AWS Redshift password rotation using Secrets Manager with Key Management Service (KMS)
 Binisha Joshi
Binisha JoshiOne way of managing, retrieving and rotating passwords, credentials and other secrets is via the use of AWS Secrets Manager along with the use of AWS Key Management Service (KMS) for encryption. Secrets Manager avoids the hardcoding of credentials into your applications or configuration files and prevents it from being exposed if the application or code is compromised.
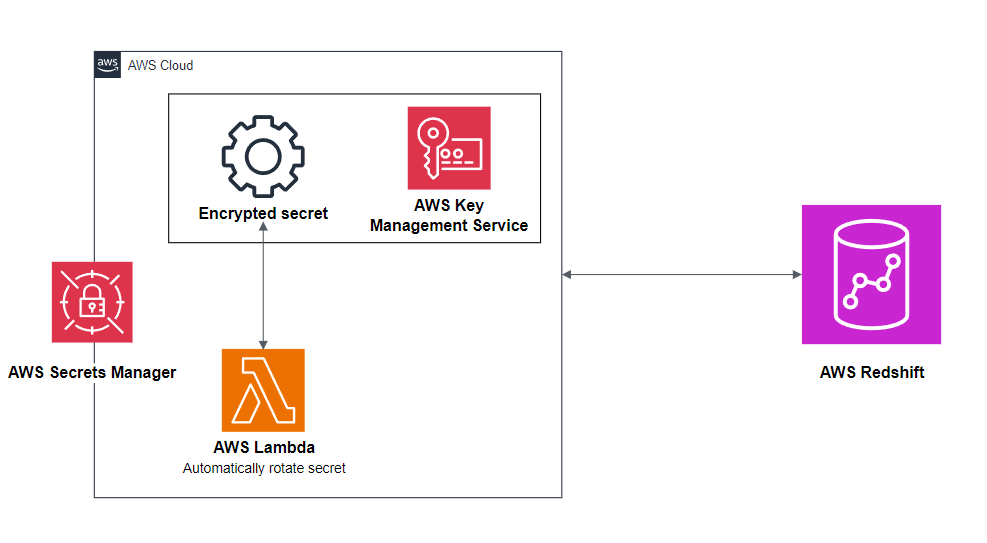
