TR-069 Demystified: Understanding the Protocol Inside Out
 Friendly Technologies
Friendly Technologies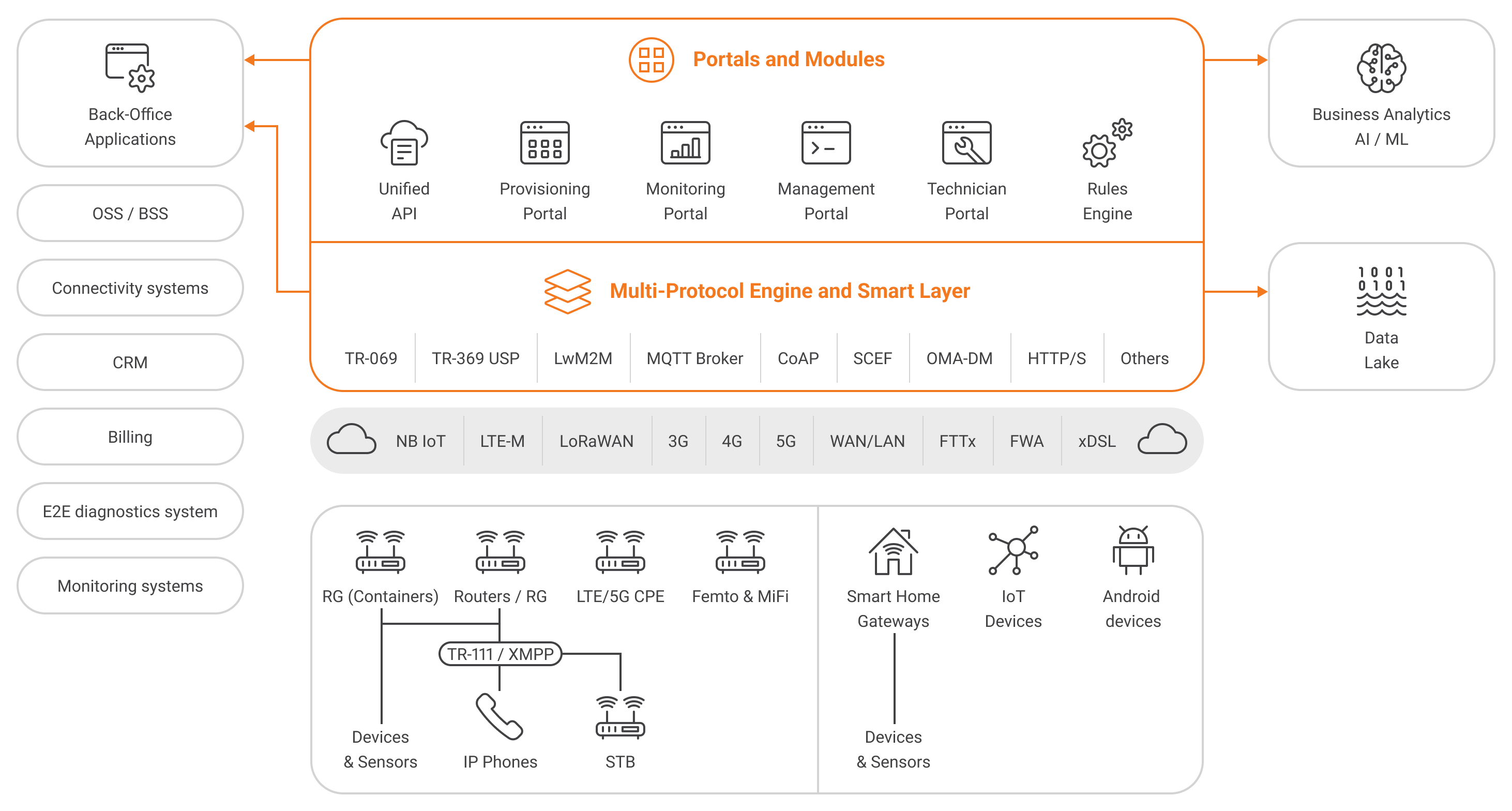
In the ever-evolving landscape of networking technologies, it stands out as a crucial protocol that plays a pivotal role in the management and provisioning of devices remotely. This aims to demystify TR-069, providing a comprehensive understanding of the protocol and its significance in the realm of telecommunications and beyond.
Origin and Evolution of TR-069:
TR-069, short for Technical Report 069, is a protocol defined by the Broadband Forum. It emerged in response to the need for a standardized approach to manage Customer Premises Equipment (CPE) remotely. The protocol has evolved over the years, with multiple versions enhancing its capabilities and security features.
Key Components of TR-069:
TR-069 consists of a client-server architecture. The "CPE WAN Management Protocol" (CWMP) defines the communication between the Customer Premises Equipment (CPE) and the Auto Configuration Server (ACS). The CPE, often a router or a modem, implements the client side, while the ACS is responsible for managing and configuring these devices remotely.
Functionality and Operations:
TR-069 facilitates a wide array of operations, including configuration, software/firmware updates, and performance monitoring. It allows service providers to remotely manage and troubleshoot devices, ensuring a seamless and efficient network operation. The protocol standardizes the methods and parameters used for communication, fostering interoperability among different vendors' equipment.
Security Measures in TR-069:
As remote device management involves sensitive information, security is a paramount concern. TR-069 employs various security mechanisms such as secure communication channels (HTTPS), authentication, and access control. These measures ensure that only authorized entities can access and manipulate device configurations.
Use Cases and Applications:
TR-069 finds applications in a multitude of scenarios. Internet Service Providers (ISPs) use it to remotely configure and manage customer routers and modems. This protocol is also prevalent in the Internet of Things (IoT) ecosystem, where it aids in the efficient management of diverse devices connected to the network.
Challenges and Concerns:
While TR-069 offers numerous benefits, it's not without challenges. Some concerns include potential security vulnerabilities if not properly implemented, interoperability issues between different implementations, and the need for careful consideration of privacy concerns, especially when dealing with sensitive customer data.
Conclusion:
In conclusion, TR-069 is a foundational protocol that empowers service providers to remotely manage and configure customer premises equipment. Its standardized approach ensures interoperability and facilitates a wide range of operations crucial for maintaining a robust network infrastructure. As technology continues to advance, understanding it becomes increasingly important for telecommunications professionals and those involved in the deployment and management of connected devices.
By demystifying TR-069 and shedding light on its key components, functionality, security measures, use cases, and challenges, this article aims to provide a comprehensive insight into the protocol. As the digital landscape continues to evolve, it remains a key player in the efficient and secure management of devices, contributing to the seamless operation of modern networks.
Subscribe to my newsletter
Read articles from Friendly Technologies directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
