Amazon VPC for Secure and Scalable Infrastructures
 Subash Neupane
Subash Neupane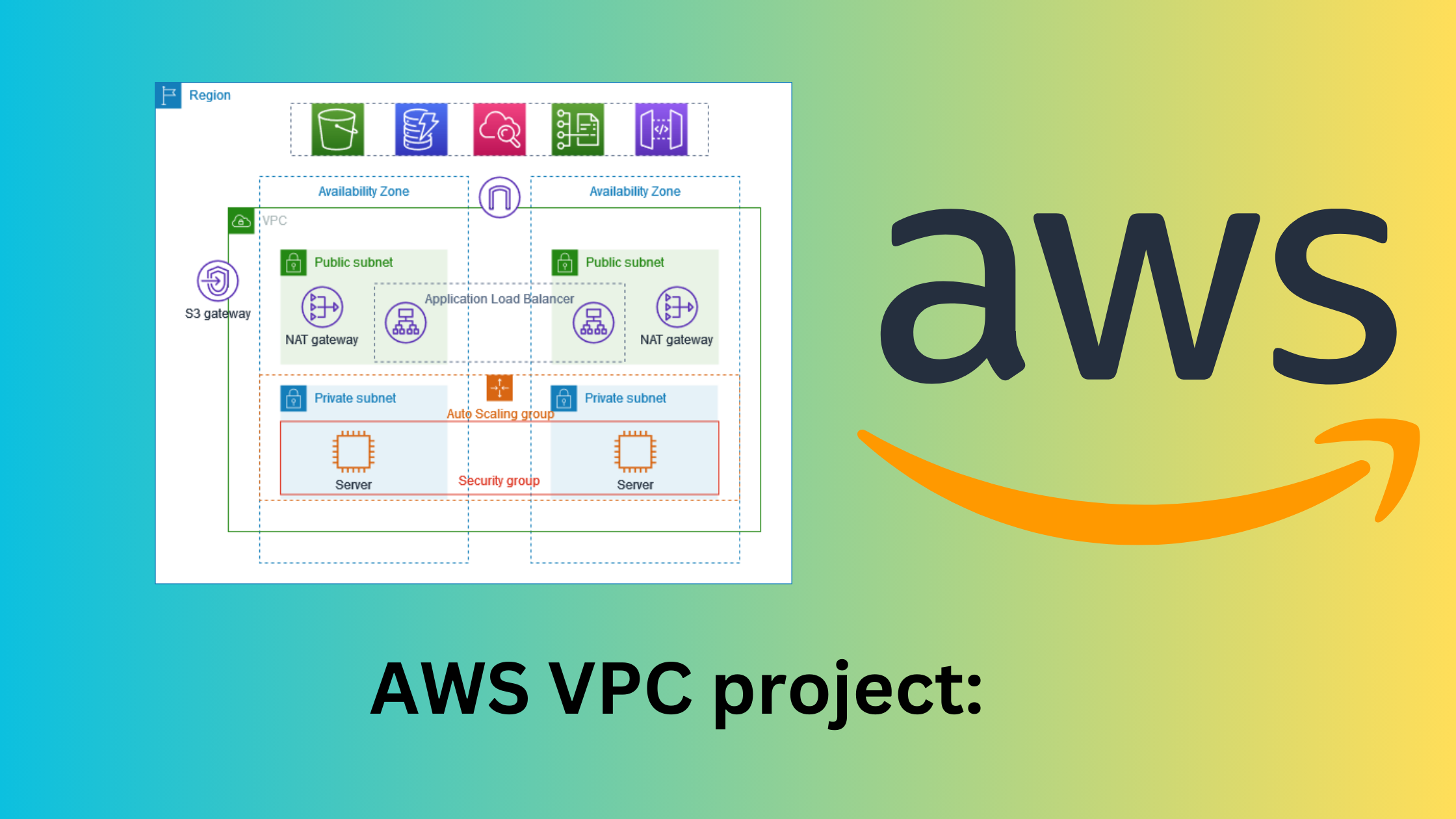
In this blog, we will deep dive into one of the important services of AWS i.e. VPC. VPC is abbreviated as the Virtual Private Network.
Virtual Private Clouds (VPCs) have become a major factor in building scalable and secured infrastructures. It provides a way to create isolated and customizable networks within the cloud environment, offering businesses the flexibility and control they need. In this blog post, we will delve into the components that make up a Virtual Private Cloud and explore how they work together to create a robust and secure networking foundation.
Why do we need VPC?
Isolation and Security
Customization of Network Architecture
Scalability
Hybrid Cloud Connectivity
High Availability and Fault Tolerance
Components of VPC
VPC: The VPC itself is the top-level container that holds all other components. It is a logically isolated section within the cloud where users can deploy their resources and make it more secure. VPCs allow any organization or users to define their IP address range, route tables, and subnets.
Subnets: Subnets are subdivisions of a VPC and are associated with a specific availability zone. Subnets allow us to isolate and group resources based on the user's needs.
Route Tables: Route tables define the rules for routing traffic within the VPC. Each subnet is associated with a route table, determining how traffic is directed. Route tables control the flow of traffic between subnets and the internet, ensuring proper communication.
Internet Gateway (IGW): The Internet Gateway is a component that facilitates communication between instances within the VPC and the Internet. It acts as a gateway for outbound and inbound traffic, allowing instances to access the internet and be accessed from the internet.
Network Access Control Lists (NACLs): NACLs are stateless filters that control traffic at the subnet level. They act as a firewall, allowing or denying traffic based on rules defined by the user. NACLs are operated at the subnet level and provide an additional layer of security.
Security Groups: Security Groups are stateful firewalls that operate at the instance level. They control inbound and outbound traffic for instance by defining rules.
Elastic Load Balancer (ELB): ELB is a service that automatically distributes incoming application traffic across multiple targets, such as EC2 instances, in multiple availability zones.
Virtual Private Network (VPN) and Direct Connect: VPN establishes a secure tunnel over the public internet, while Direct Connect provides a dedicated network connection.
Elastic IP Addresses: Elastic IP addresses provide a persistent IP address that remains associated with an instance, even if it is stopped and restarted.
Peering Connections: VPC peering allows the connection of two VPCs, enabling them to communicate with each other as if they are within the same network. It is useful when resources from different VPCs need to interact.
Now we know the basic terminologies that are used at the VPC level. Its time for us to practically implement and know the usage of AWS VPC services.
Search VPC > click on VPC > create VPC
In clicking Create VPC, you will be prompted to fill in the details below:
Resources to creat : VPC and more
Name tag auto-generation: aws-prod-project
IPv4 CIDR block**:** default
IPv6 CIDR block: No ipv6
Tenancy: default
Number of Availability Zones (AZs): 2
Number of public subnets:2
Number of private subnets:2
NAT gateways : 1 per AZ
VPC endpoints: None
Then click on Create VPC
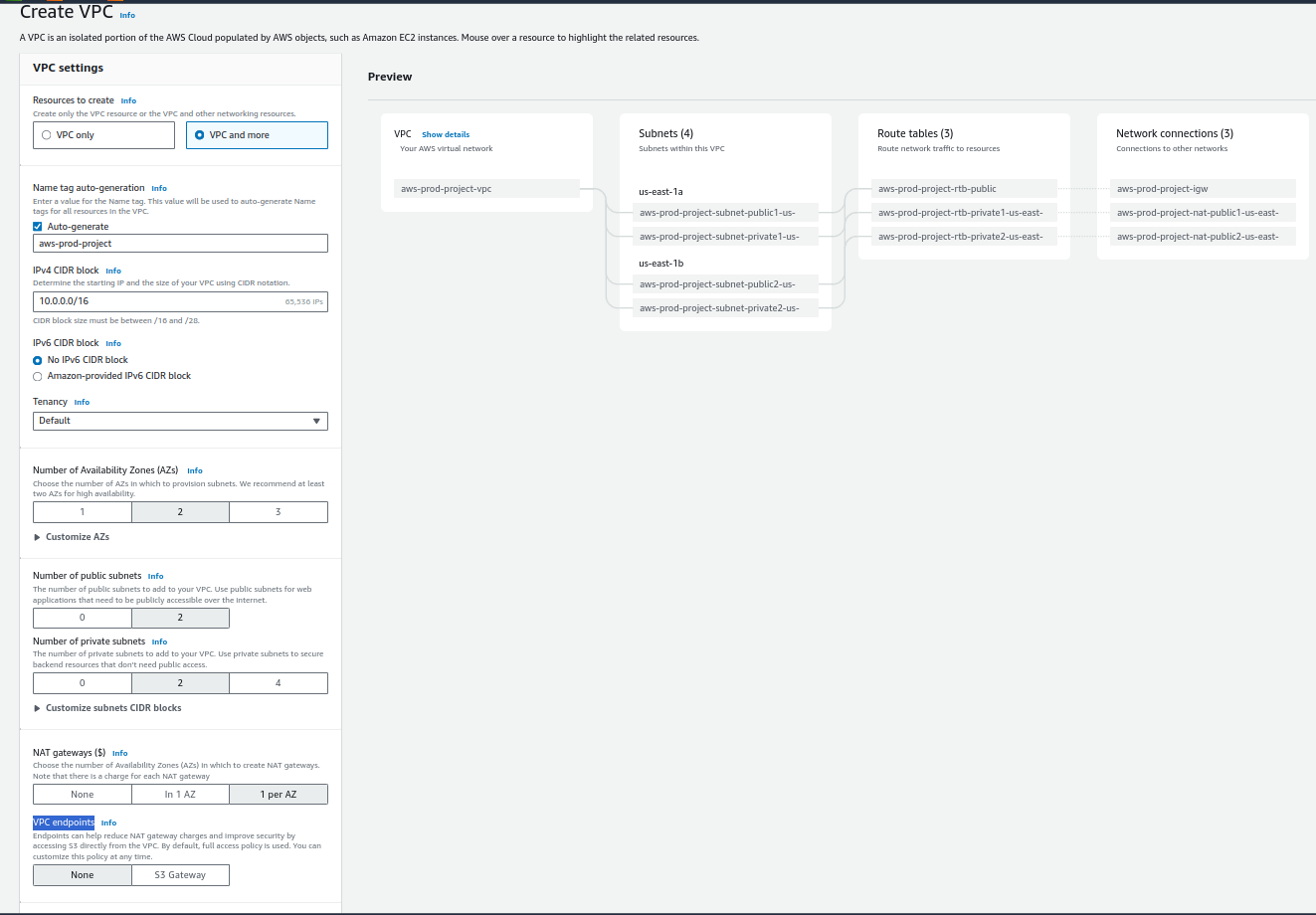
This is the configuration that I have done.
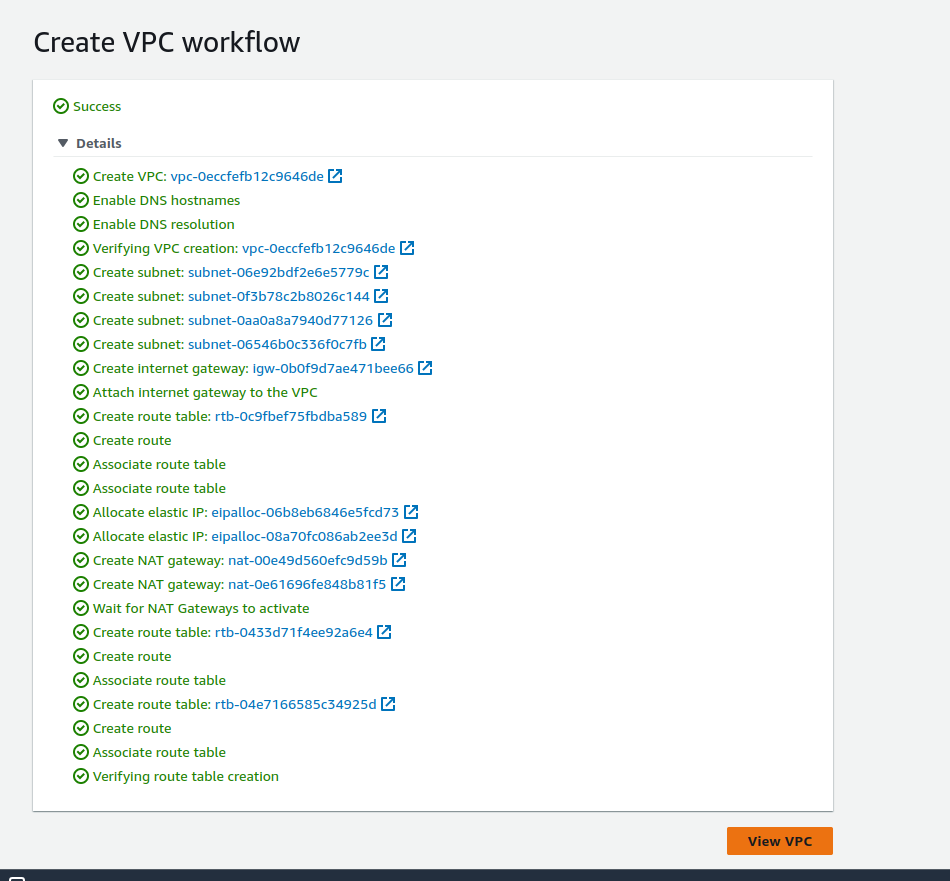
Our VPC is successfully created
Create ec2 with the autoscaling group
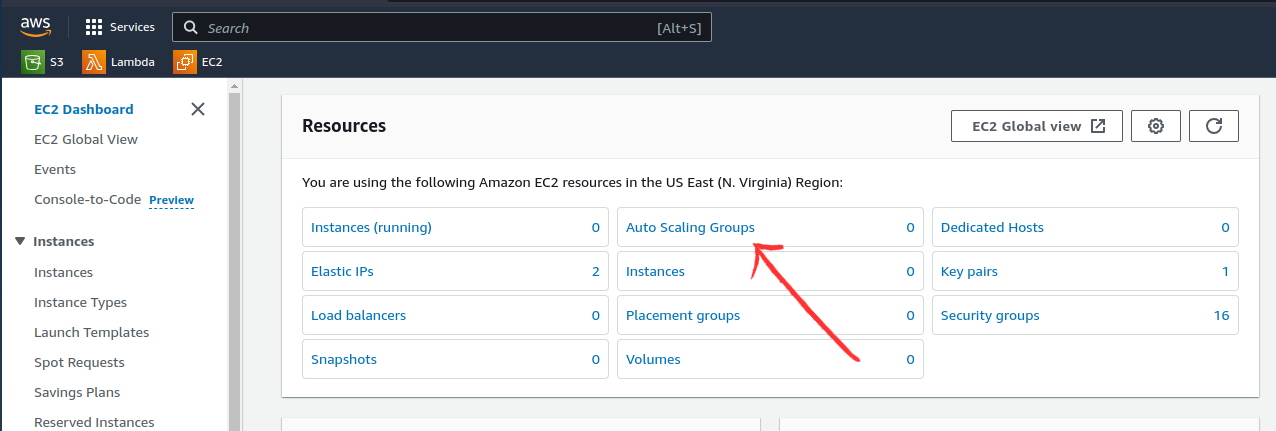
In AWS autoscaling group cannot be created directly, we need to choose Create Launch Template.
