Create IAM User and Policy in AWS
 Abdul Hakim
Abdul HakimTable of contents
- Overview
- Prerequisites
- Steps
- Step 1 - Create a user
- Step 2 - Create a bucket
- Step 3 - Create objects named "images" and "web" in the bucket
- Step 4 - Test Amazon S3 access
- Step 5 - Create a policy
- Step 6 - Grant the "aha-staff" user permission to view only the "aha-company/images" object
- Step 7 - Test Amazon S3 access
- Step 8 - Delete the Amazon S3 bucket
- Step 9 - Delete the user
- References

Overview
An IAM user in AWS (Amazon Web Services) is an entity that represents an individual or application that interacts with AWS services. IAM (Identity and Access Management) users are used to grant specific permissions for accessing AWS resources and services. Here's an overview of how IAM users work:
Creating IAM Users:
IAM users are created within an AWS account.
Users can be created using the AWS Management Console, AWS CLI (Command Line Interface), or AWS SDKs (Software Development Kits).
Assigning IAM Policies:
Permissions for IAM users are defined using IAM policies. These policies are JSON documents that specify what actions a user is allowed or denied to perform on AWS resources.
Policies can be attached to IAM users directly or assigned through IAM groups.
IAM Groups:
IAM users can be organized into groups based on common roles or responsibilities.
Groups allow you to manage permissions for multiple users collectively. Permissions assigned to a group are inherited by all users in that group.
Access Keys:
IAM users can be assigned access keys (access key ID and secret access key) for programmatic access to AWS services through the AWS CLI, SDKs, or other tools.
Access keys are not required for IAM users accessing the AWS Management Console.
IAM Roles:
IAM roles define a set of permissions for making AWS service requests. Roles are not associated with a specific user or group but are assumed by entities such as IAM users, AWS services, or identity federation.
IAM roles are often used for cross-account access and temporary permissions.
Authentication and Authorization:
IAM users can authenticate themselves to AWS using a username and password for console access or using access keys for programmatic access.
Once authenticated, AWS checks the permissions associated with the user or the roles assumed by the user to determine if the requested action is allowed (authorization).
MFA (Multi-Factor Authentication):
- IAM users can enable MFA to add an extra layer of security. MFA requires users to provide a second form of verification, such as a time-based one-time password (TOTP) from a hardware token or a virtual MFA device.
IAM users play a crucial role in managing access to AWS resources securely. By assigning granular permissions through IAM policies, organizations can ensure that users have the appropriate level of access without compromising security.
In this article, we will create an IAM user and then grant permission to the Amazon S3 resource. The steps to be taken are as follows:
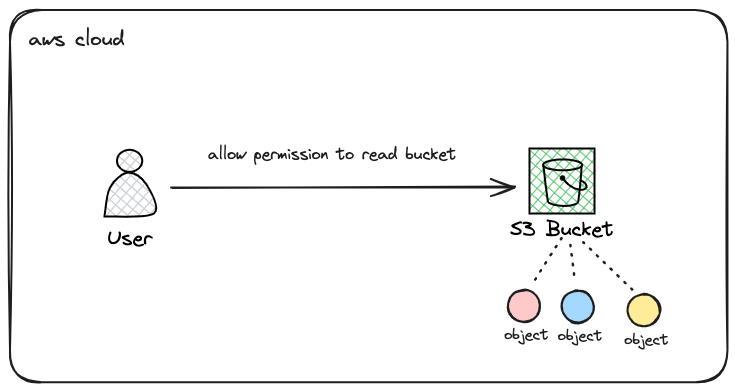
Create a user named "aha-staff"
Create a bucket named "aha-company"
Create objects named "images" and "web" in the bucket
Test Amazon S3 access
Create a policy
Grant the "aha-staff" user permission to view only the "aha-company/images" object
Test Amazon S3 access
Delete the Amazon S3 bucket
Delete the user
Prerequisites
- Akun AWS
Steps
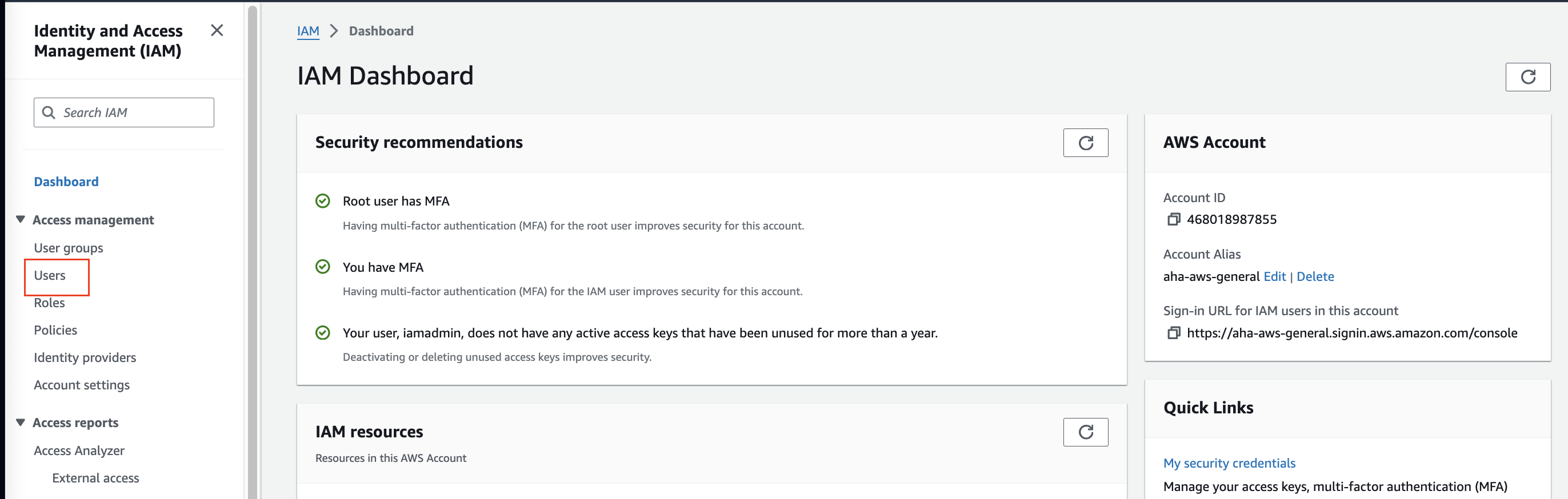
Step 1 - Create a user
Access the IAM console in your AWS account.
Navigate to the "Users" section and click on "Add user."
Click "Next: Permissions."
