Exploring InsightIDR by Rapid7: A Modern SIEM Solution — Part 3: MITRE Attack Framework
 Awais Sajid
Awais SajidUnveiling the synergy between a leading-edge SIEM solution and a strategic cybersecurity model to enhance enterprise defense mechanisms.
InsightIDR and the Pyramid: An Elevation in Defense
Rapid7’s InsightIDR stands at the forefront of this challenge, offering a Security Information and Event Management (SIEM) solution that is not just reactive but proactive. How does InsightIDR leverage the Pyramid of Pain to fortify its defenses?
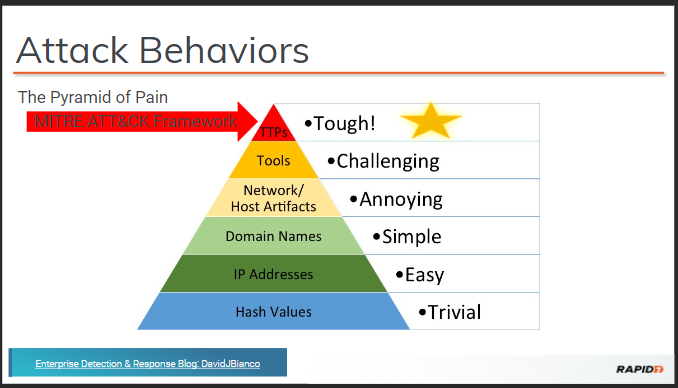
Hash Values:
Easily Altered, Yet Not Overlooked
InsightIDR transcends basic hash recognition, employing advanced analytics to identify malware variants. Its threat intelligence goes beyond static indicators, rendering attackers’ quick fixes ineffective.
IP Addresses:
Dynamic Yet Detectable
IP addresses are simple for attackers to change, but InsightIDR’s user behavior analytics (UBA) technology monitors for anomalies linked to these IPs, recognizing patterns that traditional tools miss.
Domain Names:
A Test of Persistence
InsightIDR’s correlation of domain names with known malicious entities adds a layer of defense, making it more than a nuisance for adversaries attempting to bypass security measures.
Network/Host Artifacts:
Annoyingly Persistent for Intruders
InsightIDR excels in detecting residual artifacts in network and host systems, leveraging this intel to uncover stealthy attack methods and persistent threats.
Tools:
Unveiling the Attacker’s Arsenal
By analyzing the tools used in an attack, InsightIDR provides insights into the operational aspects of threats, enabling teams to disrupt attack chains before they mature.
TTPs:
Difficult to Mimic, Harder to Change
InsightIDR’s integration with the MITRE ATT&CK Framework offers a strategic vantage point, mapping detected activities to known adversary behaviors. This alignment makes it tough for attackers to adapt without significant overhauls to their methodologies.
What is MITRE Attack ?

InsightIDR ATT&CK Data Sources:
Processes:
- Collected via Insight Agent
Command line:
- Collected via Insight Agent
Authentication Logs:
Domain Controller
Endpoint logs using Insight Agebt
Network Traffic:
- Collected via network flow data collected between internal and external hosts.
Subscribe to my newsletter
Read articles from Awais Sajid directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Awais Sajid
Awais Sajid
As a Cybersecurity student passionate about Hacking and Blockchain security, I strive to develop innovative solutions to protect against emerging threats.