Architecture diagram for Redshift admin credentials management using Secrets Manager
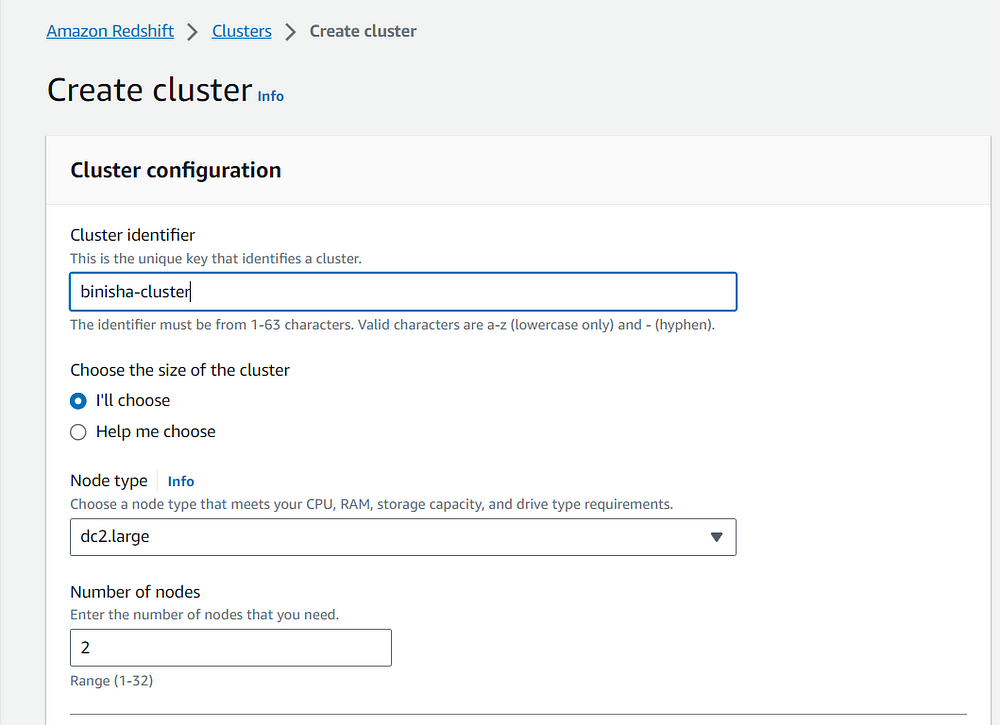
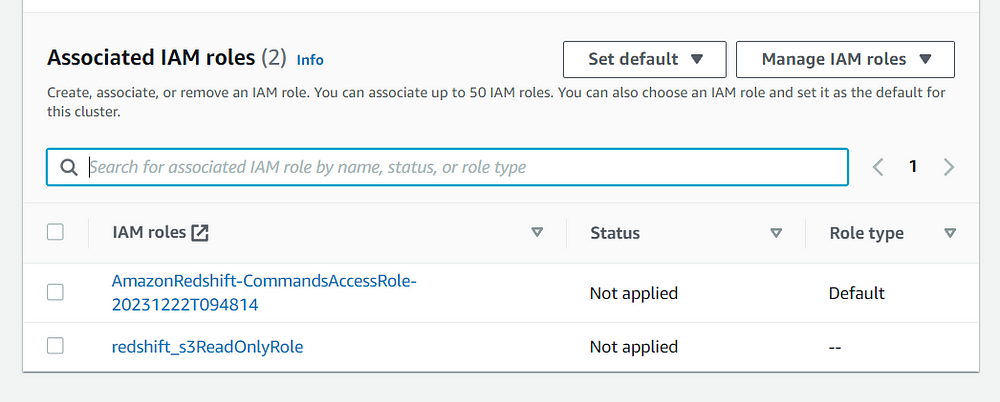
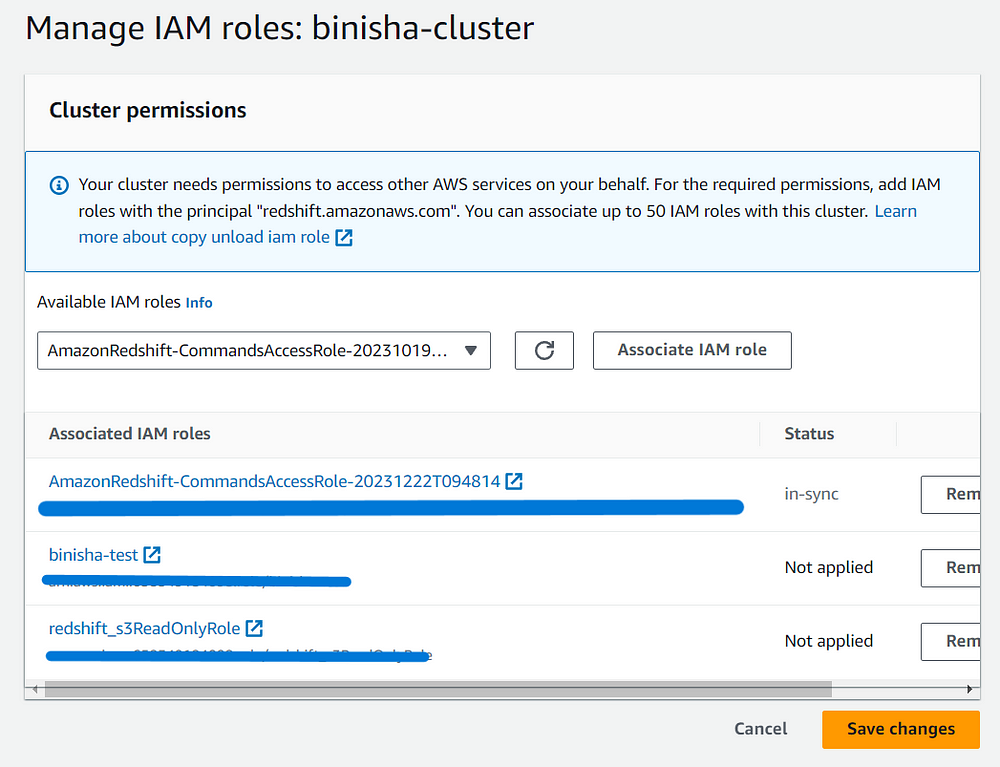
First create a Redshift cluster and give it a name with the size and node type of your choice. Associate the necessary IAM roles to the cluster, here I have given the cluster S3 read only access. You can give any necessary permissions that you want according to your project or requirements.