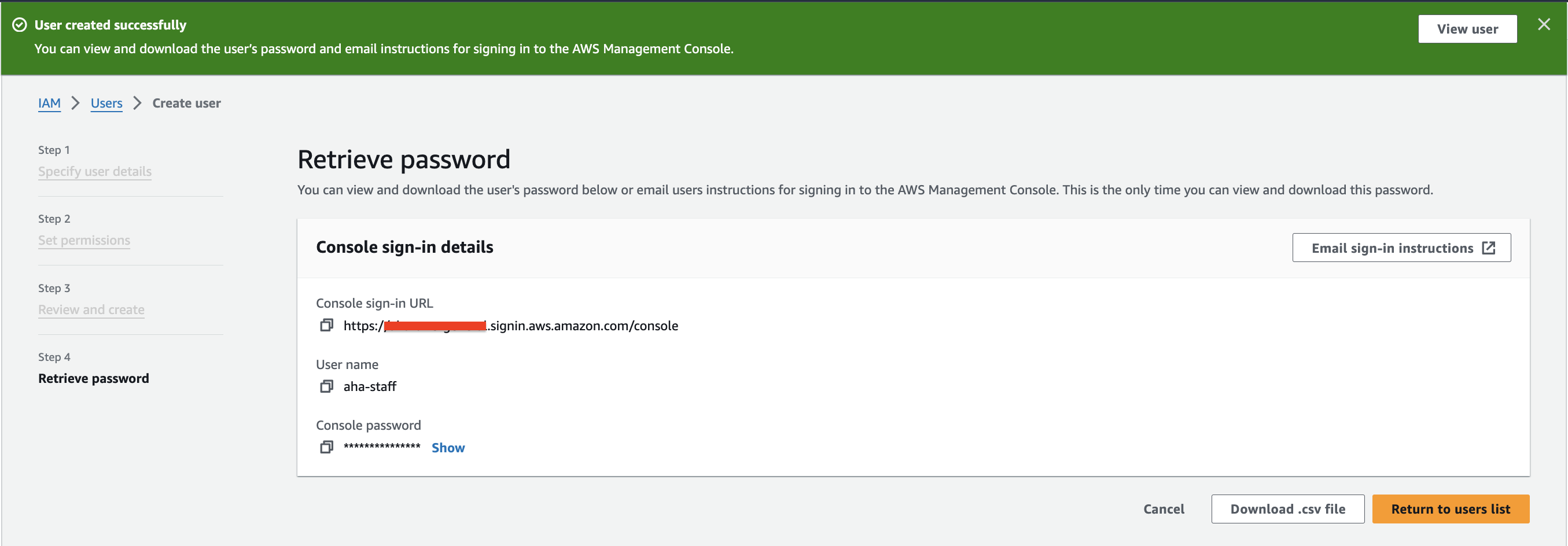
Click "Next: Review" to confirm the details and then click "Create user."
Securely store the generated access key ID and secret access key, as they'll be needed for authentication.
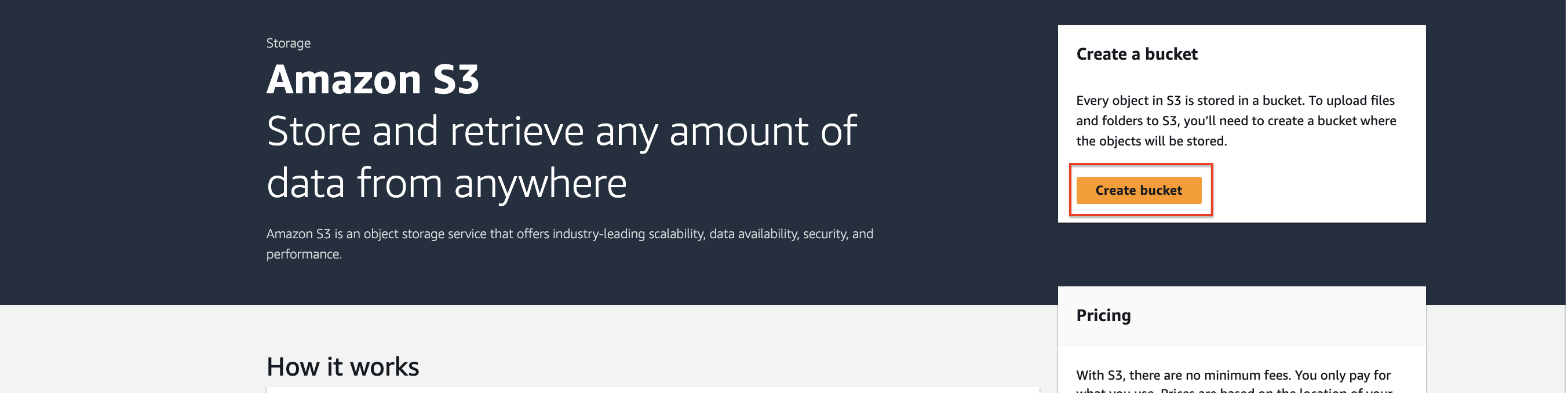
Step 2 - Create a bucket
Access the S3 console.
Click on "Create bucket."
Enter the bucket name "aha-company" and select the desired region.
