AWS IAM: Secure access control in AWS Cloud
 Subash Neupane
Subash Neupane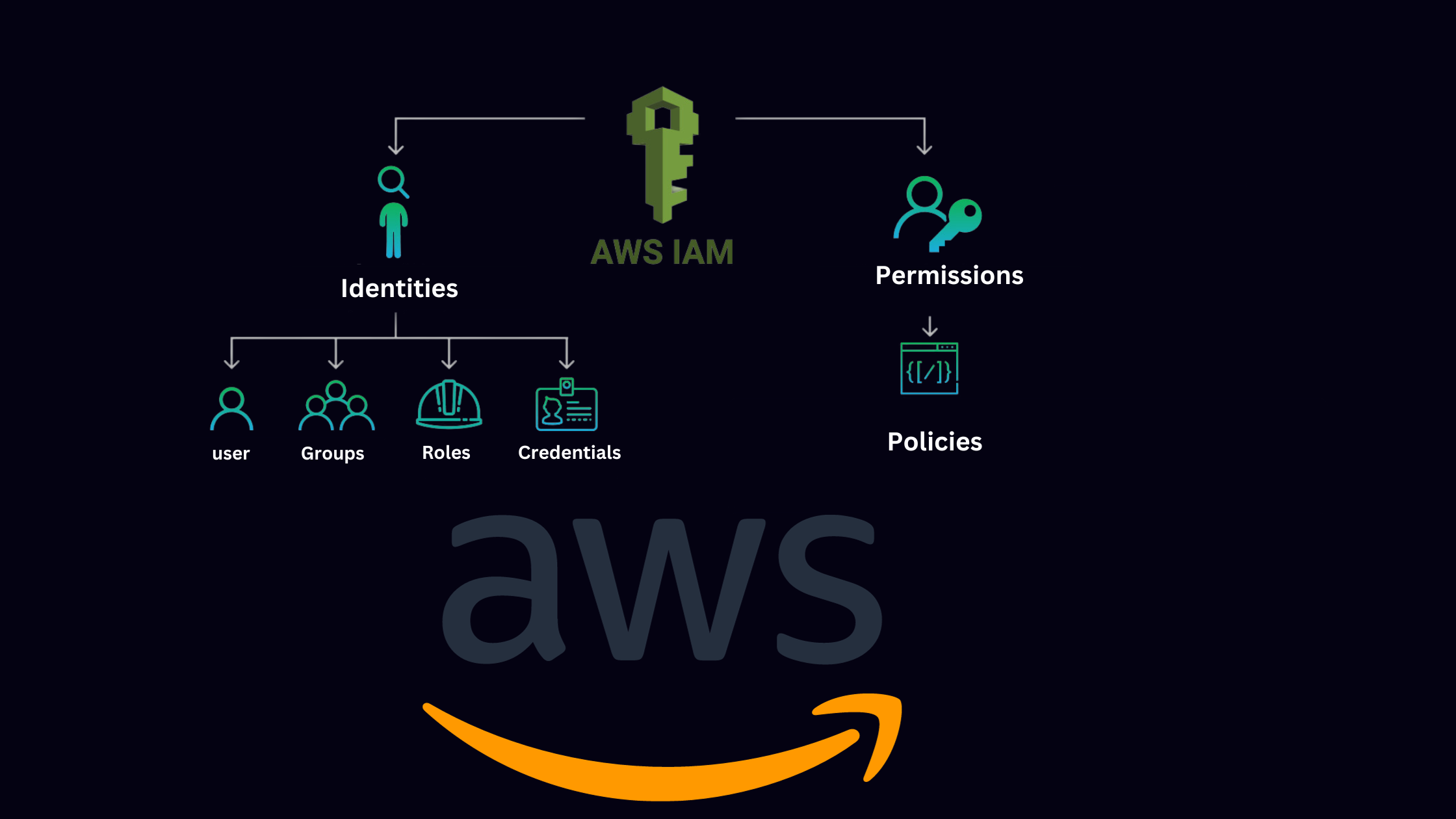
In this blog, we are going to explore one of the AWS services i.e. IAM. IAM is abbreviated as Identity Access Management and it empowers users to manage access to AWS services securely.
What is IAM?
AWS IAM is a web service that enables Amazon Web Services (AWS) customers to manage users and user permissions in the AWS cloud. It is a centralized service that enables us to manage access to AWS services and resources securely. The root user is the one who manages all the users and the permissions allowed to the permission. By using the IAM service, we can ensure that only authorized users have the right level of access to perform specific actions. In short AWS IAM does the authentication and authorization process. It defines the specific user to access the AWS services by authentication and the specific user to use the specific AWS services by authorization process.
Key Components of IAM:
Users: Users are the persons who interact with AWS services. They are created by the root user. They can use those resources if they have permission. Permissions are the policies attached to the user by the root user.
Groups: Groups are the collection of IAM users. If a certain group of users have the same permissions and are performing the same actions then instead of creating a policy for each user, we can simply create a group, attach the policy to the group, and finally add those specific users to this group. Groups reduce the burden of creating each IAM user policy.
Roles: IAM roles are similar to the users, but they are not associated with specific individuals. Instead, roles are assumed by entities such as AWS services or applications, providing temporary permissions.