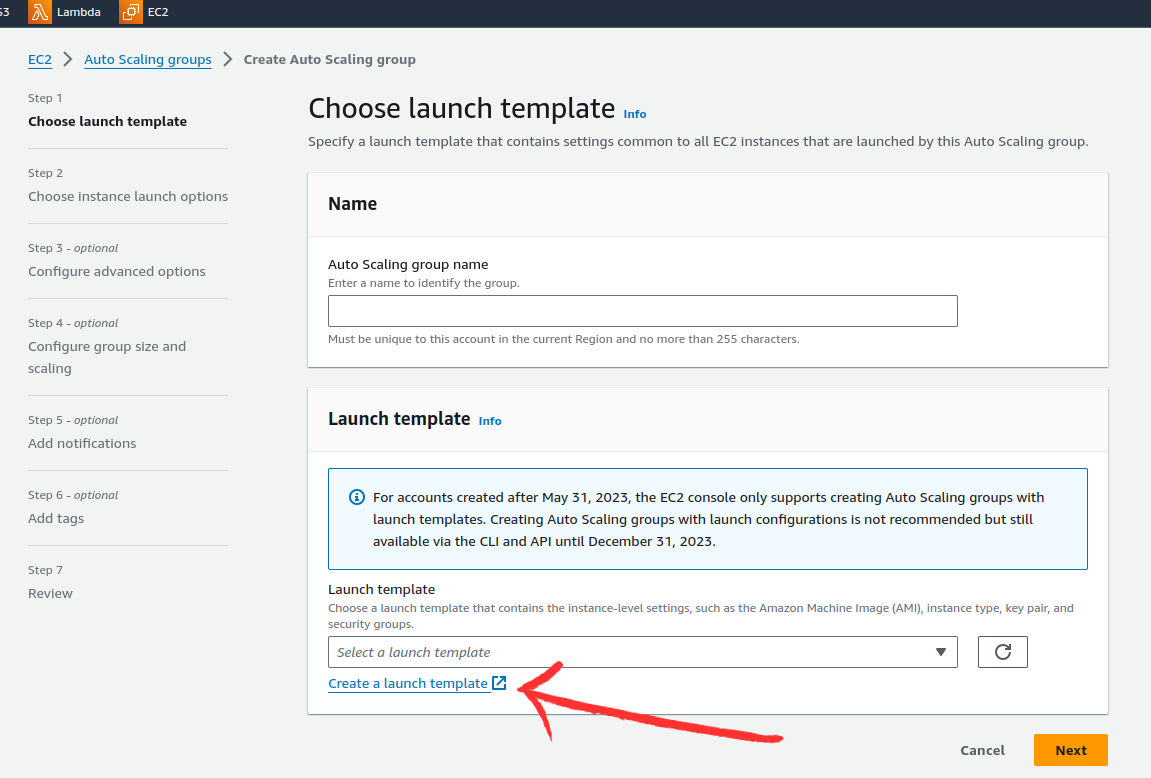
In the launch template page,enter the required details
Launch template name - required: aws-demo-proj
Template version description: describe the template
Application and OS Images (Amazon Machine Image) - required: choose any supposed Ubuntu
AMI: Free tier
instance type: t2.micro (Free Tier)
key pair: use existing or create a new key pair
In Network settings, subnet: default (do not change)
Firewall (security groups): create a security group
-Add a security group name, description
VPC: Choose a newly created VPC
Inbound Security Group Rules: add 2 rules ssh(to access ec2 instance) and custom TCP (port 8000 to access the application)
Remaining all as it is (Default)
Click Create Launch Template
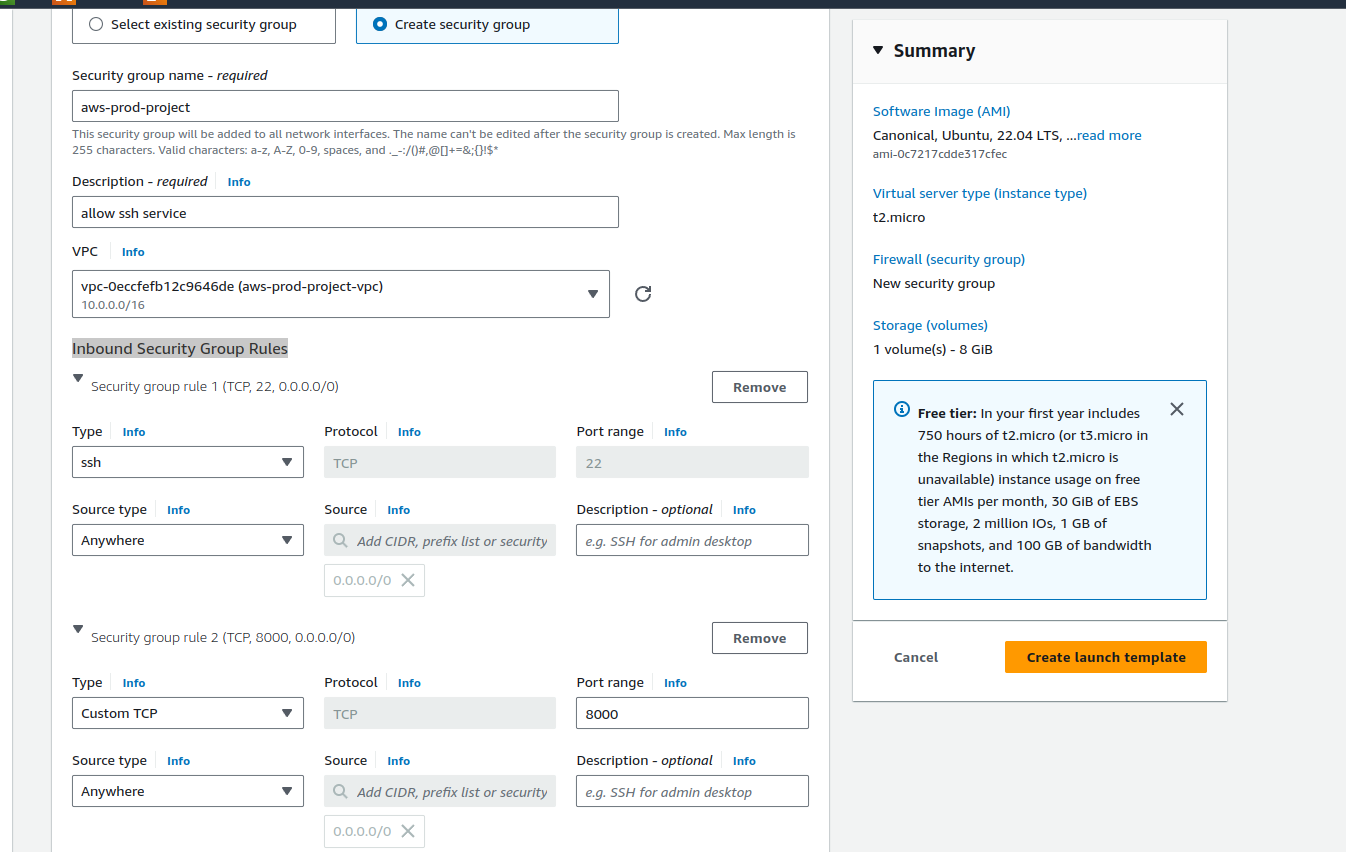
This is a sample of how I configured the template.
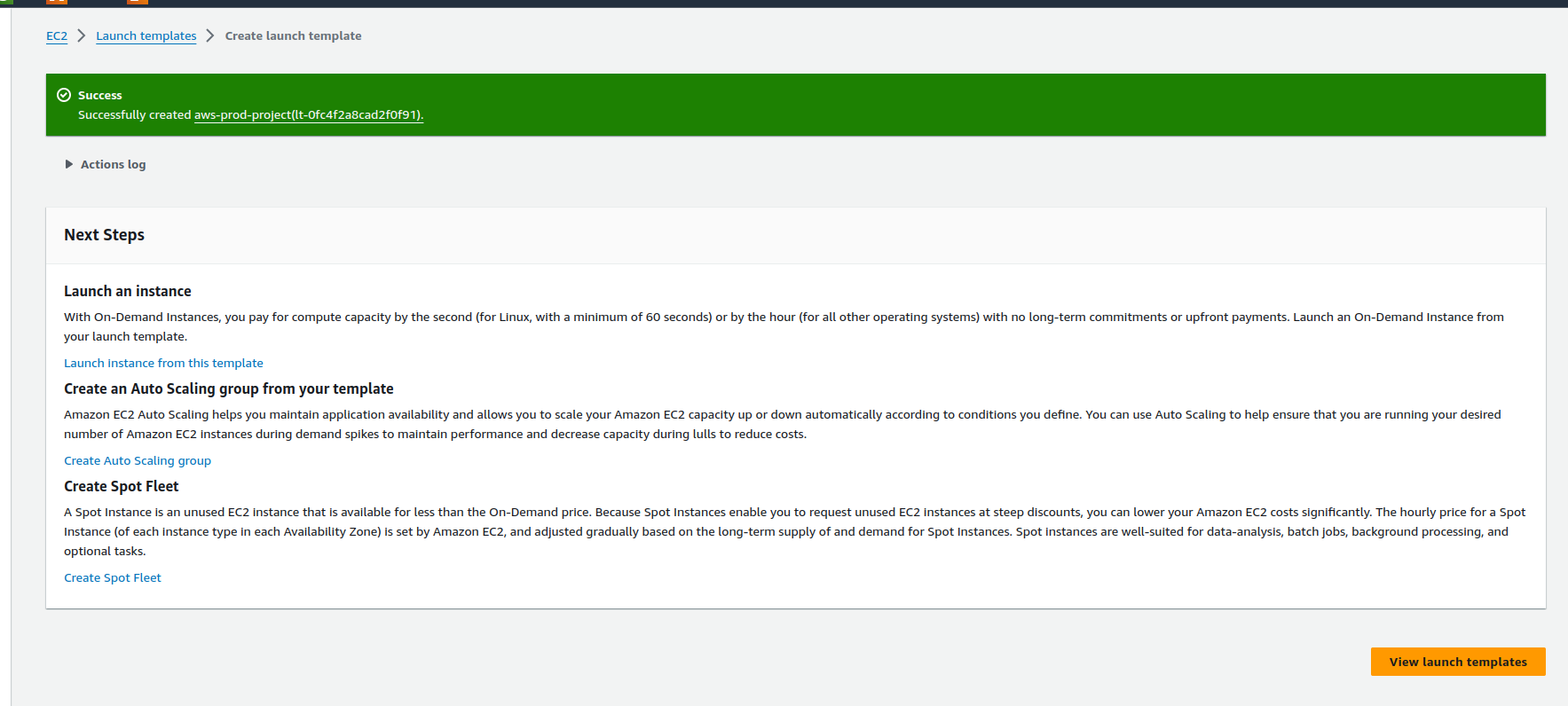
Our template is successfully created and now create the autoscaling group.
