Steganography
 Pranav Venkatesh
Pranav Venkatesh
Steganography is the practice of concealing information within other seemingly innocuous data in order to ensure its covert transmission.
Alright, imagine you have a secret message that you want to send to your friend. Now, there are two cool ways to protect your message - cryptography and steganography.
Cryptography is like putting your message in a magical box that only you and your friend have the special key to open. So, even if someone finds your box, they won't understand the message without the key. It's like having a secret code!
Steganography, on the other hand, is like hiding your message in plain sight. You could write your secret message with invisible ink on a regular piece of paper. To everyone else, it looks like a normal note, but your friend can use a special tool or trick to reveal the hidden message. It's like having a secret message hidden within something that seems ordinary!
So, in short, cryptography uses a special code to keep your message secret, and steganography hides your message so well that it's like a hidden treasure waiting to be discovered!
Exploring the Art of Concealment: A Brief Guide to Types of Steganography
Steganography, the art of hiding information in plain sight, comes in various forms, each catering to different types of data. Let's take a quick journey into the realm of steganography and uncover some of its fascinating types.
1. Image Steganography:
Concealing data within image files.
Popular technique: Least Significant Bit (LSB) replacement.
Common image formats like JPEG and PNG are often used.
2. Audio Steganography:
Hiding information within audio files.
Alters the sound imperceptibly to embed data.
FLAC, MP3, and WAV files can be carriers.
3. Text Steganography:
Secretly embedding data within text.
Techniques include modifying spacing, fonts, or using linguistic steganography.
Concealed messages within seemingly normal text.
4. Video Steganography:
Applying steganographic techniques to video files.
Challenges involve synchronization and maintaining video quality.
Concealing information within the frames of a video.
5. Digital Watermarking:
Embedding information to prove ownership or authenticity.
Often used in images, audio, and video to deter unauthorized use.
Helps in copyright protection and intellectual property.
6. Network Steganography:
Hiding information within network protocols or traffic.
Evading detection by blending with regular network activities.
A covert way of transmitting information across networks.
7. Whitespace Steganography:
Embedding data within the spaces (whitespace) of a document.
Utilizes non-printable characters or invisible spaces.
Effective for hiding information in plain text.
8. Binary and Payload Steganography:
Concealing data within the actual bits of a file (binary steganography).
In payload steganography, information is hidden in the functional part of a file, such as the code in software.
Introduction to Image Steganography:
In the vast landscape of digital communication, where images speak volumes, the art of concealing information within visual data becomes both intriguing and essential. Welcome to the world of Image Steganography, a technique that goes beyond what meets the eye. Unlike cryptography, which encrypts messages, image steganography hides them in plain sight, making it a covert and creative method of communication.
Unveiling Secrets in Pixels:
Image steganography involves the subtle manipulation of image files to embed or extract concealed information. From family photos to artistic masterpieces, images can harbor hidden messages, making them a canvas for secrecy. The methods employed can range from altering the least significant bits (LSB) of pixel values to employing advanced techniques that blend data seamlessly into the visual content.
Delving Deeper with Binary Numbers:
To understand the working of image steganography, one must first grasp the language it speaks – the language of binary numbers. In the digital realm, everything boils down to 0s and 1s, a binary code that represents the building blocks of information. The manipulation of these binary digits is the key to embedding and extracting hidden messages within images.
The Dance of 0s and 1s:
In the realm of image steganography, each pixel in an image is composed of multiple color channels, with each channel represented by a series of bits. The manipulation primarily occurs in the least significant bits (LSBs) of these channels, as altering them has minimal impact on the overall image appearance but allows for the incorporation of hidden information.