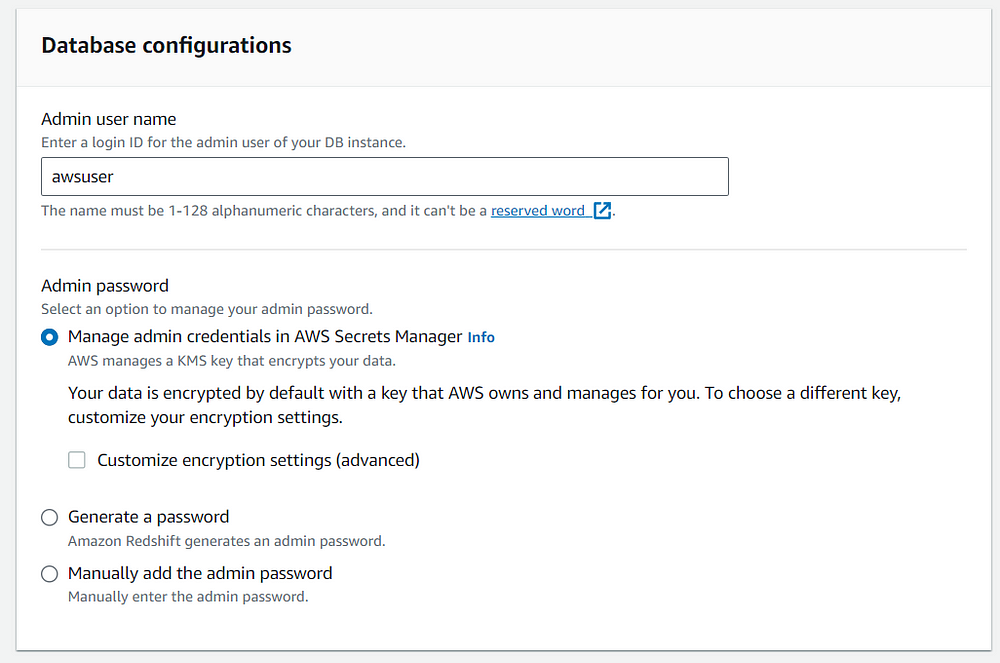
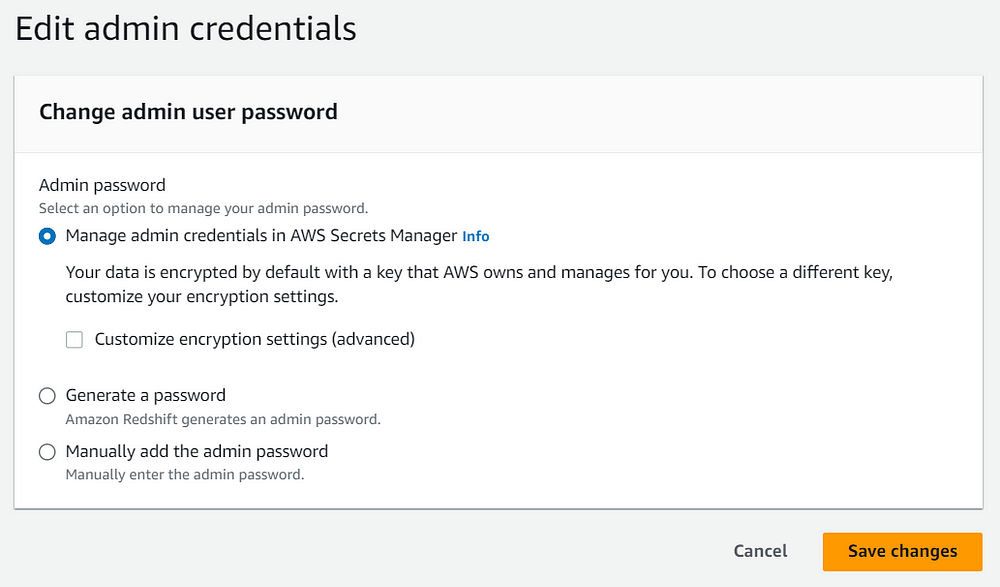
You can either create and store the password in the AWS Secrets Manager while creating the cluster or modify the settings after you have created the cluster. You can directly manage admin credentials in Secrets Manager without creating a manual password while creating the cluster in the following way.
