🔑Identity and Access Management (IAM) in AWS (Basics Concepts)🔑
 Vyankateshwar Taikar
Vyankateshwar Taikar
📌Introduction to IAM 🔑
Identity and Access Management (IAM) is an Amazon Web Services (AWS) service that allows you to securely manage access to AWS services and resources.
This allows you to control who can do what (rights) and what resources they have access to. Cloud security is one of the biggest obstacles to cloud adoption. In accordance to security best practices is important to ensure a smooth transition with a solid foundation for your SecOps and SysOps teams.
IAM gives you control over who has access to your resources (authentication) and how (permission). This is the reason why AWS may be used to create incredibly secure settings.

In AWS , IAM helps you configure and manage user identities, groups, and roles.
We cover key features, the latest updates, and how to set up basic and important features like MFA and other best practices.
Let's begin! 🚀
📌IAM Features
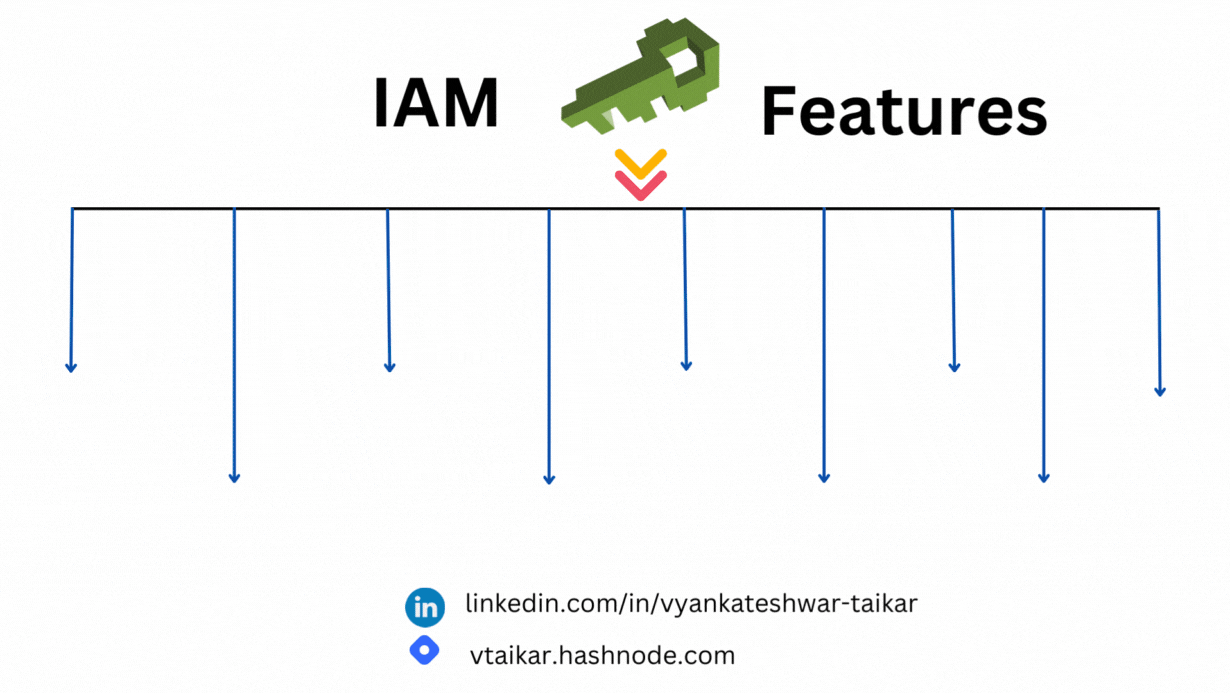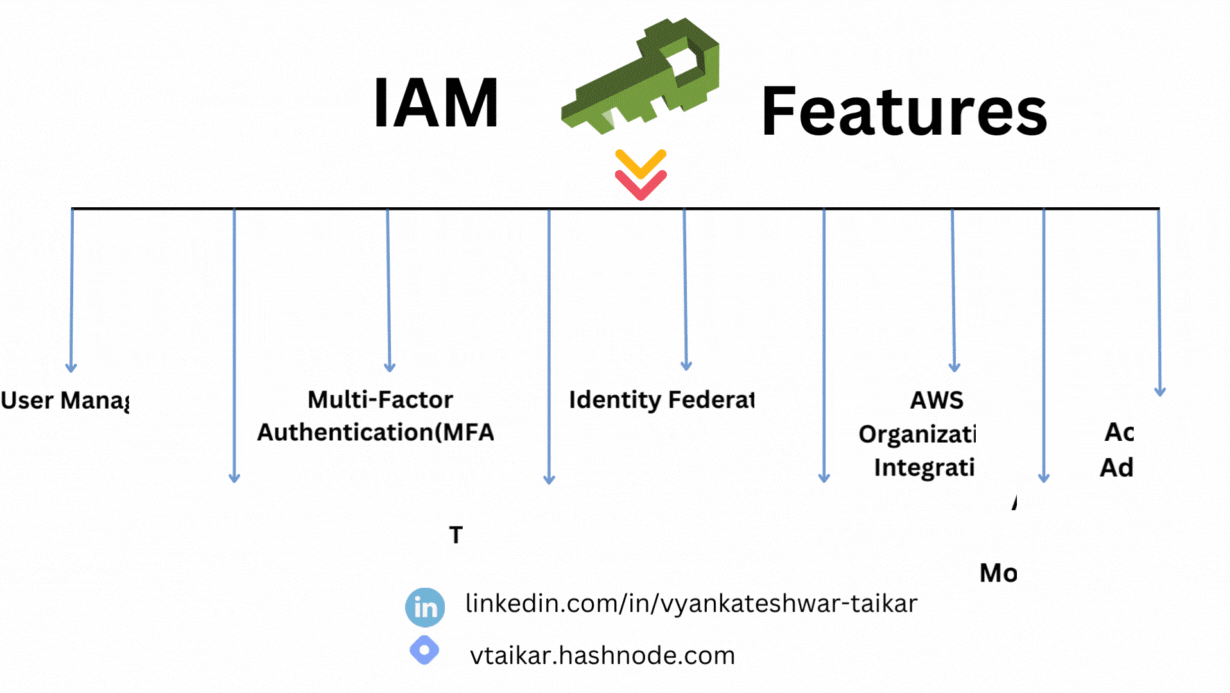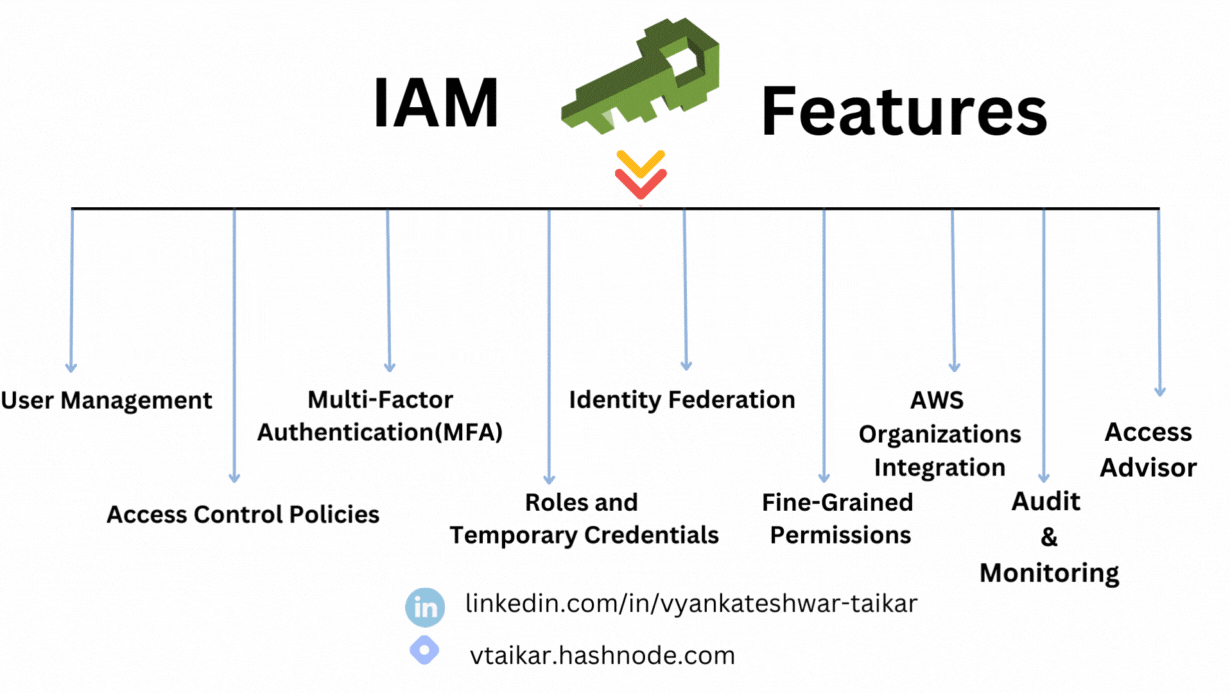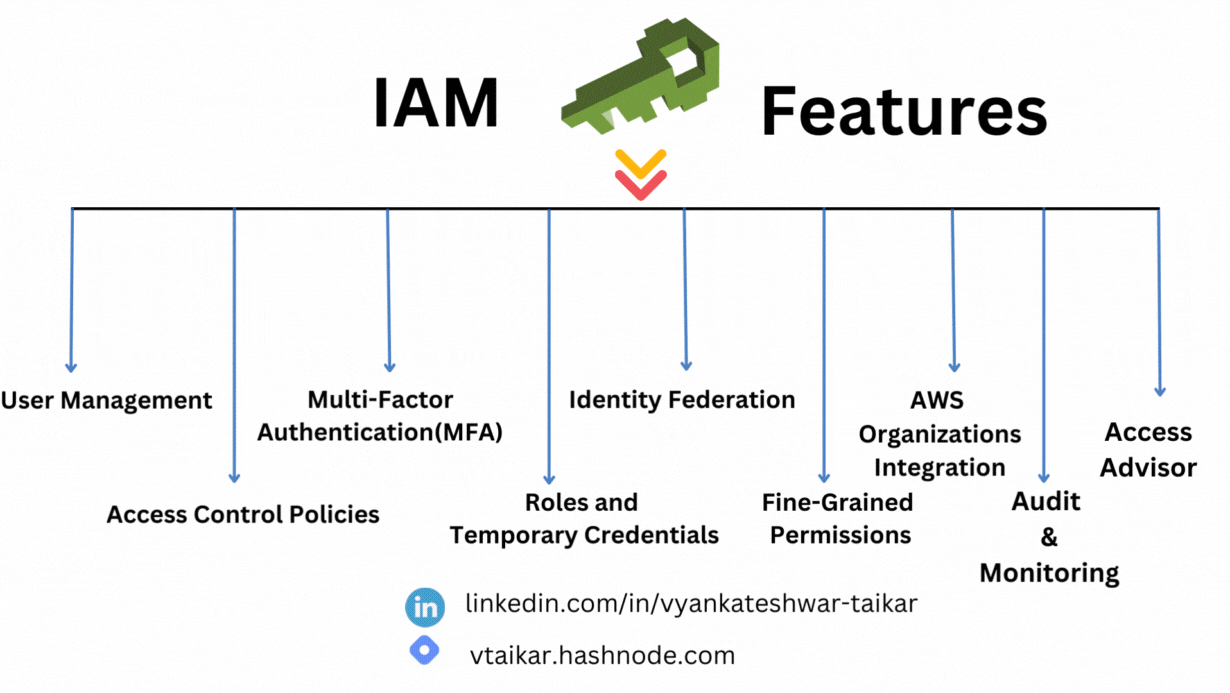
User Management : Establish and manage AWS groups and users. Permissions can also be set to allow or restrict access to specific AWS resources.