IAM Policies:
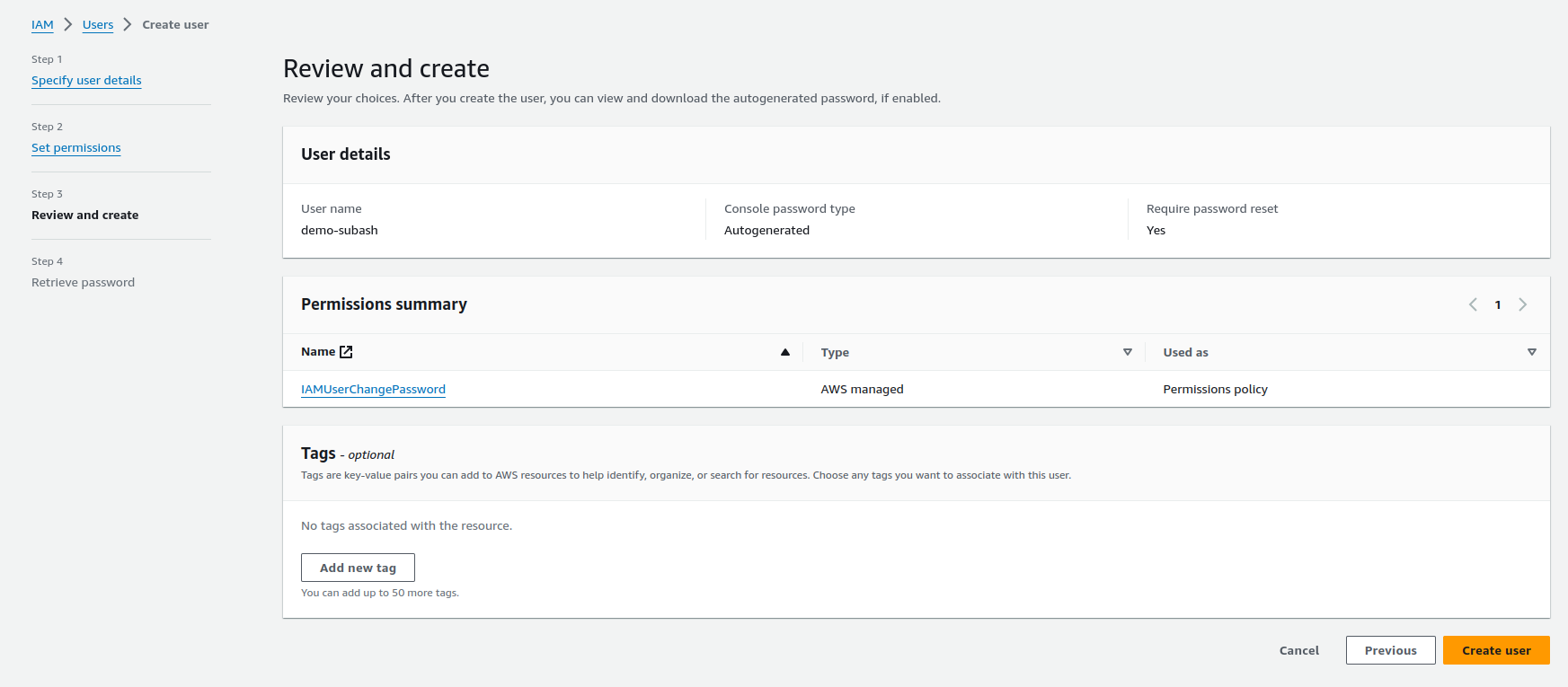
Policies are the building blocks of IAM. Policies define the permissions provided to the users, groups, or roles. AWS IAM uses JSON-based policy language, allowing fine-grained control over what actions can be performed on which resources. Policies must be attached else the users or any groups won't be able to use the AWS services. By default, the IAMUserChangePassword policy is attached to the user.
Let's create the users with and without attaching policies, attach them to the groups, and explore many more practically.
Log in as the Root user and create a user without attaching any policy.
In the search bar of AWS, search IAM > Users > Create user
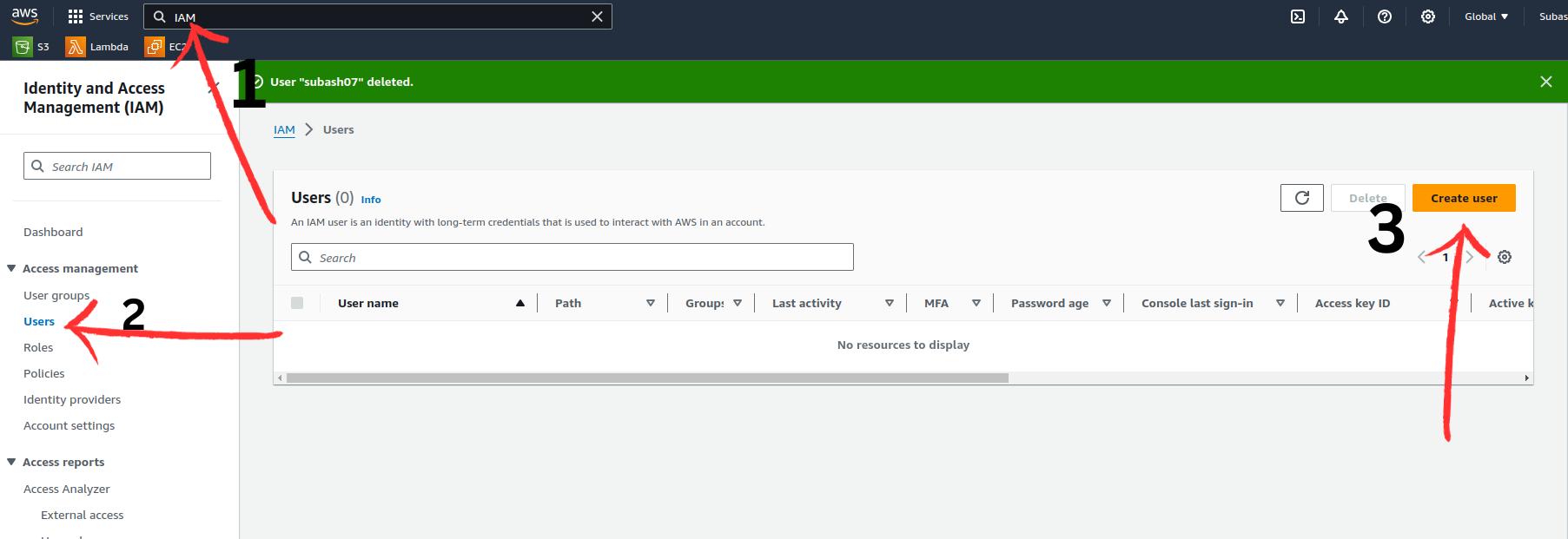
On the next page,
User name : demo
Provide user access to the AWS Management Console - optional: allow
choose: I want to create an IAM user
Console password: Autogenerated password
Users must create a new password at next sign-in - Recommended: allow
Click Next
Set permissions: Leave as it is. keep default
click next
From the above steps, we got the following details.