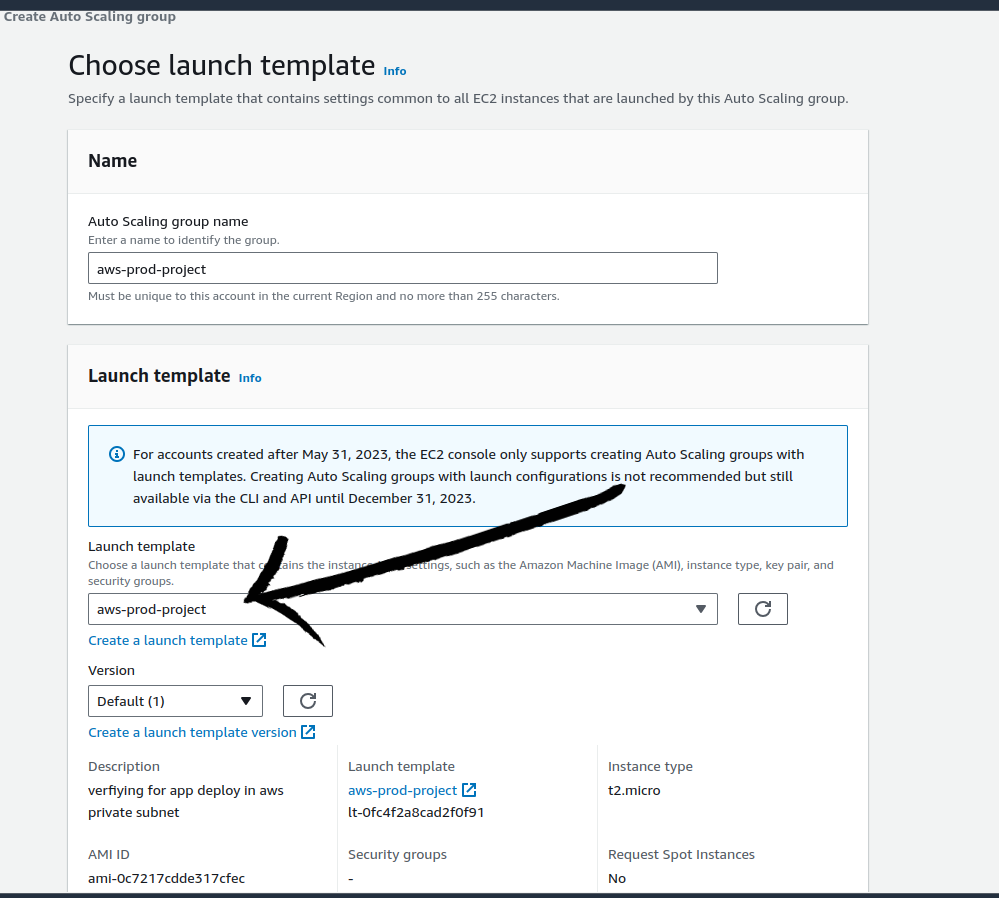
Our template is now available, if you cannot see the template just refresh the page. After adding the details click next.
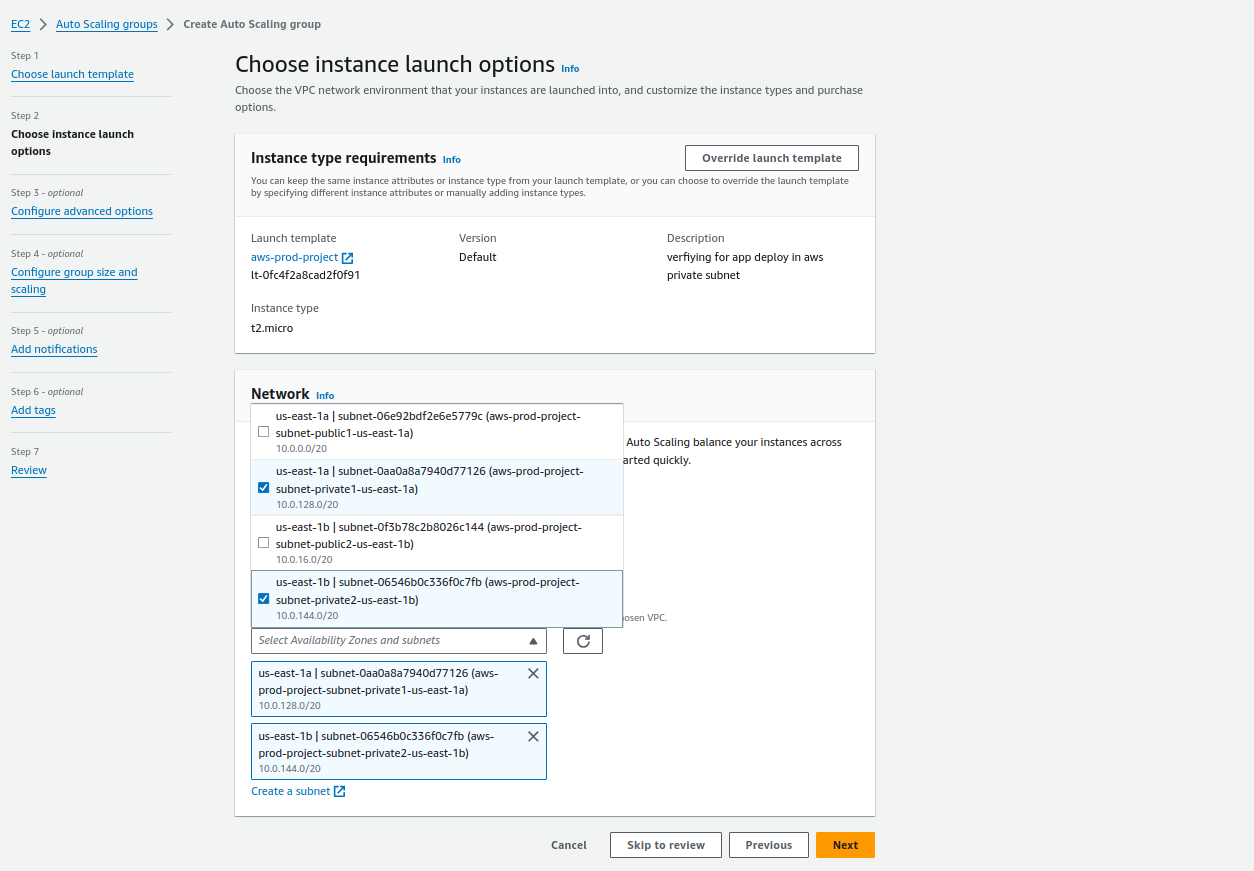
Here we have chosen our VPC and in the Availability Zones and subnets, we choose the private subnets since we want our instances in the private subnet as in the architecture of the project.
Click on Next.
Configure advanced options: keep everything default
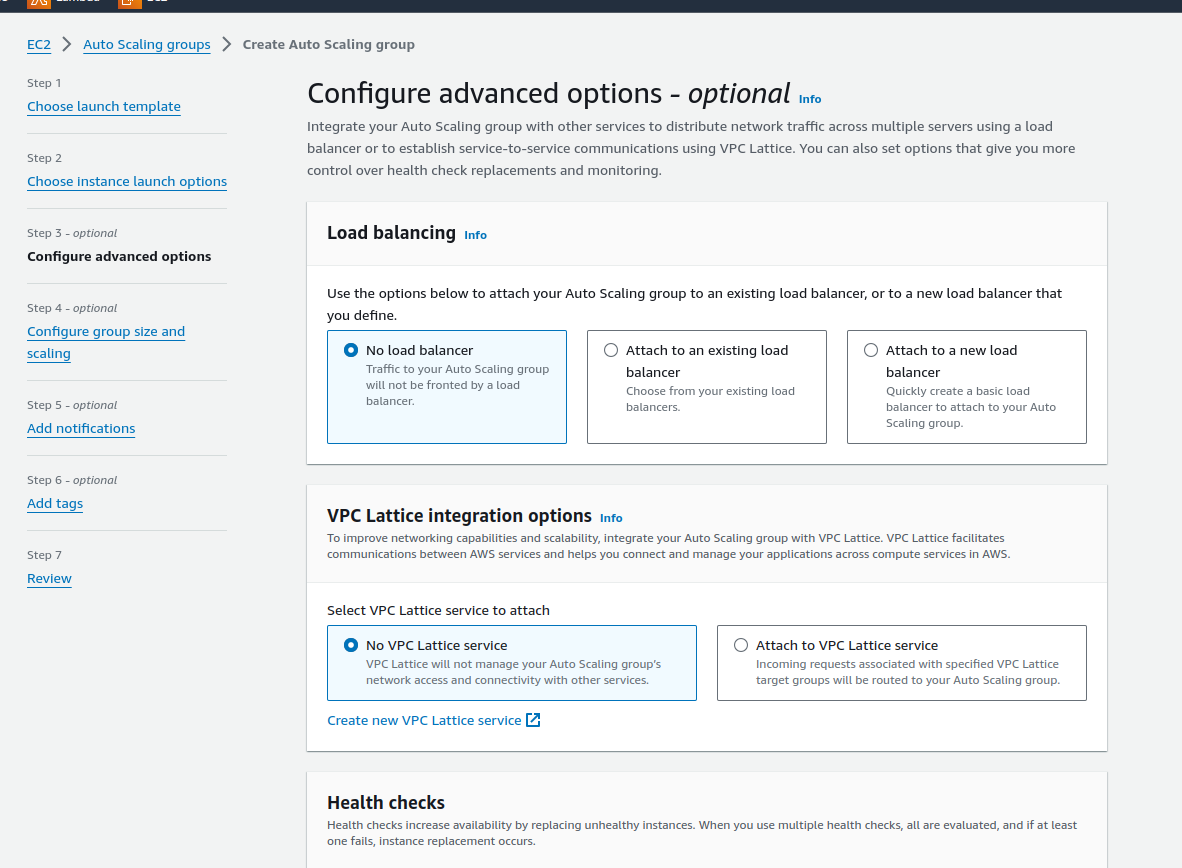
Click on Next.
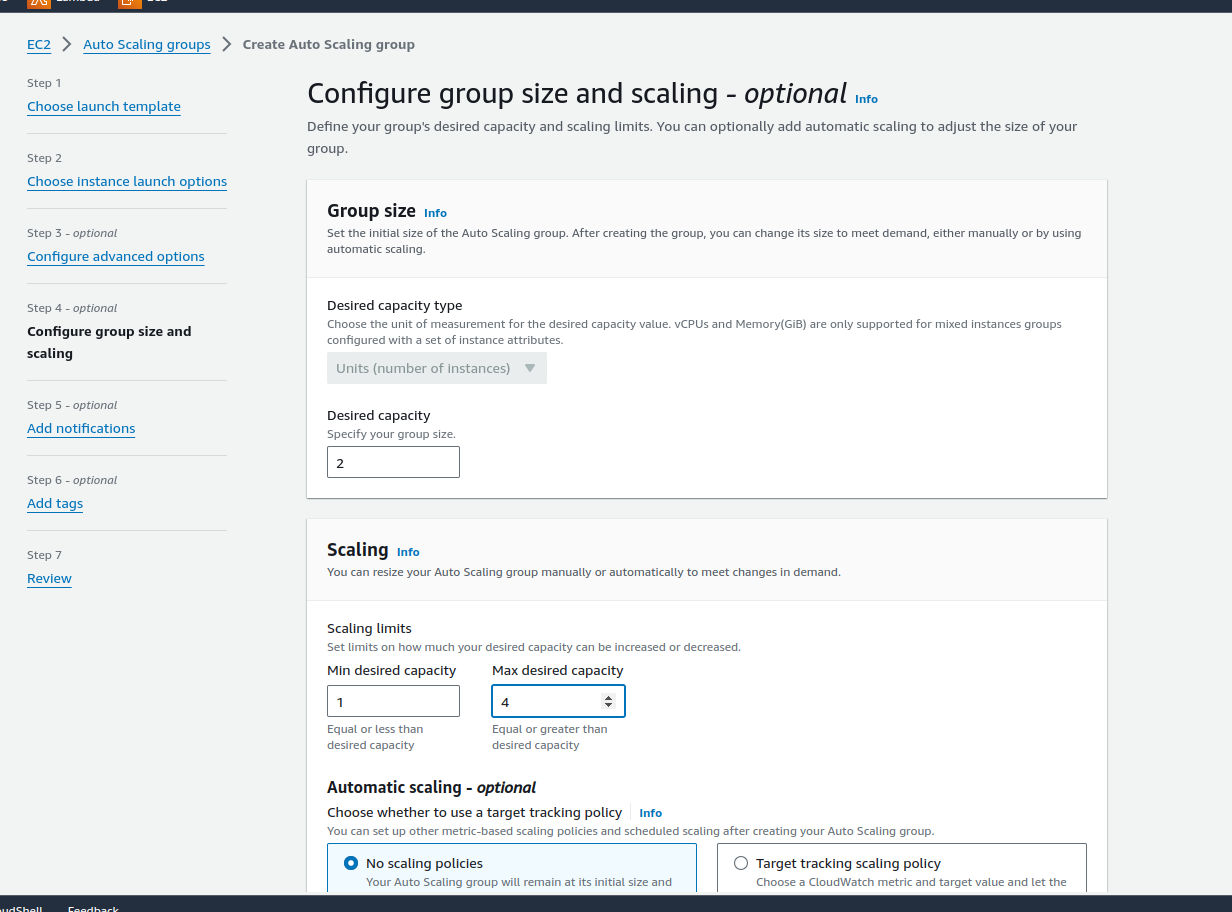
In the Configure group size, keep desired capacity=2, min.=1, and max=4
Automatic scaling= No scaling policies
Click on Next and after this all are optional to add notifications and tags. I have skipped these and created the autoscaling group.