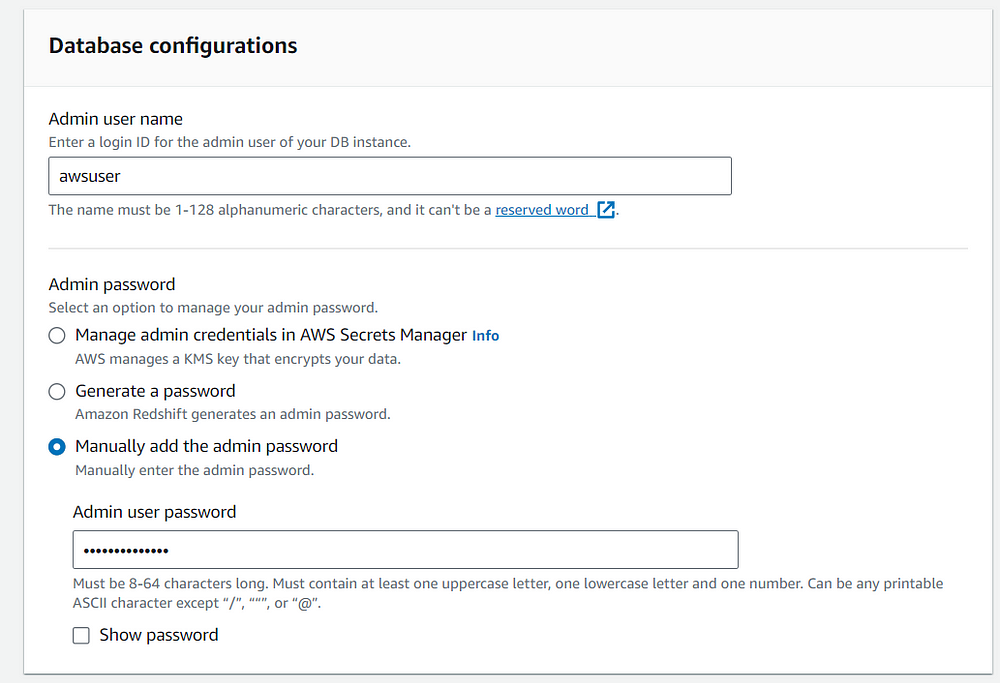
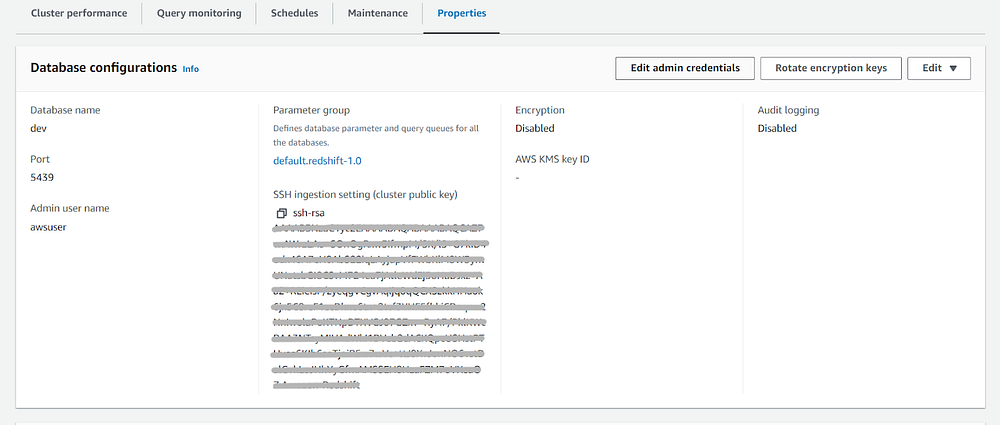
On the other hand, if you are using a manual admin password and you want to later manage it in the Secrets Manager you can simply navigate to the Properties tab in the cluster and select Edit admin credentials then you can select Manage admin credentials in AWS Secrets Manager.