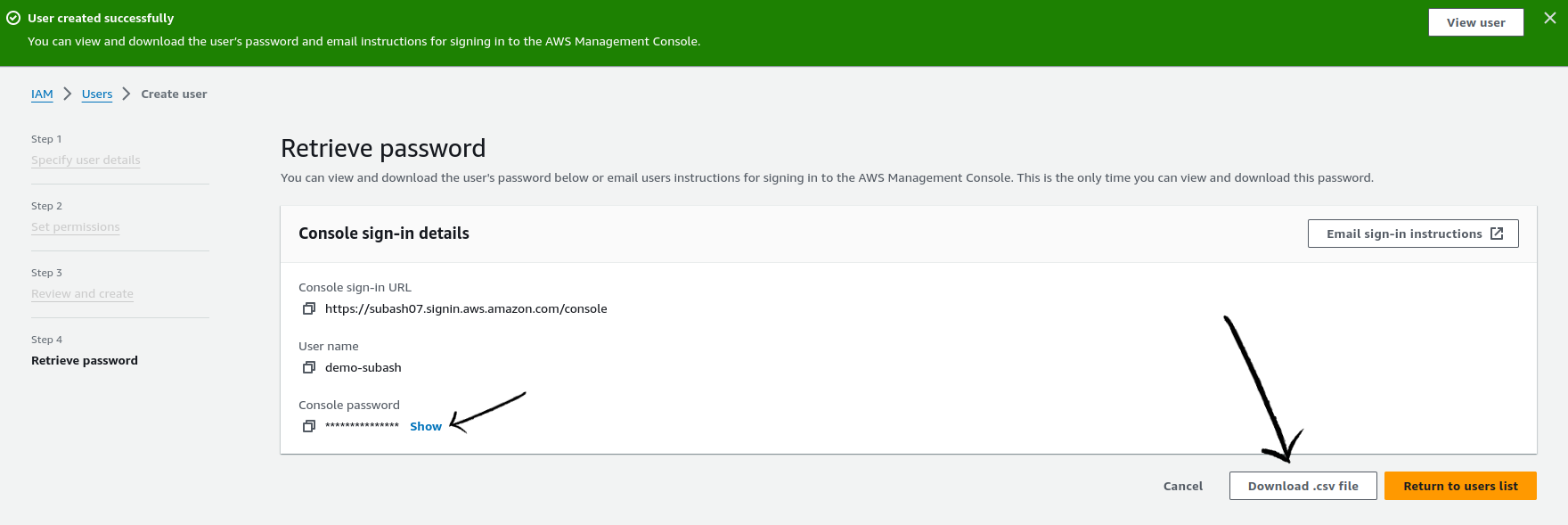
On creating the user, we will get the user credentials either by copying details or downloading the credentials in a CSV file.
Note: Before logging in as a new user, as a root user I created a s3 bucket to verify whether an IAM user would be able to view it or not.
As you can see,I have two buckets in the S3
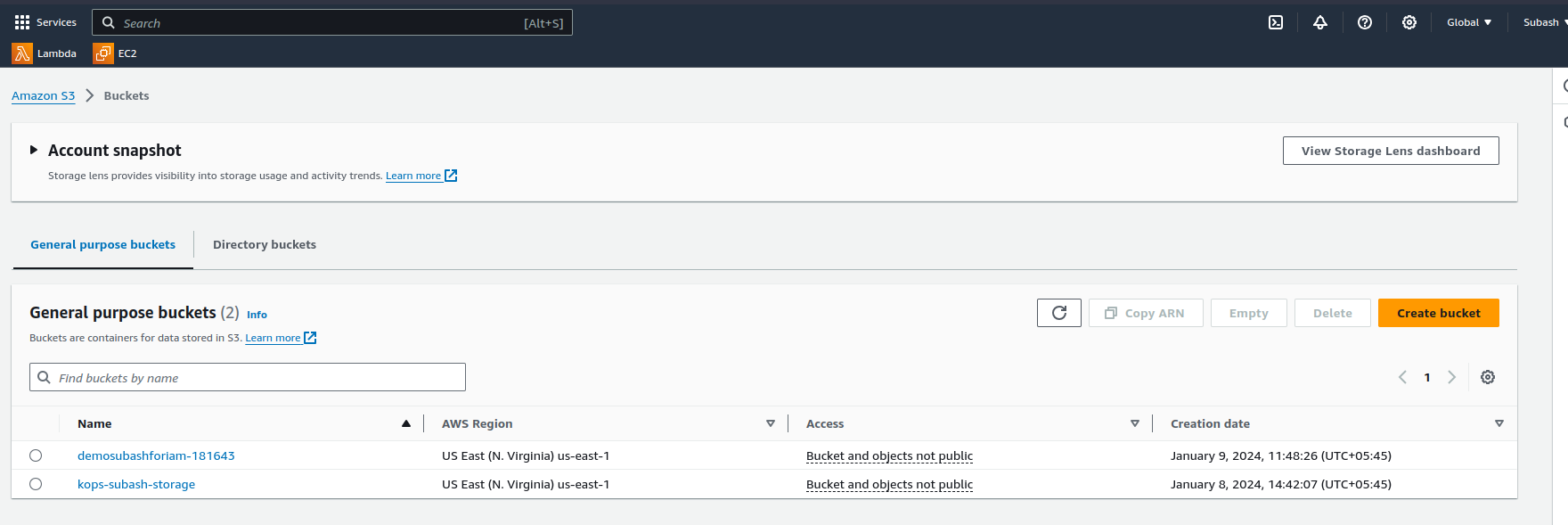