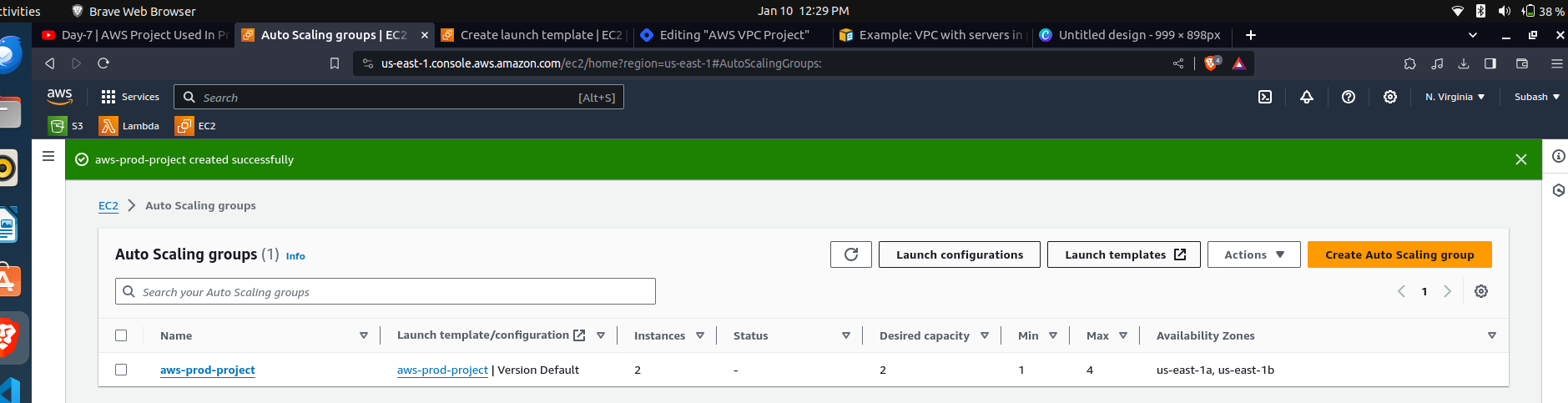
We can see our 2 instances are launched as we kept desired state as two.
Now let's verify whether the autoscaling group has created instances in us-east-1a and us-east-1b.
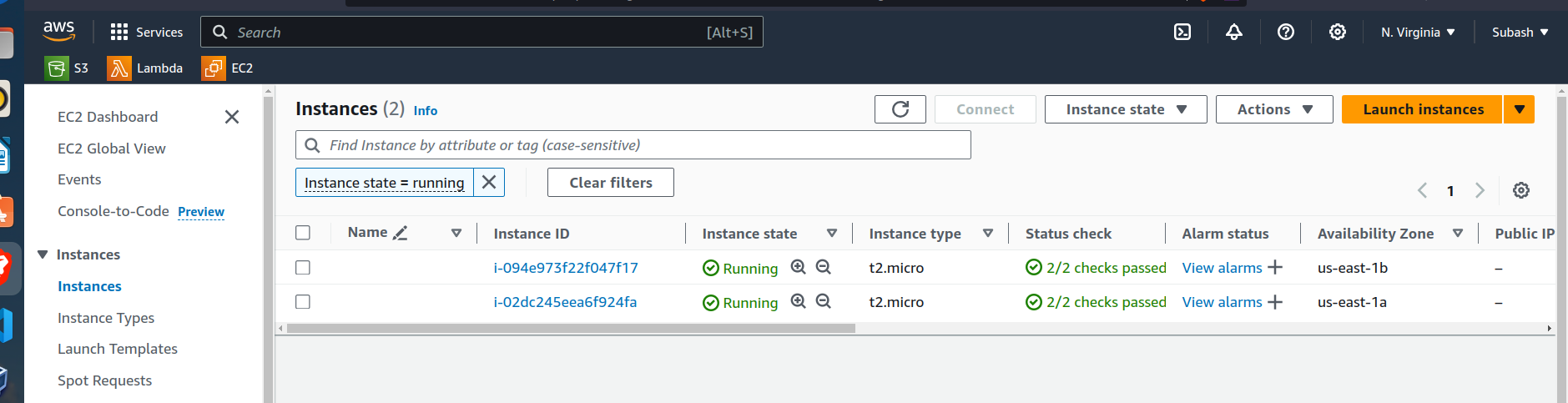
Perfect the autoscaling group has created the two instances in two zones in the private subnet.
Before creating an application load balancer we need to install the application in the server(instances).
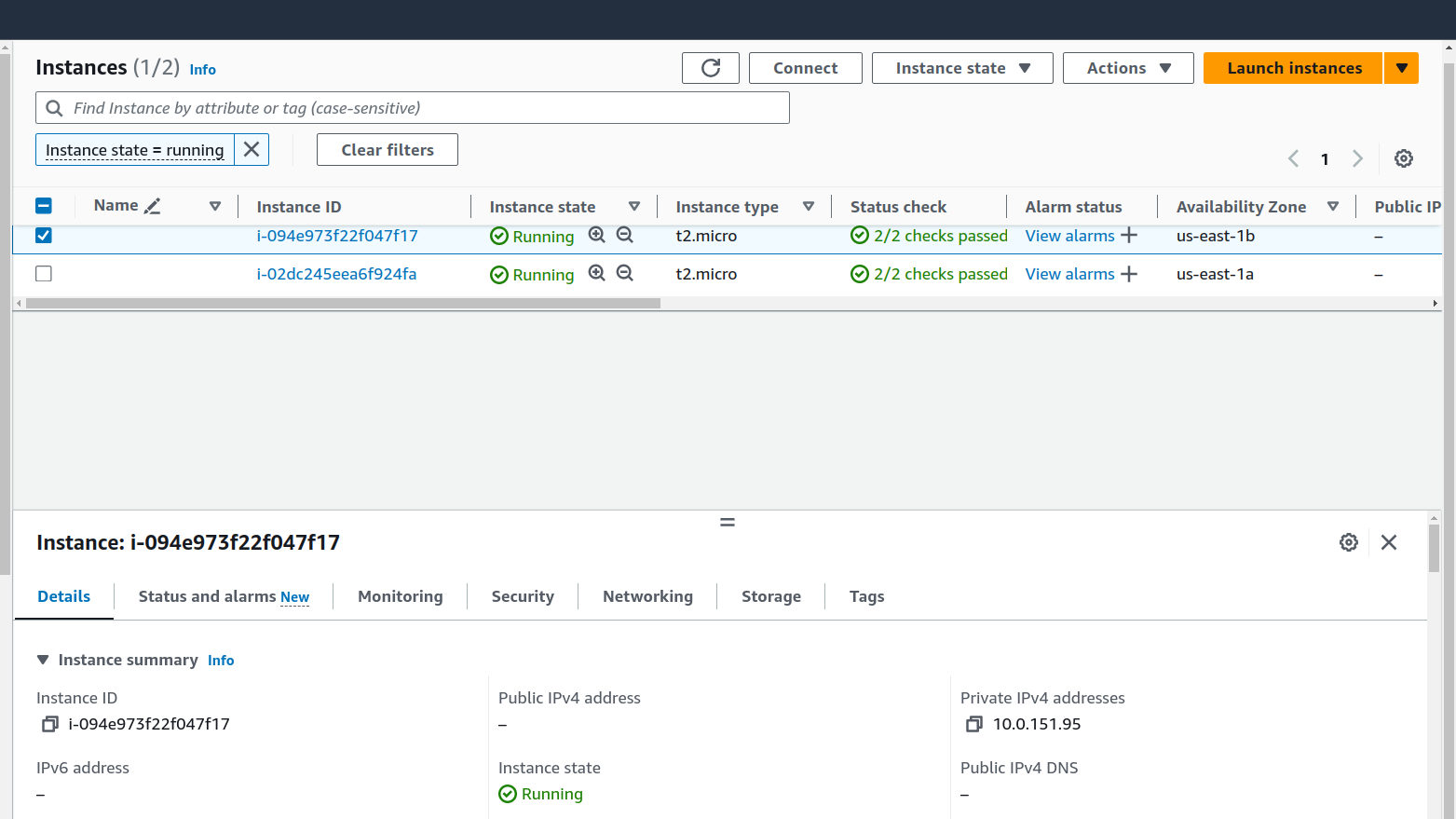
Since we need the public IPV4 address to ssh into any instance. We can see clearly in the image we have no IPv4 address as it is in a private subnet and we don't want our server to be access public. To solve this issue, a bastion host comes into the picture. Bastion host acts as a mediator between private subnet and public subnet.
So we will create a bastion host in the public subnet and try to access the server.
The process is the same to create a bastion host as creating the instance but in a bastion host, three important points are: VPC - choose the same VPC in which the above-created servers are running, choose auto-assign public IP enable and inbound rules allow ssh.
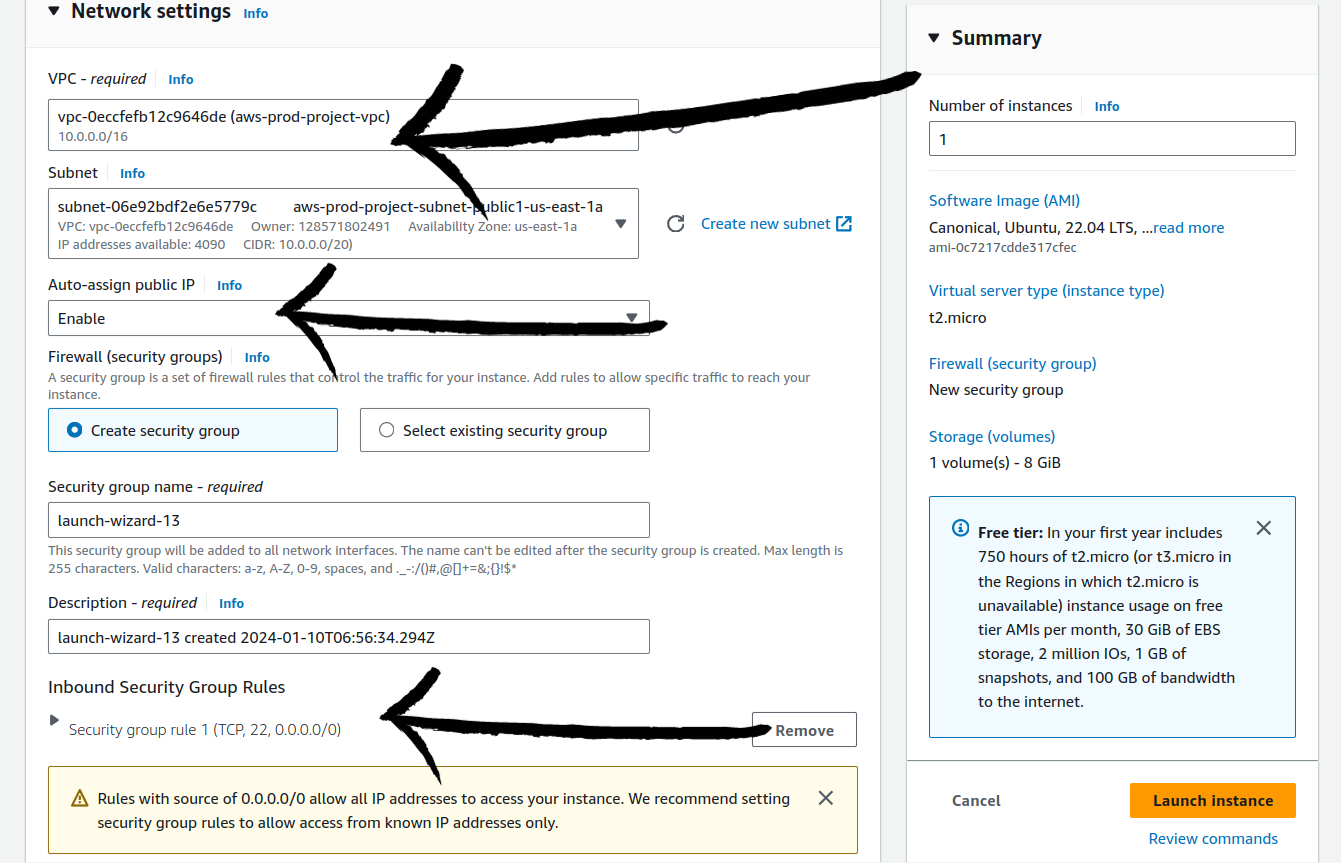
Click on the launch instance.