Choose appropriate settings for versioning, encryption, and other options as needed.
Click "Create bucket."
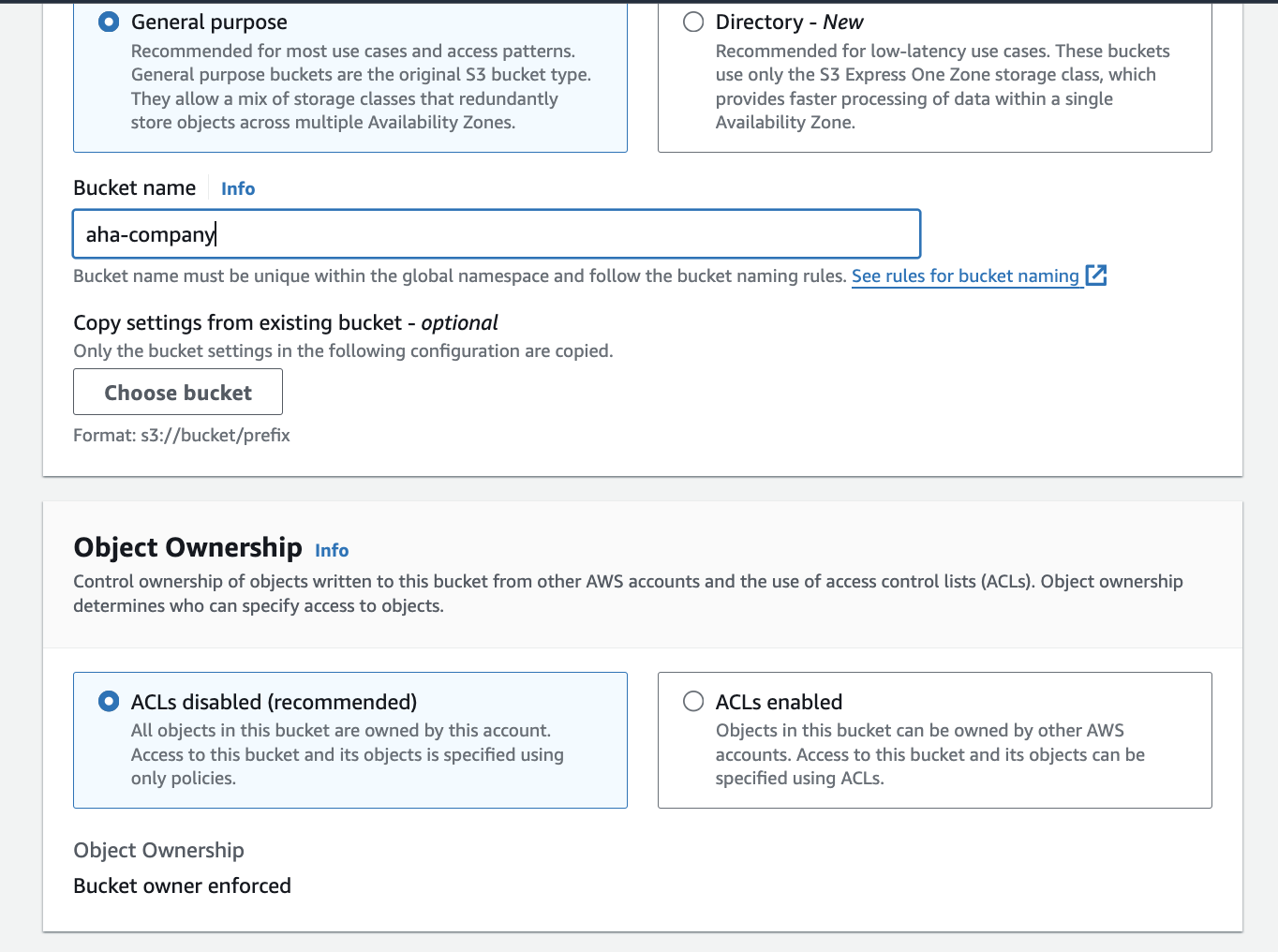
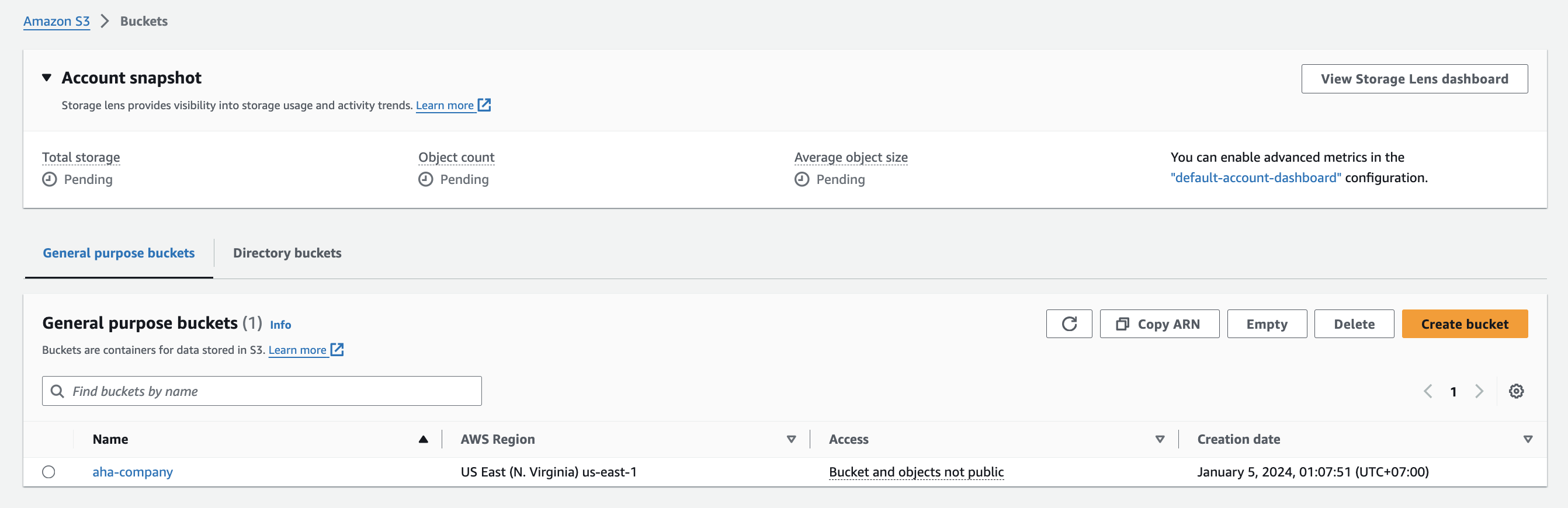
Create folders:
Click on "Create folder."
Enter the folder name web, images
Click "Create folder."
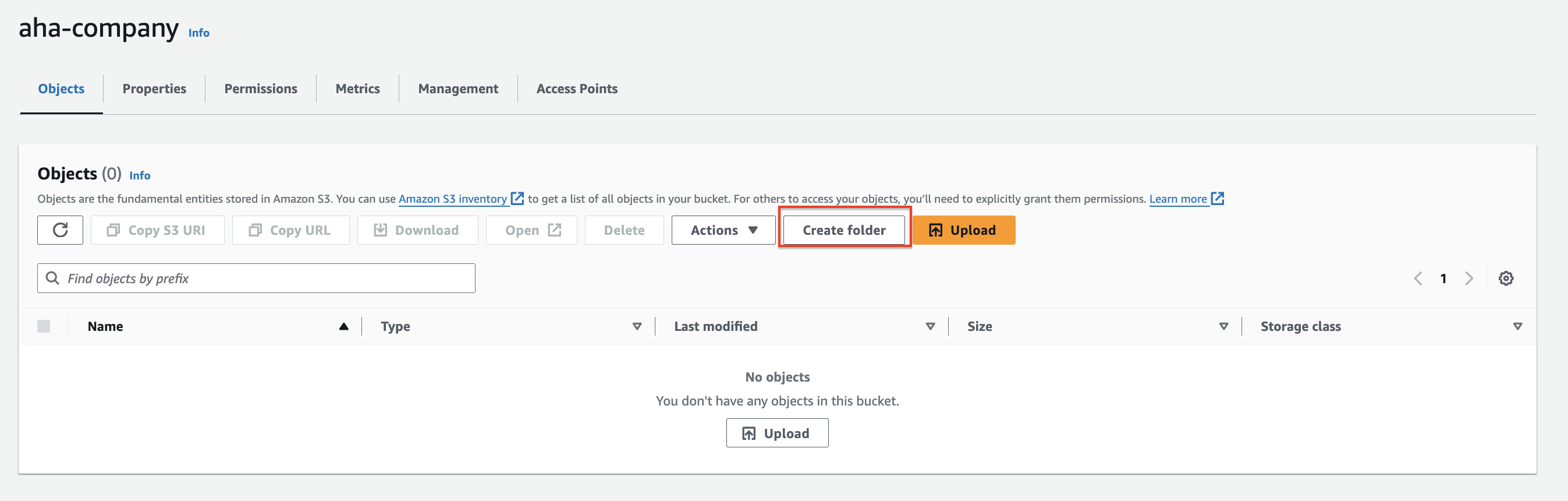
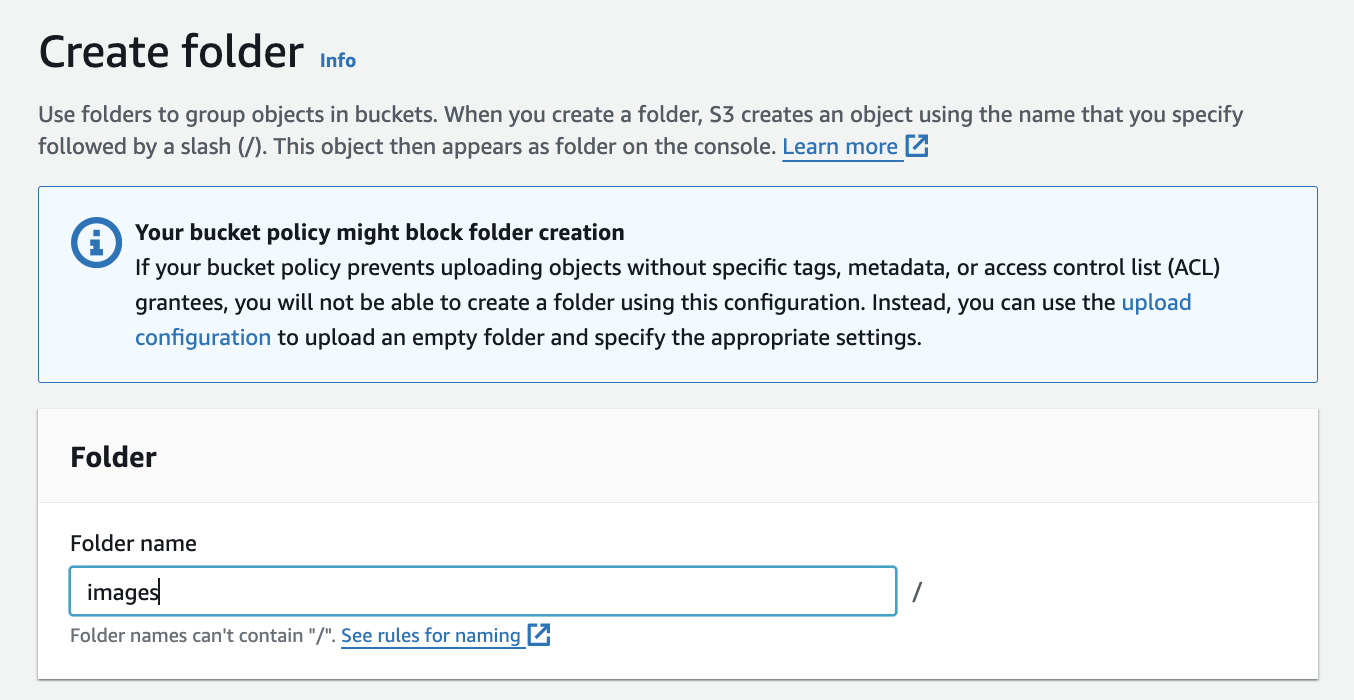
The folder has been created.