Now let us log in as an IAM user - demo-subash
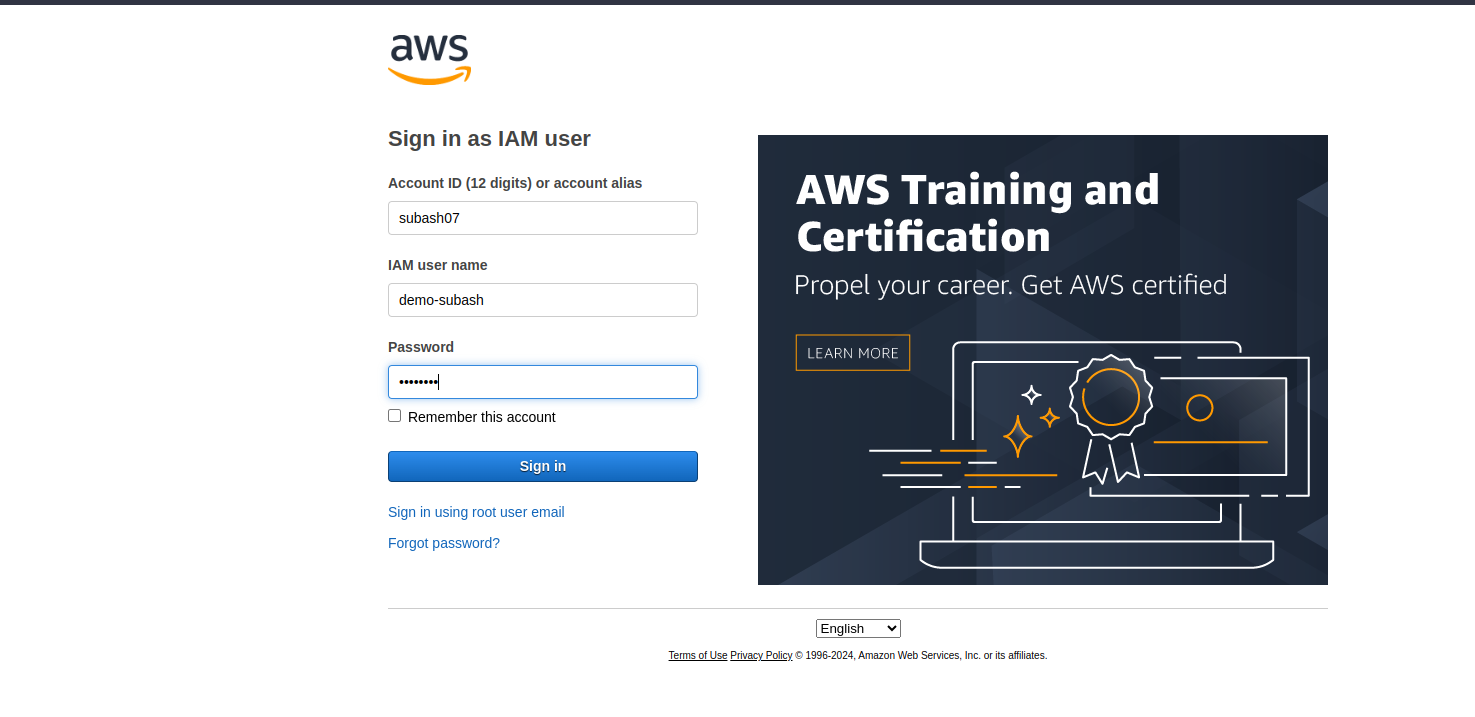
note: Account ID or account alias is taken from console sign in url https://subash07.signin.aws.amazon.com/console which can be found in csv file. subash07 in the url is th account alias
change the password once you are logged in as an IAM User
Now let's try to access the s3 bucket that we created as a root user.
