Exploring InsightIDR by Rapid7: A Modern SIEM Solution — Part 1: An In-Depth Overview
 Awais Sajid
Awais Sajid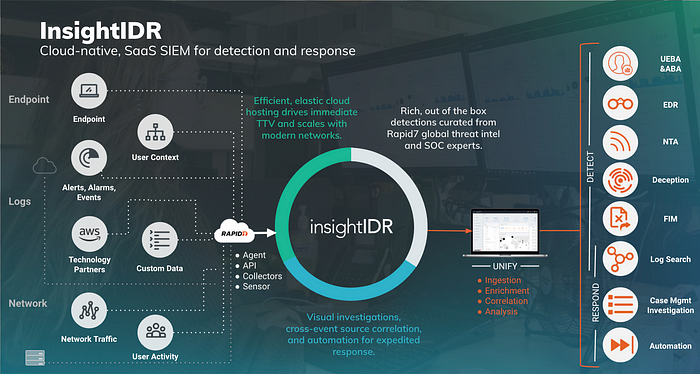
Rapid7’s InsightIDR is a powerful tool for keeping an eye on security incidents, checking who’s logging in, and watching over network devices, all part of what’s called XDR. It quickly spots any unauthorized or suspicious actions, saving you the trouble of looking through tons of data. XDR helps catch and respond to threats faster and better. InsightIDR is built for the cloud, meaning it can handle lots of different security information easily. Learn more about XDR on Rapid7’s blog.
InsightIDR combines the full power of endpoint forensics, log search, and sophisticated dashboards into a single solution. It is a Software as a Service (SaaS) tool that collects data from your existing network security tools, authentication logs, and endpoint devices. InsightIDR then aggregates the data at an on-premises Collector or a dedicated host machine that centralizes your data.
InsightIDR brings together advanced endpoint forensics, easy log search, and powerful dashboards in one tool. As a cloud-based service, it pulls data from your network security tools, login records, and network devices. This data is first collected on-site or on a central machine, which then sends it securely to Amazon Web Services (AWS). Here, Rapid7 analyses the data to connect the dots between users, accounts, logins, alerts, and access rights. This helps in understanding user behavior and spotting potential security breaches.
Rapid7 suggests using on-site Collectors for gathering all types of event and endpoint data. For up-to-the-minute data from your devices, you should install the Insight Agent on them.
Starting with InsightIDR
Choose from three InsightIDR packages to fit your security needs: Essential, Advanced, and Ultimate. For each, we have easy-to-follow Quick Start Guides. Pick the one for your chosen version!
InsightIDR Essential: A basic tool for managing security incidents and events, helping you meet compliance needs.
InsightIDR Advanced: A key tool for managing security incidents and events, focusing on detection and response.
InsightIDR Ultimate: A comprehensive tool for managing security incidents and events, offering extended detection and response (XDR).
Unsure about which Quick Start Guide is for you?
If you purchased InsightIDR (not designated as Essential, Advanced, or Ultimate), please follow InsightIDR Quick Start Guide | Advanced for tasks and materials suited to your product.
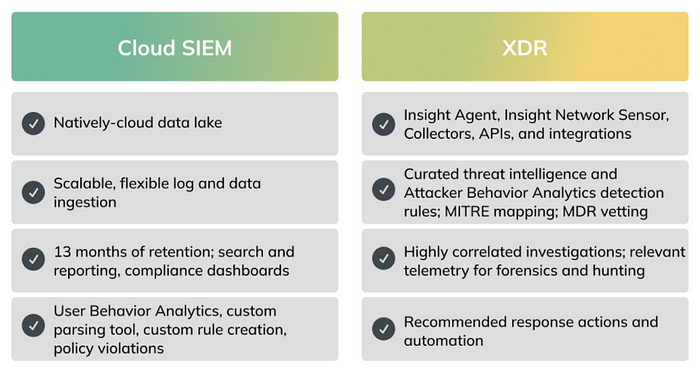
InsightIDR is your CloudSIEM for Extended Detection and Response
InsightIDR — Rapid7’s natively cloud Security Information and Event Monitoring (SIEM) and Extended Detection and Response (XDR) solution — delivers accelerated detection and response through:
A frictionless deployment experience
Intuitive SaaS interface
Comprehensive environment visibility
Expertly vetted detections
Embedded threat intelligence
Powerful investigation tools
Automated response capabilities
XDR unifies and transforms relevant security data from across your modern environment to detect real attacks and provide security teams with high-context, actionable insights to investigate and extinguish threats faster.
InsightIDR helps customers achieve SIEM and XDR outcomes
Why Choose InsightIDR?