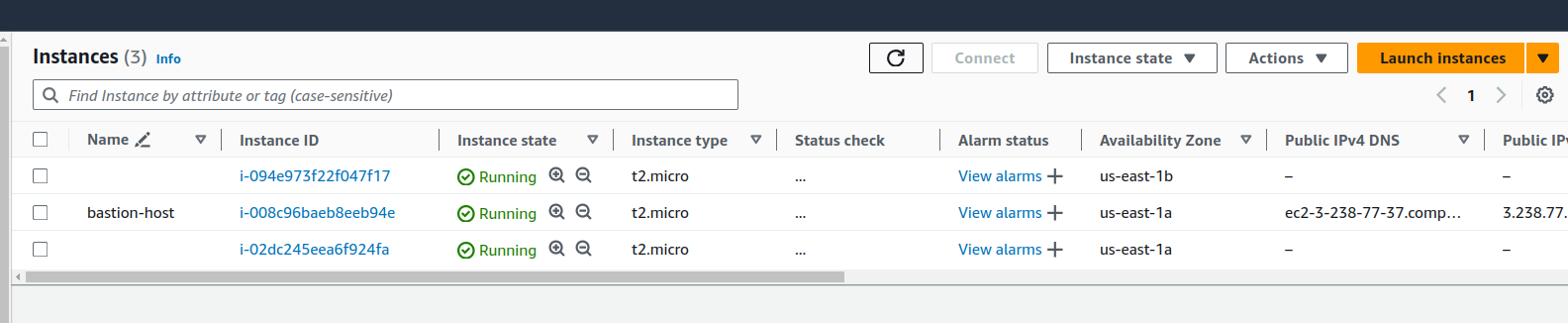
Our instance is created and we will SSH into the bastion host and from this we will try to access the other two instances and install the application.
To get access to two of these private subnets, we also need a key-pairs file in Bastion. So we will copy our pem file in Bastion host also.
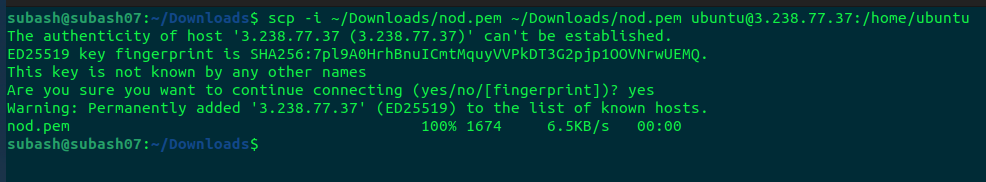
scp -i ~/Downloads/nod.pem ~/Downloads/nod.pem ubuntu@3.238.77.37:/home/ubuntu
Now let's access the bastion-host instance using SSH protocol
ssh -i .pem_fiel ubuntu@3.238.77.37
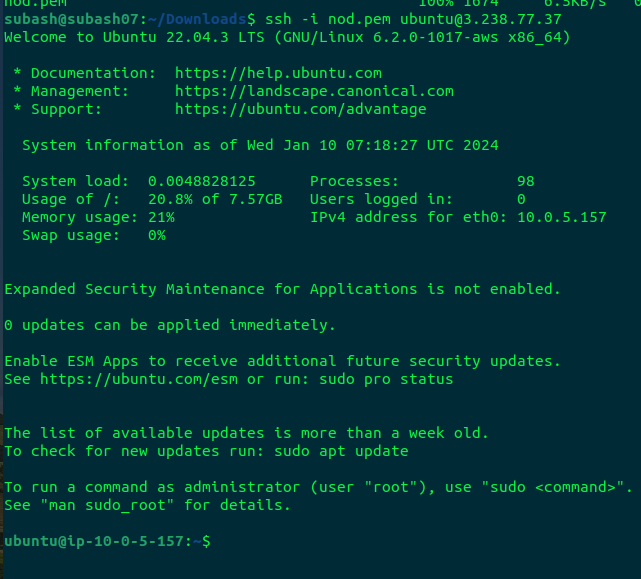
We have done this step successfully.
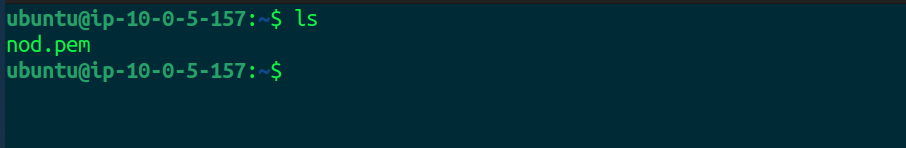
We can see our pem file is available in the instance. Now we will SSH into the other instance using the same pem file.
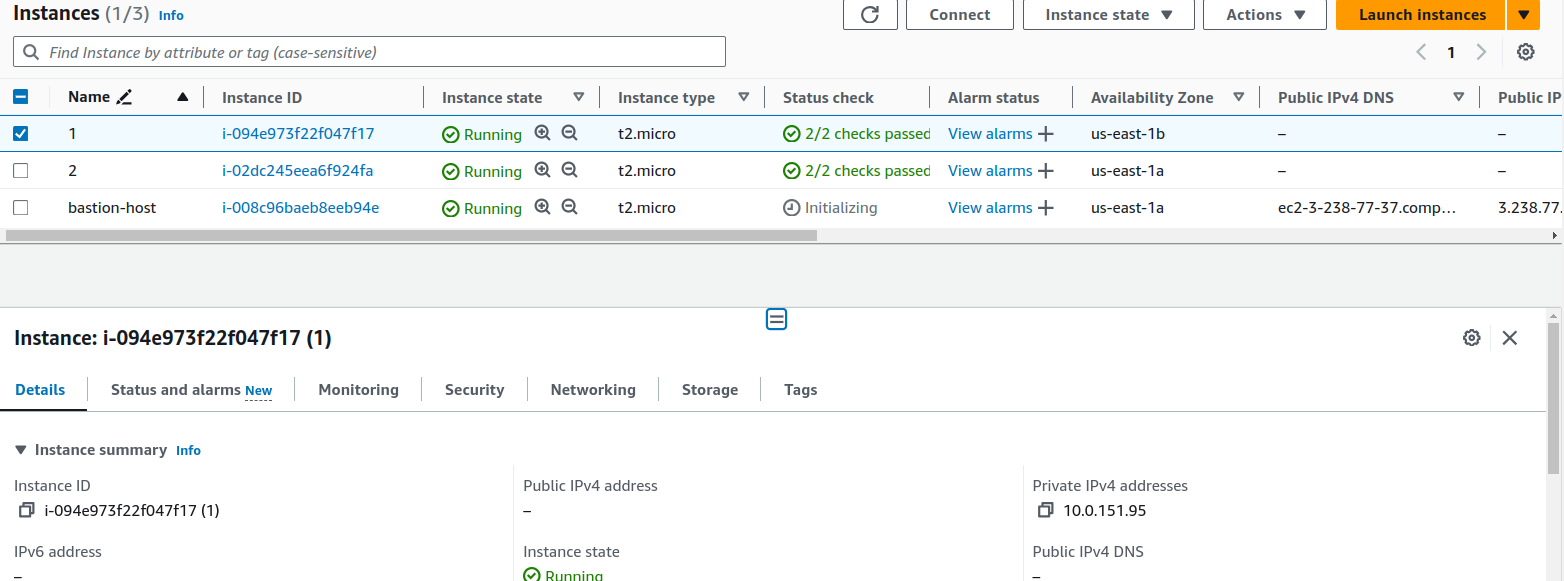
As of now we are in the bastion-host instance and from here we will ssh into instance 1 using its private IP address
ssh -i pemfile ubuntu@private_ip
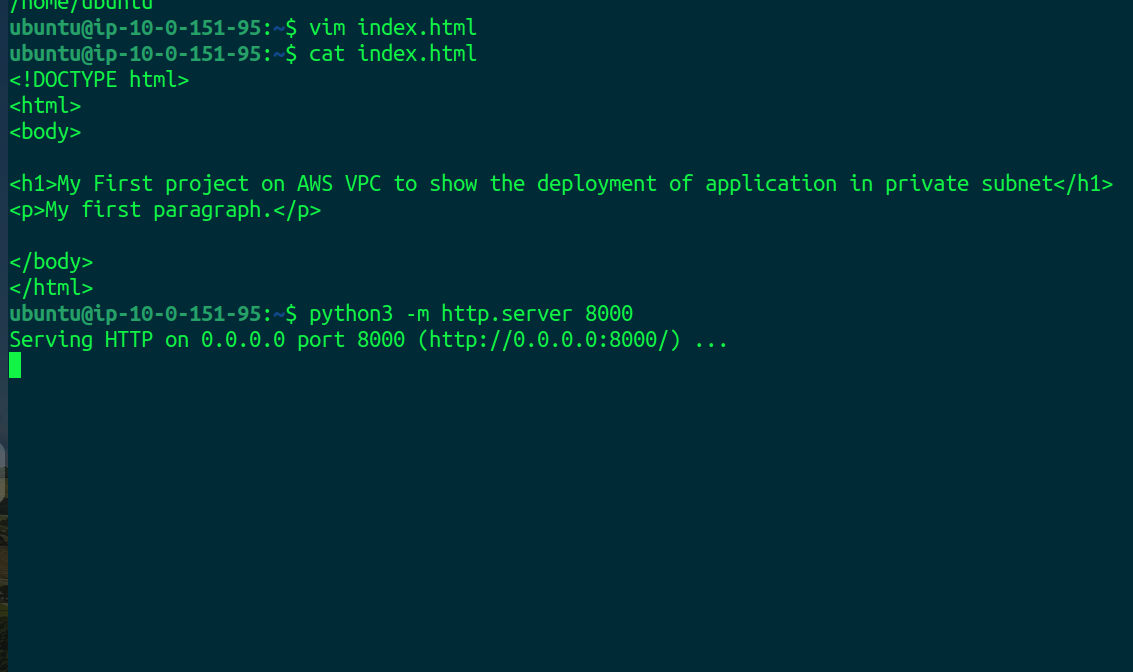
We can see the private IP of instance 1 so we have access to the instance. In this instance, we will create a very simple application and run it on port 8000.
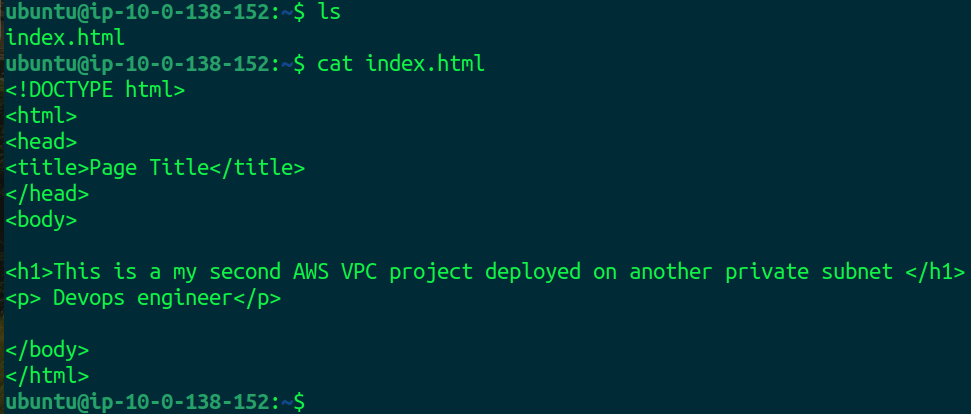
In the same way, we will create our second application on instance 2.
ssh -i nod.pem ubuntu@10.0.138.152
Now, Create a Load balancer and attach these instances as target groups
In the EC2 Dashboard select load balancers. Then click on Create the load balancer.
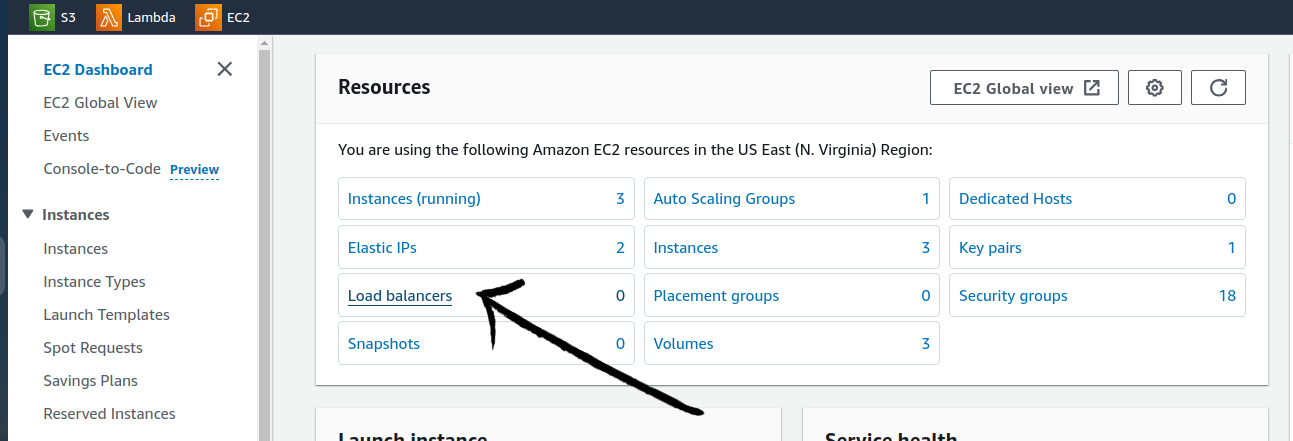
In the next step select Application load balancer.