Search s3 in the AWS search bar > click S3
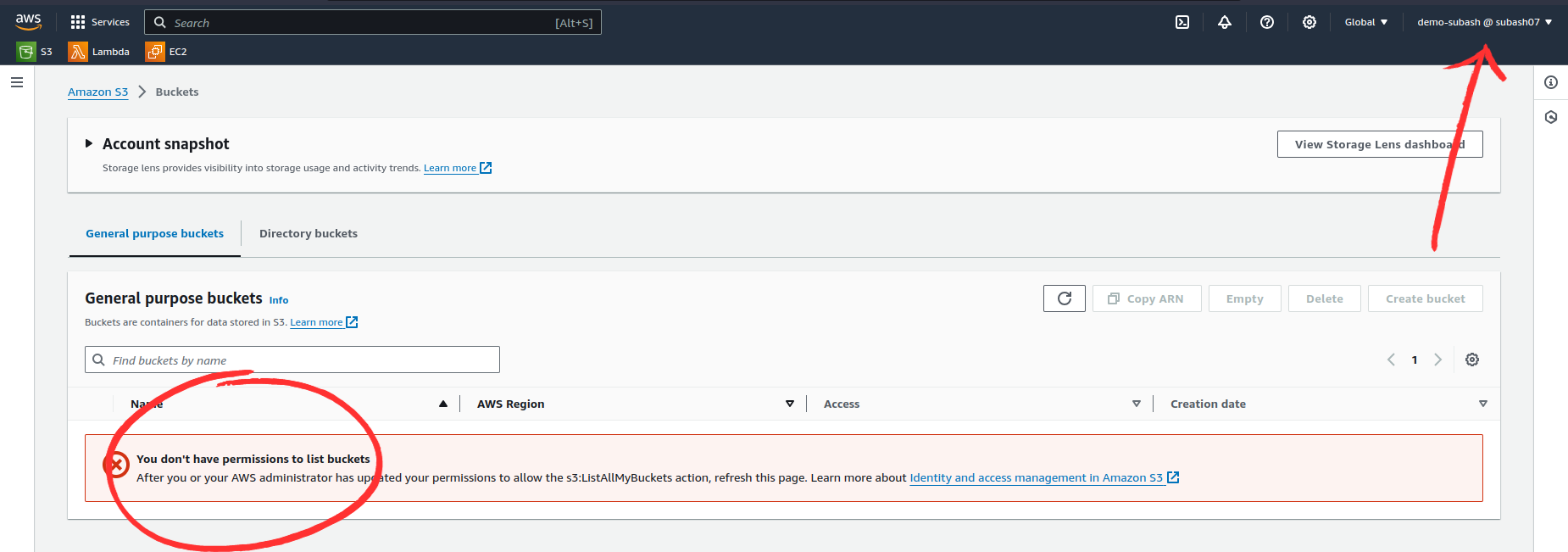
Here you can see I am logged in as subash-demo and I don't have permission even to view the created S3 buckets. Not only this, we cannot use any resources in AWS with this account. This is why attaching policy is important in AWS IAM.
We are authenticated to use an AWS account but are not authorized to use any AWS services with this account.
Let's create a new IAM user with the attached policy.
After logging in as a root user, In the search bar of AWS, search IAM > Users > Create user
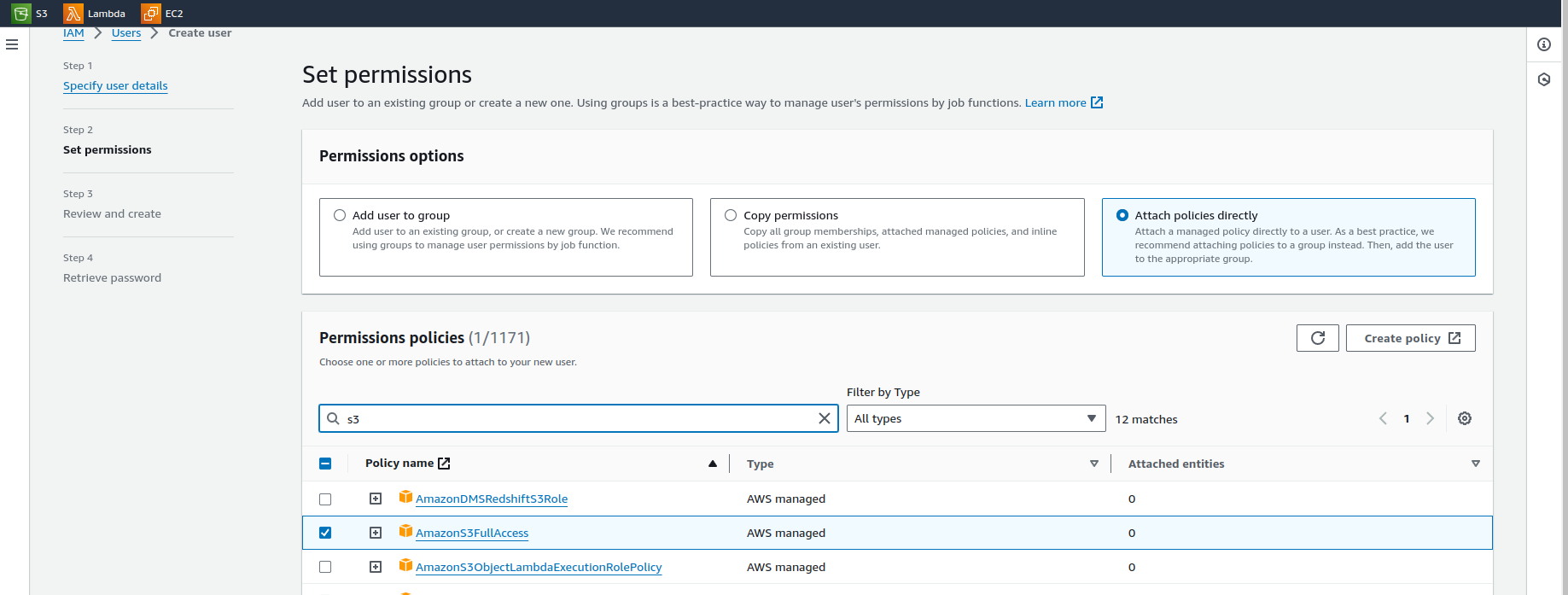
Every step is the same as the previous one, only at set permissions attach the required policy. I have attached the AmazonS3FullAccess policy with this policy a user can do anything with the bucket. This is for demo only, if you are working in a company then based on the requirements you to customize or edit the policy and then attach it to the user or groups.
Create the user and save the credentials.
