Kubernetes Configmaps and Secrets
 Subash Neupane
Subash Neupane
In this blog, we will delve into another pivotal aspect of Kubernetes – configmaps and secrets. Kubernetes primarily manages pods and containers, and the essential data needed by users for their containers is often accessed through environment variables. To streamline this process, Kubernetes employs configmaps, allowing users to create centralized configurations within the cluster. These configmaps store crucial information such as ports, database details, and more. Consequently, users can seamlessly access and utilize this information within their Kubernetes pods by either mounting or incorporating the configmap data into their container file systems.
So, configmap is solving the problem of storing the information that can be used by the application.
Secrets in Kubernetes also deals the same as the configmaps but it deals with sensitive information. Non-sensitive information is stored in configmaps and sensitive information is stored in secrets. The sensitive data of secret before stored in etcd, gets encrypted in Rest. Kubernetes does the default encryption but it also allows us to do the custom encryption.
Strong RBAC is enforced for secrets and the least privileged access is implemented for secrets.
Let's get directly into the hands-on experience.
Let's create the configmap file as cm.yml
apiVersion: v1
kind: ConfigMap
metadata:
name: test-cm
data:
db-port: "3306"
Apply
kubectl apply -f cm.yml
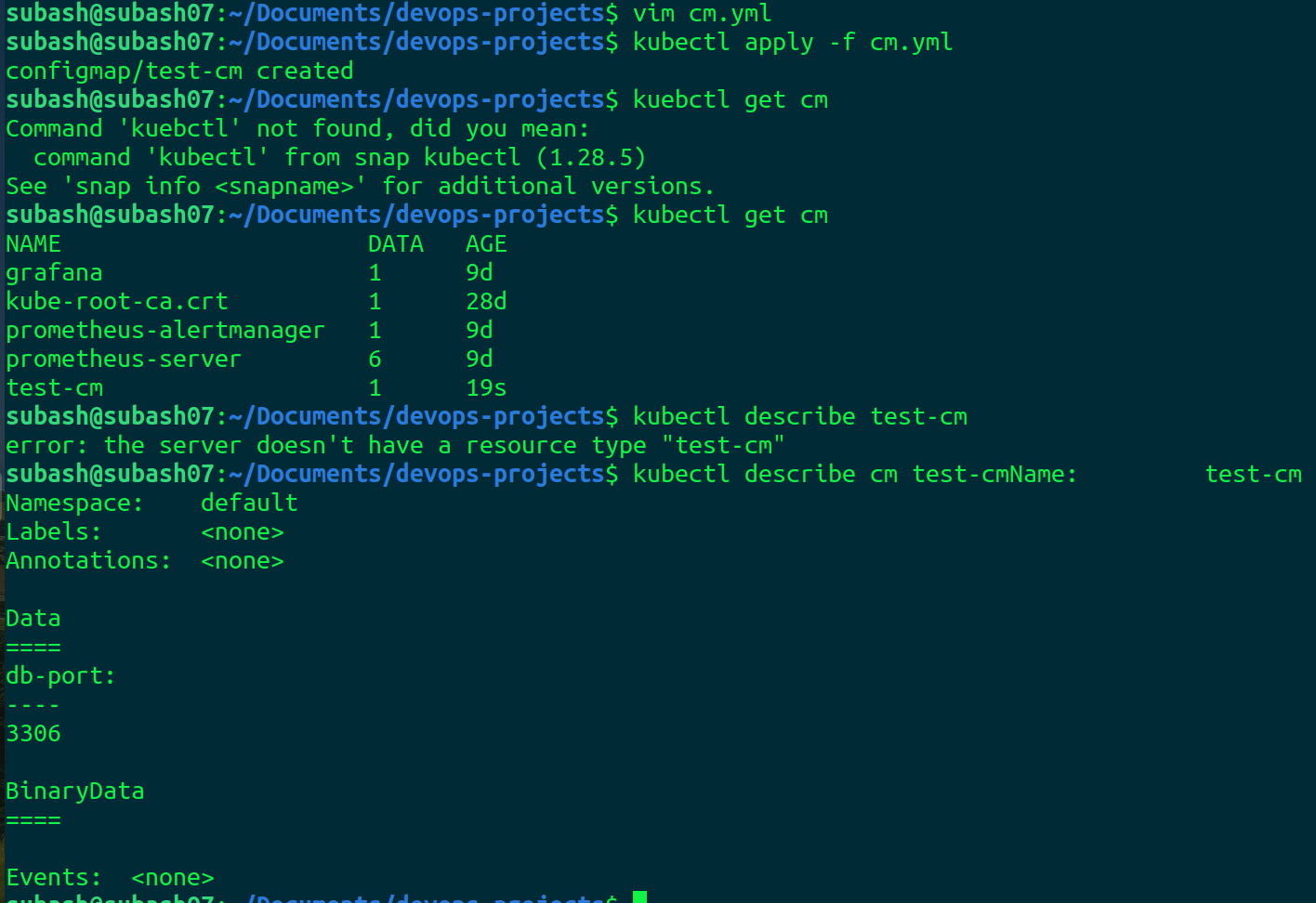
Our configmap is created.
We will take these data as environment variable in the kubernetes cluster.
We have the deployment.yml
apiVersion: apps/v1
kind: Deployment
metadata:
name: sample-python-app
labels:
app: sample-python-app
spec:
replicas: 2
selector:
matchLabels:
app: sample-python-app
template:
metadata:
labels:
app: sample-python-app
spec:
containers:
- name: python-app
image: subash07/python-app:latest
ports:
- containerPort: 8000
Create the deployment
kubectl apply -f deployment.yml
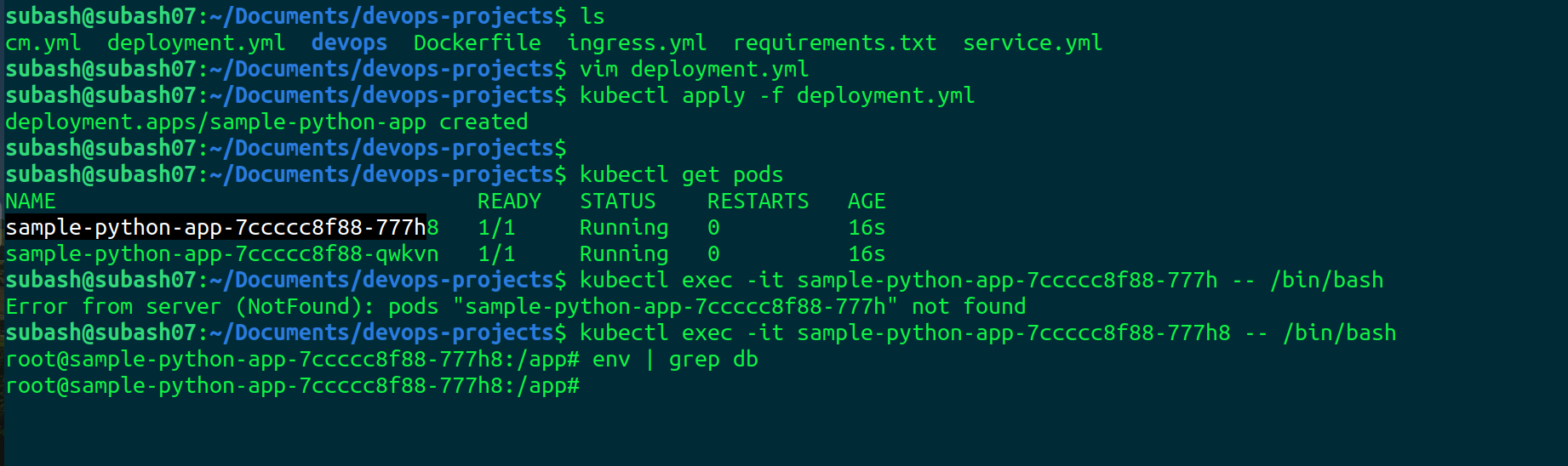
We can see that there is no environment variable concerning db.