Binary Numbers
We usually use base 10 (decimal numbers), which has 10 digits: 0, 1, 2, 3, 4, 5, 6, 7, 8, 9. In base 10, the rightmost digit represents the 1s, the next digit to the left represents the 10s, the next digit to the left represents the 100s, and so on:
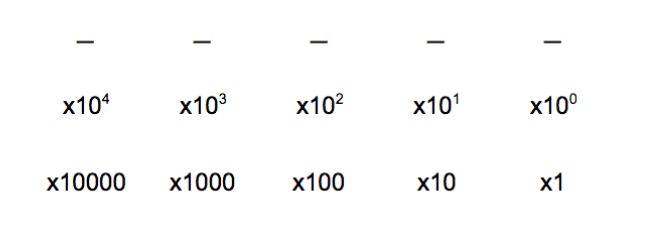
For example, the decimal number 237 is represented by 2x100 + 3x10 + 7x1, or 2x10^2 + 3x10^1 + 7x10^0 :
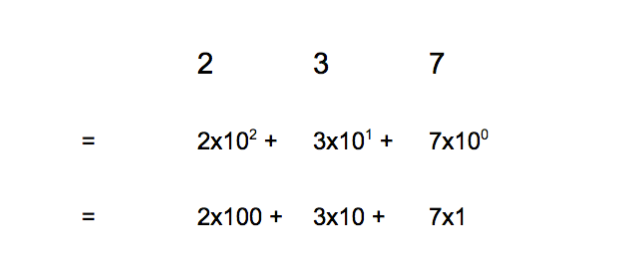
Binary numbers are numbers represented in base 2. Base 2 has just two digits: 0, 1. Base 2 works the same way as base 10, but instead of representing a power of 10, each position represents a power of 2:
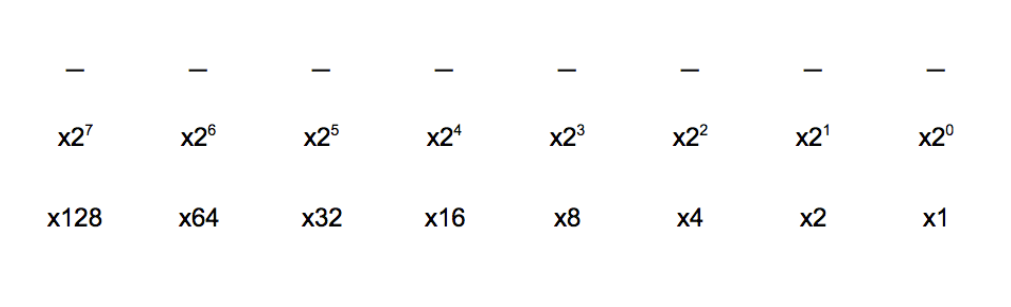
So the decimal number 237 is written in binary as:
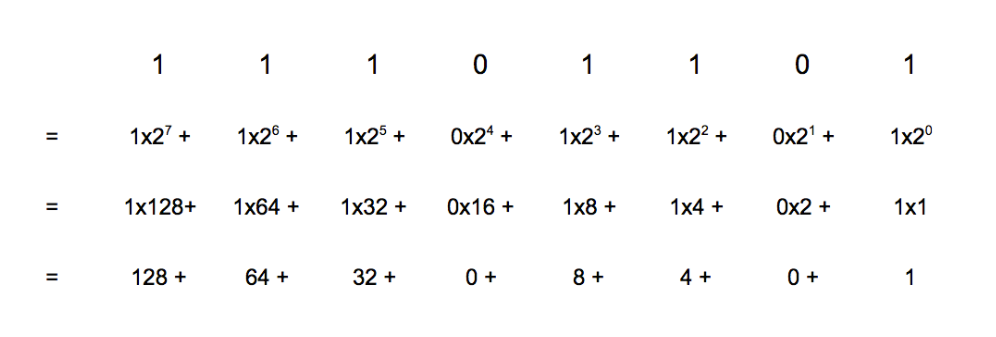
Everything in a computer is represented by a binary number—remember, everything is a number!
This is all you will need to know about binary numbers for this course, but if you would like more explanation or want to learn more, Do look at these resources:
Introduction to number systems and binary - Khan Academy
Brainstorm Question-
For color values stored as 8-bits of data, what is the maximum difference there could be between the original value in which you are hiding, and the output value with hidden data? Choose from the below options.
Hint: think about the maximum difference there could be in the least significant digits.
7
8
15
16
17
Now think for a moment .
If you think Option 3 then you're Correct!
The maximum value of four bits is 1111 = 15, and the minimum value is 0000 = 0, for a difference of 15. Try visualizing a difference of 15 with a color picker tool to convince yourself the color is not significantly different:
Click this to check out the color picker.