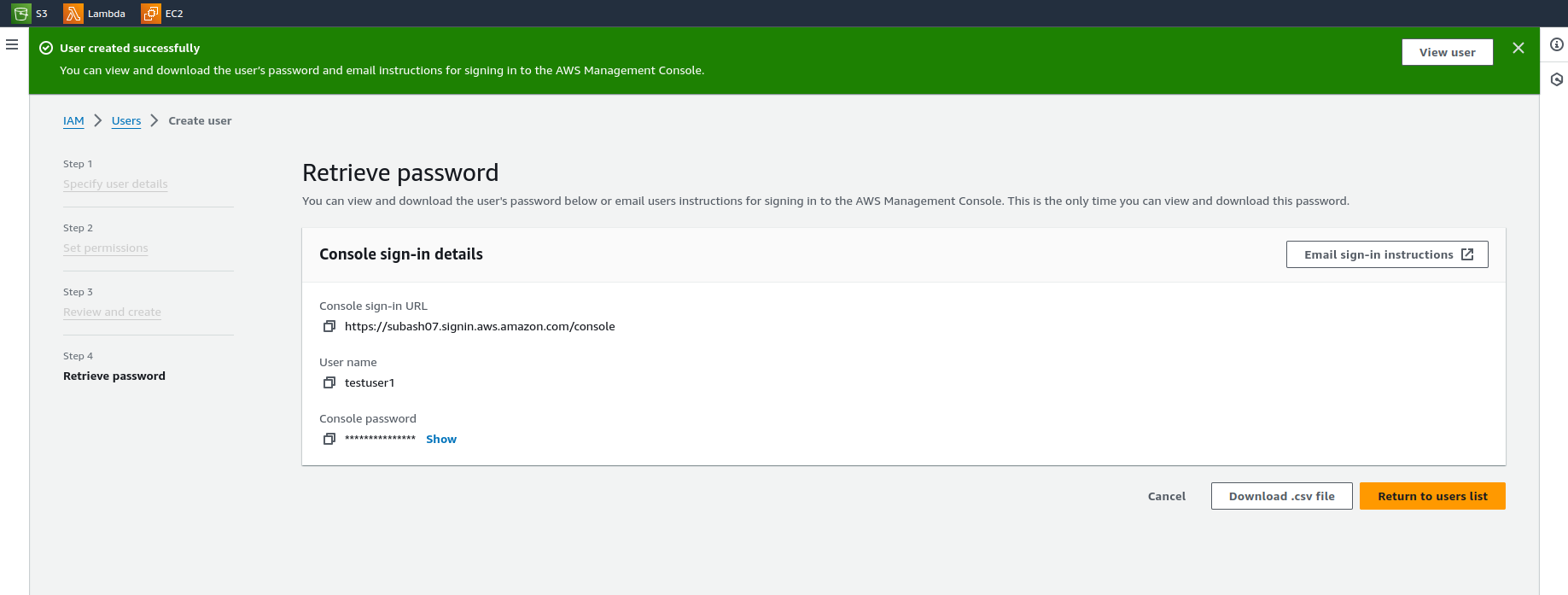
Log in as a testuser1.
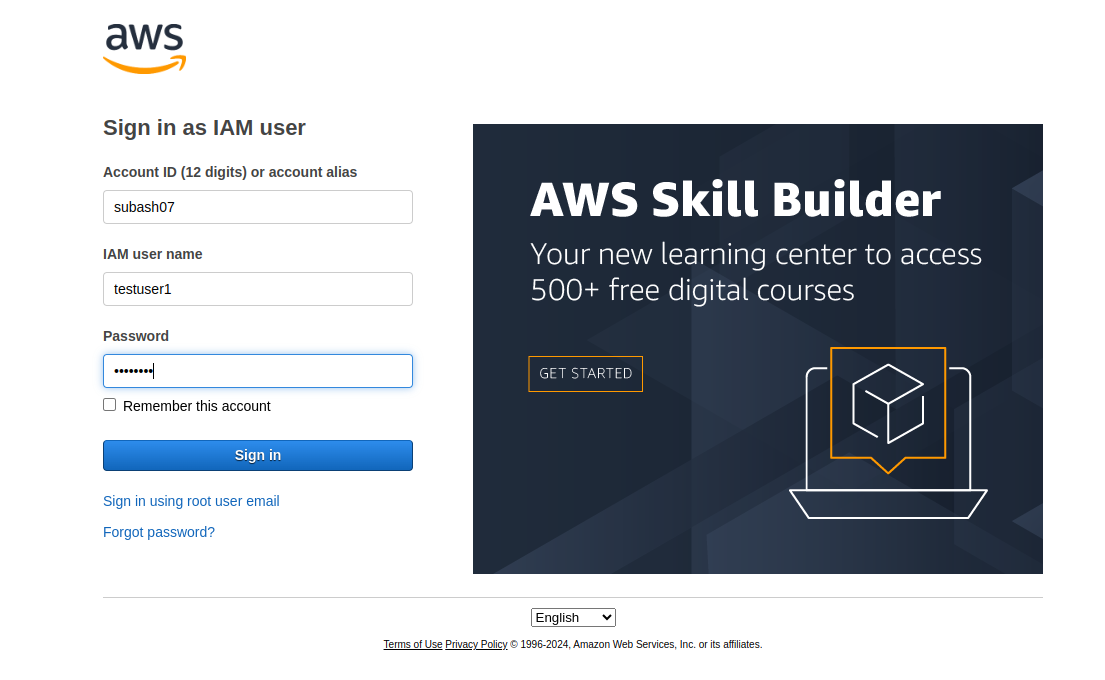
Access the S3 bucket.