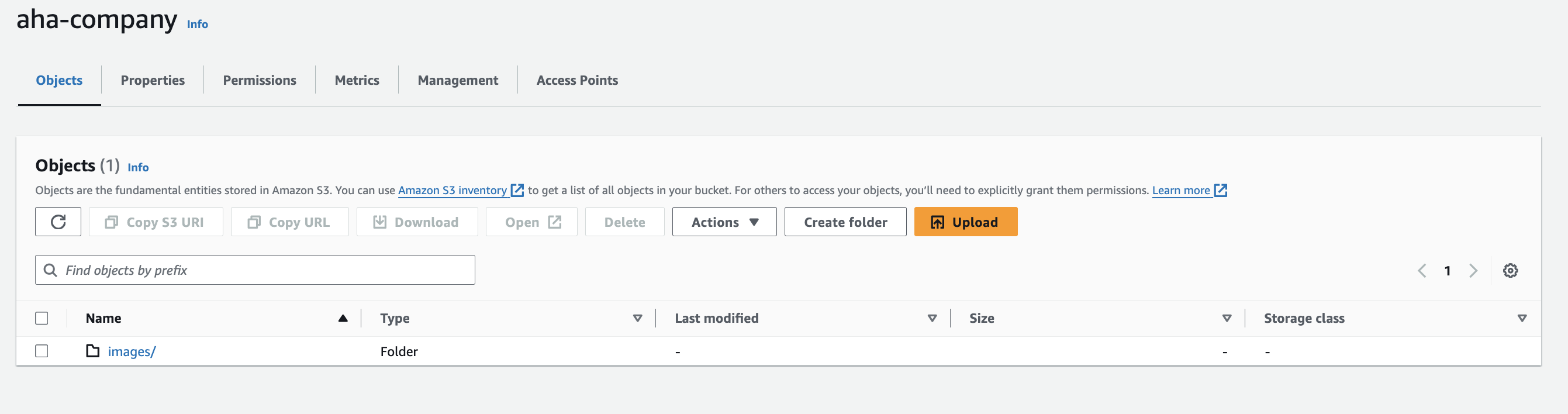
Step 3 - Create objects named "images" and "web" in the bucket
Access the S3 console and navigate to the "aha-company" bucket.
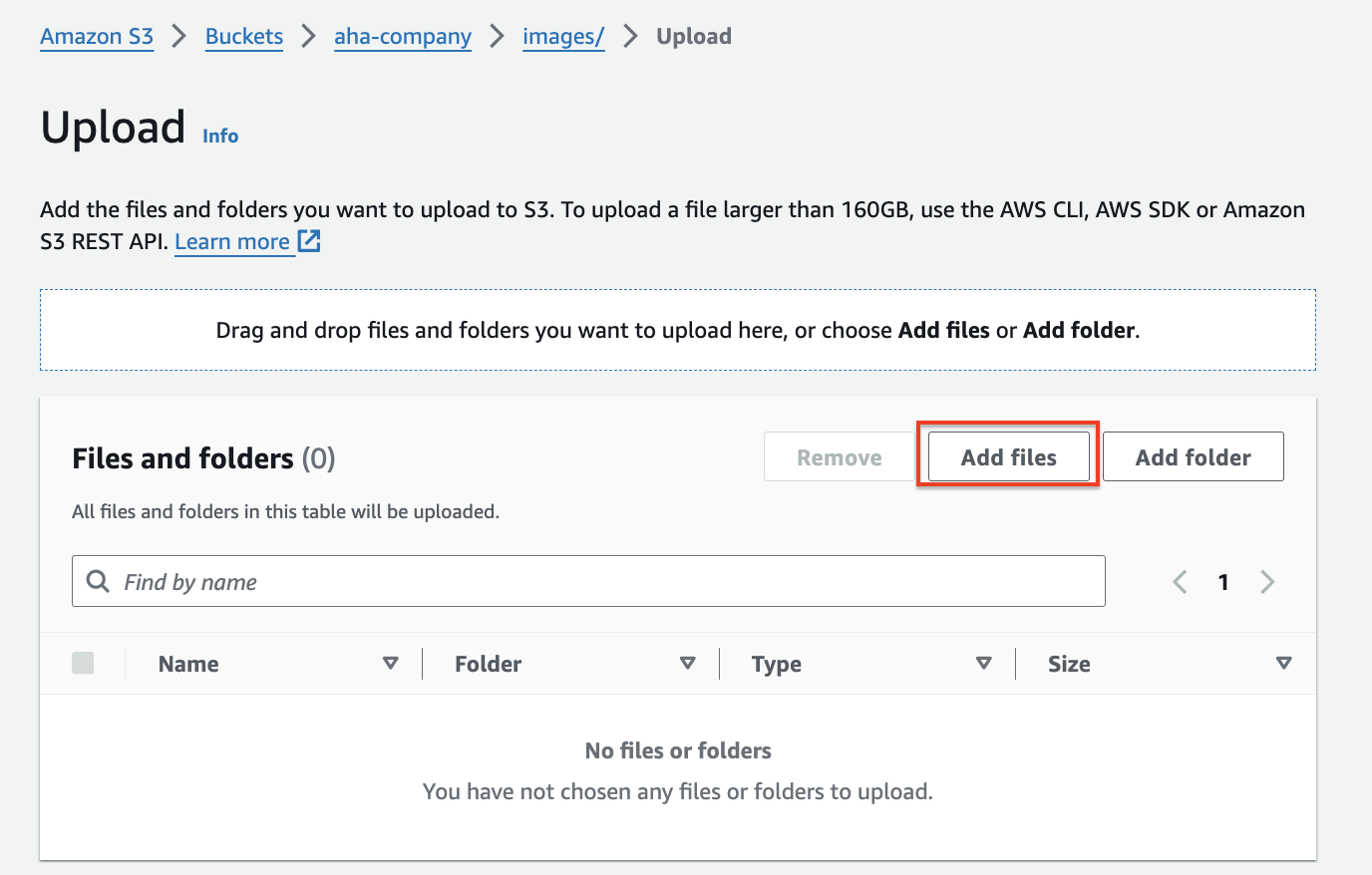
Click on "Upload" and select the files you want to upload, naming them "images" and "web" accordingly.