Let's modify the deployment.yml .
env:
- name: DB-PORT
valueFrom:
configMapKeyRef:
name: test-cm
key: db-port
We will add this in the deployment.
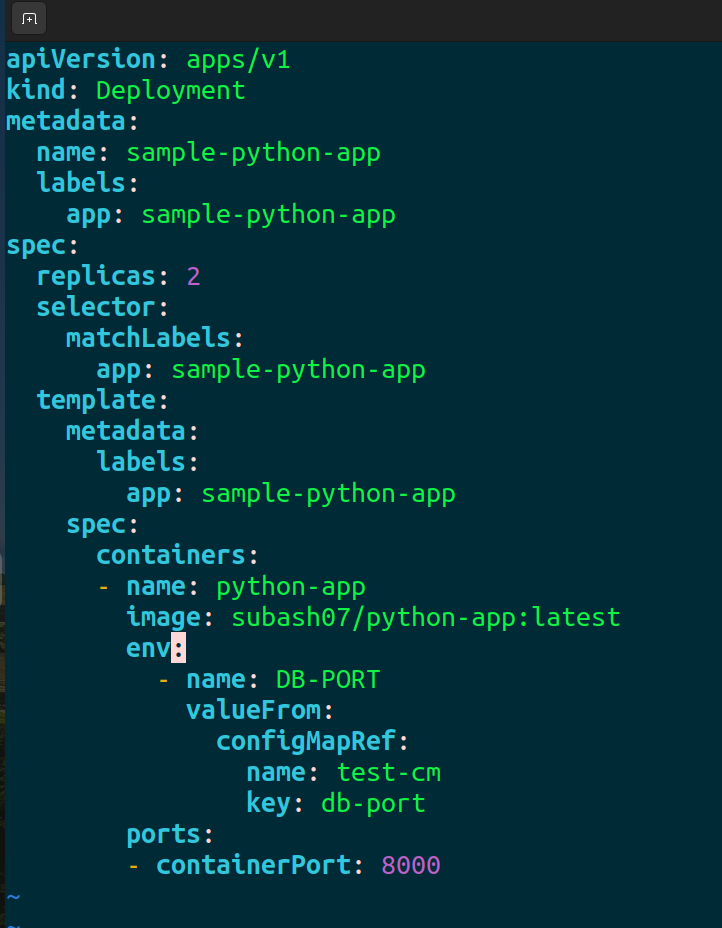
Apply it
kubectl apply -f deployment.yml
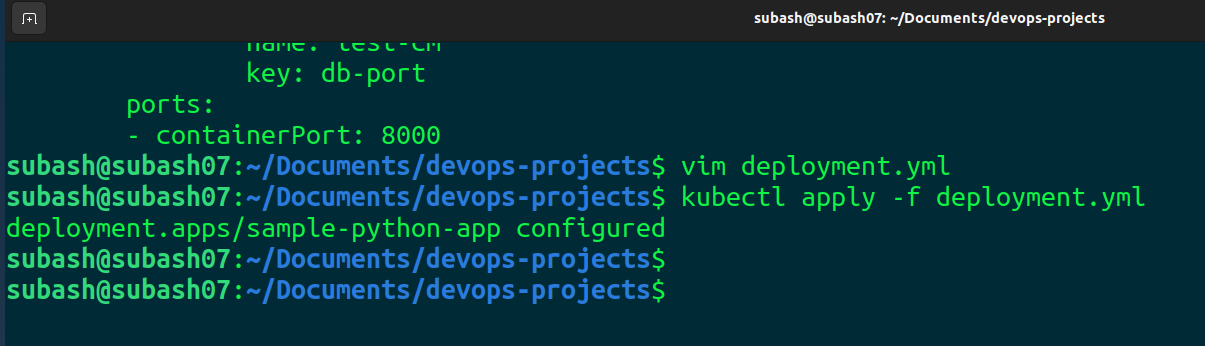