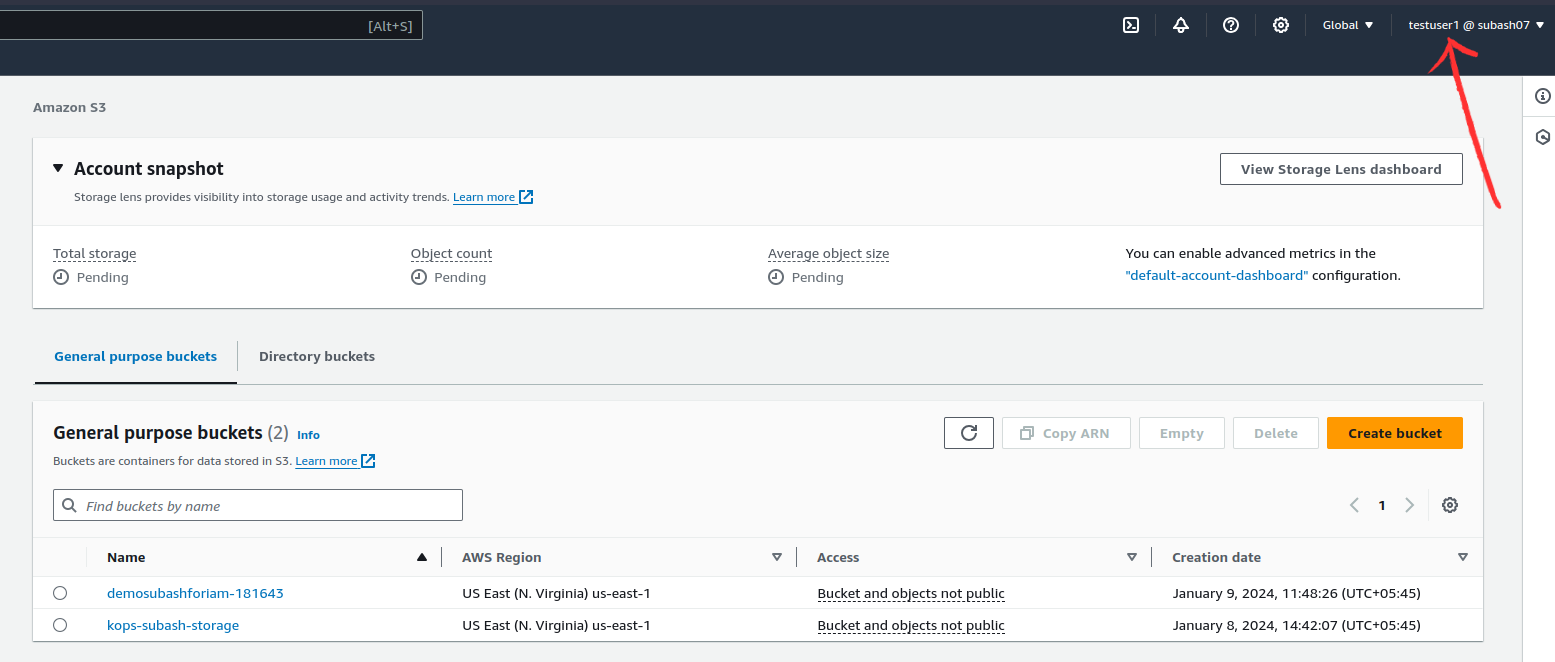
In this case, we can access the S3 buckets. Let's create a bucket as "testuser1".
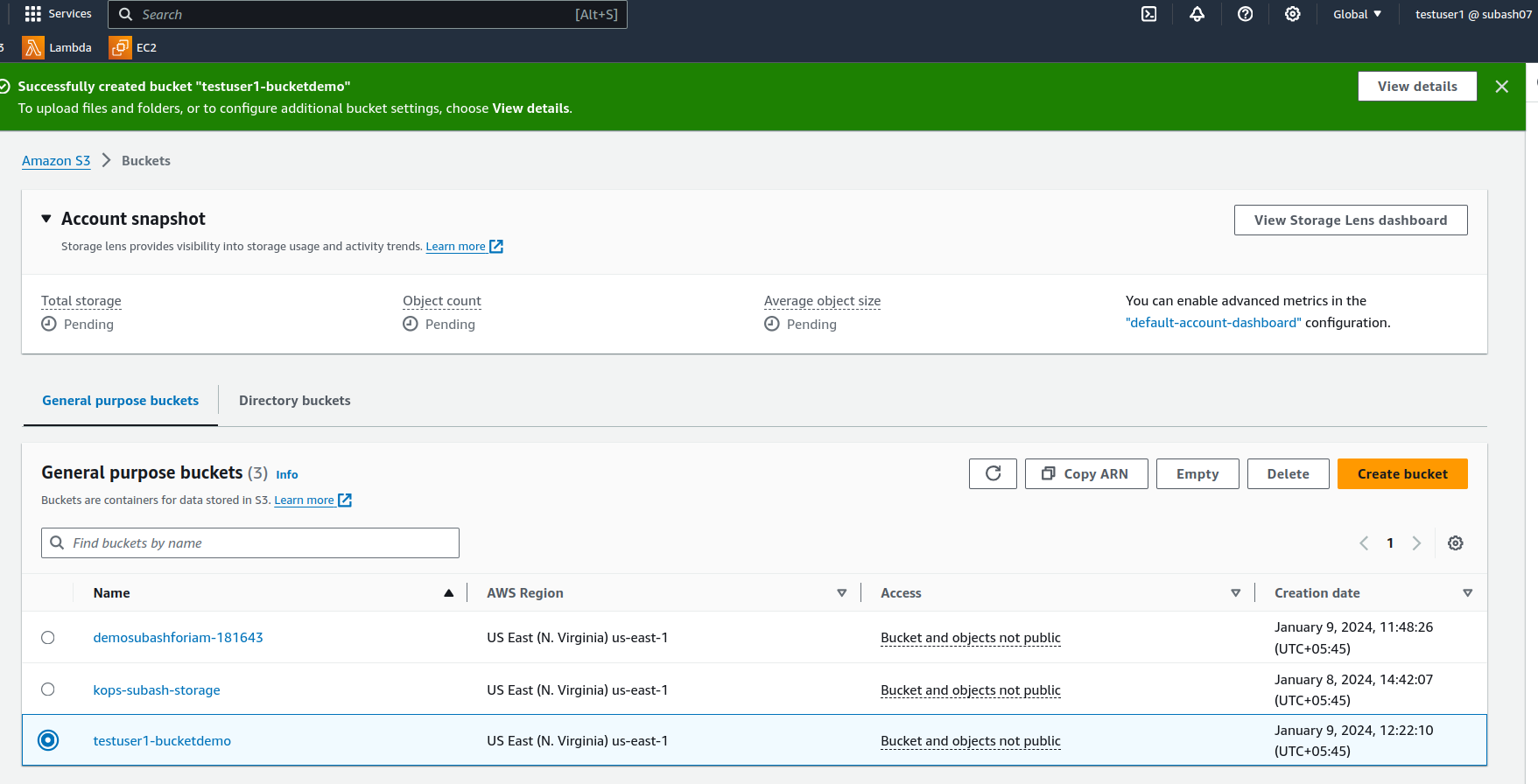
Since we have full s3 bucket access we can not only create but also delete, move, and configure the bucket permissions and securities.