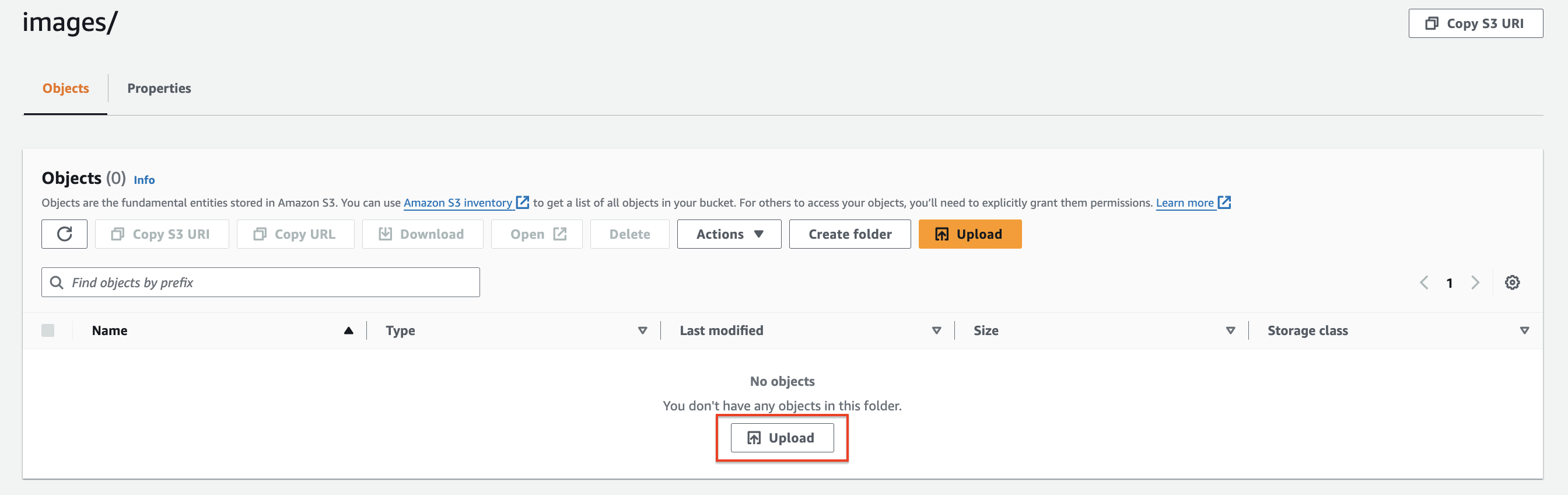
- Click "Upload" to complete the process.
Step 4 - Test Amazon S3 access
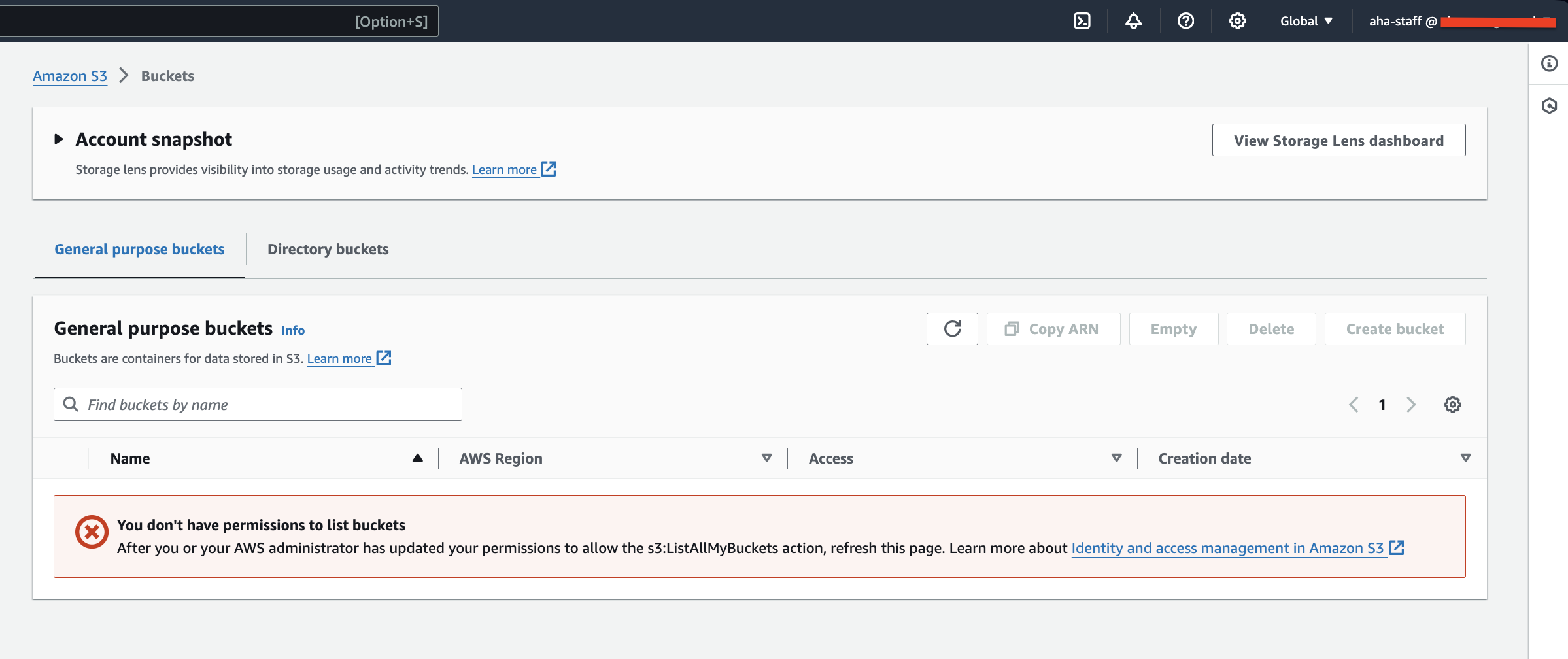
- Use either the AWS CLI or an S3 client to attempt to list the contents of the "aha-company" bucket using the "aha-staff" user's credentials.
- Verify that we can't successfully list the objects.
Step 5 - Create a policy
Access the IAM console and navigate to the "aha-staff" user's permissions.
Click on "Add inline policy."
