Protecting Your APIs in the Wild: A Deep Dive into WAF and API Gateway Integration
 Jing Yan
Jing Yan
In today's digital age, APIs have become an integral part of our daily lives. They allow us to access and exchange data between different applications and services. However, with the increasing number of API endpoints exposed to the public, there is an ever-growing risk of cyberattacks and data breaches. This is why it is crucial to implement robust security measures to protect your APIs from malicious attacks.
Benefits of Integrating WAF and API Gateway for API Protection
Web Application Firewall (WAF) and API Gateway technologies are two of the most effective ways to secure APIs from attacks. A WAF is a security solution that sits between the internet and your API server, analyzing incoming requests and blocking any malicious traffic. On the other hand, an API Gateway is a middleware layer that sits between your API server and the client, managing access control, traffic routing, and rate limiting.
Apache APISIX, a popular open-source API gateway, offers a robust set of built-in security plugins. However, in the face of increasingly sophisticated attacks like CVEs (Common Vulnerabilities and Exposures) and zero-day exploits, relying solely on these plugins can leave your APIs vulnerable. Integrating a professional Web Application Firewall (WAF) with APISIX provides a multi-layered defense strategy, ensuring comprehensive protection against modern threats.
Understanding APISIX's Security Capabilities
Authentication and Authorization: APISIX supports plugins for
JWT,basic auth,key auth, and integration with OpenID Connect providers, enforcing access control.Rate Limiting: Prevents malicious traffic spikes and DoS attacks through plugins like
limit-conn,limit-req, andlimit-count.IP Restriction and User-Agent Filtering: Allow granular control over incoming requests based on IP addresses and user agents.
CSRF Protection: Thwarts Cross-Site Request Forgery attacks.
Limitations of API Gateway
Signature-Based Detection: APISIX plugins primarily rely on known attack signatures, leaving them ineffective against zero-day exploits that lack defined patterns.
Lack of Rule Updates: Security rules are constantly changing, which requires professional security experts and companies to maintain.
Limited Scope: While APISIX safeguards the gateway layer, WAFs provide broader protection across application layers.
Benefits of WAF and API Gateway Integration
Proactive Threat Detection: Advanced WAFs leverage machine learning and behavioral analysis to detect anomalous traffic, even without prior knowledge of vulnerabilities.
Real-Time Rule Updates: Cloud-based WAFs can quickly update rules to address emerging threats, minimizing exposure windows.
Deeper Application Protection: WAFs can filter and block malicious traffic at the application layer, shielding against attacks that bypass API gateways.
Compliance and Regulatory Adherence: Certain industries mandate WAF usage for compliance with data security regulations.
Deep Dive into the Integration Process
To integrate WAF and API Gateway, you need to choose the right tools for the job. Apache APISIX is a popular API Gateway solution that provides a scalable and flexible platform for managing your APIs. Chaitin SafeLine and Coraza are the WAF solutions that offer advanced security features and customizable rule sets.
APISIX and Chaitin SafeLine
The Chaitin SafeLine WAF is a built-in plugin from APISIX 3.5. After the chaitin-waf plug-in is enabled, traffic will be forwarded to the Chaitin WAF service to detect and prevent various web application attacks to protect the security of applications and user data.
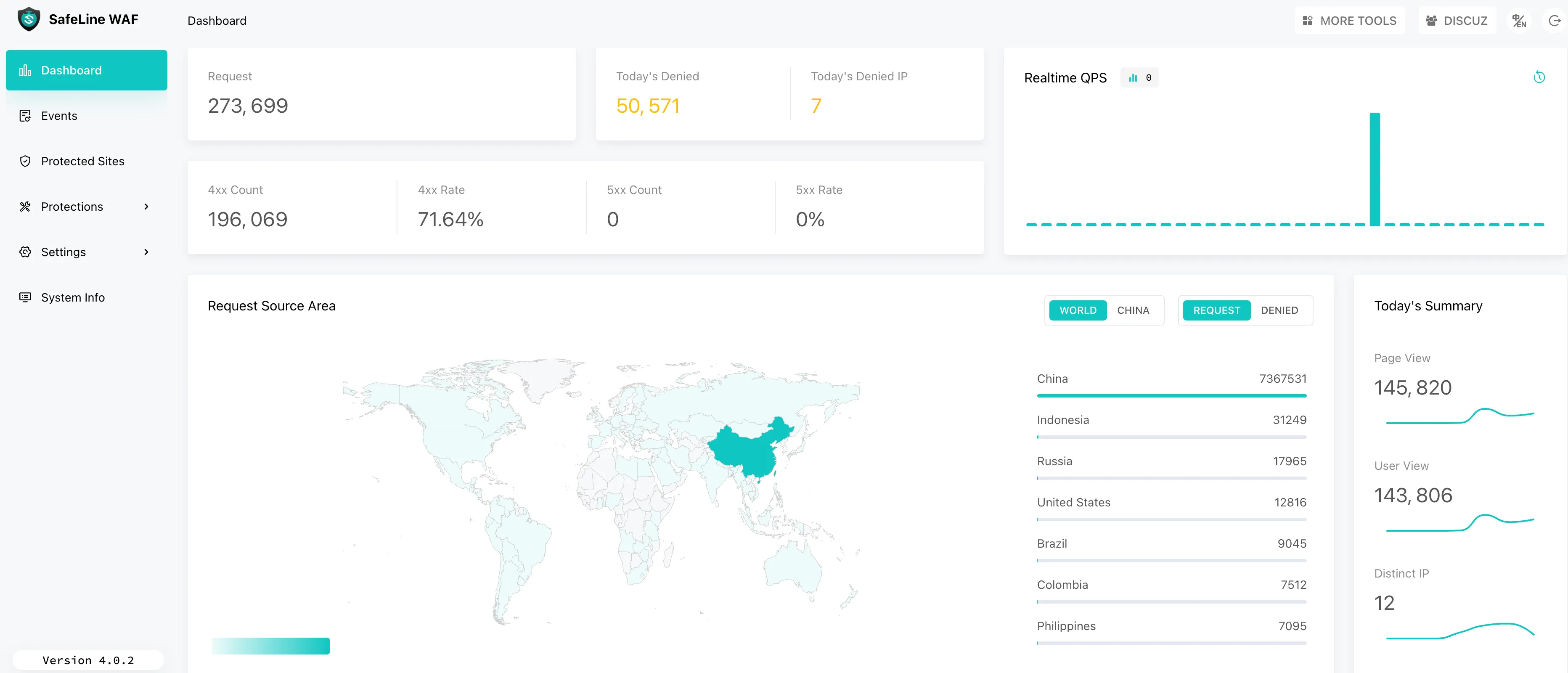
Assuming that you have installed Apache APISIX and SafeLine, the following command line can integrate the two:
curl http://127.0.0.1:9180/apisix/admin/plugin_metadata/chaitin-waf -H 'X-API-KEY: edd1c9f034335f136f87ad84b625c8f1' -X PUT -d '
{
"nodes":[