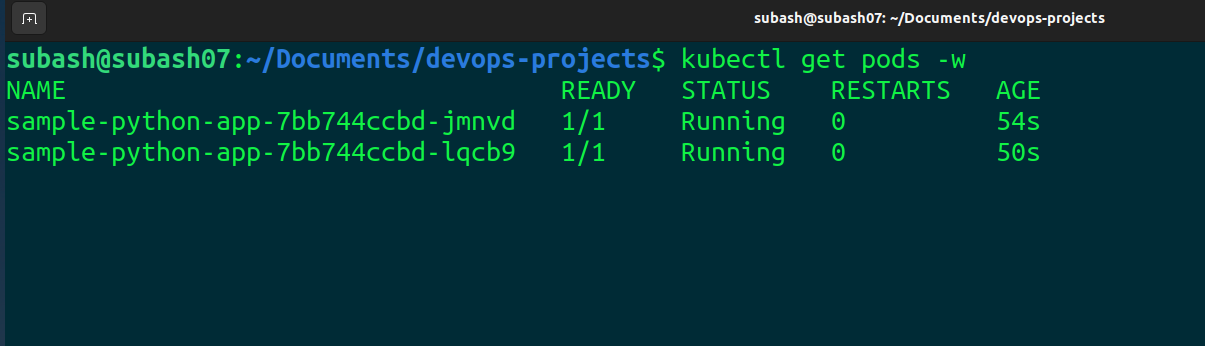
So our pods are getting restarted.
Lets exec into one of the pods
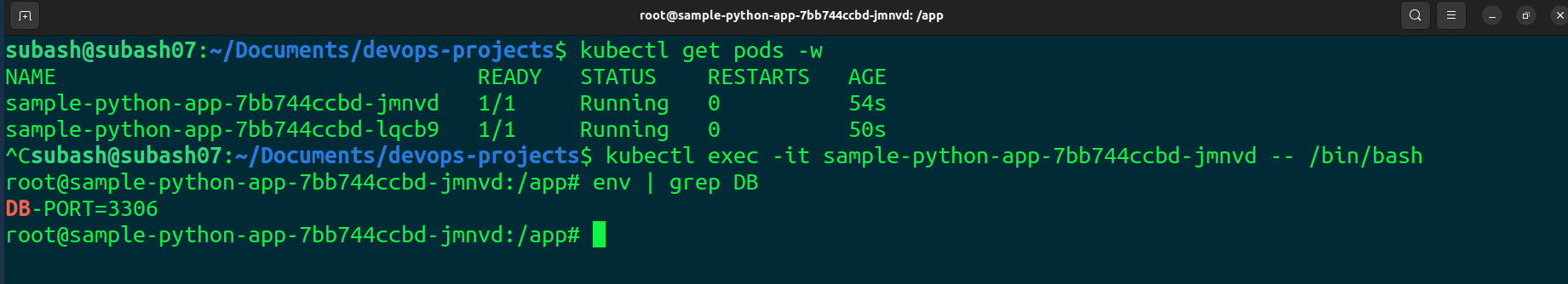
Perfect, it is working fine.
Instead of directly using the environment variable, we will mount it as a file.