InsightIDR stands out by consolidating various data sources into a comprehensive security perspective, offering user-friendly features:
Unified Security View: Track user activities across networks, devices, and cloud services. InsightIDR normalizes this data, showing you who did what and when.
Analyze Diverse Data Sources: It gathers data from everywhere, allowing you to examine logs, study endpoint data, or organize network traffic easily.
Alerts for Suspicious Activities: InsightIDR not only detects unusual activities but also sets traps to alert you about potential security breaches.
Prioritize Important Events: It sorts through the noise, highlighting crucial events and filtering out less critical ones for efficient focus.
Investigate Breaches: In case of a breach, you get detailed context about the compromised data, timing, and possible intruder actions.
Monitor Security Operations: The dashboard turns your data into actionable insights, helping in responding to alerts, tracking threat trends, and evaluating your security team’s effectiveness.
InsightIDR in Use InsightIDR is used by various operational departments, especially Information Security (InfoSec) teams, for daily network protection. InfoSec teams may use InsightIDR to:
Investigate alerts and confirm suspicions.
Review incident details like timing, user activities, and involved assets.
Use Watchlists and Restricted Asset lists to track users and assets.
Search logs and review firewall activities or IP addresses for deeper context.
Incident Response InsightIDR helps InfoSec teams differentiate between false alarms and actual threats. In response to serious threats, teams can either wipe and reinstall assets or, in extreme cases, completely destroy irreparable assets.
Detailing of the Rapid7
- InsightIDR leverages Windows Management Instrumentation (WMI) to query the Active Directory Domain Controllers for the Security Event logs with an Admin account. It also leverages Distributed Component Object Model (DCOM) technology to handle the remote calls to the Domain Controllers.
Using the WMI protocol
For logs collected using the WMI protocol, access is required through an admin account and communication occurs over ports 135, 139 and 445. When strict networking rules do not permit communication over ephemeral ports, which are used by WMI, you may need to set up a fixed port. You can read about ephemeral ports here.
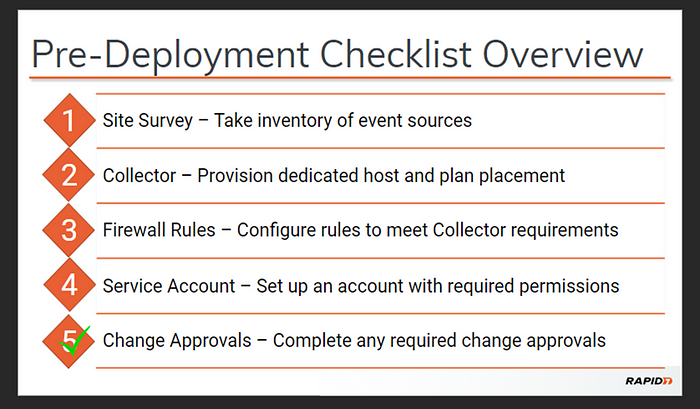
Pre-Deployment Checklist:
Collector:
The Collector is the on-premises component of InsightIDR, or a machine on your network running Rapid7 software that either polls data or receives data from Event Sources and makes it available for InsightIDR analysis. An Event Source represents a single device that sends logs to the Collector.
Advantages of the Collector
The Collector workflow has two main advantages over sending logs to InsightIDR directly: normalization and user attribution.
Normalization
Normalization transforms log data from multiple diverse sources into a common JSON format and extracts standard information such as hostnames, timestamps, and error levels. Normalization allows you to run more advanced queries on your endpoint logs and enhance your data visualization.
User Attribution
User attribution correlates endpoint activity to individual users using that endpoint while logged into applications. Attribution provides a fuller image of your security posture because user accounts are the most common targets for sophisticated attacks.
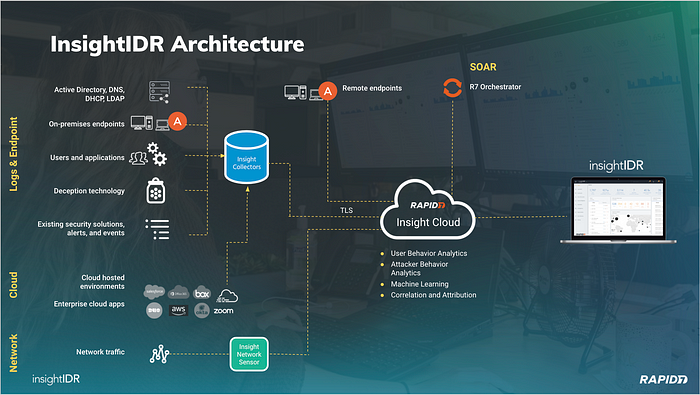
InsightIDR is a cloud-native security solution. Of course, this does not mean that everything runs in the cloud, because you will also need to do something on-premises to be able to collect log data from different systems.