From the above two users created, we have attached the different policies each time. It was just for demo but when we try to implement it at the company level then it will be the burden of work just to create the user and attach a policy to them every time. This is not an effective way to do the IAM management. So to overcome these burdens, groups are created in IAM so that similar users with the same access policy will be in the same group.
Let's create a group and explore it.
After logging in as a root user, In the search bar of AWS, search IAM > Group Users > Create Group
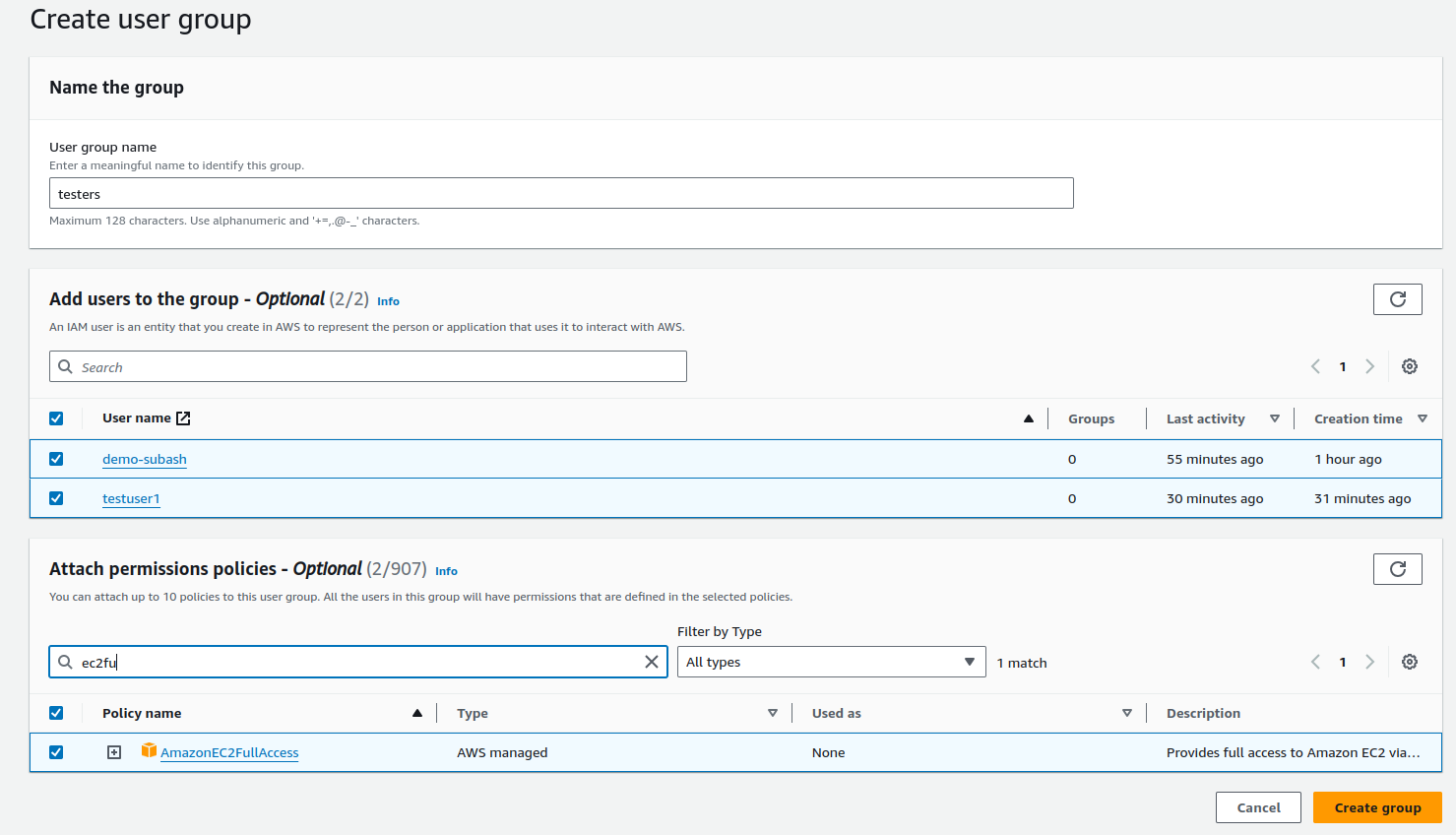
We can see we have created the group and added the users inside the group. Furthermore, we have attached the policy to the group also. We can add the users later once the group is added and customize the policies based on the requirements of users in the group.
AWS IAM is a powerful tool for securing our AWS resources. By following best practices, staying informed about new features, and regularly auditing policies, we can create a simplified access control system. Mastering IAM is not just a best practice but it's a key pillar in building a secure and scalable AWS environment.
Happy Learning!!
Subscribe to my newsletter
Read articles from Subash Neupane directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Subash Neupane
Subash Neupane
Computer Science graduate