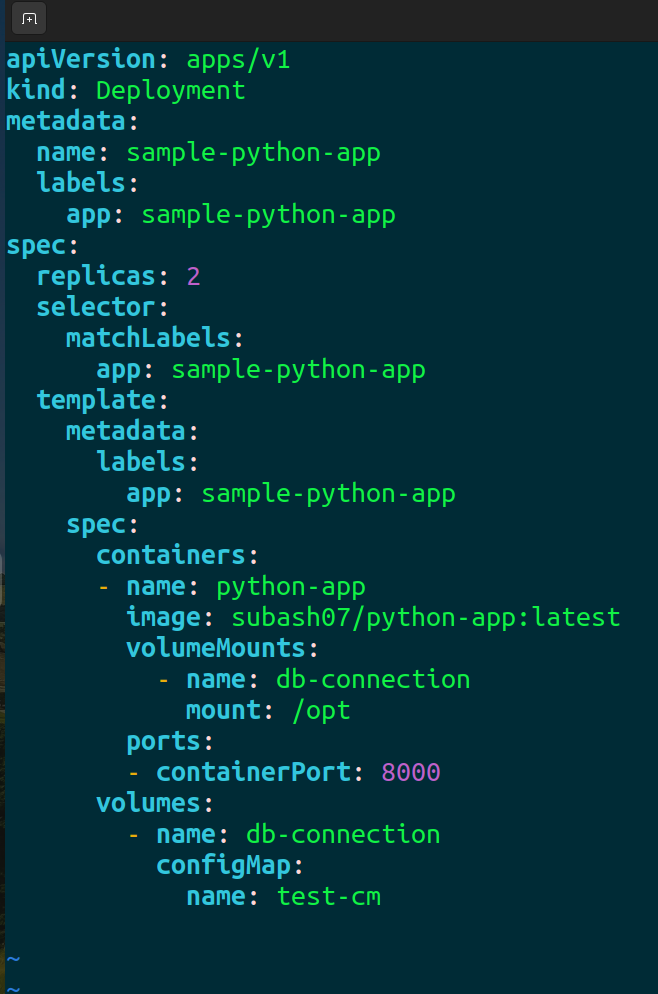
Apply
kubectl apply -f deployment.yml
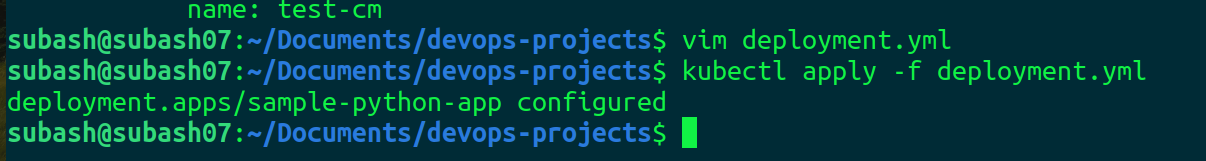
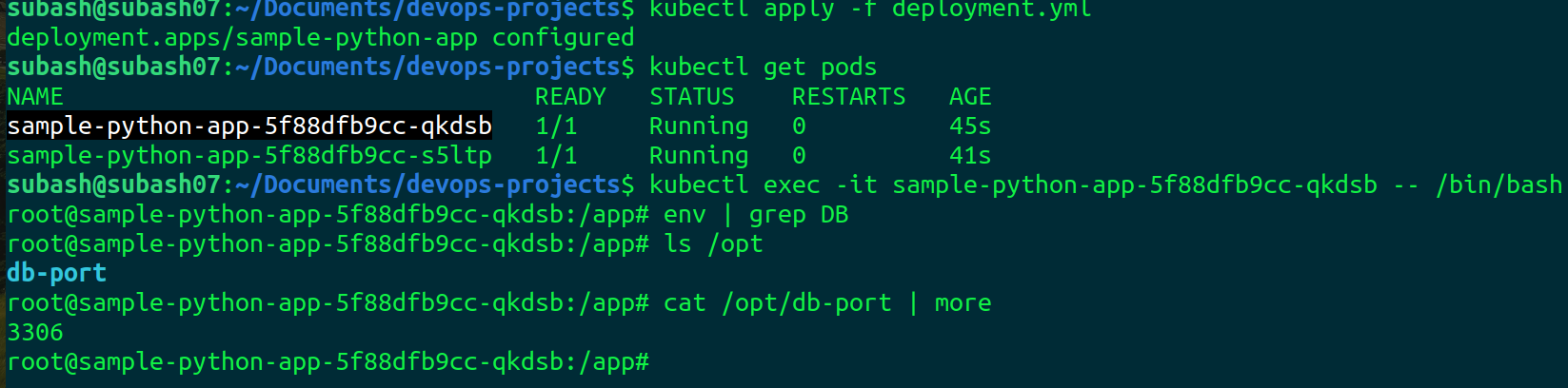
It's working perfectly fine. Now let's change the port from 3306 to 3307 in configmap and verify whether it gets updated or not.