Access Control Policies : Policies for Access Control Utilize policies based on JSON to define permissions. You can use IAM to build policies that limit what can be done by resources and users.
Multi-Factor Authentication : Enable multi-factor authentication (MFA) for IAM users to improve account security. Users must now supply additional information in addition to their passwords.
Roles and Temporary Credentials : Assume roles that have been assigned certain permissions when needed. For temporary access, IAM also facilitates the use of temporary security credentials.
Identity Federation : By utilizing federation to integrate IAM with your current identity system, you may enable users to log in with their current company credentials.
Fine-Grained Permissions : Limit the amount of privileges that individuals and organizations have access to by only granting them what they need. For more precise control, resource-level permissions are supported by IAM.
AWS Organizations Integration : Integration of Amazon Organizations To handle access control for several AWS accounts centrally, integrate IAM with AWS Organizations.
Audit and Monitoring : For auditing purposes, log every IAM operation using AWS CloudTrail. AWS CloudWatch and IAM are also integrated so that IAM events may be monitored and alerted accordingly.
Access Advisor : Use Access Advisor to learn more about service permissions. It shows the services that IAM entities can access as well as the last time they did so.
👉Concepts of Users , Groups , Roles,Policy& Permisson
Users: An individual who must use the AWS Console or the AWS CLI to engage with your AWS resources or services is an IAM user. No credentials are given when you create a new user, and they are not authorized to utilize any of your AWS resources.
Groups: An IAM group consists of a set of users and the rights that have been granted to them. Groups define users based on department, job function, or any other requirement, making it easy to manage permissions for people with comparable needs. The group then allows for the parallel management of those users permissions.
Roles: An IAM role is an entity in AWS that specifies the type of entities that can fill a specific role and the permissions it can execute. A role can be assumed by any resource that the role authorizes; it is not correlated with any specific individual or service. Role credentials are never permanent; they are changed regularly by the AWS Session Token Service (STS). Roles are thus preferred over explicitly giving user or group permissions because of this. In addition, Roles let you provide users, services, and apps outside of your company multi-account access to your AWS resources.Most system administrators are aware of the principles of users and groups, but they may not be as familiar with IAM Roles. Below, let's explore this in greater detail.