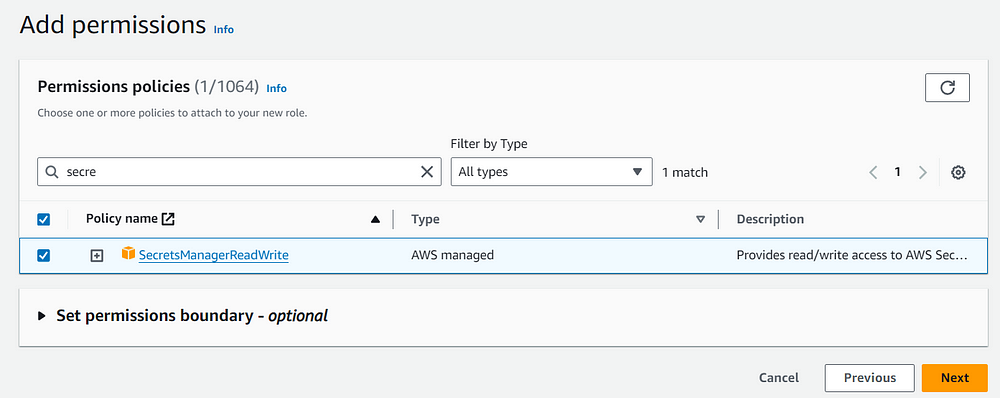
Now we have to create an IAM role for the Redshift and give it the SecretsManagerReadWrite permissions so that the Redshift can create a secret and then read the secret value and rotate the password.
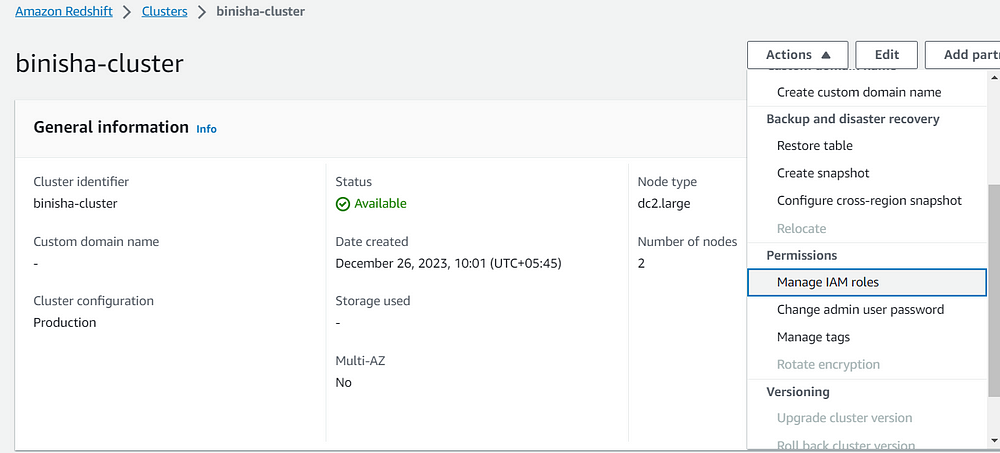
Now navigate to the cluster and configure the IAM roles by navigating to the Actions. Here add the role that you have just created and save it.