{
"host": "192.168.99.11",
"port": 8000
}
]
}'
192.168.99.11 is the ip of the SafeLine service. Then we can create a route in APISIX:
curl http://127.0.0.1:9180/apisix/admin/routes/1 -H 'X-API-KEY: edd1c9f034335f136f87ad84b625c8f1' -X PUT -d '
{
"uri": "/*",
"plugins": {
"chaitin-waf": {}
},
"upstream": {
"type": "roundrobin",
"nodes": {
"192.168.99.12:80": 1
}
}
}'
192.168.99.12 is the ip of the upstream service. The integration is complete.
Now let’s simulate SQL injection to see the effect:
curl http://127.0.0.1:9080 -d 'a=1 and 1=1'
An HTTP 403 error was returned, and as can be seen from the error message, Chaitin SafeLine successfully defended against the attack.
{"code":403,"success":false,"message":"blocked by Chaitin SafeLine Web Application Firewall","event_id":"18e0f220f7a94127acb21ad3c1b4ac47"}
APISIX and Coraza-proxy-wasm
APISIX supports developing plugins with WebAssembly (Wasm), and Coraza also provides Wasm plugins as an option. Therefore, integrating Coraza with APISIX incurs relatively low costs.
Wasm can be utilized cross-platform, allowing APISIX and Coraza to work without additional extensive modifications or adaptations. This eliminates extensive code modifications and adaptations.
Coraza is also a built-in plug-in of Apache APISIX, which can be enabled by modifying the configuration file conf/config-default.yaml:
wasm:
plugins:
- name: coraza-filter
priority: 7999
file: /home/ubuntu/coraza-proxy-wasm/build/main.wasm
Then create a route in APISIX with the rules of Coraza:
curl -i http://127.0.0.1:9180/apisix/admin/routes/1 -H 'X-API-KEY: edd1c9f034335f136f87ad84b625c8f1' -X PUT -d '{
"uri": "/anything",
"plugins": {
"coraza-filter": {
"conf": {
"directives_map": {
"default": [
"SecDebugLogLevel 9",
"SecRuleEngine On",
"SecRule REQUEST_URI \"@beginsWith /anything\" \"id:101,phase:1,t:lowercase,deny\""
]
},
"default_directives": "default"
}
}
},
"upstream": {
"type": "roundrobin",
"nodes": {
"httpbin.org:80": 1
}
}
}'
Now let's send a request to see the effect:
curl http://localhost:9080/anything -v
Check logs inlogs/error.log:
2023/08/31 09:20:39 [info] 126240#126240: *23933 Transaction interrupted tx_id="JVhHVfDuGjVbfgvDjik" context_id=2 action="deny" phase="http_request_headers", client: 127.0.0.1, server: _, request: "GET /anything HTTP/1.1", host: "localhost:9080"
2023/08/31 09:20:39 [debug] 126240#126240: *23933 Interruption already handled, sending downstream the local response tx_id="JVhHVfDuGjVbfgvDjik" context_id=2 interruption_handled_phase="http_request_headers"
Best Practices for Securing APIs Using WAF and API Gateway Integration
To ensure the security of your APIs, you should follow these best practices:
Implement a defense-in-depth strategy that includes multiple layers of security controls;
Use SSL/TLS encryption to secure data in transit;
Regularly update your WAF rule sets to ensure they are up-to-date with the latest threats;
Monitor your API traffic and logs to quickly detect and respond to security incidents.
Future Trends and Advancements in API Security and Protection
As the number of APIs in use grows, there will be a greater need for advanced security measures to protect them. Some of the future trends and advancements in API security and protection include:
AI-powered security solutions that can detect and respond to threats automatically;
Blockchain-based authentication and access control mechanisms;
Microservices-based API architectures that offer greater flexibility and scalability.
Summary
In conclusion, WAF and API Gateway integration is a critical component of API security. By following best practices and deploying the right tools, you can create a robust security layer that protects your APIs from a wide range of attacks. With the right approach, you can ensure the availability, integrity, and confidentiality of your APIs and the data they exchange.
Subscribe to my newsletter
Read articles from Jing Yan directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