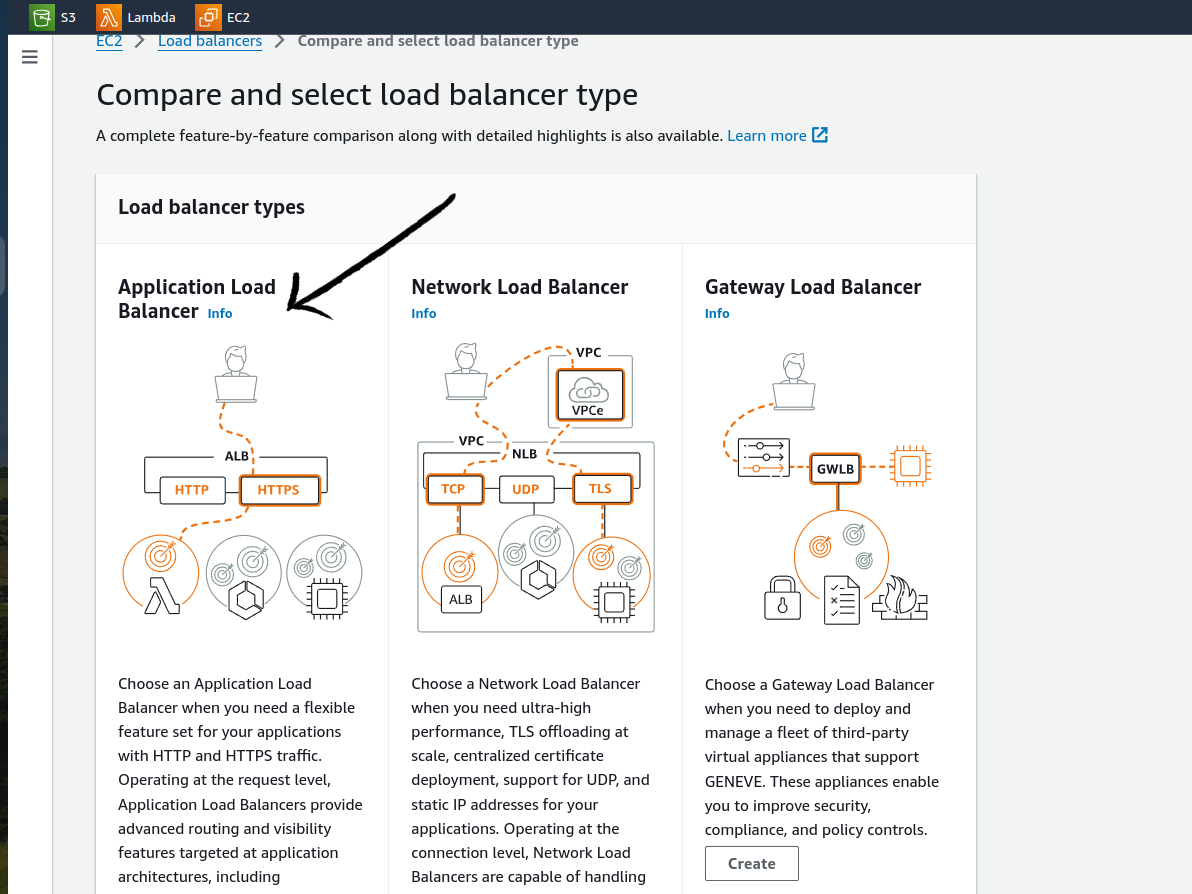
Click create.
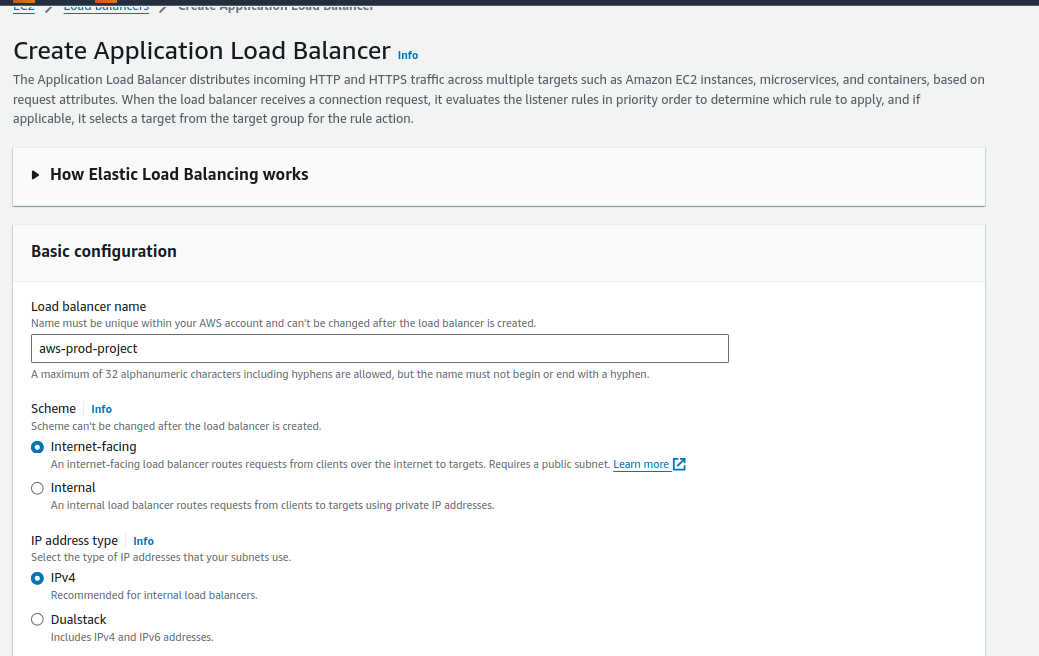
Give the name to the load balancer and it must be internet-facing and has an IPV4 address type.
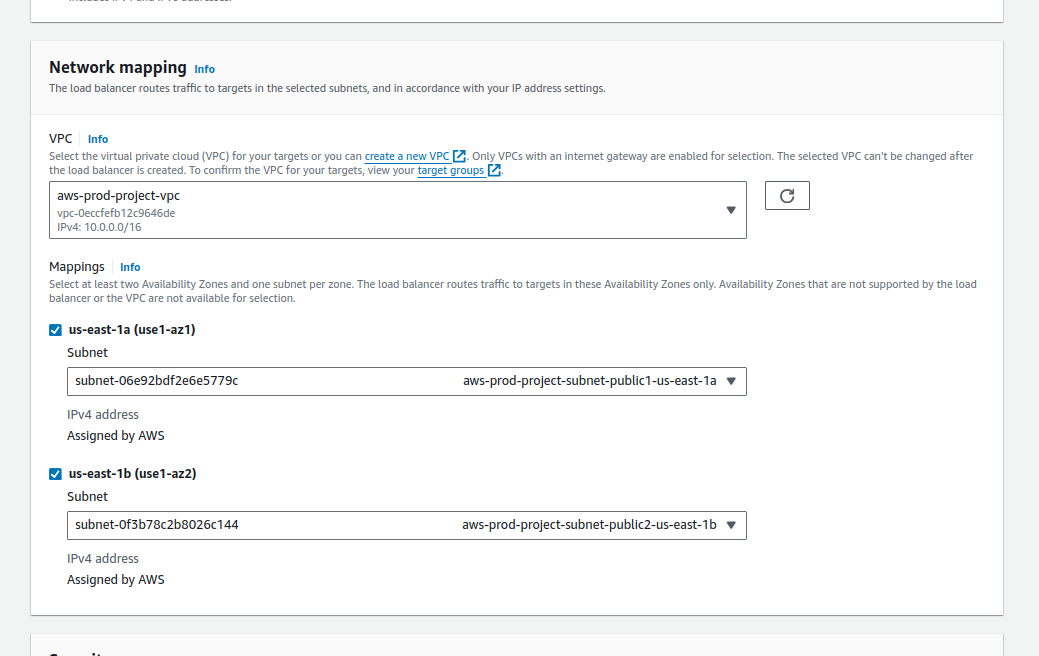
Choose the VPC that we created earlier as our servers are running on that VPC. In Loadbalancer we need to select the public subnets for mapping.
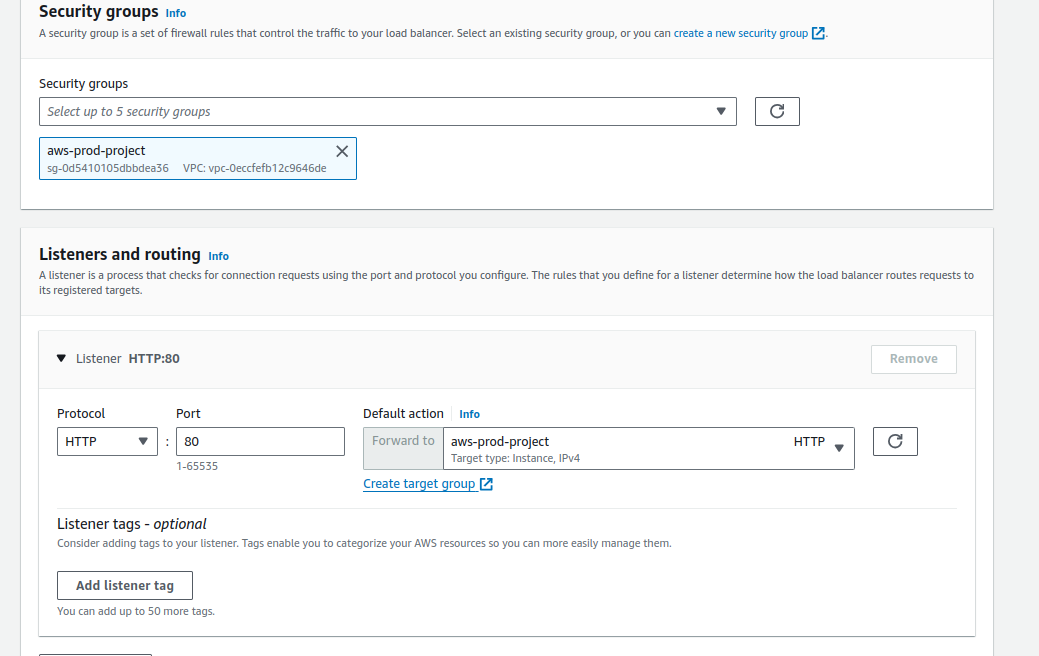
Select the Create security groups and port 80. For default action, if there is no any security group, click on Create Security group.
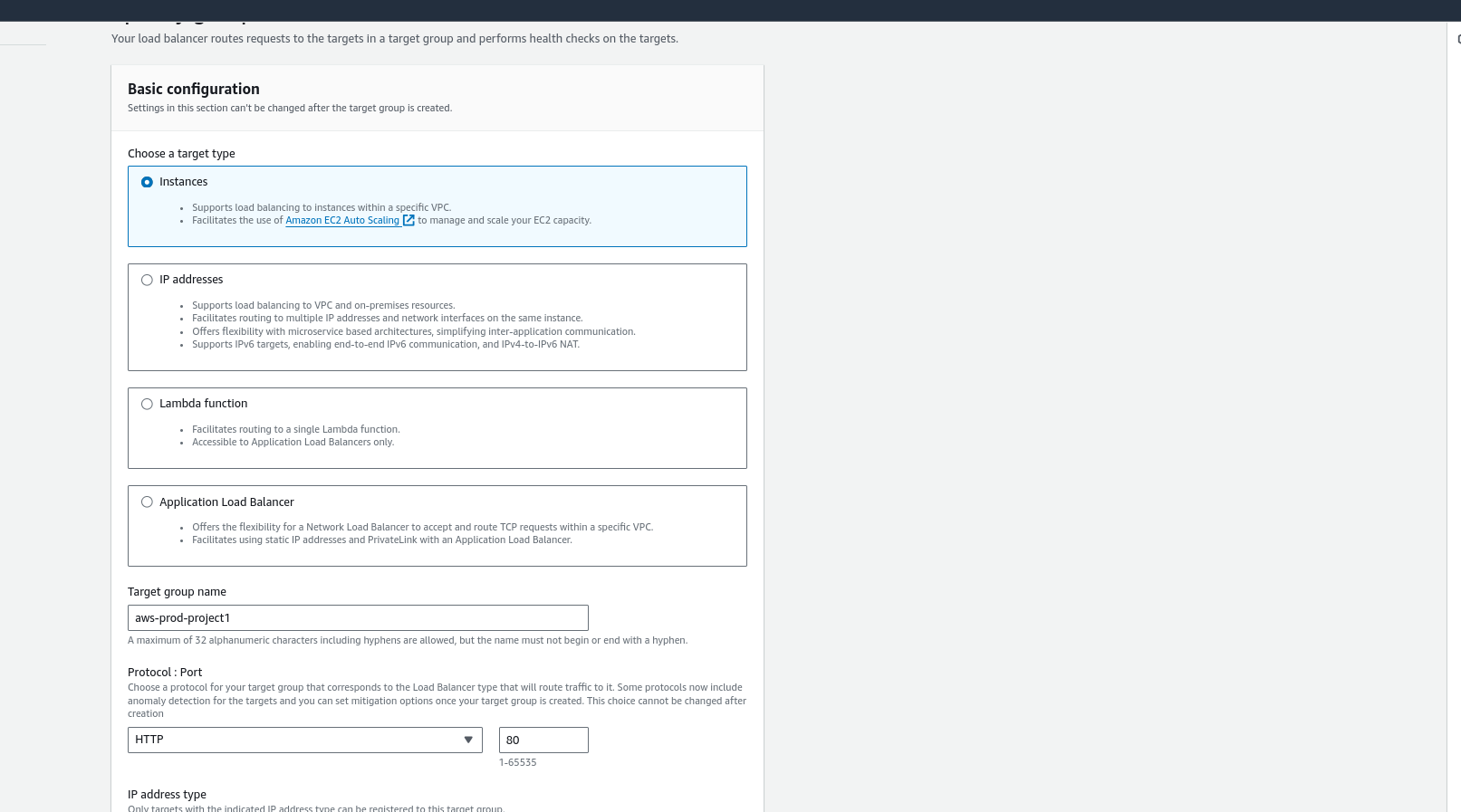
Choose instance as our target, give the target group name, keep other default, and choose next.