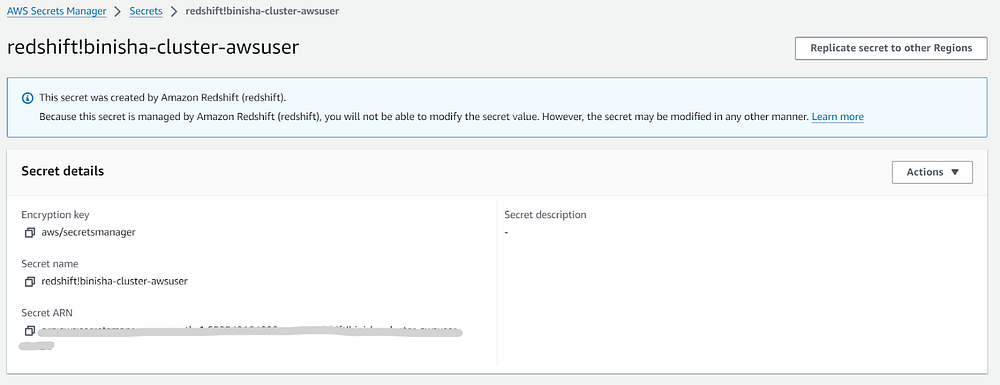
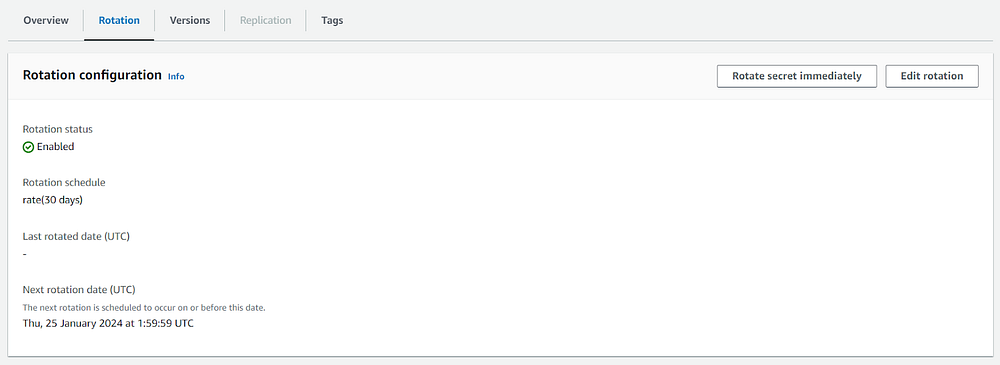
After completing all the steps, navigate to the AWS Secrets Manager and search for the secret by typing your cluster name. You can see that Redshift has automatically created a secret similar to the name of your cluster with automatic rotation of the secret value once every 30 days.
