S3: The storage wonder
 Sachin Adi
Sachin Adi
In my earlier article, I wrote about what the S3 service was doing for us and how we used it to create a bucket. In this article, let's talk about how the objects are stored and what policies will govern the access for these objects.
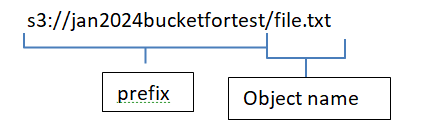
Objects in general, when we talk about with reference to cloud and specifically S3 buckets are nothing but files. These can be images, scripts, text files, excel files, word documents, pdfs etc... When you store these objects in S3 buckets these will be stored with the key. This key that I mentioned has a prefix and an object name in it. It sounds a bit confusing? Let me explain that.
Let's imagine that I have a text file called "file.txt" and I put this file straight into my bucket that I created earlier, which was "jan2024bucketfortest", there will be a key generated for this.




Let me tell you about the key now...
Now, let us discuss some of the security measures that S3 provides. These characteristics can be categorized into two types: resource-based and user-based.
User-based
IAM policies dictate which API should be allowed for a specific user from IAM.
Resource-based
This can be further split into three tunnels:
Bucket Policies
Bucket ACL
Object ACL
Bucket Policies: Bucket-wide rules from the S3 console allow cross-account access
Bucket Access Control List: These are less common and can be disabled
Object Access Control List: These are fine-grained policies and can be disabled.
Noting when the IAM principal can access an S3 object is just as important as knowing how the bucket policies are written, which is the next item I believe will be useful to know.
Condition:
If user IAM permissions ALLOW OR If the resource policy ALLOWS AND there is NO explicit DENY
Result:
IAM principal can access the S3 object
Let's talk in brief about the S3 bucket policies...
These are JSON-based policies
The structure of these policies involve Resource, Effect, Action and Principal.
Let me show you a sample of how these policies look:
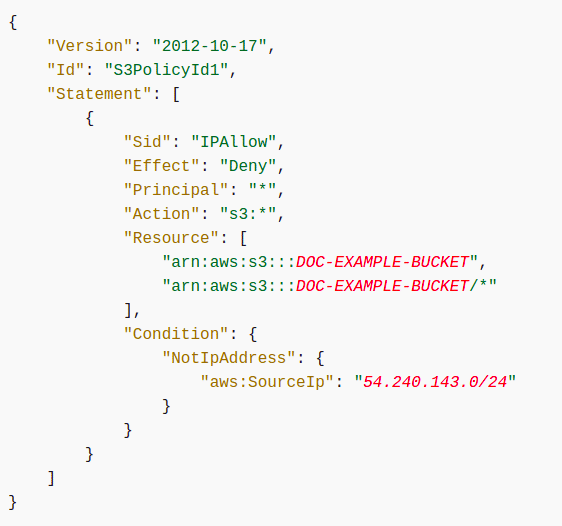
This policy specified above is used to secure AWS S3 buckets with sensitive data. You can read more about the policy and even more on security on Kloudle's Site
So what do we use this S3 bucket policy for?
This bucket policy can be used for:
Granting access to another account (Cross-Account Access)
Force the objects to be encrypted
Grant public access to the bucket.
Hmm... Well, that's all for this blog. If you feel that something is missing, you can always write to me through the comments here or feel free to drop me a note on the LinkedIn page. Happy Learning!
Subscribe to my newsletter
Read articles from Sachin Adi directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
