How to set up an example AWS environment with secure EC2 access
 Kris F
Kris F
Introduction
This guide will provide a simple way to set up an EC2 and give secure access to a user without opening any ports on the EC2.
What we'll end up with is:
an EC2 machine in our current VPC with appropriate permissions
additional permissions to a chosen user that allows sessions to above EC2
Prerequisites:
A VPC
A user with access key and ID set up on your local machine
AWS cli on your local machine to access
The advantages of this setup:
As it'll be CloudFormation, it's easy to tear it down once not used
No inbound ports need open for the EC2 => no chance to hack in via open port 22 or any other port
still full access from your own local terminal application
The CloudFormation template
AWSTemplateFormatVersion: '2010-09-09'
Description: EC2 with Session access to a user
Parameters:
InstanceType:
Type: String
Description: EC2 instance type
Default: t2.micro
VPCId:
Type: AWS::EC2::VPC::Id
Description: VPC ID where the instance will be launched
AMIId:
Type: String
Description: AMI ID for the EC2 instance
Default: ami-0a3c3a20c09d6f377
IAMUser:
Type: String
Description: The name of the existing IAM user
Resources:
MyInstance:
Type: 'AWS::EC2::Instance'
Properties:
ImageId: !Ref AMIId
InstanceType: !Ref InstanceType
IamInstanceProfile: !Ref SSMInstanceProfile
SSMInstanceProfile:
Type: 'AWS::IAM::InstanceProfile'
Properties:
Path: "/"
Roles:
- !Ref SSMRole
SSMRole:
Type: 'AWS::IAM::Role'
Properties:
AssumeRolePolicyDocument:
Version: '2012-10-17'
Statement:
- Effect: Allow
Principal:
Service: ec2.amazonaws.com
Action: 'sts:AssumeRole'
Path: "/"
ManagedPolicyArns:
- arn:aws:iam::aws:policy/AmazonSSMManagedInstanceCore
IAMUserPolicy:
Type: 'AWS::IAM::Policy'
Properties:
PolicyName: 'StartSessionPolicy'
Users:
- !Ref IAMUser
PolicyDocument:
Version: '2012-10-17'
Statement:
- Effect: "Allow"
Action: "ssm:StartSession"
Resource: !Sub "arn:aws:ec2:${AWS::Region}:${AWS::AccountId}:instance/${MyInstance}"
- Effect: "Allow"
Action:
- "ssm:DescribeSessions"
- "ssm:GetConnectionStatus"
- "ssm:DescribeInstanceProperties"
- "ec2:DescribeInstances"
Resource: "*"
- Effect: "Allow"
Action:
- "ssm:TerminateSession"
- "ssm:ResumeSession"
Resource: !Sub "arn:aws:ssm:${AWS::Region}:${AWS::AccountId}:session/${IAMUser}-*"
Outputs:
InstanceId:
Description: The Instance ID
Value: !Ref MyInstance
To run this, go to CloudFormation and upload a new template.