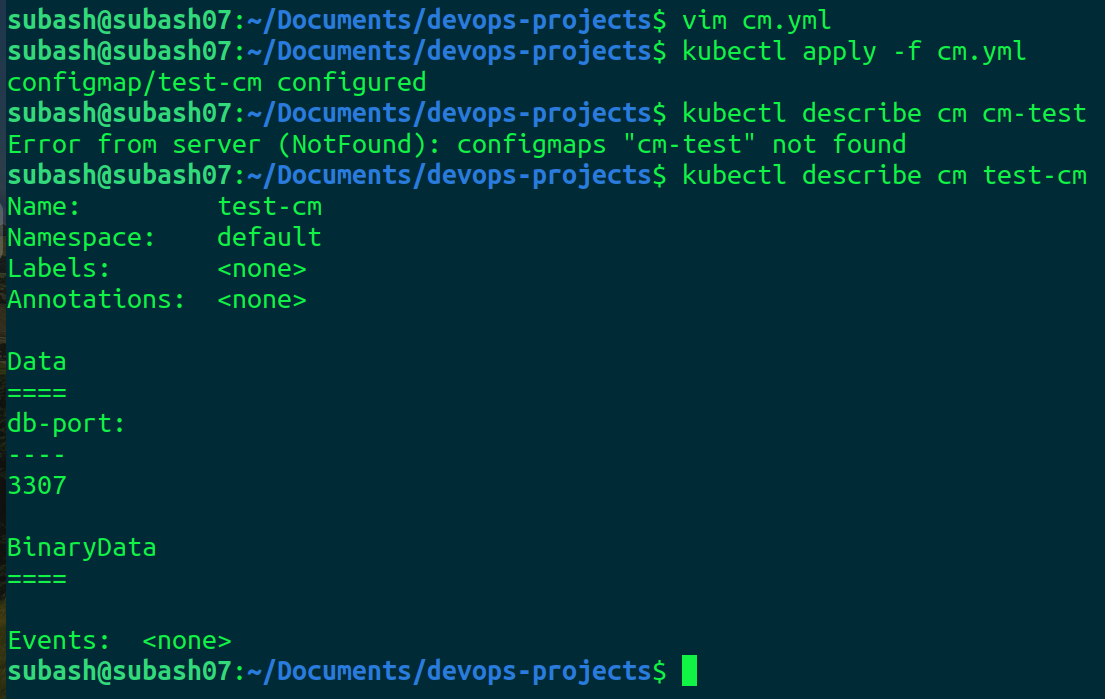
configmap is updated.
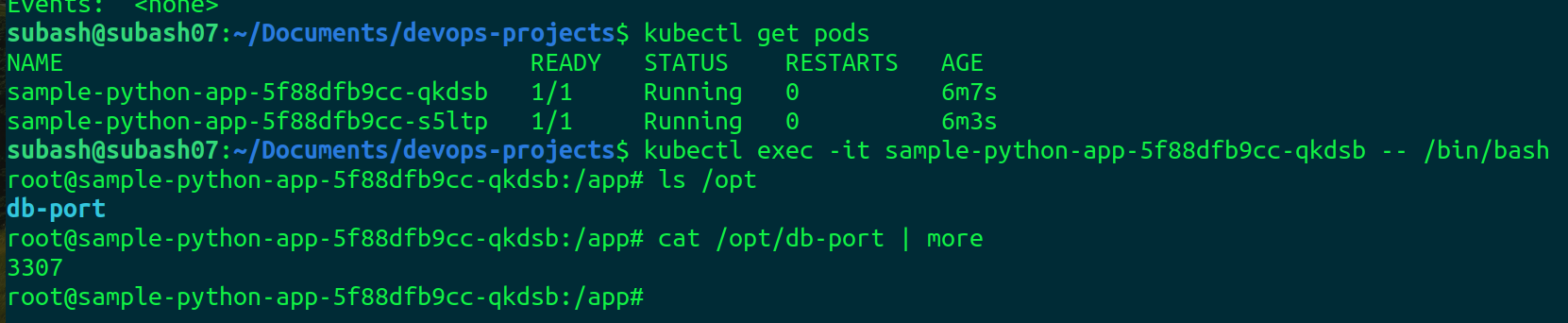
So the changes in the configmap are also updated in the app.