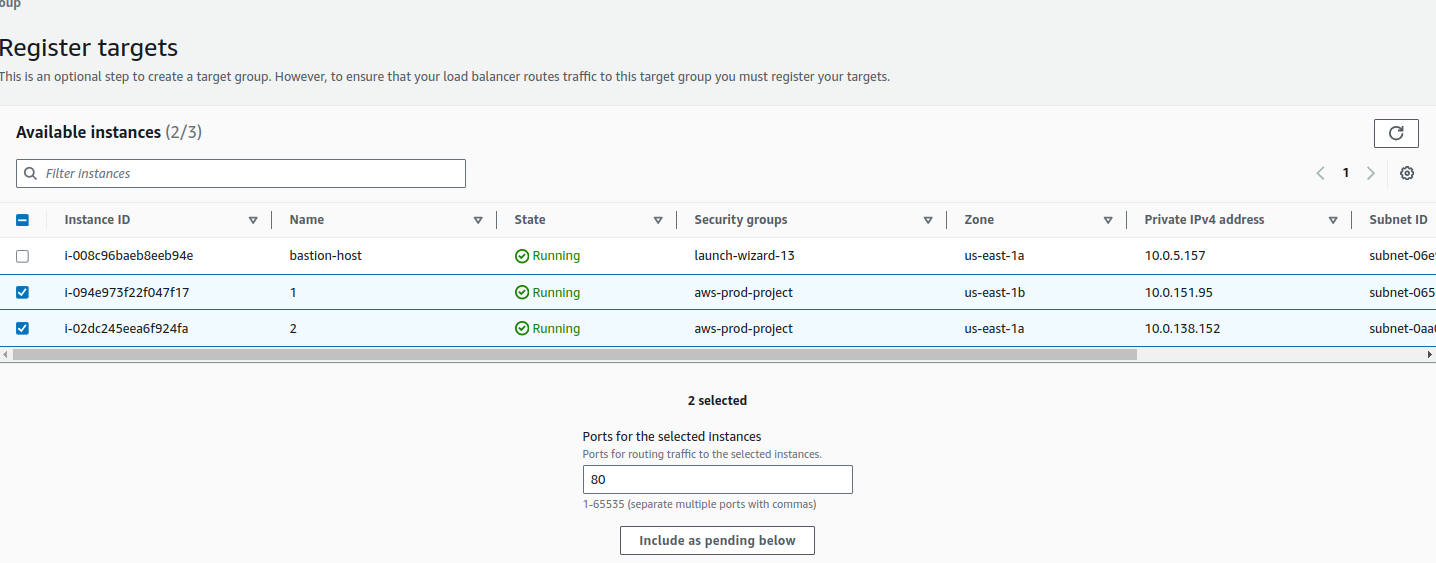
Select the target instances in which the application will be running or application is running and also click include as pending below. Then click Create Target group.
In the load balancer configuration select the recently created target group.
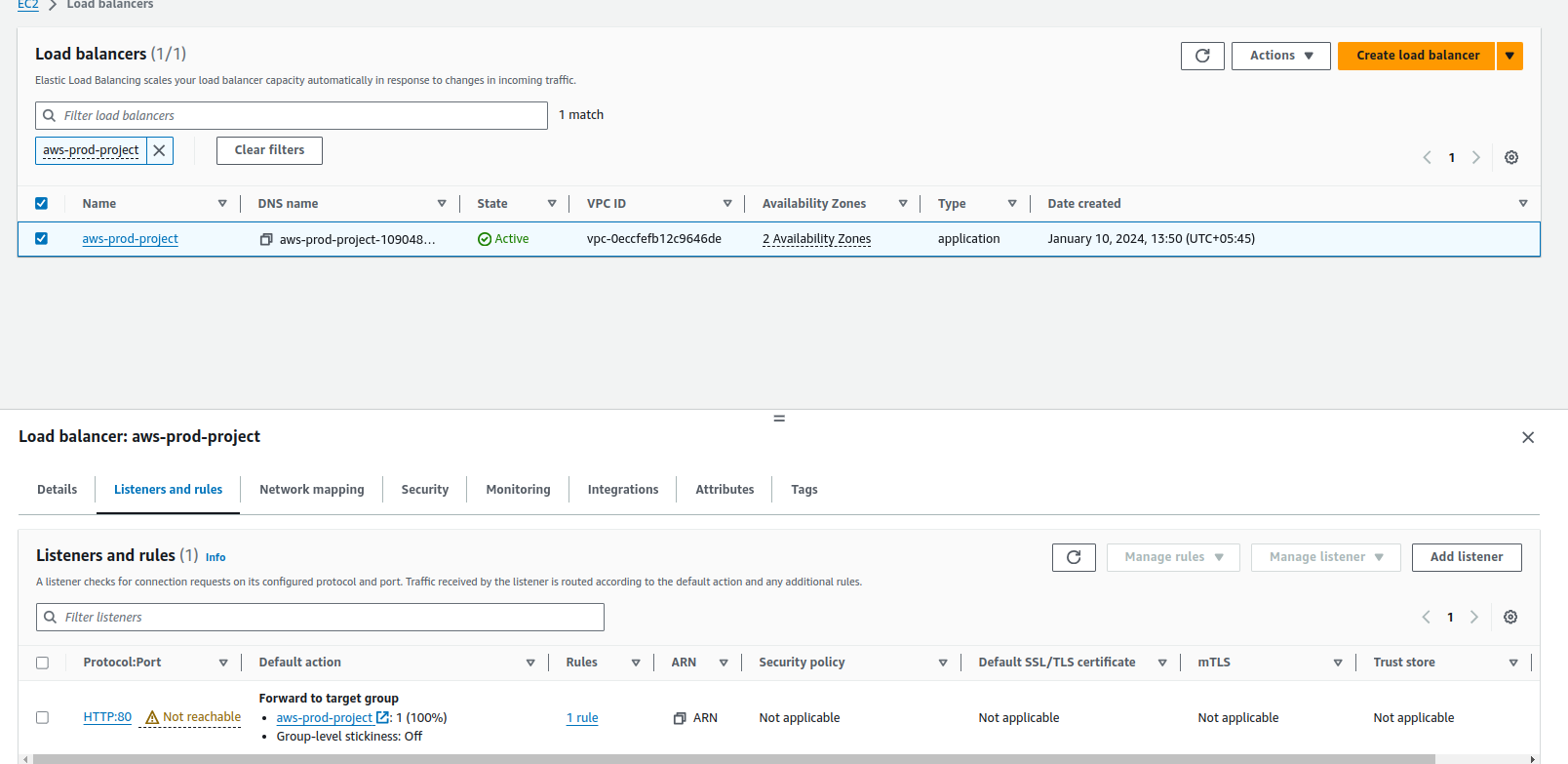
Finally, our load balancer is created and also we can see the HTTP protocol at port 80 is not reachable. So click on the Security tab, choose security group, and in the inbound rule add HTTP at port 80.
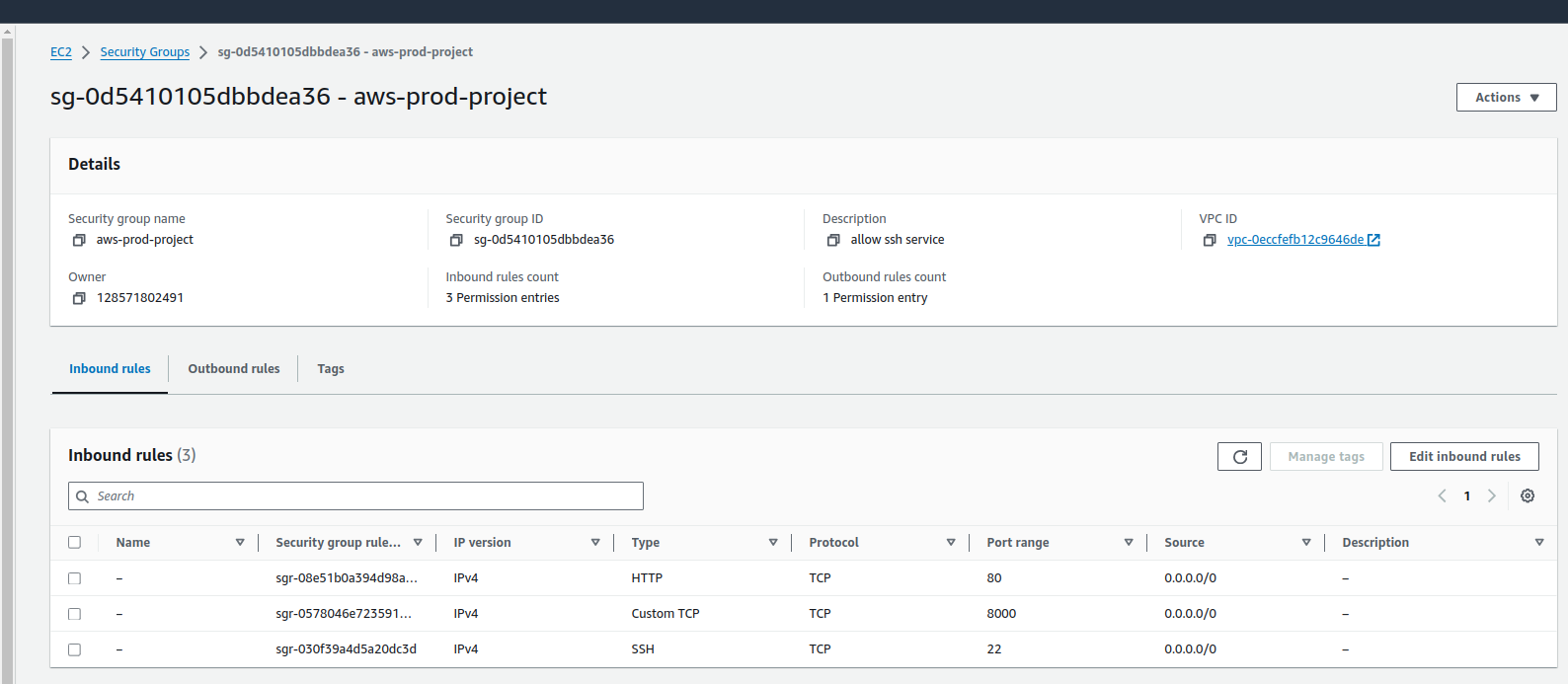
Now let's check the load balancers.