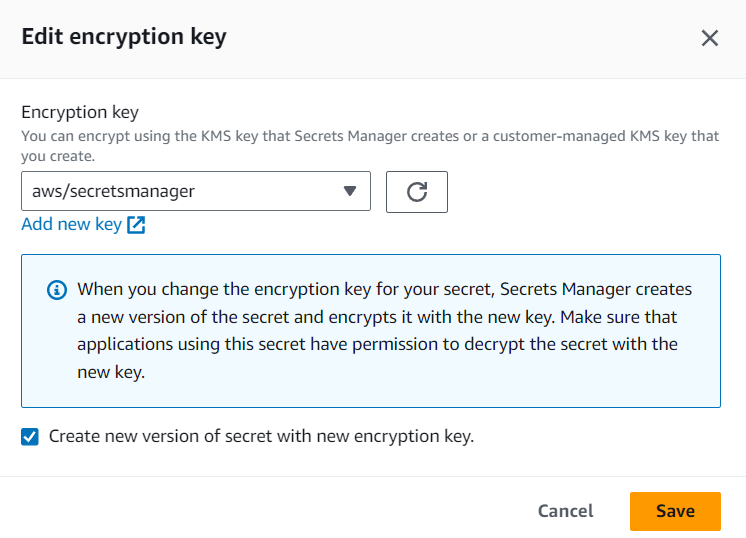
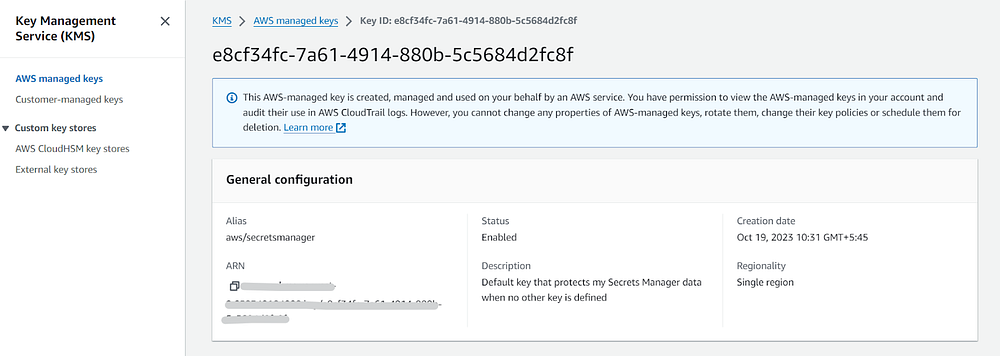
This secret is automatically encrypted using AWS Key Management Service (KMS). If the user doesn’t create an encryption key by him/herself, it uses the default encryption key for Secrets Manager aws/secretsmanager.
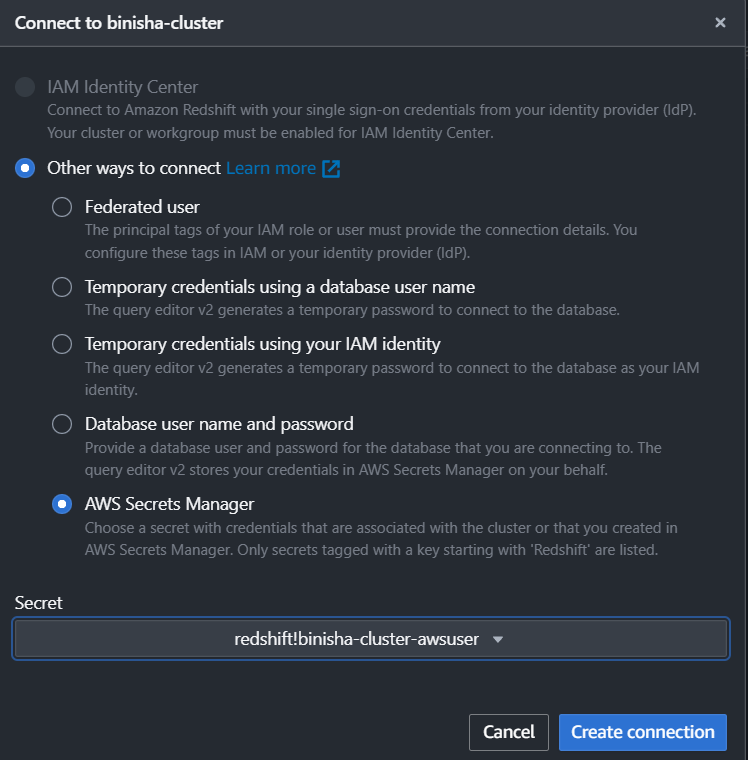
Now when connecting to the Query Editor, you can retrieve the password by selecting the AWS Secrets Manager option without having to manually type the password while creating the connection.
CONGRATULATIONS!!!
You have successfully managed your Redshift credentials using Secrets Manager and KMS.
Subscribe to my newsletter
Read articles from Binisha Joshi directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by