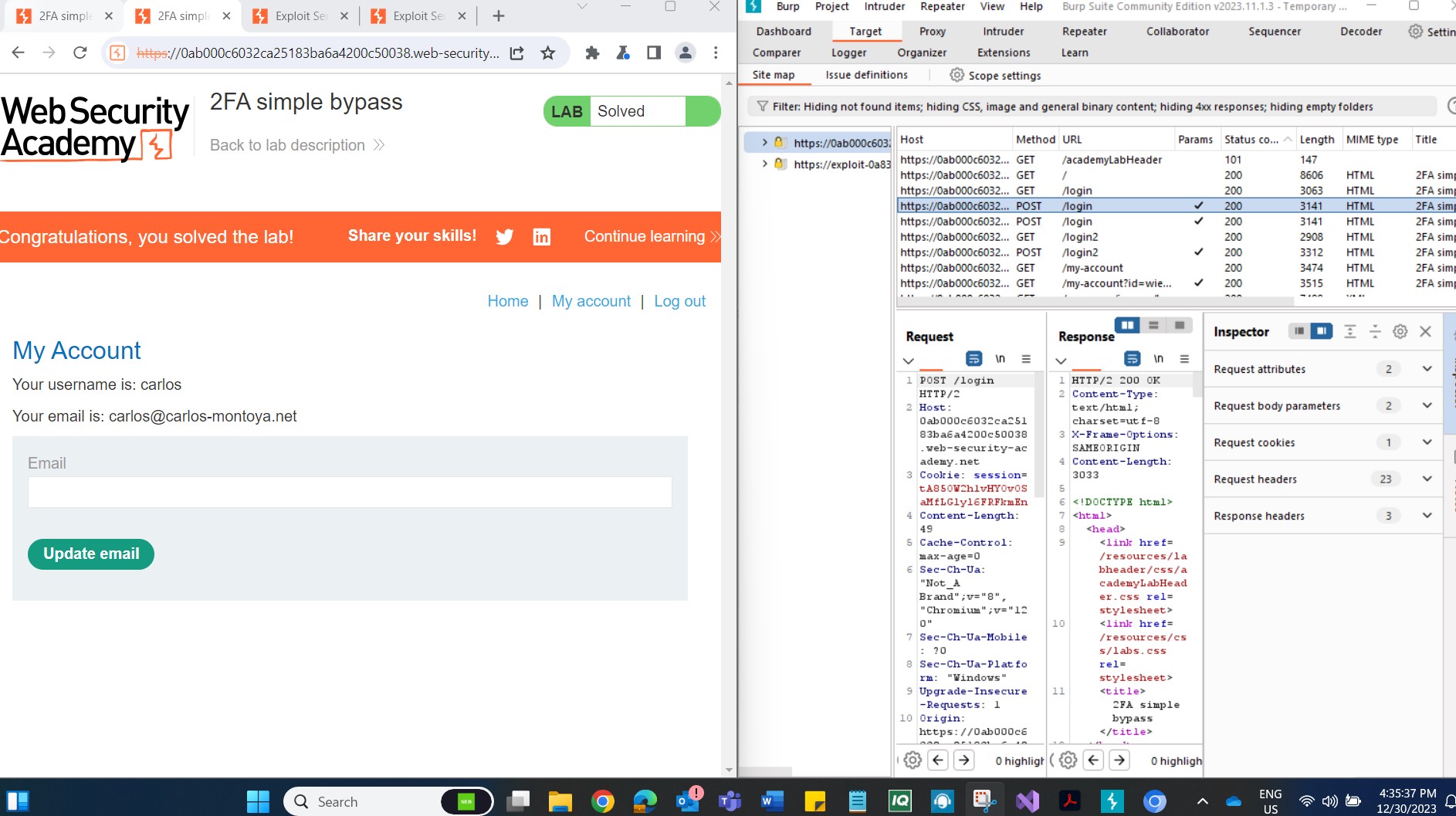
Conclusion: This lab exercise provides insight into a simple 2FA bypass scenario, emphasizing the importance of secure implementation and awareness. It's essential to recognize that security measures, including 2FA, are not foolproof, and understanding potential weaknesses is vital for robust defense strategies.
By following this step-by-step guide, users gain hands-on experience in identifying and exploiting a 2FA vulnerability. However, it's crucial to approach such exercises responsibly and within ethical bounds. Security professionals can leverage this knowledge to fortify systems and educate others about the importance of implementing and continuously improving security measures.
Reference:
Lab: 2FA simple bypass | Web Security Academy (portswigger.net)
Subscribe to my newsletter
Read articles from Ohekpeje Joel Odey directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Ohekpeje Joel Odey
Ohekpeje Joel Odey
Cybersecurity professional sharing insights on securing ecosystems, exploring cloud tech, and simplifying concepts for pros, enthusiasts, and beginners alike.