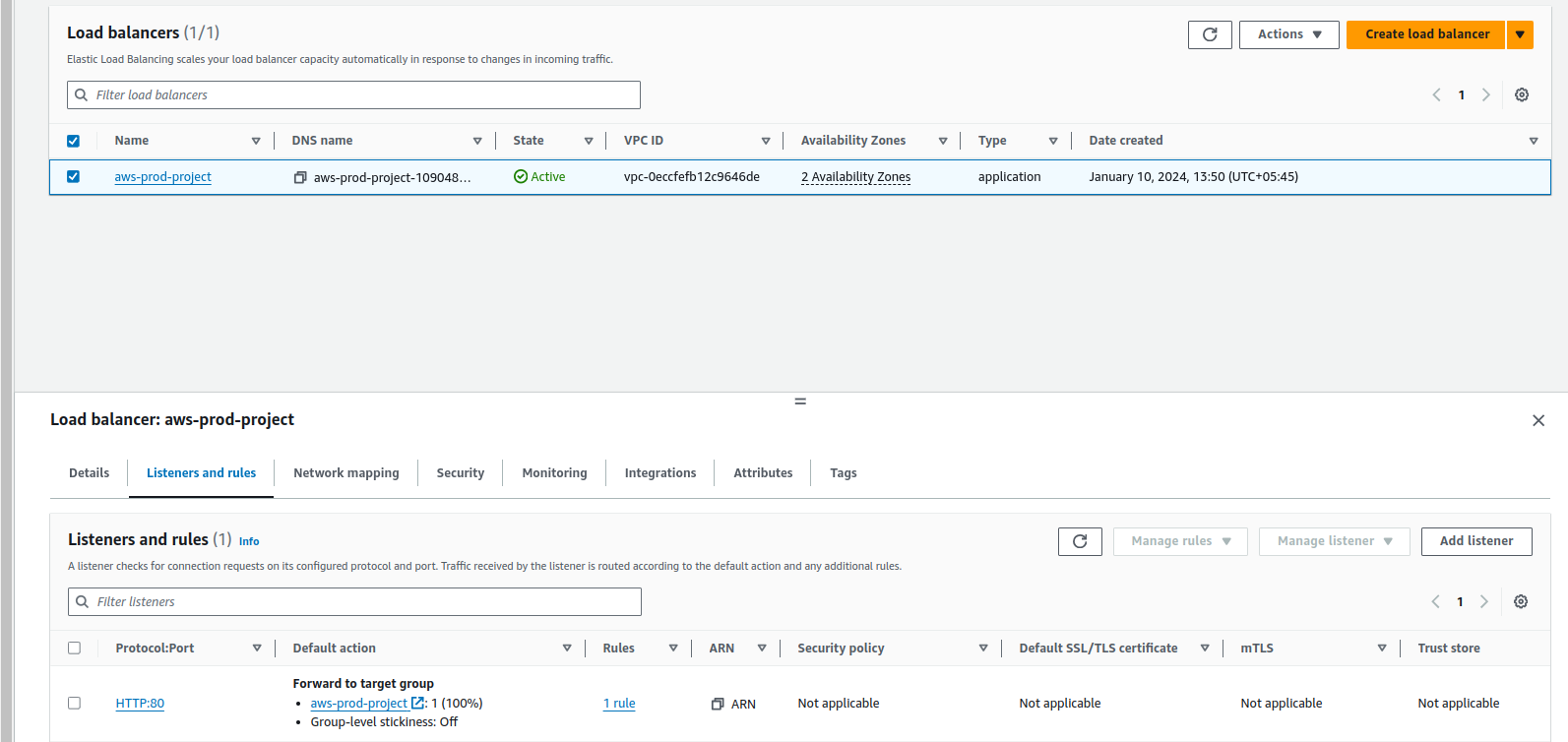
Now it is reachable.
To check the health status of the Targets click on the project name.
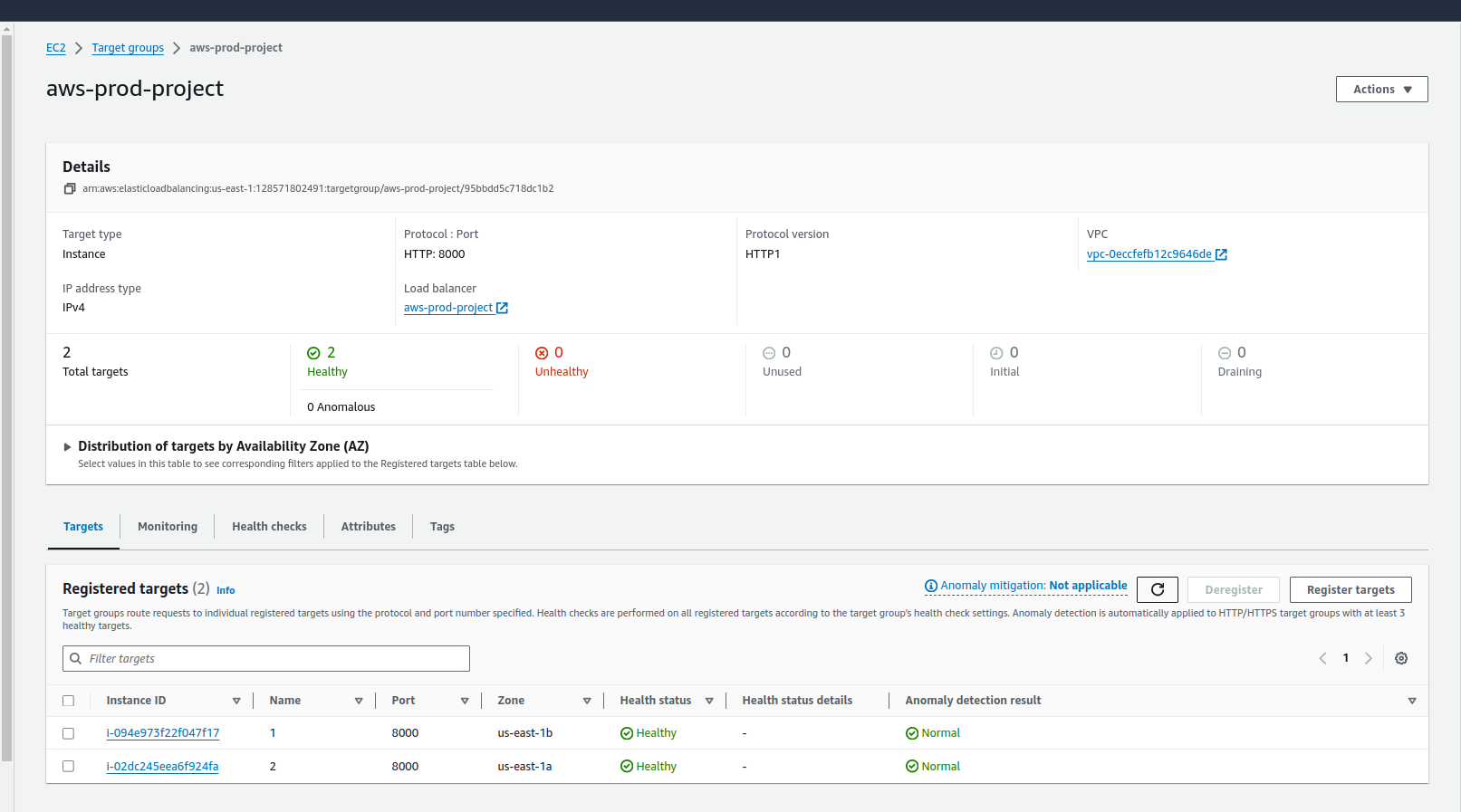
We can see our servers are both healthy. We will try to access our applications using this link aws-prod-project-1090487507.us-east-1.elb.amazonaws.com, it will be available under the Details section (DNS name) in the load balancer page.
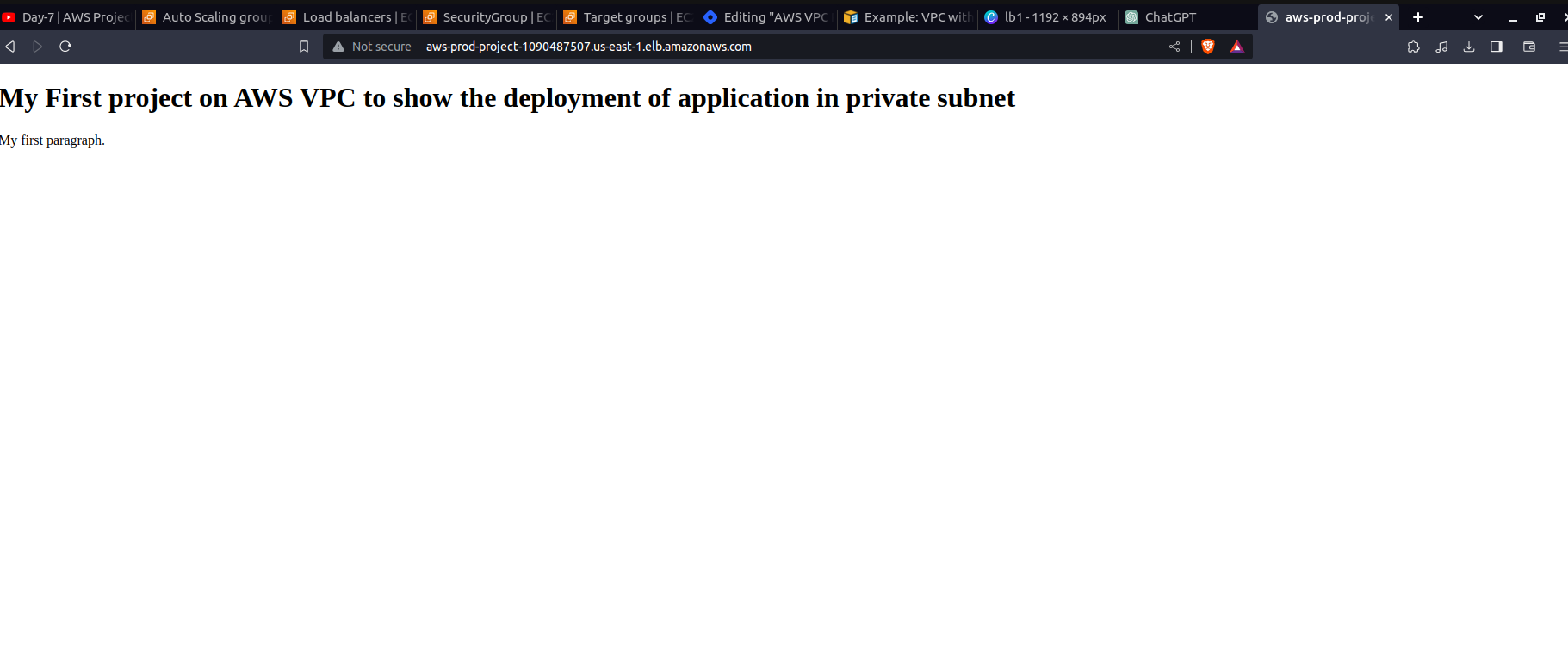
Our first application is perfectly running.
Again let's try to access the same URL in another tab.
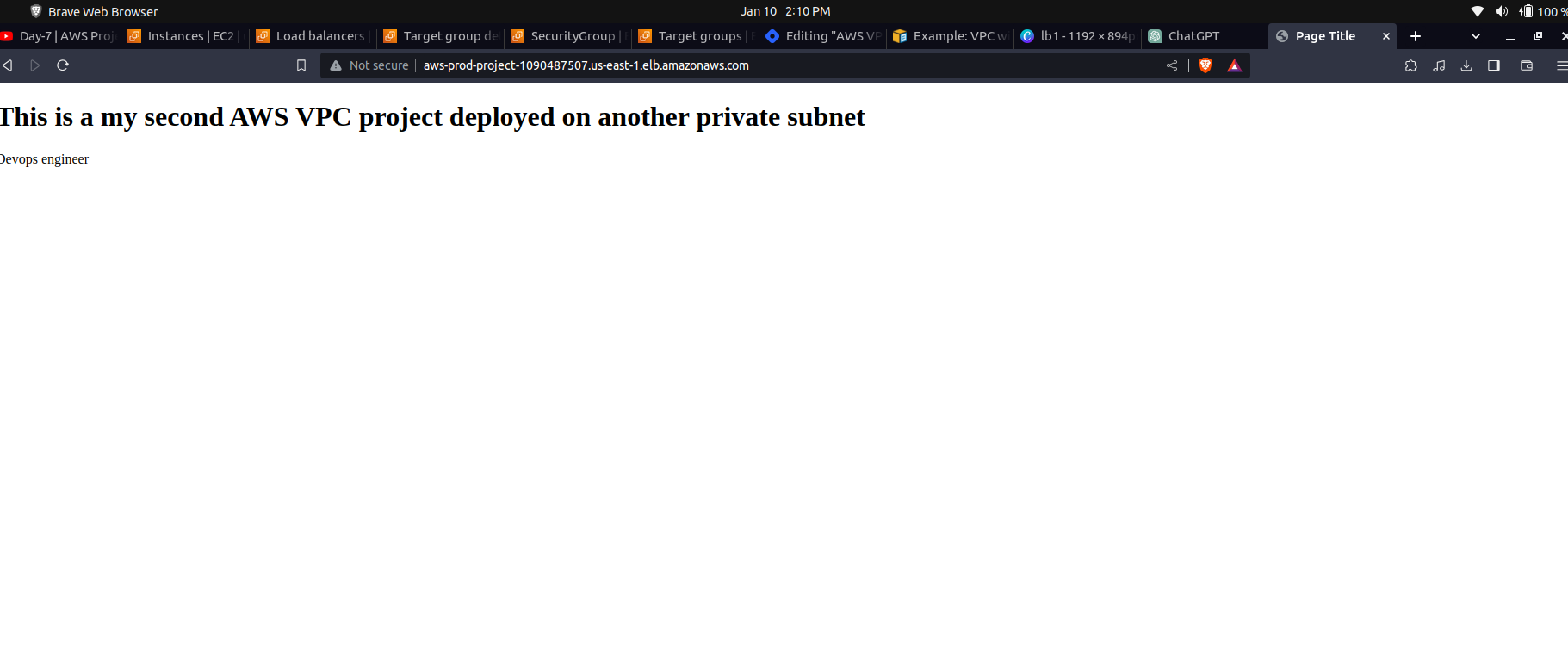
We can see our second app running on the second server is loaded successfully. Hence the load balancer has successfully distributed the server requests.
We covered the basic building blocks like subnets and route tables, and walked through practical steps for setting up a secure and scalable cloud environment. Think of VPCs as the foundation for creating a safe and flexible space in the cloud, and learning about them is a valuable skill for anyone working with online services.
Happy Learning!!
Subscribe to my newsletter
Read articles from Subash Neupane directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Subash Neupane
Subash Neupane
Computer Science graduate