Let's create a simple secret to store the username password
kubectl create secret generic test-secret --from-literal=db-port="3307"
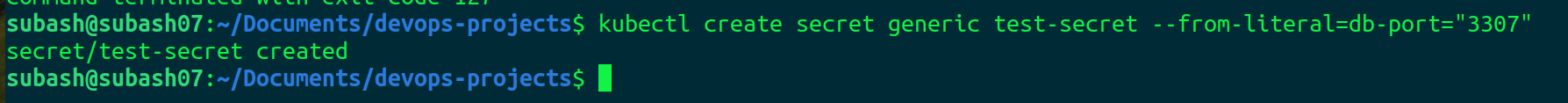
Our secret is created.
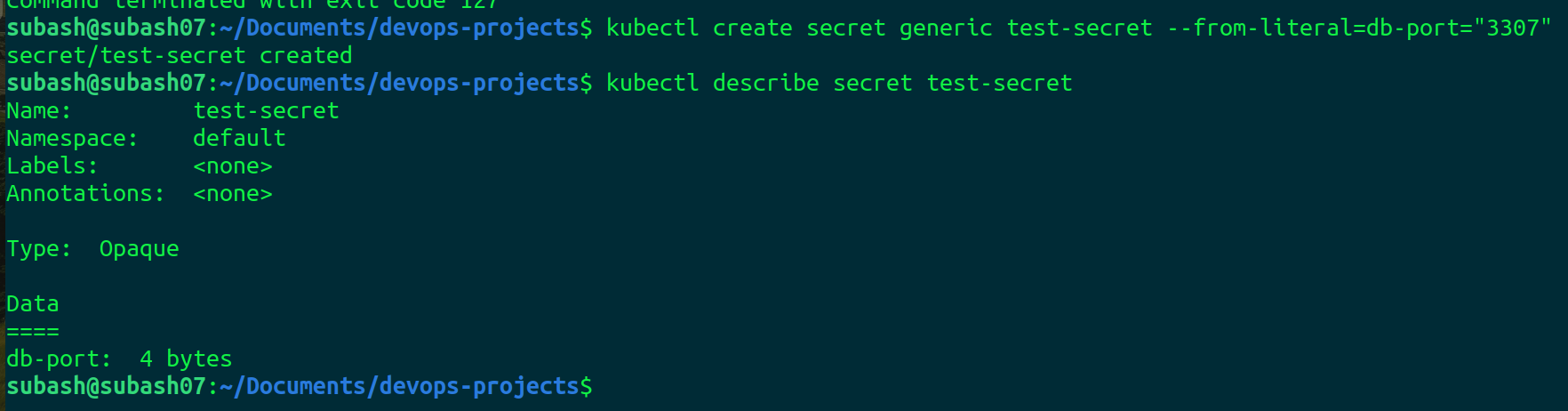
Here the db-port is encrypted.
I hope you liked this blog. If any mistake, do comment down below 🚀.
Do like and share this blog♥️
Subscribe to my newsletter
Read articles from Subash Neupane directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Subash Neupane
Subash Neupane
Computer Science graduate