Pixel Clearing
Let's look at an example of clearing space in pixels using base 10 first, then think about doing the same thing using binary. Let's imagine we have a value of 4781 in the start image combining with 5236 in the hide image to give the result 4752 in the final image.
To clear the rightmost 2 digits of a 4-digit decimal number, you divide and multiply by 100, or 10^2:
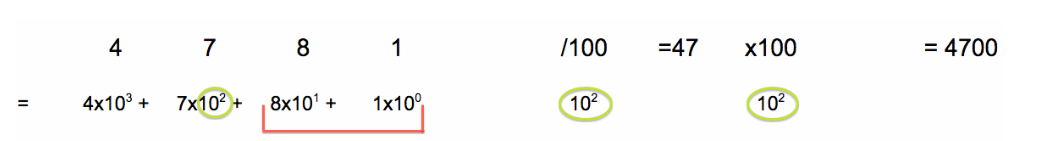
Let’s try to apply the same logic to an 8-digit binary number. We can’t use the value 4781 since the maximum value of an 8-digit binary number is 255 (1111 1111). Let’s use the binary number 1010 1010, or 170 in decimal.
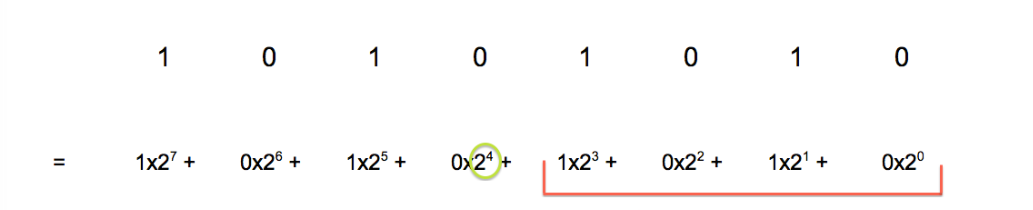
It looks like the analogous value to divide and multiply by is 2^4, or 16. This makes sense: to clear 2 digits in a base 10 number, we divided and multiplied by 10^2; to clear 4 digits in a base 2 number we divide and multiply by 2^4.
This means that if we divide the binary number 1010 1010 by the decimal number 16 we should get the binary number 1010 0000 (the left 4 digits are the same as in our original number, the right 4 digits are all 0s). Let’s check this by hand by doing the math in base 10. The binary number 1010 1010 is 170 in base 10. If we divide and then multiply 170 by 16 and then convert the answer to binary, we should get 1010 0000.
170 / 16 = 10
10 x 16 = 160
160 in binary:
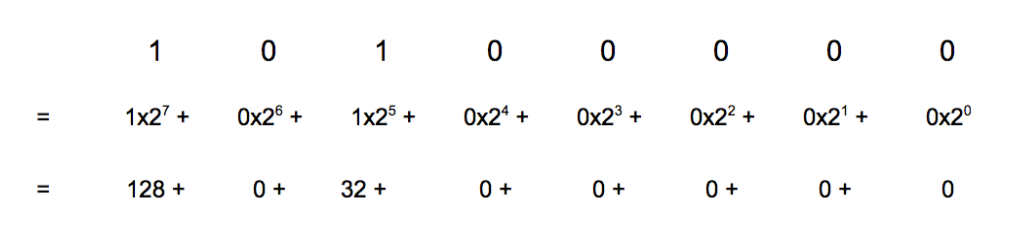
160 in binary is 1010 0000, which is what we expected.
You can also show that it works using code. I have written and run some JavaScript code to demonstrate this example. Below is the code and the output. You might find it helpful to run and play with the following code to help convince yourself that it works!
var image = new SimpleImage(1,1); //creates an image of one black pixel
var pix = image.getPixel(0,0);// gets the only pixel in the image
pix.setRed(170);// sets its red value to 170
print(image) //check that image is now 1 red pixel
var r = pix.getRed();
print(r);
r= Math.floor(r/16)*16 //divide and mul by 16
print(r) // see that it is now 160
It is important to remember that although the computer is storing binary numbers, you are writing decimal numbers in your code and see decimal numbers printed out. This is why you divide and multiply by the decimal number 16 and not the binary number 10000 (if you wrote 10000 instead of 16, the program would assume you mean the decimal number ten thousand, rather than the binary representation of the number sixteen). You can actually do this assignment without knowing anything about binary numbers as long as you know that the number to divide and multiply by is 16. However, if you want to check that the pixel values are being transformed and combined correctly, it will be helpful to understand binary numbers. It is also helpful to understand binary numbers if later you want to change the number of bits to hide the image in.