Consider one scenario :
One of your organization's administrators may have unintentionally issued a command to remove a production resource. This command would run in a system where users and groups are the only entities with permission control. However, this command would only succeed in a role-controlled system if the administrator has just been assigned the DeleteProductionResources role, or a role similar to it. This reduces the possibility of compromised credentials and systems while allowing services and users to perform all of the necessary operations.
👉Policy: what is it?
A policy is a written declaration that contains one or more rules. Every policy can be linked to any of the IAM identities we discussed previously, including users, groups, and roles, and it grants a certain set of rights. Every policy has a name and is written in either YAML or JSON format.
There are two categories of policies that you ought to be aware of:
Managed policies: It is possible to develop and affix managed policies to several entities. There are numerous use cases covered by the integrated managed policies in AWS. Additionally, managed rules can be combined and matched to grant roles, users, or groups general access. Customers of AWS are also able to design their own managed policies.
Inline policies : Policies that are applied directly to IAM entities are known as inline policies; they require unique ARNs. Inline policies are not reusable because you use them for a single purpose.
For more consistent and reusable permissions, AWS advises using managed policies rather than inline policies.
👉Concept of Permissions
You can work with AWS resources and take actions because of permissions. Upon creation, a new user or group lacks rights and requires the attachment of a policy to authorize actions on AWS resources.
Permissions can be granted to all AWS identities, including roles,groups, and users.
Two methods are used to assign permissions:
Identity-based: Policies directly linked to individuals, teams, or positions.
Resource-based: Policies linked to AWS resources, like ECR repositories and S3 buckets, among others.
The following resources can be useful for creating new policies:
Manage IAM Permissions: You can assign and manage IAM permissions with the help of this website, which provides rapid reference.
Resources, Actions, and Condition Keys: An exhaustive list of all the things that can be done with different
AWS services Policy Simulator on AWS: Confirm that recently established policies function seamlessly by generating access simulations.
Policies should generally adhere to the least privilege principle, which states that only the bare minimum of access should be allowed in order to complete the task at hand. Policies can be very detailed. Take a look at the code block below, for instance:
{
"Version": "2024-01-02",
"Statement": [
{
"Action": [
"iam:ChangePassword",
"iam:CreateLoginProfile",
"iam:DeleteLoginProfile",
"iam:GetLoginProfile",
"iam:GetUser",
"iam:UpdateLoginProfile"
],
"Resource": "arn:aws:iam::*:user\/${aws:username}",
"Effect": "Allow",
"Sid": "AllowManageOwnPasswords"
}
]
}
Alternatively, policies may be more generally defined, as in the code block that follows:
{
"Version": "2024-01-02",
"Statement": [
{
"Action": [
"iam:*"
],
"Resource": "*",
"Effect": "Allow",
"Sid": "IAMAdmin"
}
]
}
To finding the correct balance is important because overly broad policies can result in unauthorized entry, which is a significant contributing reason to security breaches, and excessively granular regulations provide unneeded detail. Ensuring that unanticipated security incidents cause no damage as possible can be done by keeping to the principle of least privilege.
✨More Learn From AWS Documentation 👉 Click Here
Below Diagram will give more clarity about the above concepts 👇
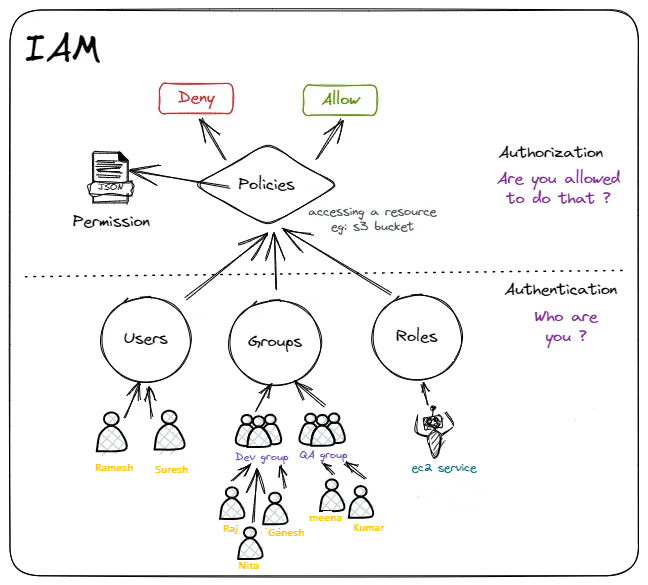
I hope you enjoy the blog post!
If you do, please show your support by giving it a like ❤, leaving a comment 💬, and spreading the word 📢 to your friends and colleagues 😊
Subscribe to my newsletter
Read articles from Vyankateshwar Taikar directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Vyankateshwar Taikar
Vyankateshwar Taikar
Hi i am Vyankateshwar , I have a strong history of spearheading transformative projects that have a direct impact on an organization's bottom line as a DevOps Engineer with AWS DevOps tools implementations.