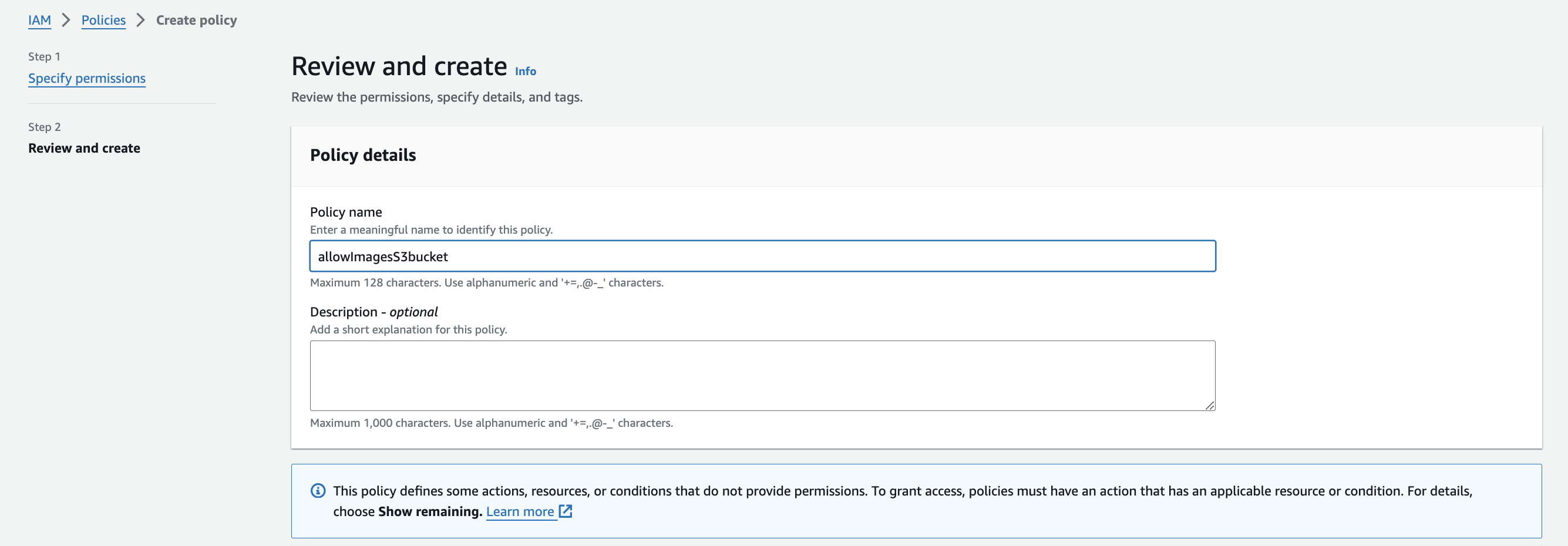
- In the JSON editor, add this line
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowS3",
"Effect": "Allow",
"Action": ["s3:*"],
"Resource": ["*"]
},
{
"Sid": "DenyBucket",
"Effect": "Deny",
"Action": ["s3:*"],
"Resource": ["arn:aws:s3:::aha-company/web/","arn:aws:s3:::aha-company/web/*"]
}
]
}
- Review and apply the policy.
Step 6 - Grant the "aha-staff" user permission to view only the "aha-company/images" object
Access the IAM console and navigate to the "aha-staff" user.
Click on the "Permissions" tab.
Click on "Add permissions."

Choose either "Attach existing policies directly" to attach a pre-existing policy
Select the appropriate policy for the user's required permissions.
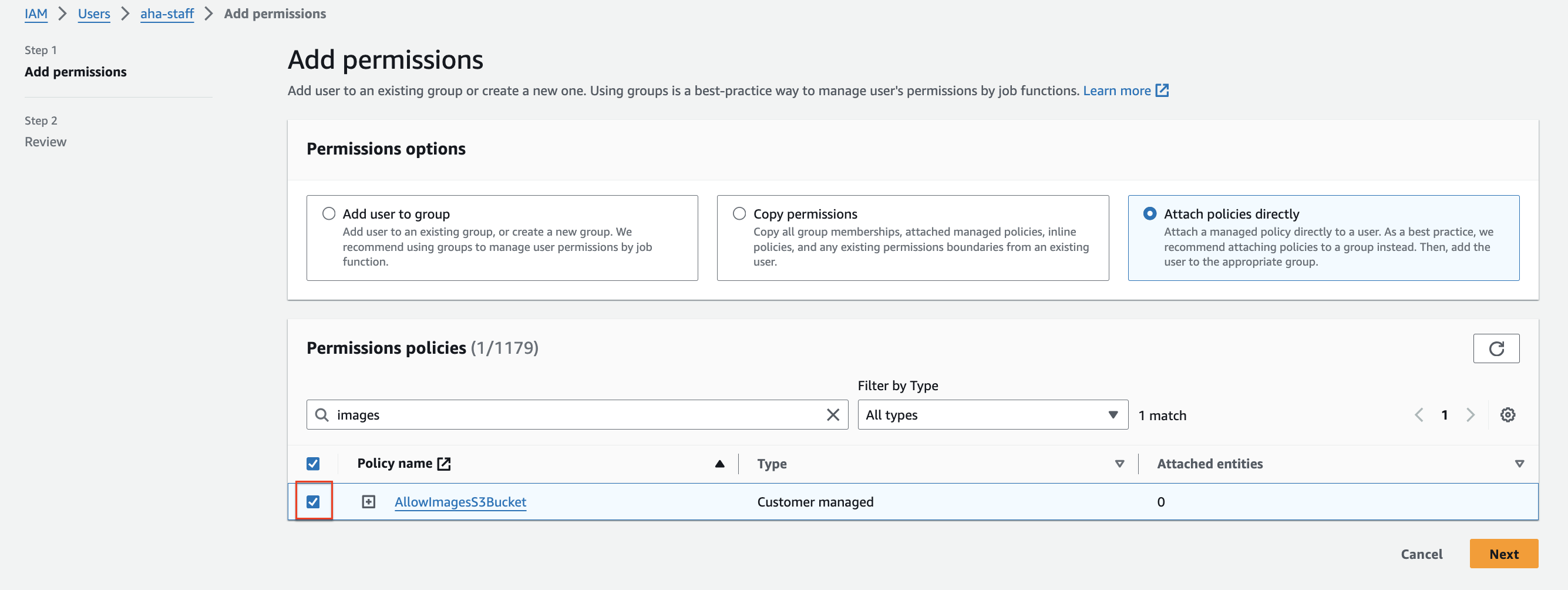
Click on "Attach policy." and click Next
Click add permissions
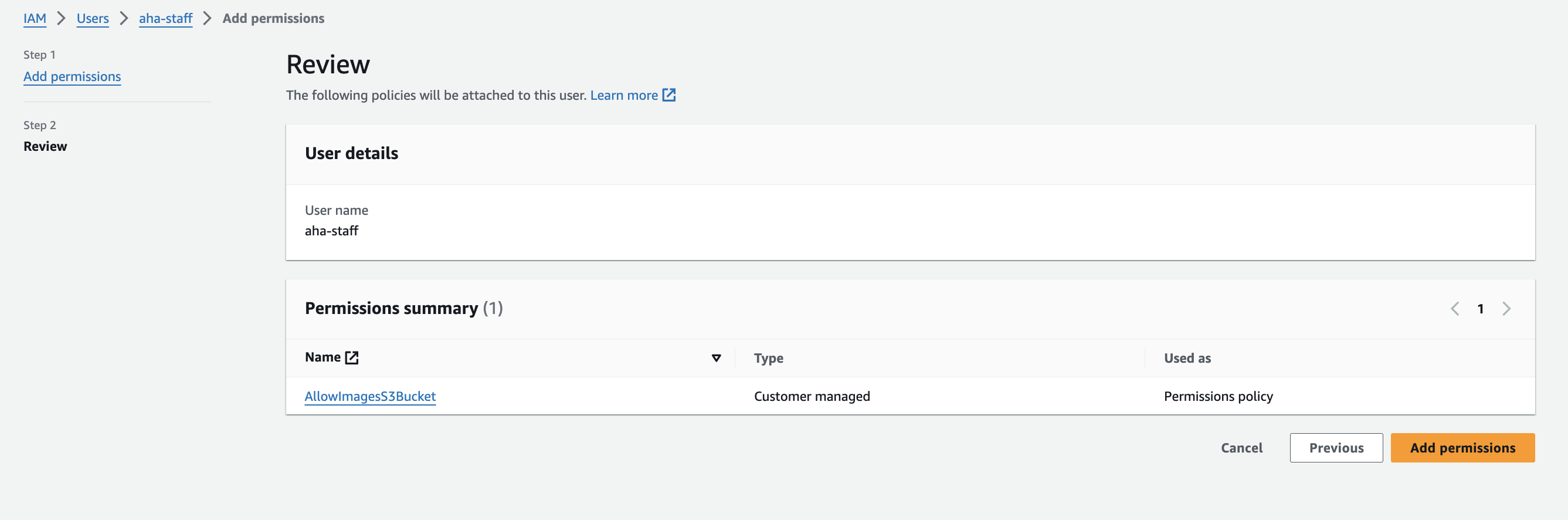
Step 7 - Test Amazon S3 access
- Repeat the access test, but this time verify that the "aha-staff" user can only view the "images" object and not the "web" object.

