Security Testing Methodologies
 Vimal Girija V
Vimal Girija V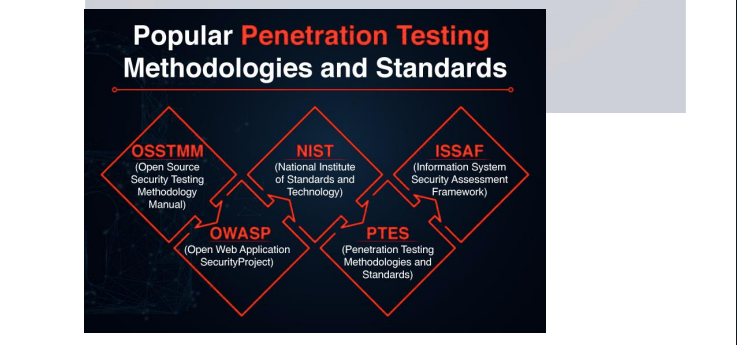
Security testing methodologies are systematic approaches or frameworks that guide the process of evaluating the security of a system, application, or network. These methodologies help identify vulnerabilities, weaknesses, and potential risks to implement effective security measures. Here are some widely recognized security testing methodologies:
OWASP Application Security Verification Standard (ASVS):

Overview: ASVS is a community-driven framework that establishes a security standard for web applications and services. It provides security controls and requirements across three levels (L1-L3) to guide the development and testing of web applications. OWASP Application Security Verification Standard (ASVS), which is indeed a project within the OWASP organization
Focus: Primarily for web application security.
Key Features: Detailed security controls, three security levels, technology-agnostic.
PTES (Penetration Testing Execution Standard):
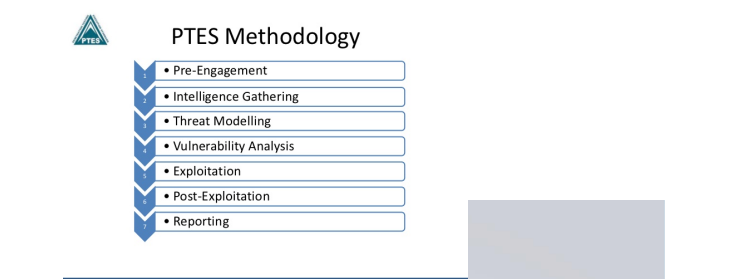
Overview: PTES is a framework that defines a consistent and comprehensive approach to penetration testing. It guides testers through seven stages, from pre-engagement to reporting, ensuring a thorough and structured testing process.
Focus: Primarily for penetration testing and ethical hacking.
Key Features: Seven-stage methodology emphasizes targeted assessments and point-in-time assessment.
OSSTMM (Open Source Security Testing Methodology Manual):

Overview: OSSTMM is a manual that provides a holistic approach to security testing, covering technical, operational, and human security aspects. It emphasizes realistic testing scenarios and offers guidelines for security professionals.
Focus: Holistic security testing covering technical, operational, and human aspects.
Key Features: Realistic testing scenarios, comprehensive manual, diverse testing areas.
ISSAF (Information Systems Security Assessment Framework):

Overview: ISSAF is a framework designed to assist security professionals in conducting security assessments of information systems. It provides guidelines, tools, and methodologies for comprehensive security assessments.
Focus: Security assessments of information systems.
Key Features: Structured approach, covers reconnaissance to reporting, includes tools and techniques.
NIST (National Institute of Standards and Technology):
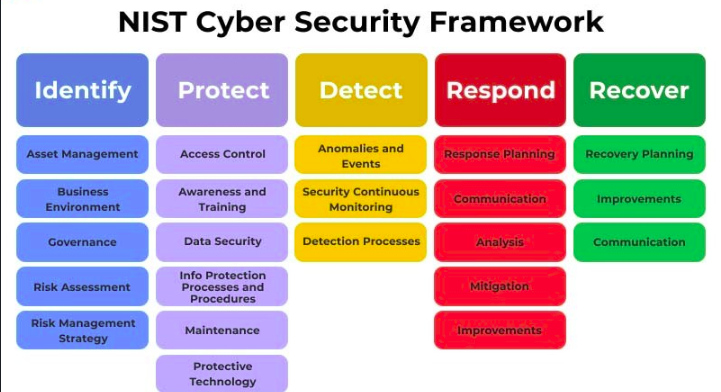
Overview: NIST SP 800-115 is a technical guide from the National Institute of Standards and Technology (NIST) that guides information security testing and assessment. It covers the planning, execution, and management of security testing activities.
Focus: Information security testing and assessment.
Key Features: Guidance for planning and executing security testing aligns with the NIST framework.
Difference between OWASP and OWASP (ASVS)