You'll be requested to enter a few details:
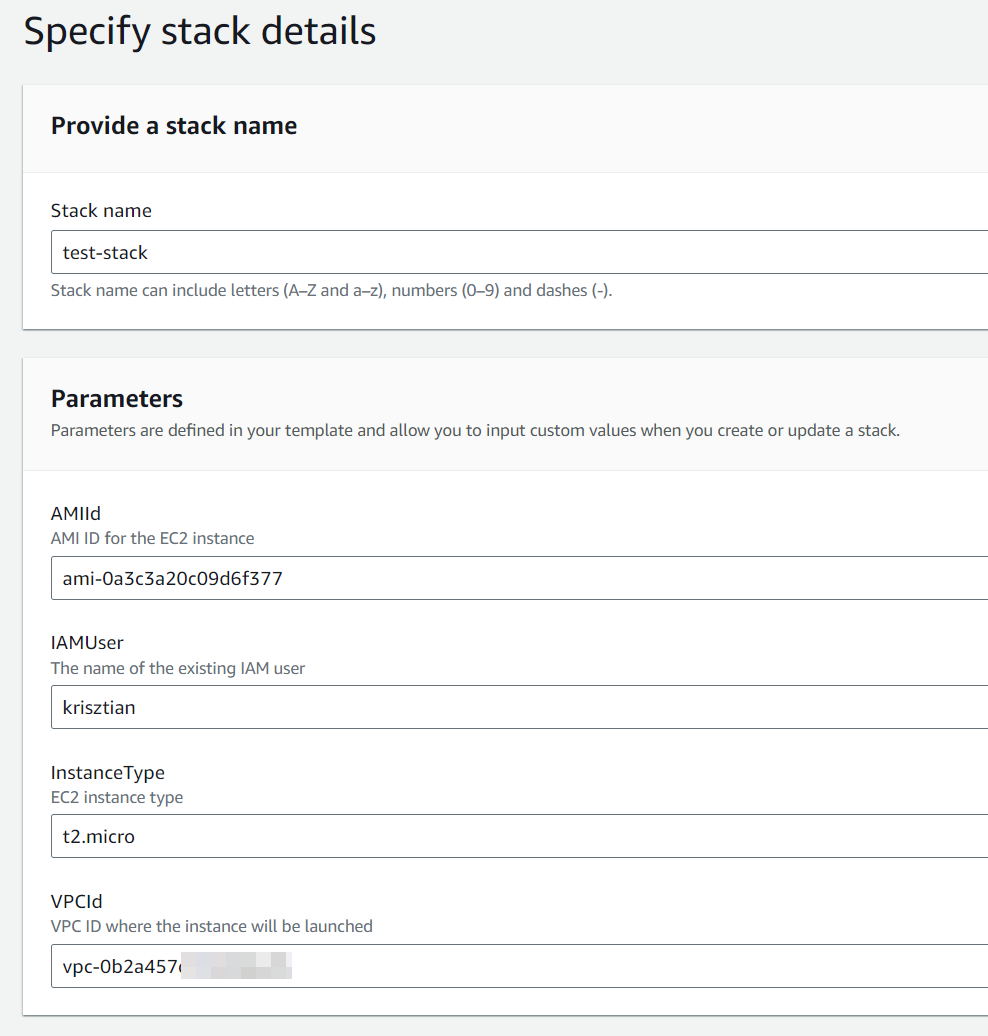
Stack name: doesn't matter, let your imagination free 🙂
IAMUser: the user you want to assign permissions to access the new EC2
AMIId : it's the ID of the amazon machine image that you should use. You can get this by manually trying to create an EC2 machine. This will be unique to your operating system requirements and region, but feel free to copy mine (us-east-1).
InstanceType: it's the type and size of instance you want to deploy.
VPCId: it's going to be a dropdown with all your VPCs. Pick one.
Once you filled this in, click next a few times and accept the checkbox about creating IAM resources.
Wait a few minutes until the stack completes and you'll be presented with your EC2 machine.
This machine will have the appropriate security groups, instance profile and your user will receive the necessary permissions to access this machine.
Accessing the machine
Port 22 SSH access will not work, as no port is open, however you can access your machine the following way from your terminal:
Make sure your and
credentialsfile contains your access key and ID and yourconfigfile contains the correct region.make a note of the instance ID. You can see that in the "outputs" tab of your CloudFormation stack.
in your console
aws ssm start-session --target i-1234567890abcdefthis will give you the default shell. If you want say bash, then run
/bin/bash
You should now have an EC2 with secure access.
Tearing everything down
Go back to your CloudFomation and click the "Delete" button on the stack.
This will remove all resources that was created beforehand.
Subscribe to my newsletter
Read articles from Kris F directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Kris F
Kris F
I am a dedicated double certified AWS Engineer with 10 years of experience, deeply immersed in cloud technologies. My expertise lies in a broad array of AWS services, including EC2, ECS, RDS, and CloudFormation. I am adept at safeguarding cloud environments, facilitating migrations to Docker and ECS, and improving CI/CD workflows with Git and Bitbucket. While my primary focus is on AWS and cloud system administration, I also have a history in software engineering, particularly in Javascript-based (Node.js, React) and SQL. In my free time I like to employ no-code/low code tools to create AI driven automations on my self hosted home lab.