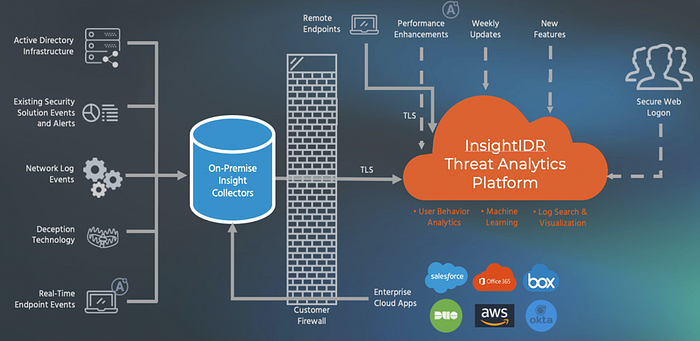
The advantage of such an architecture is that the collection and encryption of log data takes place on-premises, while the correlation and analysis of the data is done in the cloud. This eliminates the need for heavy servers with lots of processing power to quickly search through log data and the need to continuously schedule software updates to have the latest threat intelligence feeds.
InsightIDR Event Sources
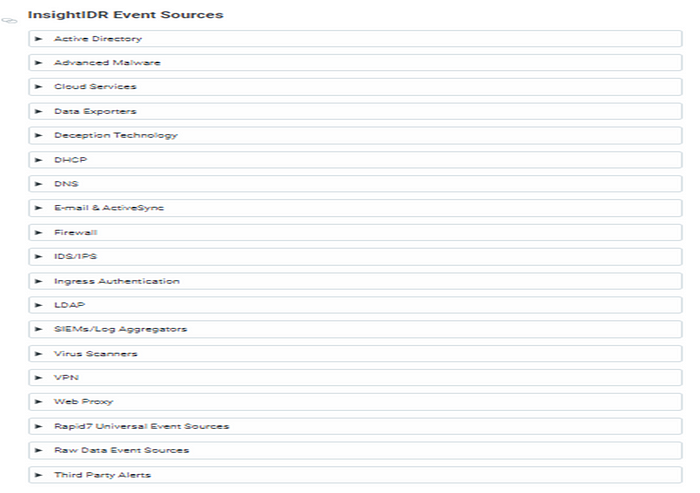
InsightIDR has the ability to automatically discover and configure certain sources (Active Directory via WMI; LDAP; Microsoft DHCP and DNS via Network Shares) in your environment. Auto configure is especially helpful with core event sources, as the core user attribution engine can be setup in just a few minutes.
You can run the auto-configure feature just to discover event sources without configuring those event sources themselves. This practice can be helpful to discover any newly deployed servers in your environment that haven’t been configured for monitoring.
Agent Installation
You can install the Insight Agent on your target assets using one of two distinct installer types. While both installer types functionally achieve the same goal.
Token-Based Installer (Preferred)
Certificate Package Installer (Legacy)
How the Certificate Package Works
The certificate package installer comes in the form of a ZIP file that also contains the necessary certificates that pertain to your organization. Since these dependencies come in the ZIP file itself, the installer does not rely on the Insight Platform to retrieve them. However, this also means that you must properly locate the installer with its dependencies in order for the installation to complete successfully.
SIEM Challenges
One of the biggest challenges in most SIEM implementations is writing detection rules: after you have connected various systems to your SIEM and ensured that all log data is collected in one central location, how does the SIEM make sense of the incoming log data? With traditional SIEM solutions, use cases or detection rules need to be written for each event. InsightIDR does this differently.
1. InsightIDR comes standard with about 900 ready-made detection rules based on the MITRE ATT&CK Framework.
2. Because InsightIDR is a cloud solution, new detection rules for new attack methods can be added in real-time by the Rapid7 Security Operations Centre (SOC) to customer InsightIDR tenants.

InsightIDR is equipped with detection rules that cover the behaviour of users, endpoints, servers, peripherals and even network traffic. Once you have connected the 3 mandatory log sources — LDAP, Active Directory and DHCP — you can easily connect all desired IT / Security systems to InsightIDR.
Subscribe to my newsletter
Read articles from Awais Sajid directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Awais Sajid
Awais Sajid
As a Cybersecurity student passionate about Hacking and Blockchain security, I strive to develop innovative solutions to protect against emerging threats.