- Open the object

- The object has successfully access.
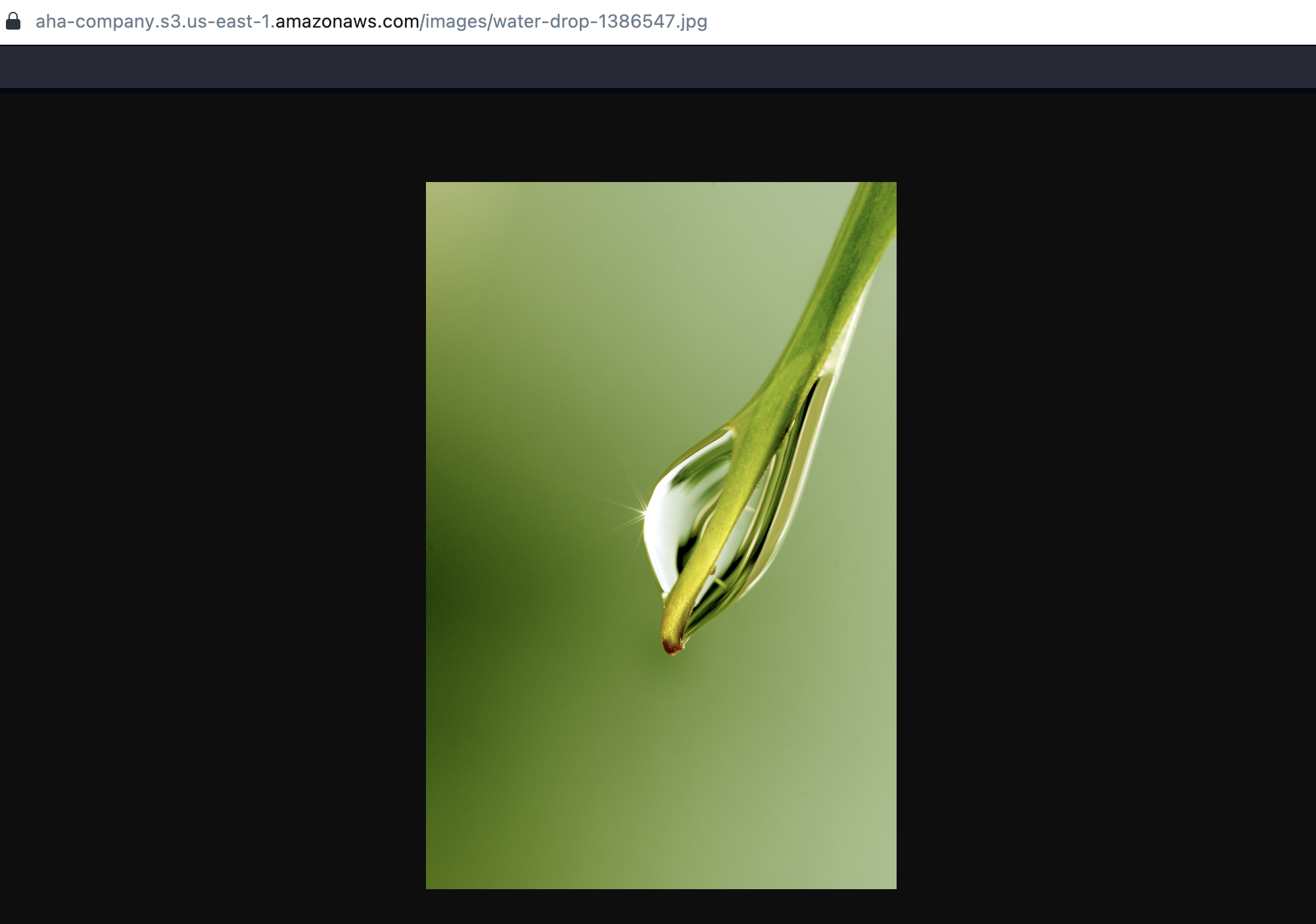
- Testing to open the web object
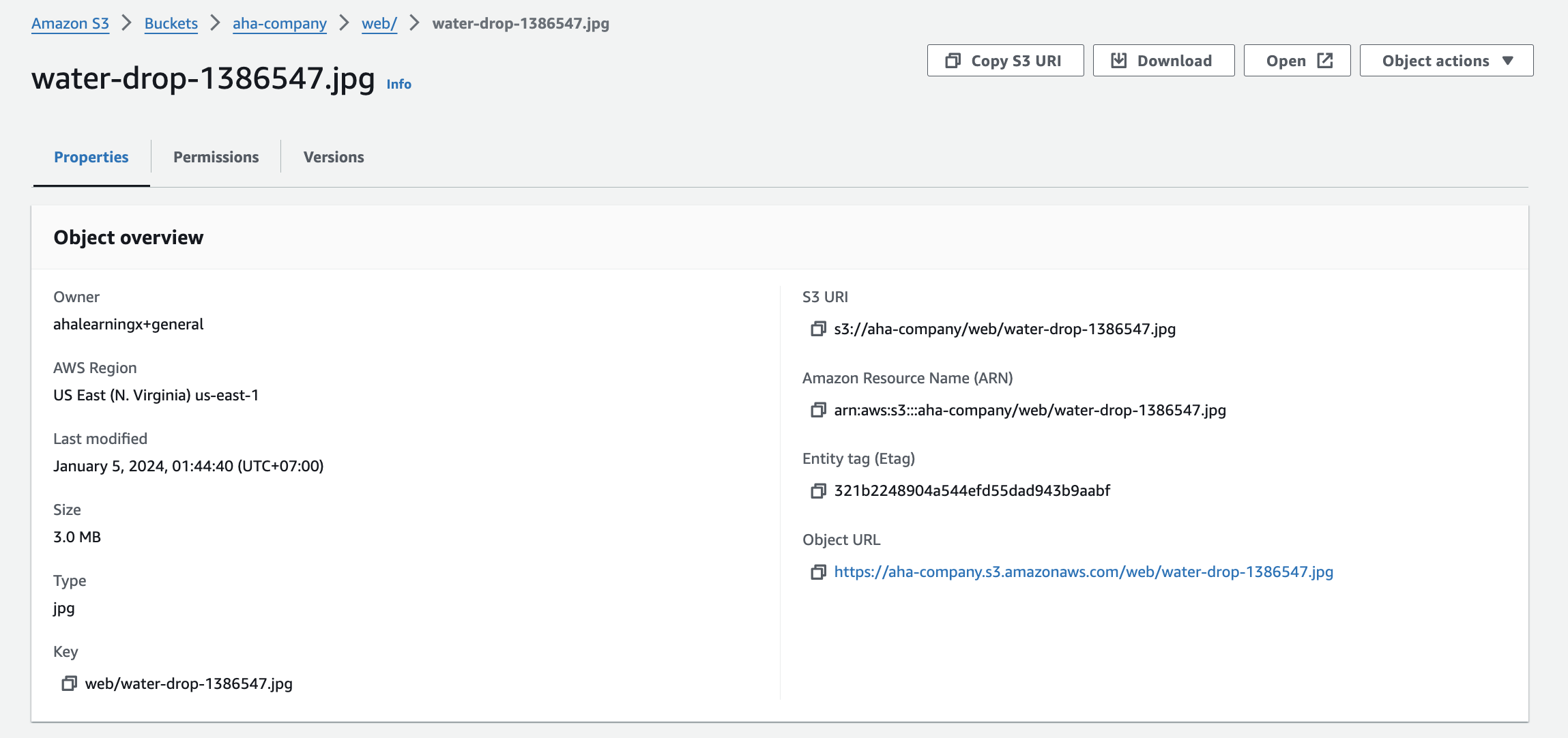

It appears that the user "aha-staff" cannot be granted permission to access objects in the "web" folder.