Now we have seen why you divide and multiply by 16 to clear the rightmost 4 digits in an 8-digit binary number RGB value. This is what you will do to pixels in the start image. What about pixels in the hide image? For those we want to move the leftmost 4 digits to the rightmost 4 digits and make the leftmost 4 digits 0s. You saw that with a 4-digit decimal number you can divide by 100, or 10^2:
5236 / 100 = 52
This means that with an 8-digit binary number, you can divide by 16 (2^4). So if we divide the binary number 1010 1111 by 16 we should end up with the binary number 0000 1010.
Let’s check this by hand by doing the math in base 10. The binary number 1010 1111 is 175 in base 10. If we divide 175 by 16 and then convert the answer to binary, we should get 0000 1010.
175 / 16 = 10
10 in binary:
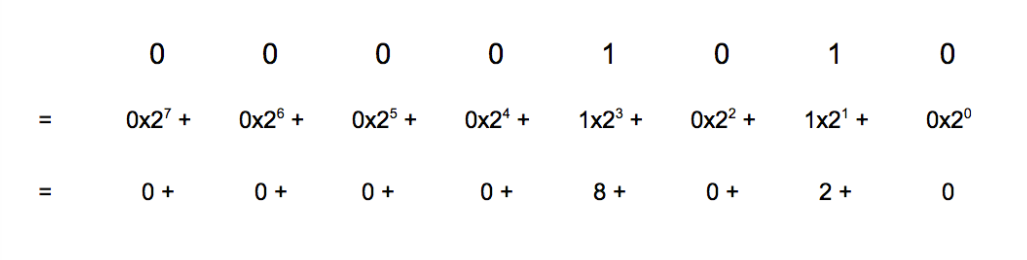
Hiding images
We have walked through how to modify one of the RGB values of one pixel in a start or hide image. How do you hide a whole image in another image?
Look at this -
var start = new SimpleImage("jpg1");
var hide = new SimpleImage("jpg2");
start = chop2hide(start);
hide = shift(hide);
var stego = combine(start,hide);
print(stego);
The basic outline of the algorithm is:
For each pixel in the start image, replace each of its red, green, and blue values with the cleared pixel value (keep the 4 leftmost digits the same, replace the 4 rightmost with 0s). This is what the line start = chop2hide(start) does. The code for the chop2hide() function is shown in the video.
For each pixel in the hide image, replace each of its red, green, and blue values by moving the 4 leftmost digits to the right and replacing the 4 leftmost digits with 0s. This is what the line hide = shift(hide) does.
Calculate the pixel RGB values in the final image by adding the values of the pixels in the modified start and modified hide images. This is what the line var stego = combine(start,hide) does.
EXAMPLE -
// Steganography DaiSwap
function clearbits(colorval){
//compute the same color value with low bits zeroed
var x = Math.floor(colorval/16)*16;
return x;
}
function chop2hide(image){
//for each pixel in image
for(var px of image.values()){
//clear low bits of the red , green and blue
px.setRed(clearbits(px.getRed()));
px.setGreen(clearbits(px.getGreen()));
px.setBlue(clearbits(px.getBlue()));
}
return image;
}
function shift(image){
//similarly , for each pixel in the image
for(var px of image.values()){
//shift the red,green and blue bits over
px.setRed(px.getRed()/16);
px.setGreen(px.getGreen()/16);
px.setBlue(px.getBlue()/16);
}
return image;
}
function combine(show,hide){
// make new image the same size as "show"
var answer = new SimpleImage(show.getWidth(),show.getheight());
for(var px of answer.values()){
var x = px.getX();
var y = px.getY();//get X and Y of that pixel
var showPixel = show.getPixel(x,y);
var hidePixel = hide.getPixel(x,y);
px.setred(showPixel.getRed()+hidePixel.getRed());
px.setGreen(showPixel.getGreen()+hidePixel.getGreen());
px.setblue(showPixel.getblue()+hidePixel.getBlue());
//Set RGB of px to sum of showpixel and hidepixel
}
return answer;
}
var start = new SimpleImage("any jpg1");
var hide = new SimpleImage("any jpg2");
start = chop2hide(start);
hide = shift(hide);
var stego = combine(start,hide);
print(stego);

Steganography Unveiled: Real-world Applications
Digital Watermarking:
In the dynamic digital landscape, protecting intellectual property has become paramount, and digital watermarking, a specialized form of steganography, emerges as a powerful tool.
