AWS Systems Manager(SSM)
 Ramana Reddy
Ramana ReddyWhat is SSM? AWS Systems Manager (SSM) is an agent-based service for managing servers on any infrastructure: AWS, on-premise and other clouds. Amazon used to provide loosely wrapped services for managing EC2 instances such as EC2 Run Command for executing remote commands and AWS Ops Works for configuration management using Chef Agents. But there used to be a gap where no single service was available to manage all servers easily and in an efficient manner. So we have SSM which fills the gap.
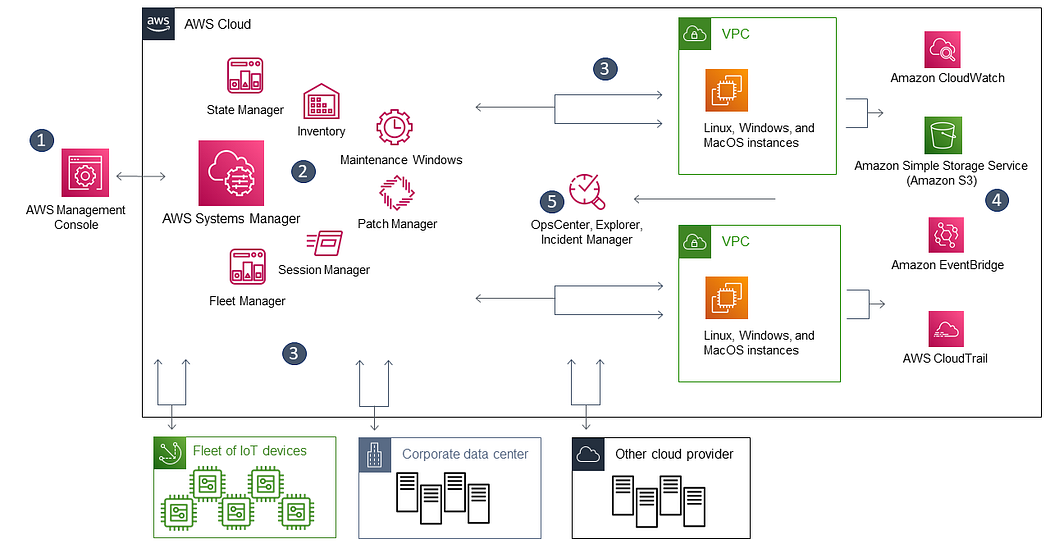
Features:
Run command
This allows us to execute ad-hoc remote commands on the managed instances. Earlier the same used to be achieved using Ansible, Chef or Bastion host to execute ad-hoc commands to our remote hosts. All these solutions require quite a lot of setup to get started and also there are no easy ways to know who is executing what. SSM gives far greater control over managing remote command executions by integrating with AWS Identity and Access Management (IAM). It provides logs of the remote commands for auditing purpose. We can also create SSM documents for frequently running commands.
State Manager
Over time things change, so keeping our environment complaint with the best security and operating guidelines is a challenge. State Manager makes it very easy to maintain the desired state for our application environment, by giving the ability to execute a set of commands using SSM documents periodically. Let’s say we don’t want to allow SSH in any of our instances, then we schedule an SSM document which shuts down the SSH demon, every 30 mins on all our servers.
Automation
This is an extension to Run Command feature which has been discussed earlier, we know that Run command allows us to execute remote commands on the instances. Automation allows more than just remote commands, for example, we can also call AWS APIs as part of the execution. Using an SSM automation type document, we can combine multiple steps to accomplish complex tasks. Please note Automation documents gets executed on SSM Service and with a maximum of 1,000,000 seconds per AWS account per region.
Inventory
Often we would want to know what software and services are running on our instances, SSM Inventory gives an ability create association an SSM document to a managed instance which gather inventory information continuously and make it available for reviewing later.
Patch Manager
One of an important feature for keeping our environment up to date with newly released patches. SSM Patch manager lets us create patch baselines and apply them to managed instances during the Maintenance Windows. This is done automatically whenever the maintenance window period is arrived so reduces the risk of a manual miss.
Maintenance Windows
SSM provides this feature to schedule a set of tasks to be executed on our environment on regular basis. We can apply patches, install new software and upgrade operating system during this period. We can leverage SSM Run commands and Automation features during the maintenances windows.
Compliance
This is a reporting mechanism of SSM to tell us whether or not our instances are compliant as per patch baselines or States Manager associations. We can use this feature to drill down the issues and fix using SSM Run commands or Automation.
Parameter Store
SSM parameter store is like “salt in our food”. This feature removes the risk of exposing DB passwords and other sensitive parameters we would like to use in our SSM Documents by integrating AWS KMS service. This is a small component of SSM but an essential one without which the service will be incomplete.
Documents
SSM provides several predefined documents for using with Run Commands, Automation, and States Manager. We can also define our own custom documents too. SSM Document permissions are integrated with AWS IAM so we can control who has the execution rights on which documents using AWS IAM policies.
Concurrency
SSM allows specifying either percentage or count of the target instances to execute commands or automation documents in parallel. We can also stop executions based on the number of target instances throwing errors.
Security
Security is the most important component in any system and also SSM agent runs as root on the instance so that we can better understand its security posture.
SSM agent uses a pull mechanism to fetch pending commands from SSM service and executes on the instance.
Communication between SSM agent and service happens over a secure channel using HTTPS protocol.
SSM agent code is open source so we know exactly what it does.
SSM service can be integrated with AWS CloudTrail to log all API calls.
What’s next?
Bastion-free setup: We can manage instances without having an additional bastion server or without opening SSH port (22) on the instances, you can read more about it here.
Windows Log Management: We can send logs from windows instances to Cloud watch using SSM, you can read more about it here.
Conclusion:
In total AWS Systems Manager is a feature-rich production ready AWS service to manage the servers from anywhere.
Subscribe to my newsletter
Read articles from Ramana Reddy directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