OWASP (Open Web Application Security Project):

Definition: OWASP Top Ten is a nonprofit organization dedicated to improving the security of software. It was designed in 2003 to demonstrate applications’ key risks. It provides resources, tools, guidelines, and projects to help organizations and individuals develop, maintain, and operate secure software.
Role: OWASP's role is to raise awareness about application security, provide educational resources, and offer tools and projects to assist in the secure development and testing of web applications. The OWASP Top Ten is updated periodically; the most recent version was released in 2021. The OWASP Top Ten includes the following risks:
1. A01:2021-Broken Access Control
2. A02:2021-Cryptographic Failures
3. A03:2021-Injection
4. A04:2021-Insecure Design
5. A05:2021-Security Misconfiguration
6. A06:2021-Vulnerable and Outdated Components
7. A07:2021-Identification and Authentication Failures
8. A08:2021-Software and Data Integrity Failures
9. A09:2021-Security Logging and Monitoring Failures
10. A10:2021-Server-Side Request Forgery
OWASP Application Security Verification Standard (ASVS):
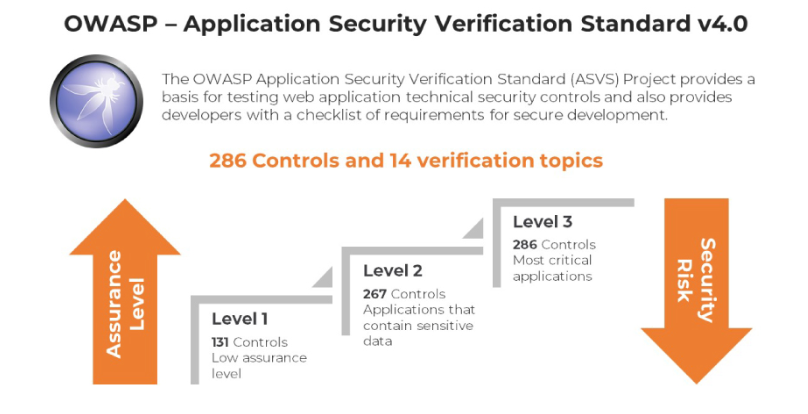
Definition: The OWASP ASVS is a specific project within the OWASP organization. It is a framework and a set of security controls that provide security requirements for web applications and web services. ASVS aims to standardize the security controls required during development and testing.
Role: ASVS focuses on establishing a security standard for web applications by providing a structured set of security controls across three levels (L1-L3). It is used to guide developers and security professionals in implementing and testing security features in web applications.
Level 1 (L1) is designed for low assurance levels and is fully penetration-testable.
Level 2 (L2) is recommended for most apps and is for applications that include sensitive data that requires protection.
Level 3 (L3) is intended for the most critical applications, such as those that handle high-value transactions, hold sensitive medical data, or require the highest level of trust.
Prev: Chapter 1
Next: Chapter 3
Subscribe to my newsletter
Read articles from Vimal Girija V directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Vimal Girija V
Vimal Girija V
Hey there! I'm a passionate tech enthusiast with a diverse skill set in software development, DevOps, and cybersecurity. I love building robust APIs with Python Django and creating interactive user interfaces with React.js. My journey has taken me through the fascinating world of IoT, where I've tinkered with Arduino and Rasberry Pi devices, and I've also delved into the exciting realm of ethical hacking and penetration testing. Technologies I Know: Python Django Framework for API: I have hands-on experience in building APIs using the powerful Python Django framework, enabling me to create scalable and efficient web applications. React.js for Frontend Development: With proficiency in React.js, I craft engaging and responsive user interfaces, making the web experience seamless and enjoyable. Python Automation Testing with Selenium, Pytest, and Appium: My expertise in automation testing using Selenium, Pytest, and Appium ensures that software projects are thoroughly tested, reducing manual effort and improving the overall quality of the code. AWS DevOps with Git, Jenkins, Docker, SonarQube, Terraform, Ansible, Kubernetes, and Maven: I've mastered various DevOps tools and practices on the AWS platform, streamlining the development and deployment process. Git, Jenkins, Docker, SonarQube, Terraform, Ansible, Kubernetes, and Maven are among the tools I'm proficient in. IoT with Arduino and Raspberry Pi: Exploring the Internet of Things world, I've successfully worked with Arduino and Raspberry Pi to build exciting and innovative projects that leverage sensor data and real-world interactions. Certified Ethical Hacking and Penetration Testing: My passion for cybersecurity has driven me to become a Certified Ethical Hacker. I conduct penetration testing to identify and fix security vulnerabilities, ensuring systems and applications are protected against potential threats.