What is Digital Watermarking?
Digital watermarking involves embedding imperceptible information within digital content, serving as an invisible identifier. Unlike overt branding, digital watermarks are subtle, hidden within images, audio, or videos, enabling content owners to assert ownership and trace unauthorized usage.
Applications of Digital Watermarking:
Media Authentication:
- Content creators embed watermarks to authenticate their work, ensuring it hasn't been tampered with or used without permission.
Copyright Protection:
- Artists, photographers, and musicians utilize digital watermarks to safeguard their creative works, discouraging unauthorized duplication or distribution.
Ownership Tracing:
- Watermarks act as a unique fingerprint, aiding in tracing the origin of leaked or pirated content back to its source.
Transaction Verification:
- In digital transactions, such as stock imagery sales, digital watermarks provide proof of ownership, reducing disputes and ensuring fair compensation.
Document Security:
- For sensitive documents, digital watermarks help establish authenticity and prevent unauthorized alterations.
Brand Protection:
- Companies employ watermarks to protect their logos and branding assets, thwarting counterfeit activities.
Digital watermarking, as a form of steganography, plays a pivotal role in preserving the integrity and ownership of digital assets in an increasingly interconnected world.
Security and Privacy:
Steganography, with its ability to conceal information, finds a multifaceted application in enhancing both security and privacy.
Enhancing Security:
Covert Communication:
- Security agencies employ steganography to transmit sensitive information covertly, ensuring secure communication channels.
Data Concealment:
- Confidential data can be hidden within seemingly innocuous files, thwarting unauthorized access and maintaining the confidentiality of critical information.
Evasion of Detection:
- Steganography aids in evading detection by blending encrypted data within common files, making it challenging for adversaries to identify and intercept.
Safeguarding Privacy:
Private Messaging:
- Individuals can use steganography to conceal private messages within media files, adding an extra layer of privacy to their communication.
Personal Data Protection:
- Concealing sensitive information within files ensures an added level of protection against unauthorized access or data breaches.
Anti-Surveillance Measures:
- In environments where surveillance is a concern, steganography provides a means to exchange information without raising suspicion.
Ethical Considerations and Legal Implications:
While steganography offers valuable tools for security and privacy, ethical considerations and legal implications cannot be ignored.
Ethical Use:
- Responsible and ethical use of steganography is crucial to prevent misuse for malicious purposes or to facilitate illegal activities.
Legal Frameworks:
- Legal systems around the world may have varying perspectives on the use of steganography. Understanding and adhering to applicable laws is essential.
Informed Consent:
- The use of steganography should align with principles of informed consent, ensuring that all parties involved are aware of and agree to the concealment of information.
In conclusion, while steganography serves as a powerful ally in securing information and preserving privacy, its ethical application and adherence to legal frameworks are imperative to maintain a delicate balance between innovation and responsibility in the digital realm.
Conclusion:
Steganography, in its various forms, continues to be a captivating field where creativity meets technology. From images and audio to text and videos, the ways to hide information are as diverse as the data itself. Understanding these types allows us to appreciate the depth of this ancient art, which has seamlessly transitioned into the digital age, offering both challenges and innovative solutions. As we navigate this concealed world, it's essential to recognize the balance between security measures and the ever-evolving techniques of information concealment.
Subscribe to my newsletter
Read articles from Pranav Venkatesh directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Pranav Venkatesh
Pranav Venkatesh
Mathematics & Computing enthusiast diving into the realms of algorithms, machine learning, quantum computing, and blockchain. Exploring the infinite possibilities of Web 3.0. Join me in unraveling the mysteries of numbers and codes! 🌐✨ #Mathematics #Computing #MachineLearning #Quantum #Blockchain #Web3