Step 8 - Delete the Amazon S3 bucket
Access the S3 console and navigate to the "aha-company" bucket.
Click on "Empty bucket"

- Click on "Delete bucket."

- Confirm the deletion.
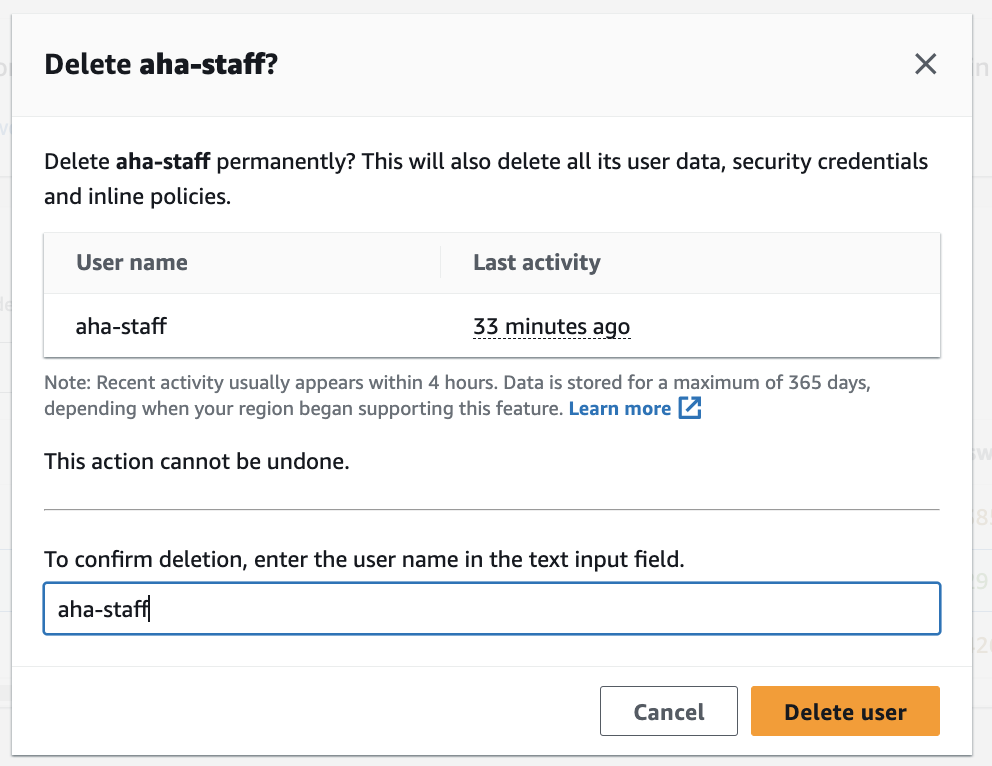
Step 9 - Delete the user
Access the IAM console and navigate to the "aha-staff" user.
Click on "Delete user."
Confirm the deletion.
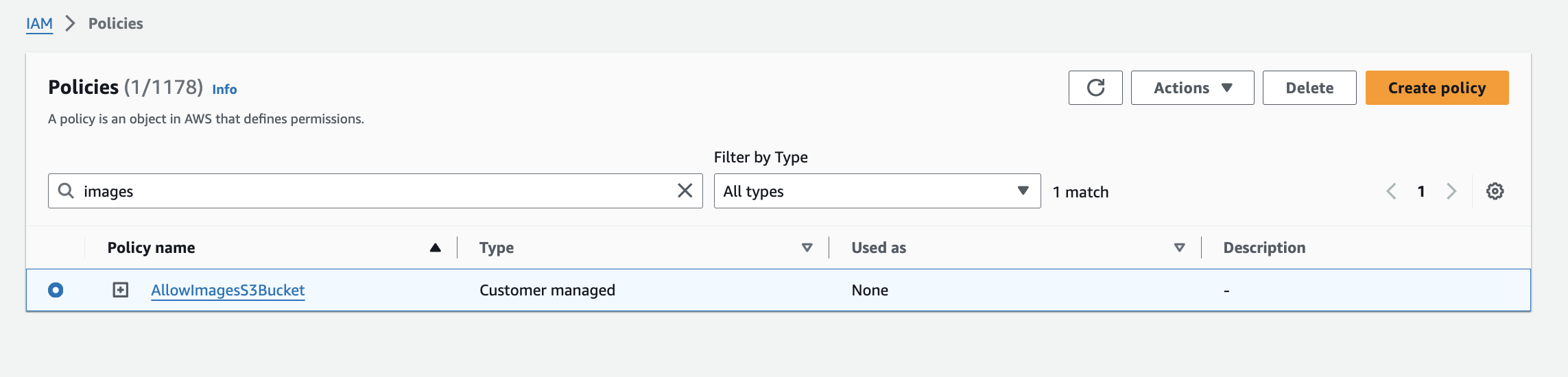
Delete policy to navigate to policies IAM
Click the AllowImagesS3Bucket then click "Delete"
The user and policy has been deleted.
Thank you.
References
https://docs.aws.amazon.com/IAM/latest/UserGuide/intro-structure.html
https://docs.aws.amazon.com/IAM/latest/UserGuide/access_policies_create-console.html
https://docs.aws.amazon.com/IAM/latest/UserGuide/when-to-use-iam.html
Subscribe to my newsletter
Read articles from Abdul Hakim directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Abdul Hakim
Abdul Hakim
I'm Cloud DevOps Enthusiast | AWS Community Builders.